- ABP Framework version: v5.3.1
- UI type: Angular
- DB provider: EF Core
- Exception message and stack trace:
 Cross-site scripting works by manipulating a vulnerable web site so that it returns malicious JavaScript to users. When the malicious code executes inside a victim's browser, the attacker can fully compromise their interaction with the application.
Cross-site scripting works by manipulating a vulnerable web site so that it returns malicious JavaScript to users. When the malicious code executes inside a victim's browser, the attacker can fully compromise their interaction with the application. - Steps to reproduce the issue:"
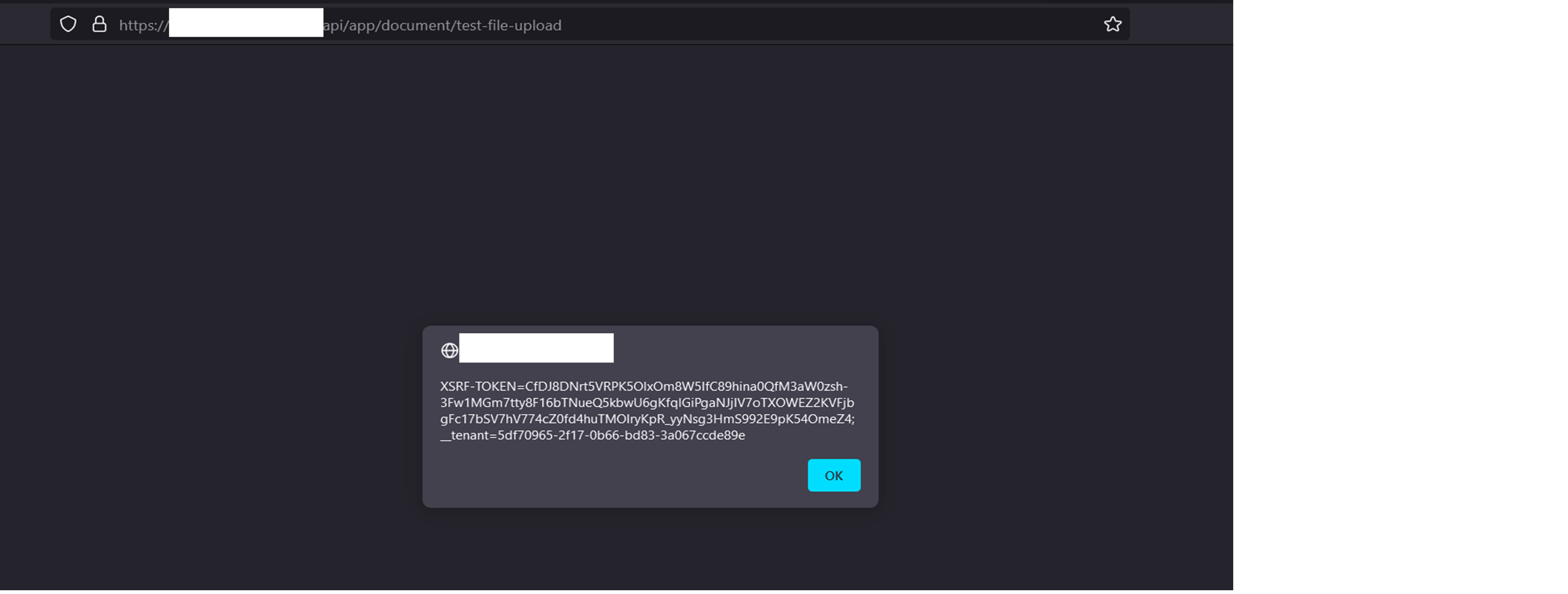
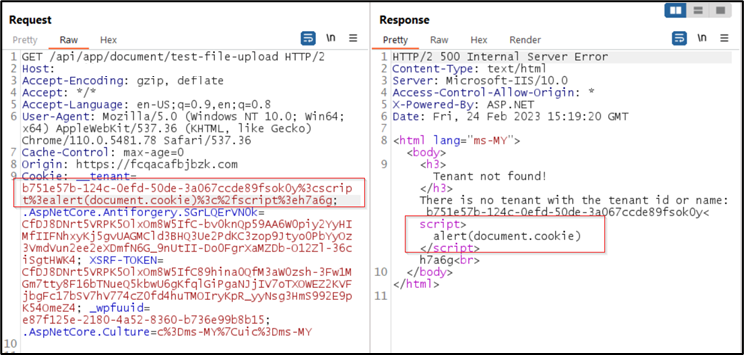
We identify that a cookie name “_tenant” was infected with XSS attack. Please sanitize this to block all executable payload in the cookie. It affected on HttpApi.Host and IdentityServer
Preventing cross-site scripting is trivial in some cases but can be much harder depending on the complexity of the application and the ways it handles user-controllable data.
3 Answer(s)
-
0
did you set this cookie value manually?
-
0
Yes, I set manually. But this issue still harmful is if attackers attack local machine and change this cookies manually to put some script. I hope ABP can take this issue seriously because it will effect our current development in term of security if this issue not solve. Tq
-
0
This is not a security issue because only the website can modify the cookies. 3rd Parties cannot alter the cookie value as the browser is responsible to secure the cookies. The scenario of attacking the local machine and getting the cookie is another issue that the victim should care about because even if the attacker retrieves the cookie, there's no need to evaluate a script on it. They can log in to your account with the cookie without any password and do whatever they want.
As summary, this is not a real-world attack vector.