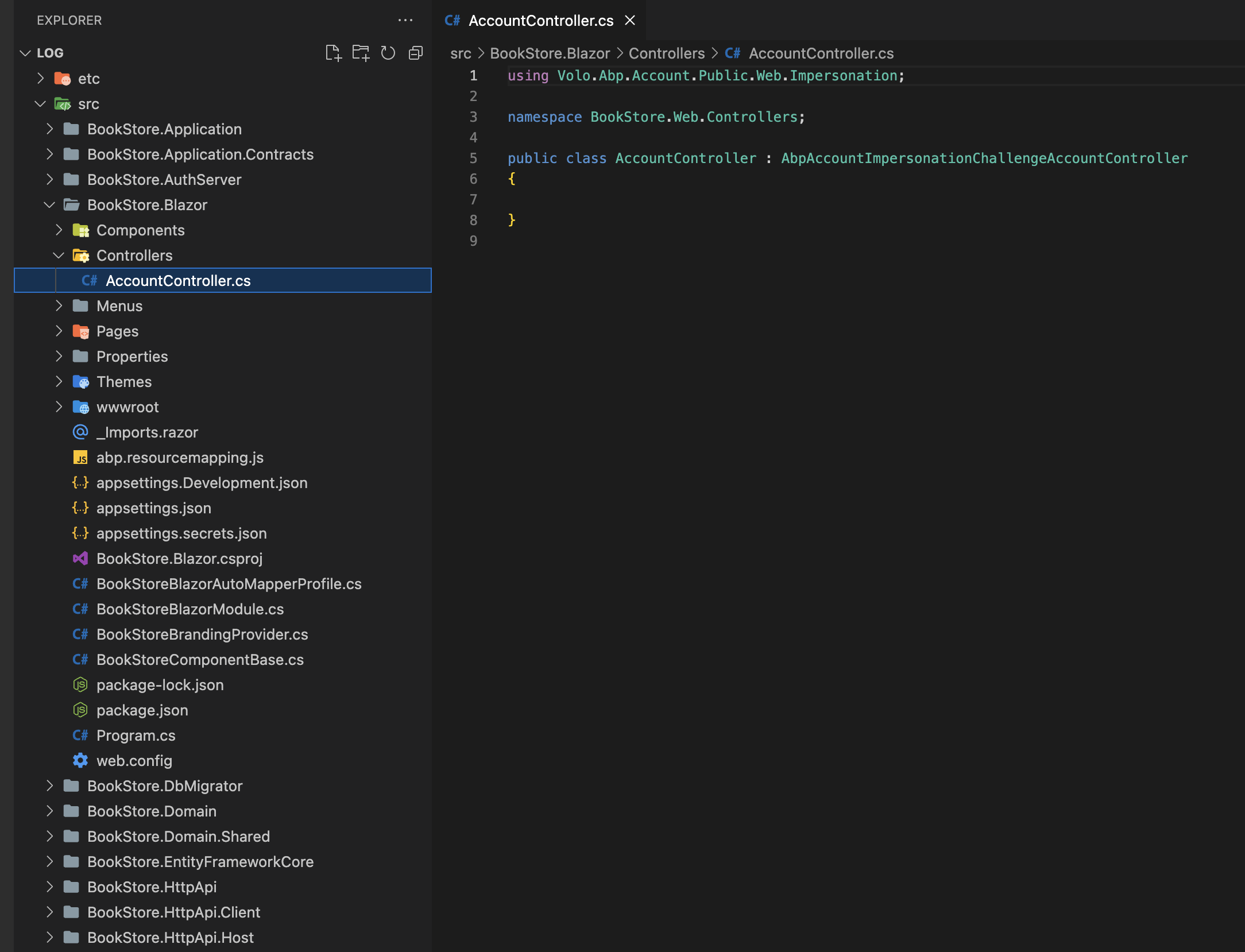
- ABP Framework version: 7.0.0
- UI type: Blazor
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): yes
- Exception message and stack trace:
2023-03-16 15:05:14.210 +07:00 [ERR] An unhandled exception has occurred while executing the request.
Volo.Abp.BusinessException: Exception of type 'Volo.Abp.BusinessException' was thrown.
at Volo.Abp.Account.Public.Web.Pages.Account.ImpersonateTenantModel.OnPostAsync()
at Microsoft.AspNetCore.Mvc.RazorPages.Infrastructure.ExecutorFactory.GenericTaskHandlerMethod.Convert[T](Object taskAsObject)
at Microsoft.AspNetCore.Mvc.RazorPages.Infrastructure.ExecutorFactory.GenericTaskHandlerMethod.Execute(Object receiver, Object[] arguments)
at Microsoft.AspNetCore.Mvc.RazorPages.Infrastructure.PageActionInvoker.InvokeHandlerMethodAsync()
at Microsoft.AspNetCore.Mvc.RazorPages.Infrastructure.PageActionInvoker.InvokeNextPageFilterAsync()
at Microsoft.AspNetCore.Mvc.RazorPages.Infrastructure.PageActionInvoker.Rethrow(PageHandlerExecutedContext context)
at Microsoft.AspNetCore.Mvc.RazorPages.Infrastructure.PageActionInvoker.Next(State& next, Scope& scope, Object& state, Boolean& isCompleted)
at Microsoft.AspNetCore.Mvc.RazorPages.Infrastructure.PageActionInvoker.InvokeInnerFilterAsync()
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.<InvokeNextExceptionFilterAsync>g__Awaited|26_0(ResourceInvoker invoker, Task lastTask, State next, Scope scope, Object state, Boolean isCompleted)
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.Rethrow(ExceptionContextSealed context)
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.Next(State& next, Scope& scope, Object& state, Boolean& isCompleted)
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.<InvokeNextResourceFilter>g__Awaited|25_0(ResourceInvoker invoker, Task lastTask, State next, Scope scope, Object state, Boolean isCompleted)
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.Rethrow(ResourceExecutedContextSealed context)
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.Next(State& next, Scope& scope, Object& state, Boolean& isCompleted)
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.<InvokeFilterPipelineAsync>g__Awaited|20_0(ResourceInvoker invoker, Task lastTask, State next, Scope scope, Object state, Boolean isCompleted)
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.<InvokeAsync>g__Logged|17_1(ResourceInvoker invoker)
at Microsoft.AspNetCore.Mvc.Infrastructure.ResourceInvoker.<InvokeAsync>g__Logged|17_1(ResourceInvoker invoker)
at Microsoft.AspNetCore.Routing.EndpointMiddleware.<Invoke>g__AwaitRequestTask|6_0(Endpoint endpoint, Task requestTask, ILogger logger)
at Volo.Abp.AspNetCore.Serilog.AbpSerilogMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext()
--- End of stack trace from previous location ---
at Volo.Abp.AspNetCore.Auditing.AbpAuditingMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Volo.Abp.AspNetCore.Auditing.AbpAuditingMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext()
--- End of stack trace from previous location ---
at Swashbuckle.AspNetCore.SwaggerUI.SwaggerUIMiddleware.Invoke(HttpContext httpContext)
at Swashbuckle.AspNetCore.Swagger.SwaggerMiddleware.Invoke(HttpContext httpContext, ISwaggerProvider swaggerProvider)
at Microsoft.AspNetCore.Authorization.AuthorizationMiddleware.Invoke(HttpContext context)
at IdentityServer4.Hosting.IdentityServerMiddleware.Invoke(HttpContext context, IEndpointRouter router, IUserSession session, IEventService events, IBackChannelLogoutService backChannelLogoutService)
at IdentityServer4.Hosting.MutualTlsEndpointMiddleware.Invoke(HttpContext context, IAuthenticationSchemeProvider schemes)
at Microsoft.AspNetCore.Authentication.AuthenticationMiddleware.Invoke(HttpContext context)
at IdentityServer4.Hosting.BaseUrlMiddleware.Invoke(HttpContext context)
at Volo.Abp.AspNetCore.Uow.AbpUnitOfWorkMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext()
--- End of stack trace from previous location ---
at Volo.Abp.AspNetCore.ExceptionHandling.AbpExceptionHandlingMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Volo.Abp.AspNetCore.ExceptionHandling.AbpExceptionHandlingMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext()
--- End of stack trace from previous location ---
at Volo.Abp.AspNetCore.MultiTenancy.MultiTenancyMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext()
--- End of stack trace from previous location ---
at Microsoft.AspNetCore.Builder.ApplicationBuilderAbpJwtTokenMiddlewareExtension.<>c__DisplayClass0_0.<<UseJwtTokenMiddleware>b__0>d.MoveNext()
--- End of stack trace from previous location ---
at Microsoft.AspNetCore.Builder.ApplicationBuilderAbpJwtTokenMiddlewareExtension.<>c__DisplayClass0_0.<<UseJwtTokenMiddleware>b__0>d.MoveNext()
--- End of stack trace from previous location ---
at Microsoft.AspNetCore.Authentication.AuthenticationMiddleware.Invoke(HttpContext context)
at Volo.Abp.AspNetCore.Security.AbpSecurityHeadersMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext()
--- End of stack trace from previous location ---
at Volo.Abp.AspNetCore.Tracing.AbpCorrelationIdMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext()
--- End of stack trace from previous location ---
at Microsoft.AspNetCore.Localization.RequestLocalizationMiddleware.Invoke(HttpContext context)
at Microsoft.AspNetCore.RequestLocalization.AbpRequestLocalizationMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext()
--- End of stack trace from previous location ---
at Microsoft.AspNetCore.Diagnostics.DeveloperExceptionPageMiddlewareImpl.Invoke(HttpContext context)
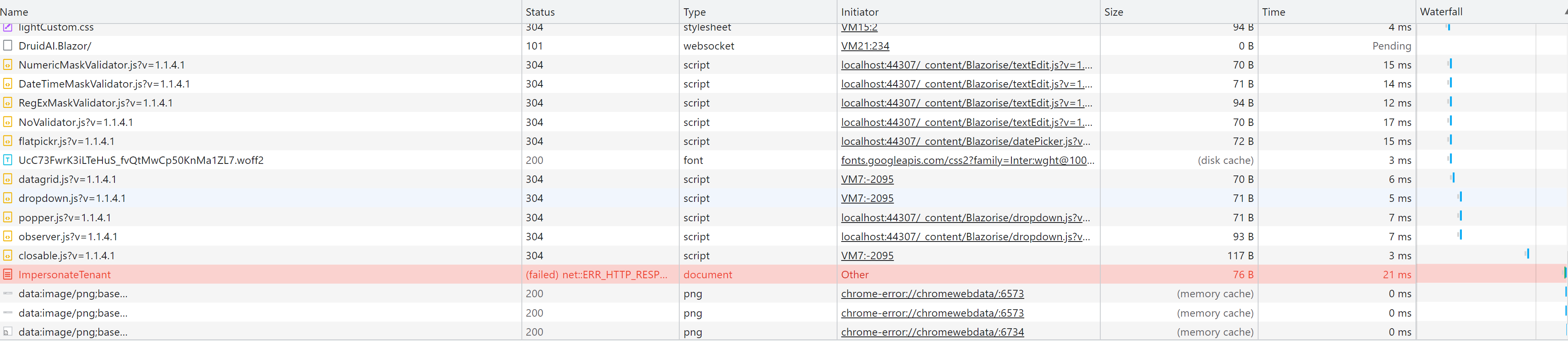
- Steps to reproduce the issue:" When I implement Impersonation and login tenant from Host or login to any user from host admin, I got this error I follow document here https://docs.abp.io/en/commercial/latest/modules/account/impersonation I have added new authentication so I am not sure it is correct or not. Here is my configuration
private void ConfigureAuthentication(ServiceConfigurationContext context, IConfiguration configuration)
{
context.Services.AddAuthentication()
.AddJwtBearer(options =>
{
options.Authority = configuration["AuthServer:Authority"];
options.RequireHttpsMetadata = Convert.ToBoolean(configuration["AuthServer:RequireHttpsMetadata"]);
options.Audience = "DruidAI";
})
.AddJwtBearer("Default", options =>
{
options.Authority = configuration["AuthServer:Authority"];
options.RequireHttpsMetadata = Convert.ToBoolean(configuration["AuthServer:RequireHttpsMetadata"]);
options.Audience = "DruidAI";
options.Configuration = new OpenIdConnectConfiguration();
options.TokenValidationParameters = new TokenValidationParameters
{
ValidateIssuer = false,
ValidateAudience = false,
ValidateLifetime = true,
ValidateIssuerSigningKey = true,
IssuerSigningKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(configuration["Jwt:SecretKey"]))
};
});
context.Services
.AddAuthorization()
.AddAuthorization(options =>
{
var defaultAuthorizationPolicyBuilder = new AuthorizationPolicyBuilder(
JwtBearerDefaults.AuthenticationScheme, "Default");
defaultAuthorizationPolicyBuilder =
defaultAuthorizationPolicyBuilder.RequireAuthenticatedUser();
options.DefaultPolicy = defaultAuthorizationPolicyBuilder.Build();
});
}
private void ConfigureImpersonation(ServiceConfigurationContext context, IConfiguration configuration)
{
context.Services.Configure<SaasHostBlazorOptions>(options =>
{
options.EnableTenantImpersonation = true;
});
context.Services.Configure<AbpIdentityProBlazorOptions>(options =>
{
options.EnableUserImpersonation = true;
});
context.Services.Configure<AbpAccountOptions>(options =>
{
options.TenantAdminUserName = "admin";
options.ImpersonationTenantPermission = SaasHostPermissions.Tenants.Impersonation;
options.ImpersonationUserPermission = IdentityPermissions.Users.Impersonation;
});
}
32 Answer(s)
-
0
hi
What the code of
BusinessException? -
0
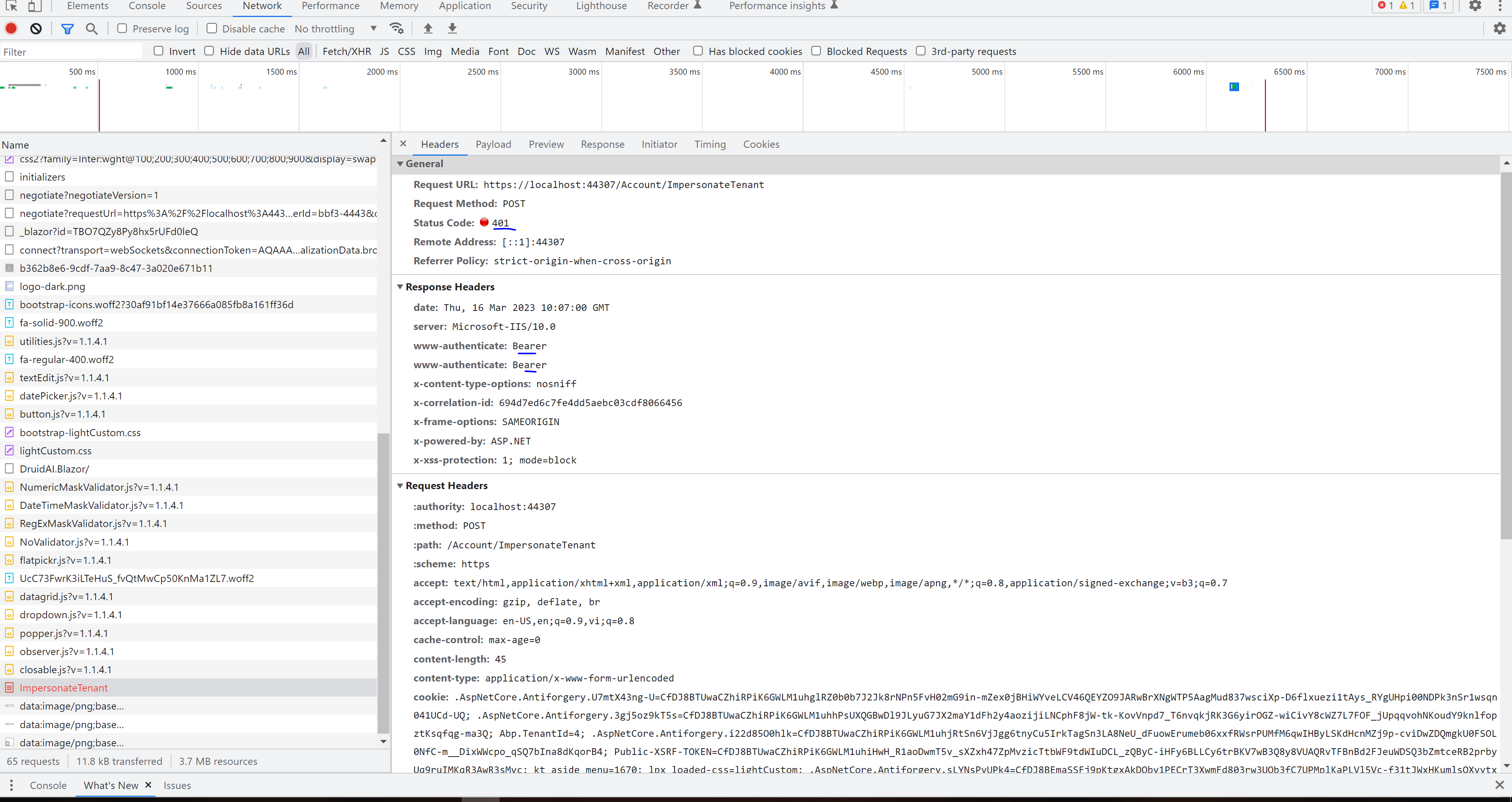
I think I do not update any in business, it was error on this page Volo.Abp.BusinessException: Exception of type 'Volo.Abp.BusinessException' was thrown. at Volo.Abp.Account.Public.Web.Pages.Account.ImpersonateTenantModel.OnPostAsync()
That one I have not modified yet! Regards,
-
0
hi
Please remove
UseDeveloperExceptionPagerelated code and catch the exception to see its code and message.// if (env.IsDevelopment()) // { // app.UseDeveloperExceptionPage(); // } // else // { // app.UseErrorPage(); // app.UseHsts(); // } app.Use(async (httpContext, func) => { try { await func(httpContext); } catch (BusinessException e) { Console.WriteLine(e.Code); throw; } }); -
0
-
0
And I got this in log 2023-03-16 17:11:23.873 +07:00 [INF] Authorization failed. These requirements were not met: DenyAnonymousAuthorizationRequirement: Requires an authenticated user.
-
0
If I disabled app.UseDeveloperExceptionPage(); It gives error 401 UnauthorizedAn internal error occurred during your request!
-
0
hi
Please share with me a project that can reproduce the problem, Thanks liming.ma@volosoft.com
-
0
I could not share project due to confidentiality, is there anything I can try or help in debug? I could share configure file if it is help
-
0
hi
How can I reproduce this in a new project? Please steps and code. Thanks
-
0
-
0
CLI will write secrets in
appsettings.secrets.jsonMake sure you've logged in.
Usage: abp login <username> abp login <username> -p <password> abp login <username> --device Example: abp login john abp login john -p 1234 See the documentation for more info: https://docs.abp.io/en/abp/latest/CLI -
0
-
0
hi
What do you mean
enable IdentityServer? -
0
I see this in MVC project if (bool.Parse(configuration["IdentityServer:IsEnabled"])) { IdentityModelEventSource.ShowPII = true; authenticationBuilder.AddIdentityServerAuthentication("IdentityBearer", options => { options.Authority = configuration["IdentityServer:Authority"]; options.ApiName = configuration["IdentityServer:ApiName"]; options.ApiSecret = configuration["IdentityServer:ApiSecret"]; options.RequireHttpsMetadata = false; }); }
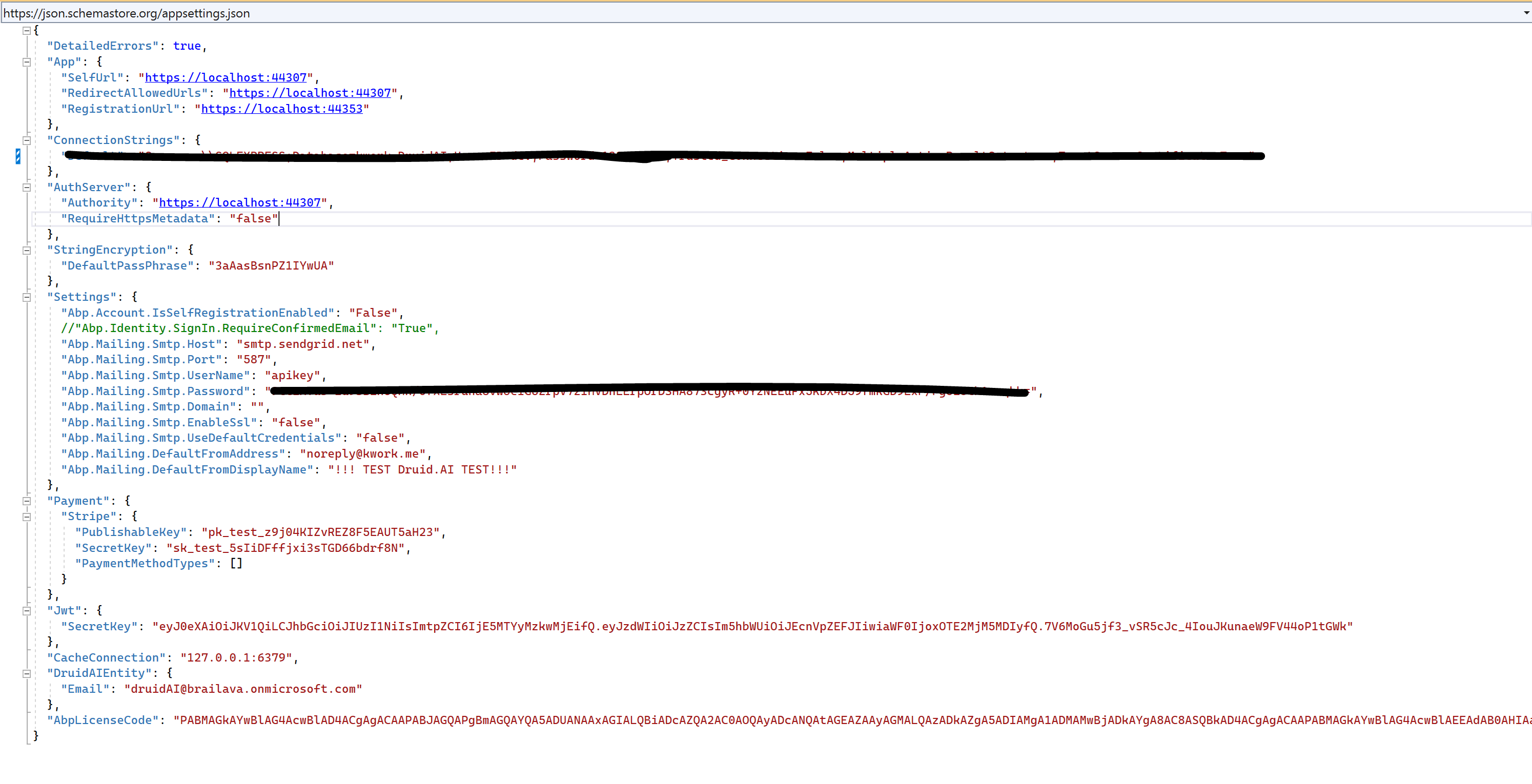
but in Blazor app, we do not have it. Can I send you appsetting and module configure so you can give me a suggestion? appsetting.json { "DetailedErrors": true, "App": { "SelfUrl": "https://localhost:44307", "RedirectAllowedUrls": "https://localhost:44307", "RegistrationUrl": "https://localhost:44353" }, "ConnectionStrings": { "Default": "Server=.\\SQLEXPRESS;Database=druidAI;User ID=dev;Password=123456789;Trusted_Connection=False;MultipleActiveResultSets=true;TrustServerCertificate=True" }, "AuthServer": { "Authority": "https://localhost:44307", "RequireHttpsMetadata": "false" }, "StringEncryption": { "DefaultPassPhrase": "3aAasBsnPZ1IYwUA" }, "Settings": { "Abp.Account.IsSelfRegistrationEnabled": "False", //"Abp.Identity.SignIn.RequireConfirmedEmail": "True", "Abp.Mailing.Smtp.Host": "", "Abp.Mailing.Smtp.Port": "587", "Abp.Mailing.Smtp.UserName": "", "Abp.Mailing.Smtp.Password": "", "Abp.Mailing.Smtp.Domain": "", "Abp.Mailing.Smtp.EnableSsl": "false", "Abp.Mailing.Smtp.UseDefaultCredentials": "false", "Abp.Mailing.DefaultFromAddress": "", "Abp.Mailing.DefaultFromDisplayName": "" }, "Payment": { "Stripe": { "PublishableKey": "", "SecretKey": "", "PaymentMethodTypes": [] } }, "Authentication": { "JwtBearer": { "IsEnabled": "true", "SecurityKey": "key", "Issuer": "DruidAI", "Audience": "DruidAI" } }, "IdentityServer": { "IsEnabled": "false", "Authority": "https://localhost:44307/", "ApiName": "default-api", "ApiSecret": "secret", "Clients": [] }, "CacheConnection": "127.0.0.1:6379", "DruidAIEntity": { "Email": "druidAI@brailava.onmicrosoft.com" }, "AbpLicenseCode": "" }
-
0
DruidAIBlazorModule
namespace DruidAI.Blazor { [DependsOn( typeof(AIGeneratorBlazorModule), typeof(DruidAIApplicationModule), typeof(DruidAIEntityFrameworkCoreModule), typeof(DruidAIHttpApiModule), typeof(AbpAutofacModule), typeof(AbpSwashbuckleModule), typeof(AbpAccountPublicWebImpersonationModule), typeof(AbpAspNetCoreSerilogModule), //typeof(AbpAccountPublicWebOpenIddictModule), typeof(AbpAspNetCoreComponentsServerLeptonXThemeModule), typeof(AbpAspNetCoreMvcUiLeptonXThemeModule), typeof(AbpAccountPublicWebIdentityServerModule), // typeof(AbpAccountPublicBlazorServerModule), typeof(AbpAccountAdminBlazorServerModule), typeof(AbpAuditLoggingBlazorServerModule), typeof(AbpIdentityProBlazorServerModule), //typeof(LeptonThemeManagementBlazorServerModule), typeof(AbpIdentityServerBlazorServerModule), typeof(LanguageManagementBlazorServerModule), typeof(SaasHostBlazorServerModule), typeof(TextTemplateManagementBlazorServerModule), typeof(AbpPaymentStripeWebModule), typeof(AbpPaymentWebModule), typeof(AbpPaymentAdminBlazorModule), typeof(AbpPaymentAdminBlazorServerModule), typeof(AbpGdprBlazorServerModule) )] public class DruidAIBlazorModule : AbpModule { public override void PreConfigureServices(ServiceConfigurationContext context) { context.Services.PreConfigure<AbpMvcDataAnnotationsLocalizationOptions>(options => { options.AddAssemblyResource( typeof(DruidAIResource), typeof(DruidAIDomainModule).Assembly, typeof(DruidAIDomainSharedModule).Assembly, typeof(DruidAIApplicationModule).Assembly, typeof(DruidAIApplicationContractsModule).Assembly, typeof(DruidAIBlazorModule).Assembly, typeof(AbpPaymentStripeWebModule).Assembly, typeof(AbpPaymentWebModule).Assembly ); }); } public override void ConfigureServices(ServiceConfigurationContext context) { var hostingEnvironment = context.Services.GetHostingEnvironment(); var configuration = context.Services.GetConfiguration(); //From Startup.cs removed context.Services.AddTransient<TokenManagerMiddleware>(); context.Services.AddTransient<ITokenManager, TokenManager>(); context.Services.AddSingleton<IHttpContextAccessor, HttpContextAccessor>(); ConfigureAuthentication(context, configuration); ConfigureUrls(configuration); ConfigureBundles(); ConfigureImpersonation(context, configuration); ConfigureAutoMapper(); ConfigureVirtualFileSystem(hostingEnvironment); ConfigureLocalizationServices(); ConfigureSwaggerServices(context.Services); ConfigureExternalProviders(context, configuration); ConfigureAutoApiControllers(); ConfigureBlazorise(context); ConfigureRouter(context); ConfigureMenu(context); ConfigureCookieConsent(context, configuration); ConfigureLeptonTheme(); ConfigurePaymentModule(configuration); ConfigureIdentityOptions(context); ConfigureHubOptions(); //Not configure here as done on Startup (required from Azure deployment...) ConfigureDistributedCacheOptions(context, configuration);
ServicePointManager.Expect100Continue = true; ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls | SecurityProtocolType.Tls11 | SecurityProtocolType.Tls12; } /// <summary> /// Define Cache connection string /// </summary> private void ConfigureDistributedCacheOptions(ServiceConfigurationContext context, IConfiguration configuration) { Configure<RedisCacheOptions>(options => { options.Configuration = configuration["redis:connectionString"]; }); //context.Services.AddDistributedRedisCache(r => { r.Configuration = configuration["redis:connectionString"]; }); } private void ConfigureCookieConsent(ServiceConfigurationContext context, IConfiguration configuration) { context.Services.AddAbpCookieConsent(options => { options.IsEnabled = true; options.CookiePolicyUrl = "https://www.druid.ai/privacy/"; options.PrivacyPolicyUrl = "https://www.druid.ai/privacy/"; }); } /// <summary> /// Refresh filter Features / Edition through EditionEndDate /// </summary> private void ConfigureHubOptions() { Configure<HubOptions>(options => { options.AddFilter<AbpRefreshEditionIdFilter>(); }); } private void ConfigureIdentityOptions(ServiceConfigurationContext context) { #if !DEBUG context.Services.Configure<IdentityOptions>(options => { options.SignIn.RequireConfirmedAccount = true; options.SignIn.RequireConfirmedEmail = true; options.SignIn.RequireConfirmedPhoneNumber = false; }); #endif } private void ConfigurePaymentModule(IConfiguration configuration) { Configure<AbpSaasPaymentOptions>(options => { options.IsPaymentSupported = true; }); Configure<PaymentWebOptions>(options => { options.RootUrl = configuration["App:SelfUrl"]; options.CallbackUrl = configuration["App:SelfUrl"]; }); } private void ConfigureRouter(ServiceConfigurationContext context) { Configure<AbpRouterOptions>(options => { options.AppAssembly = typeof(DruidAIBlazorModule).Assembly; }); } private void ConfigureUrls(IConfiguration configuration) { Configure<AppUrlOptions>(options => { options.Applications["MVC"].RootUrl = configuration["App:SelfUrl"]; options.RedirectAllowedUrls.AddRange(configuration["App:RedirectAllowedUrls"].Split(',')); }); } private void ConfigureMenu(ServiceConfigurationContext context) { Configure<AbpNavigationOptions>(options => { options.MenuContributors.Add(new DruidAIMenuContributor(/*context.Services.GetConfiguration()*/)); }); } private void ConfigureBundles() { Configure<AbpBundlingOptions>(options => { // MVC UI options.StyleBundles.Configure( LeptonXThemeBundles.Styles.Global, bundle => { bundle.AddFiles("/global-styles.css"); } ); // Blazor UI options.StyleBundles.Configure( BlazorLeptonXThemeBundles.Styles.Global, bundle => { bundle.AddFiles("/blazor-global-styles.css"); } ); }); } ///Added private void ConfigureAuthentication(ServiceConfigurationContext context, IConfiguration configuration) { context.Services.AddAuthentication() .AddJwtBearer(options => { options.Authority = configuration["AuthServer:Authority"]; options.RequireHttpsMetadata = Convert.ToBoolean(configuration["AuthServer:RequireHttpsMetadata"]); options.Audience = "DruidAI"; }); if (bool.Parse(configuration["Authentication:JwtBearer:IsEnabled"])) { IdentityModelEventSource.ShowPII = true; context.Services.AddAuthentication() .AddJwtBearer("Default", options => { options.Authority = configuration["AuthServer:Authority"]; options.RequireHttpsMetadata = Convert.ToBoolean(configuration["AuthServer:RequireHttpsMetadata"]); options.Audience = "Brailava"; options.Configuration = new OpenIdConnectConfiguration(); options.TokenValidationParameters = new TokenValidationParameters { ValidateIssuer = false, ValidateAudience = false, ValidateLifetime = true, ValidateIssuerSigningKey = true, IssuerSigningKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(configuration["Authentication:JwtBearer:SecurityKey"])) }; }); context.Services.AddAuthorization(options => { var defaultAuthorizationPolicyBuilder = new AuthorizationPolicyBuilder(JwtBearerDefaults.AuthenticationScheme, "Default"); defaultAuthorizationPolicyBuilder = defaultAuthorizationPolicyBuilder.RequireAuthenticatedUser(); options.DefaultPolicy = defaultAuthorizationPolicyBuilder.Build(); }); } //if (bool.Parse(configuration["IdentityServer:IsEnabled"])) //{ // IdentityModelEventSource.ShowPII = true; // context.Services.AddAuthentication().add("IdentityBearer", options => // { // options.Authority = configuration["IdentityServer:Authority"]; // options.ApiName = configuration["IdentityServer:ApiName"]; // options.ApiSecret = configuration["IdentityServer:ApiSecret"]; // options.RequireHttpsMetadata = false; // }); //} } private void ConfigureImpersonation(ServiceConfigurationContext context, IConfiguration configuration) { context.Services.Configure<SaasHostBlazorOptions>(options => { options.EnableTenantImpersonation = true; }); context.Services.Configure<AbpIdentityProBlazorOptions>(options => { options.EnableUserImpersonation = true; }); context.Services.Configure<AbpAccountOptions>(options => { options.TenantAdminUserName = "admin"; options.ImpersonationTenantPermission = SaasHostPermissions.Tenants.Impersonation; options.ImpersonationUserPermission = IdentityPermissions.Users.Impersonation; }); } private void ConfigureVirtualFileSystem(IWebHostEnvironment hostingEnvironment) { if (hostingEnvironment.IsDevelopment()) { Configure<AbpVirtualFileSystemOptions>(options => { options.FileSets.ReplaceEmbeddedByPhysical<DruidAIDomainSharedModule>(Path.Combine(hostingEnvironment.ContentRootPath, $"..{Path.DirectorySeparatorChar}DruidAI.Domain.Shared")); options.FileSets.ReplaceEmbeddedByPhysical<DruidAIDomainModule>(Path.Combine(hostingEnvironment.ContentRootPath, $"..{Path.DirectorySeparatorChar}DruidAI.Domain")); options.FileSets.ReplaceEmbeddedByPhysical<DruidAIApplicationContractsModule>(Path.Combine(hostingEnvironment.ContentRootPath, $"..{Path.DirectorySeparatorChar}DruidAI.Application.Contracts")); options.FileSets.ReplaceEmbeddedByPhysical<DruidAIApplicationModule>(Path.Combine(hostingEnvironment.ContentRootPath, $"..{Path.DirectorySeparatorChar}DruidAI.Application")); options.FileSets.ReplaceEmbeddedByPhysical<DruidAIBlazorModule>(hostingEnvironment.ContentRootPath); }); } } private void ConfigureSwaggerServices(IServiceCollection services) { services.AddAbpSwaggerGen( options => { options.SwaggerDoc("v1", new OpenApiInfo { Title = "DruidAI API", Version = "v1" }); options.DocInclusionPredicate((docName, description) => true); options.CustomSchemaIds(type => type.FullName); } ); } private void ConfigureExternalProviders(ServiceConfigurationContext context, IConfiguration configuration) { context.Services.AddAuthentication() .AddGoogle(GoogleDefaults.AuthenticationScheme, _ => { }) .WithDynamicOptions<GoogleOptions, GoogleHandler>( GoogleDefaults.AuthenticationScheme, options => { options.WithProperty(x => x.ClientId); options.WithProperty(x => x.ClientSecret, isSecret: true); } ) .AddMicrosoftAccount(MicrosoftAccountDefaults.AuthenticationScheme, options => { //Personal Microsoft accounts as an example. options.AuthorizationEndpoint = "https://login.microsoftonline.com/consumers/oauth2/v2.0/authorize"; options.TokenEndpoint = "https://login.microsoftonline.com/consumers/oauth2/v2.0/token"; }) .WithDynamicOptions<MicrosoftAccountOptions, MicrosoftAccountHandler>( MicrosoftAccountDefaults.AuthenticationScheme, options => { options.WithProperty(x => x.ClientId); options.WithProperty(x => x.ClientSecret, isSecret: true); } ) .AddTwitter(TwitterDefaults.AuthenticationScheme, options => options.RetrieveUserDetails = true) .WithDynamicOptions<TwitterOptions, TwitterHandler>( TwitterDefaults.AuthenticationScheme, options => { options.WithProperty(x => x.ConsumerKey); options.WithProperty(x => x.ConsumerSecret, isSecret: true); } ); } private void ConfigureLocalizationServices() { Configure<AbpLocalizationOptions>(options => { options.Languages.Add(new LanguageInfo("ar", "ar", "العربية", "ae")); options.Languages.Add(new LanguageInfo("cs", "cs", "Čeština")); options.Languages.Add(new LanguageInfo("en", "en", "English")); options.Languages.Add(new LanguageInfo("en-GB", "en-GB", "English (UK)")); options.Languages.Add(new LanguageInfo("hu", "hu", "Magyar")); options.Languages.Add(new LanguageInfo("fi", "fi", "Finnish", "fi")); options.Languages.Add(new LanguageInfo("fr", "fr", "Français", "fr")); options.Languages.Add(new LanguageInfo("hi", "hi", "Hindi", "in")); options.Languages.Add(new LanguageInfo("it", "it", "Italiano", "it")); options.Languages.Add(new LanguageInfo("pt-BR", "pt-BR", "Português")); options.Languages.Add(new LanguageInfo("ru", "ru", "Русский")); options.Languages.Add(new LanguageInfo("sk", "sk", "Slovak", "sk")); options.Languages.Add(new LanguageInfo("tr", "tr", "Türkçe")); options.Languages.Add(new LanguageInfo("zh-Hans", "zh-Hans", "简体中文")); options.Languages.Add(new LanguageInfo("zh-Hant", "zh-Hant", "繁體中文")); options.Languages.Add(new LanguageInfo("de-DE", "de-DE", "Deutsch", "de")); options.Languages.Add(new LanguageInfo("es", "es", "Español")); }); } ///end added private void ConfigureBlazorise(ServiceConfigurationContext context) { context.Services .AddBootstrap5Providers() .AddFontAwesomeIcons(); } private void ConfigureLeptonTheme() { Configure<LeptonXThemeOptions>(options => { options.Styles.Remove(LeptonXStyleNames.Dark); options.Styles.Remove(LeptonXStyleNames.Light); options.Styles.Remove(LeptonXStyleNames.Dim); options.Styles.Remove(LeptonXStyleNames.System); options.Styles.Add("lightCustom", new LeptonXThemeStyle( LocalizableString.Create<DruidAIResource>("Theme:lightCustom"), "bi bi-sun-fill")); options.Styles.Add("darkCustom", new LeptonXThemeStyle( LocalizableString.Create<DruidAIResource>("Theme:darkCustom"), "bi bi-moon-fill")); options.DefaultStyle = "lightCustom"; //options.DefaultStyle = LeptonXStyleNames.System; }); } private void ConfigureAutoApiControllers() { Configure<AbpAspNetCoreMvcOptions>(options => { options.ConventionalControllers.Create(typeof(DruidAIApplicationModule).Assembly); }); } private void ConfigureAutoMapper() { Configure<AbpAutoMapperOptions>(options => { options.AddMaps<DruidAIBlazorModule>(); }); } public override void OnApplicationInitialization(ApplicationInitializationContext context) { var env = context.GetEnvironment(); var app = context.GetApplicationBuilder(); var configuration = context.GetConfiguration(); if (env.IsDevelopment()) { app.UseDeveloperExceptionPage(); } else { app.UseErrorPage(); app.UseHsts(); } app.UseAbpRequestLocalization();
app.UseHttpsRedirection(); app.UseCorrelationId(); app.UseAbpSecurityHeaders(); app.UseStaticFiles(); app.UseRouting(); app.UseAuthentication(); app.UseJwtTokenMiddleware(); app.UseJwtTokenMiddleware("Default"); //if (bool.Parse(configuration["IdentityServer:IsEnabled"])) //{ // app.UseJwtTokenMiddleware("IdentityBearer"); // app.UseIdentityServer(); //} app.UseIdentityServer(); if (MultiTenancyConsts.IsEnabled) { app.UseMultiTenancy(); } app.UseUnitOfWork(); app.UseAuthorization(); app.UseSwagger(); app.UseAbpSwaggerUI(options => { options.SwaggerEndpoint("/swagger/v1/swagger.json", "DruidAI API"); }); app.UseAuditing(); app.UseAbpSerilogEnrichers(); app.UseConfiguredEndpoints();
} } }
I have not enable IdentityBearer, is that problem? Thank you for your patience
-
0
Sorry, I think it is not supported yet https://docs.abp.io/en/commercial/latest/modules/account/impersonation#blazor-wasm
-
0
I'm afraid yes, Wasm is not supported yet.
-
0
Thank you, I got it
-
0
-
0
I have create simple project but could not get Impersonation works, I share it to you, could you help me to check?
Thank you
-
0
hi
Please send it to email. liming.ma@volosoft.com
-
0
Yes I shared your email or you can get from this link
-
0
-
0
Thank you, in my project it missed OpenId configuration (missing these tables)
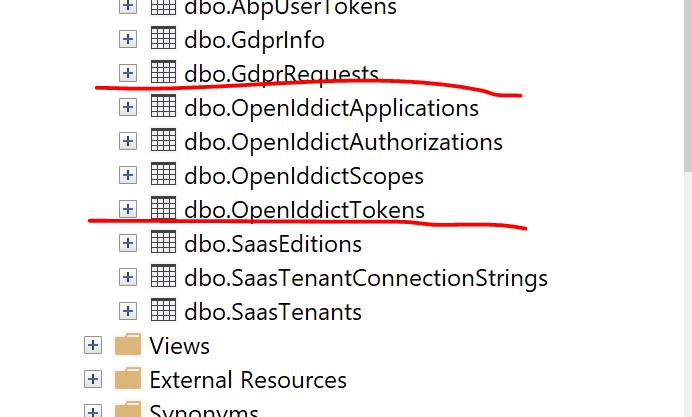
and missing OpenIddictDataSeedContributor class because we upgrade our project from early version.
Do we need to have these all to get impersonation work? Is there any alternative way to get impersonation work without OpenId?