- ABP Framework version: v5.1.3
- UI type: Angular
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): yes (Microservice template)
- Exception message and stack trace:
- Steps to reproduce the issue:"
Hi,
I'm currently using the microservice template (v5.1.3)
I'm trying to figure out how to make a custom claim visible to when using CurrentUser.FindClaim in one of my custom services.
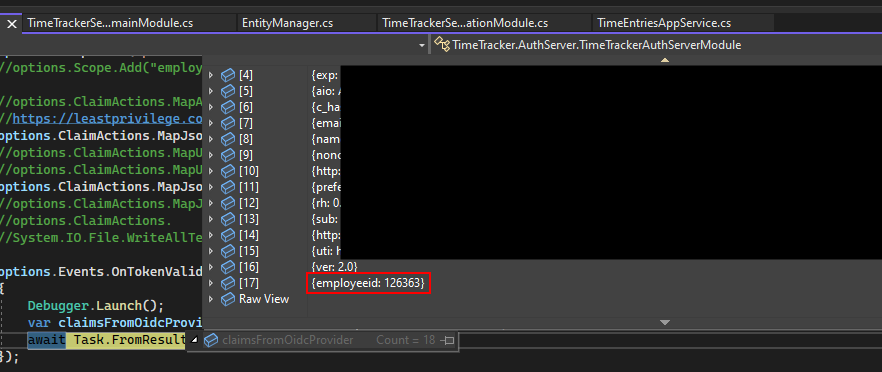
I'm using Azure Open Id Connect. The claim is in the returned Id token from Azure as seen below
I'm struggling to understand how to get that to appear as a claim on the currently logged in user.
I followed the instructions in this issue https://github.com/abpframework/abp/issues/42 but much like piresashwin in the last comment the CreateAsync method of the custom ClaimsPrincipalFactory never appears to be called.
Cheers,
Steve.
7 Answer(s)
-
0
You can check this class as sample of adding custom claims using custom claims principal factory.
-
0
You can check this class as sample of adding custom claims using custom claims principal factory.
Hi,
Thanks for that. I can now add claims to the abp user.
What would be the best way to take a value from the Azure user claims (such as the employeeid i have) and get it added to the abp user?
In the linked example it looks like the claims value is being taken from a cookie that is being set by some middleware. I'm not sure that'll work in my scenario.
Cheers,
Steve.
-
0
Can you try creating a new claims principle using claims from azure ad (employeeId) and add it to current userprinciple when onTokenReceived event?
-
0
Can you try creating a new claims principle using claims from azure ad (employeeId) and add it to current userprinciple when onTokenReceived event?
Hi,
Thanks for getting back to me.
Do you mean the OnTokenResponseReceived event?
In that event I can’t see where I would get the current user principle. I can access the claims principal, but I believe that’s just the user that authenticated with Azure. At the point that OnTokenResponseReceived is fired I’m not sure we have access to any other user principle?
Cheers,
Steve
-
0
hi
Can you try this?
var auth = await _httpContextAccessor.HttpContext.AuthenticateAsync(IdentityConstants.ExternalScheme);https://github.com/abpframework/eShopOnAbp/blob/b48dc3465980856c4f61b3532ad51fe211a6cbf7/apps/auth-server/src/EShopOnAbp.AuthServer/EShopUserPrincipleFactory.cs#L42-L53
-
0
Hi,
That works great thanks!
Cheers,
Steve.
-
0
You are welcome.