Hi Support Team,
We deployed the application on windows server and pointed to https://api.dev.mydomain.com/
Swagger UI is working perfect. When Click on Authorize it goes to login page, after successful login it is not redirecting to https://api.dev.mydomain.com
I put the app settings and openid-configuration. both seems ok but It is not running on server. Can you please help us in regards
App Settings
{
"App": {
"SelfUrl": "https://api.dev.mydomain.com",
"AngularUrl": "http://localhost:4200",
"CorsOrigins": "https://*.mydomain.com,http://10.1.48.149:4200",
"RedirectAllowedUrls": "http://localhost:4200,https://*.mydomain.com",
"DisablePII": "false",
"HealthCheckUrl": "/health-status"
},
"ConnectionStrings": {
"Default": "Connecting string....."
},
"AuthServer": {
"Authority": "https://api.dev.mydomain.com",
"RequireHttpsMetadata": "true"
},
"StringEncryption": {
"DefaultPassPhrase": "45AgJEywOpMbL0rN"
},
"OpenIddict": {
"Applications": {
"MyAppSaaS_Web": {
"ClientId": "MyAppSaaS_Web",
"ClientSecret": "1q2w3e*",
"RootUrl": "https://localhost:44361"
},
"MyAppSaaS_Web_Public_Tiered": {
"ClientId": "MyAppSaaS_Web_Public_Tiered",
"ClientSecret": "1q2w3e*",
"RootUrl": "https://localhost:44367"
},
"MyAppSaaS_App": {
"ClientId": "MyAppSaaS_App",
"RootUrl": "http://localhost9:4200"
},
"MyAppSaaS_Maui": {
"ClientId": "MyAppSaaS_Maui",
"RootUrl": "MyAppSaaS://"
},
"MyAppSaaS_Swagger": {
"ClientId": "MyAppSaaS_Swagger",
"RootUrl": "https://api.dev.mydomain.com",
"ClientSecret": "1q2w3e*"
}
}
}
}
openid-configuration
{
"issuer": "https://api.dev.mydomain.com/",
"authorization_endpoint": "https://api.dev.mydomain.com/connect/authorize",
"token_endpoint": "https://api.dev.mydomain.com/connect/token",
"introspection_endpoint": "https://api.dev.mydomain.com/connect/introspect",
"end_session_endpoint": "https://api.dev.mydomain.com/connect/logout",
"revocation_endpoint": "https://api.dev.mydomain.com/connect/revocat",
"userinfo_endpoint": "https://api.dev.mydomain.com/connect/userinfo",
"device_authorization_endpoint": "https://api.dev.mydomain.com/device",
"jwks_uri": "https://api.dev.mydomain.com/.well-known/jwks",
"grant_types_supported": [
"authorization_code",
"implicit",
"password",
"client_credentials",
"refresh_token",
"urn:ietf:params:oauth:grant-type:device_code",
"LinkLogin",
"Impersonation"
],
"response_types_supported": [
"code",
"code id_token",
"code id_token token",
"code token",
"id_token",
"id_token token",
"token",
"none"
],
"response_modes_supported": [
"form_post",
"fragment",
"query"
],
"scopes_supported": [
"openid",
"offline_access",
"email",
"profile",
"phone",
"roles",
"address"
],
"claims_supported": [
"aud",
"exp",
"iat",
"iss",
"sub"
],
"id_token_signing_alg_values_supported": [
"RS256"
],
"code_challenge_methods_supported": [
"S256"
],
"subject_types_supported": [
"public"
],
"token_endpoint_auth_methods_supported": [
"client_secret_basic",
"client_secret_post"
],
"introspection_endpoint_auth_methods_supported": [
"client_secret_basic",
"client_secret_post"
],
"revocation_endpoint_auth_methods_supported": [
"client_secret_basic",
"client_secret_post"
],
"claims_parameter_supported": false,
"request_parameter_supported": false,
"request_uri_parameter_supported": false,
"authorization_response_iss_parameter_supported": true
}
5 Answer(s)
-
0
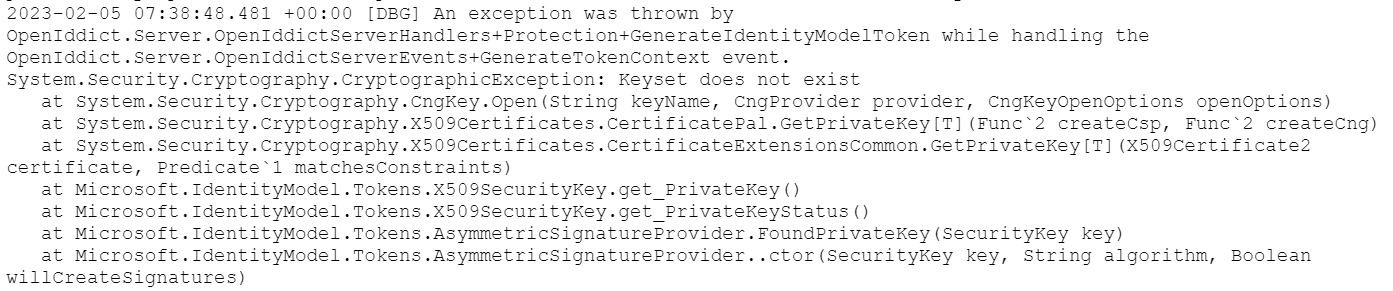
Please share the authserver logs.
-
0
-
0
If you are using IIS or Azure App Service, they may display a “Keyset does not exist” error while trying to set the application pool identity. As in your log records, so I assume you use IIS or Azure App Service and it seems your problem is in the certifications.
To avoid that, It's recommended to creating self-signed self-signed certificates and store them in the X.509 certificates store of the host machine(s). Please refer to: https://documentation.openiddict.com/configuration/encryption-and-signing-credentials.html#registering-a-development-certificate.
For more info check the documentation and also you can see this answer.
-
0
We are not using IIS or Azure App Service. Its AWS load balancer pointing to Ec2 server that is running API on it. The load balancer only forwards requests to the ec2. That's our scenario.
Secondly, We made a sample project using abp suite then published and run it at http://localhost:5000 we faced the same project. If possible please a call or teamviewer session or allow me to send you sample project to check it.
Kindly reply at your earliest, We are stuck into a point further development is halted.
-
1
The openid-providers (openiddict library in abp templates after v6) uses certificates to sign and encrypt the tokens. This is not related to ABP.
When you build your application on development environment, you use the temprorary/non-secure development signin certificate defined by the openid-provider library to not bother developers with deployment configurations in the development process. In ABP templates, you can see a code pieceas below under the AuthServer project:
if (!hostingEnvironment.IsDevelopment()) { PreConfigure<AbpOpenIddictAspNetCoreOptions>(options => { options.AddDevelopmentEncryptionAndSigningCertificate = false; }); PreConfigure<OpenIddictServerBuilder>(builder => { builder.AddSigningCertificate(GetSigningCertificate(hostingEnvironment, configuration)); builder.AddEncryptionCertificate(GetSigningCertificate(hostingEnvironment, configuration)); builder.SetIssuer(new Uri(configuration["AuthServer:Authority"])); }); }When deploying your application in different environments, you need to create a self-signed certificate or use a real certificate that handles the signing and encryption of the tokens.
If you follow the souce of
GetSigninCertificatemethod, shortest way to handle it is, creating a self signed certificate called authserver.pfx with a password and set it as embedded resource (or manually copy it to your server) so it can be read by the server.Here is a code piece how to generate self signed certificate using dotnet tooling to create a dev-cert for localhost:
dotnet dev-certs https -v -ep authserver.pfx -p 3A2AA457-5D33-48D6-936F-C48E5EF46A21Kindly reminder, this is not related to ABP.