I am trying to work with multiple developers with API generated via template and they are complaining the cookie handling and XSRF token header is causing error 400 and redirects to the login page.
- ABP Framework version: v4.2.2
- UI type: MVC
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): yes, tiered MVC
- Exception message and stack trace:
- Steps to reproduce the issue:
- spin up a project
- create an aggregate root with app service to automatically expose
- create a mobile react native app (or use POSTMAN to mimic the calls)
- try to call API endpoints of your appService from mobile app or POSTMAN using /api/app/{aggregate root endpoint}
- you will need to add RequestVerificationToken with value from XSRF cookies
- try to disable that requirement with this in webmodule configure startup:
Configure<AbpAntiForgeryOptions>(options =>
{
options.AutoValidate = false;
});
- in addition, try to disable at the controller level like
[IgnoreAntiforgeryToken]
- Scratch your head because you can't figure out why the XSRF is a requirement with API and how you can disable it on automaticly exposed app service endpoints like CreateAsync() or UpdateAsync()
Errors I am seeing in the logs
[17:13:24 ERR] The required antiforgery header value "RequestVerificationToken" is not present.
- if you do not provide the header value in a POST / PUT
[16:43:35 ERR] The provided antiforgery token was meant for a different claims-based user than the current user.
[16:43:44 ERR] The required antiforgery cookie ".AspNetCore.Antiforgery.9TtSrW0hzOs" is not present.
[16:44:18 ERR] The antiforgery cookie token and request token do not match.
[18:16:19 INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy
[18:19:05 ERR] The antiforgery token could not be decrypted.
- if you use an old token value?
[18:20:33 ERR] The provided antiforgery token was meant for a different claims-based user than the current user.
- if you do not use the fresh value of the XSRF-Token cookie from last request in this request
2 Answer(s)
-
0
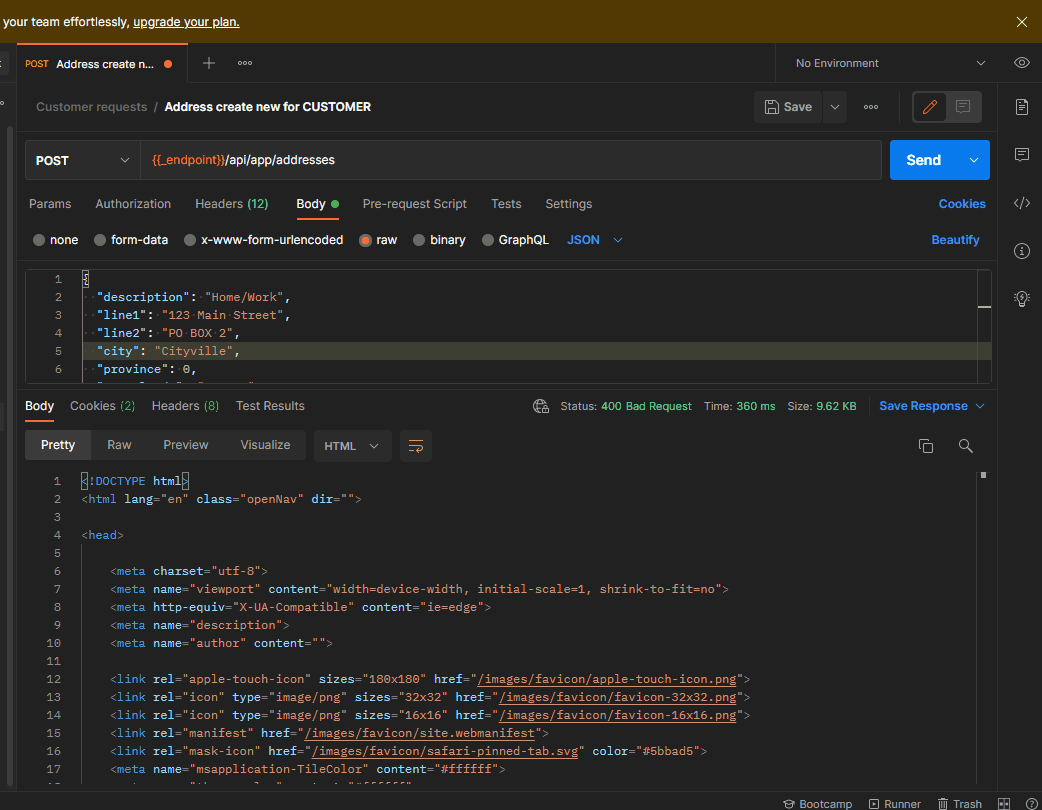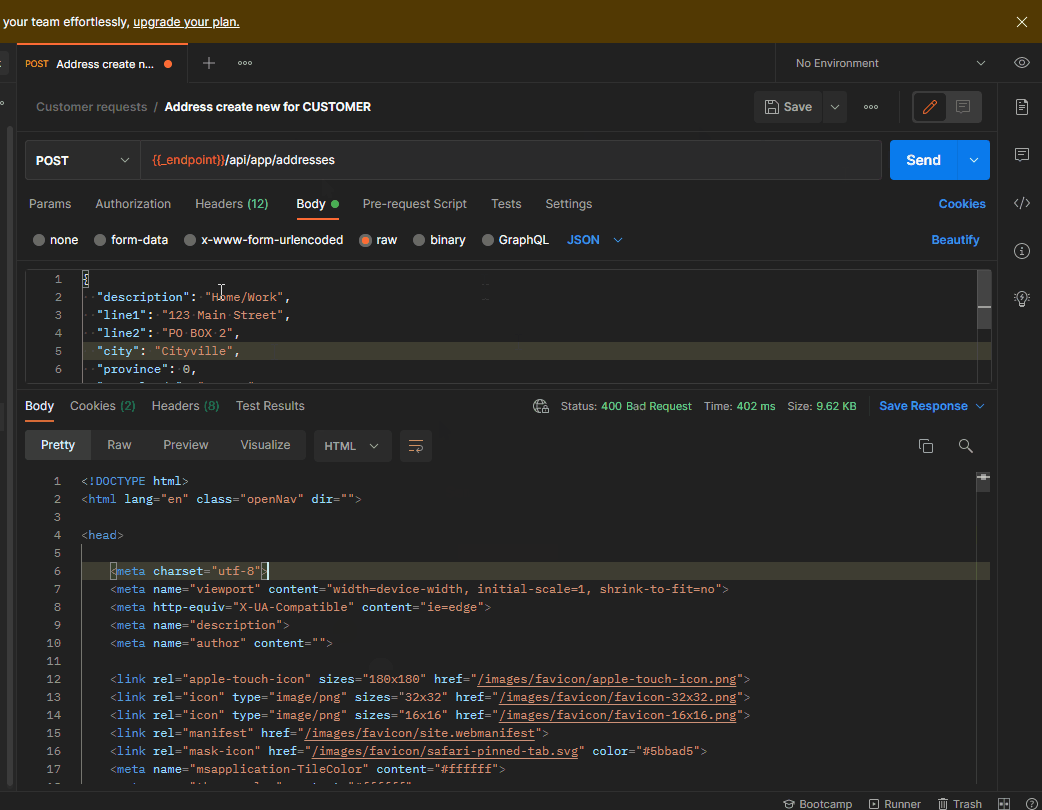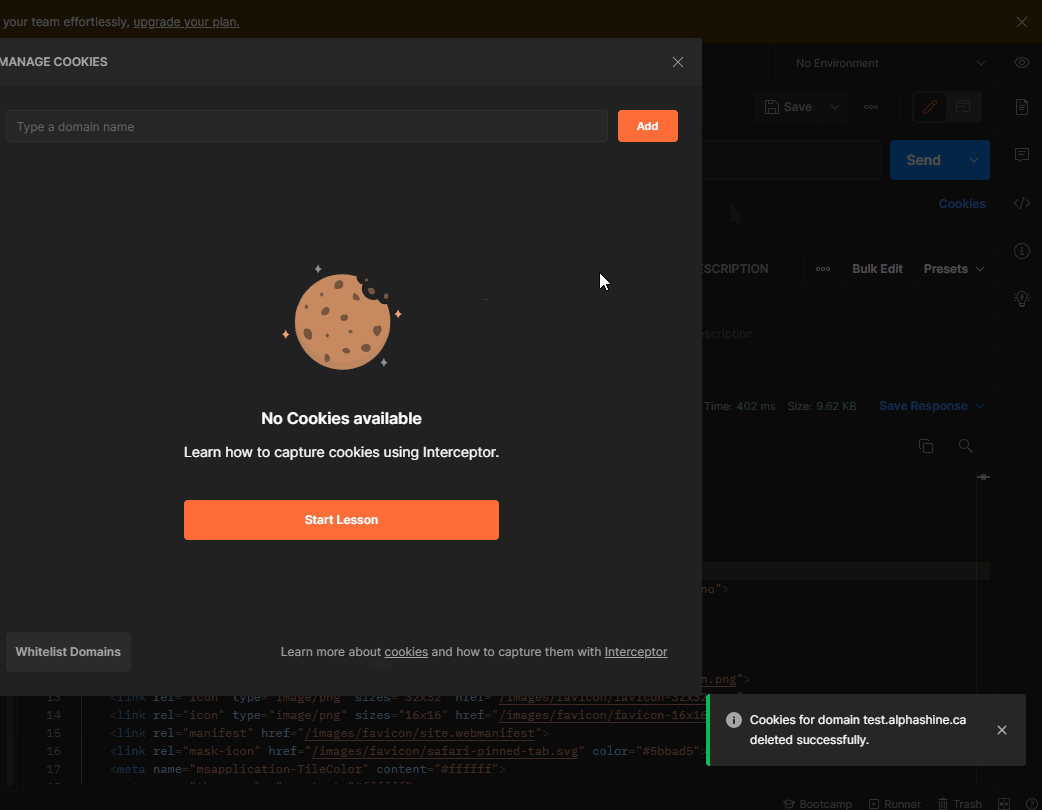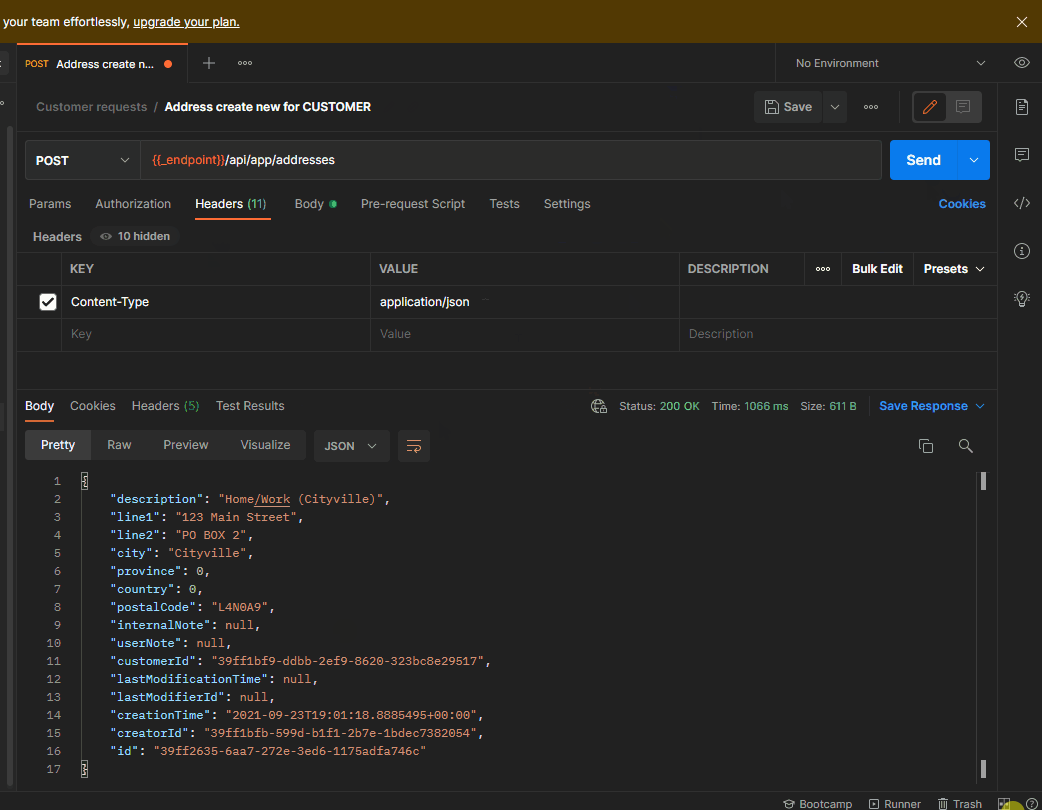
Perhaps just allowing the client to send cookies it received from the response is forcing the API system to think that RequestVerificationToken is required?? If I clear out cookies in POSTMAN then it does not have the requirement to include the RequestVerificationToken header.
Please confirm my understanding?
-
1
hi
You can remove
Configure<AbpAntiForgeryOptions>(options => { options.AutoValidate = false; }); [IgnoreAntiforgeryToken]No need to validate if antiforgery cookie is not sent. That means the request is sent from a non-browser client.
Please do not carry Cookies when you call the API in POSTMAN.