- ABP Framework version: v7.3.0
- UI type: MVC
- DB provider: EF Core
- Tiered (MVC): yes
- Exception message and stack trace:
- Steps to reproduce the issue:"
Issue 1: Login page not showing background svg when deploying on K8s (but show normally when running docker compose on local machine)
On local machine
 On K8s
On K8s

Issue 2: Login with tenant and Login in with this user not work when deploying on K8s (but work normally when running docker compose on local machine) I follow this article: https://docs.abp.io/en/commercial/latest/modules/account/impersonation to enable impersonation feature, but it can only work on local machine.
Issue 3: Authority delegation can't save TenantId (other infor is OK) when running docker compose on local machine without any error logs
I login with a specific tenant and user. I clicked on Authority delegation menu under User menu but nothing happened. I had to go to My account page, and clicked again on Authority delegation menu under User menu. Here, that menu worked and showed Authority delegation popup. I inputted required infor an clicked Save but TenantId couldn't be saved.
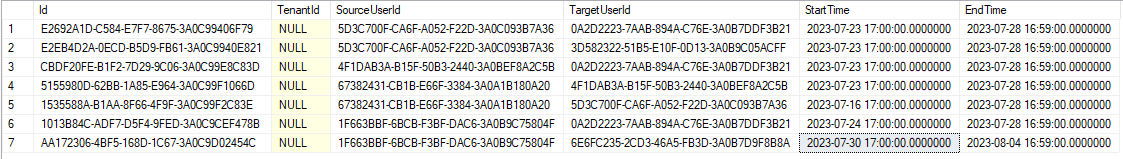
I don't know what I missed. Pls help to check. Thank you.
7 Answer(s)
-
0
hi
1.
You can check it using browser dev tools to see what's happening.
2.
Please check your application logs. You can share it here.
3.
Does it work locally without
docker?dotnet runDo you have steps to reproduce it? -
0
Hi, 1. I found differency on svg data source, but I don't know why. You can see below. On local machine:
data:image/svg+xml,%3Csvg width='2560' height='1600' viewBox='0 0 2560 1600' fill='none' xmlns='http://www.w3.org/2000/svg'%3E%3Cg clip-path='url(%23clip0_4014_34701)'%3E%3Crect width='2560' height='1600' fill='url(%23paint0_linear_4014_34701)'/%3E%3Crect opacity='0.9' width='2560' height='1686' fill='url(%23paint1_linear_4014_34701)'/%3E%3Cg style='mix-blend-mode:overlay'%3E%3Cpath d='M1.74072 1337.63C680.763 1414.42 465.955 401.198 805.448 407.212C1138.23 413.13 796.852 1215.7 1228.1 1168.22C1442.94 1144.58 1155.03 529.083 1432.96 427.322C1806.88 290.432 2008.9 1151.55 2560 338.353' stroke='white' stroke-width='1.25'On K8s
data:image/svg+xml,%3Csvg width='2560' height='1600' viewBox='0 0 2560 1600' fill='none' xmlns='http://www.w3.org/2000/svg'%3E%3Cg clip-path='url(../Themes/LeptonX/Global/side-menu/css/#clip0_4014_34701)'%3E%3Crect%20width='2560'%20height='1600'%20fill='url(../Themes/LeptonX/Global/side-menu/css/#paint0_linear_4014_34701)'/%3E%3Crect%20opacity='0.9'%20width='2560'%20height='1686'%20fill='url(../Themes/LeptonX/Global/side-menu/css/#paint1_linear_4014_34701)'/%3E%3Cg%20style='mix-blend-mode:overlay'%3E%3Cpath%20d='M1.74072%201337.63C680.763%201414.42%20465.955%20401.The url path is different. It's changed automatically.
2. There is no error when I click on Log in with this user menu, it come back to home page
[10:12:09 INF] Request starting HTTP/1.1 GET http://myapp-authserver/connect/authorize?client_id=Web.HelmHttpTesting&redirect_uri=http%3A%2F%2Fmyapp-web%2Fsignin-oidc&response_type=code%20id_token&scope=openid%20profile%20roles%20email%20phone%20AccountService%20IdentityService%20AdministrationService%20SaasService%20CommonService%20CustomerService%20TestService&response_mode=form_post&nonce=638258767295213312.YmJhNjg4NzktMGEyYy00MjE4LThhY2ItMjk4NGM5NjFhZWZmZmZiNGExYmEtNGNkNC00MjFhLTgzMWQtZDJmMGM4NjZhNTVj&access_token=eyJhbGciOiJSUzI1NiIsImtpZCI6IkVBMTg0ODJFQjg0QUNCRjZCRkVCQ0FFMjRCQ0NFNjg0MURBQzVBRTEiLCJ4NXQiOiI2aGhJTHJoS3lfYV82OHJpUzh6bWhCMnNXdUUiLCJ0eXAiOiJhdCtqd3QifQ.eyJzdWIiOiI0ZjFkYWIzYS1iMTVmLTUwYjMtMjQ0MC0zYTBiZWY4YTJjNWIiLCJwcmVmZXJyZWRfdXNlcm5hbWUiOiJuZGFuIiwiZW1haWwiOiJuZGFuQGRldm1oY2JobmkubmV0Iiwicm9sZSI6ImFkbWluIiwidGVuYW50aWQiOiJlZTJiM2YxOS0wZTJlLTAyNWItMjg3OS0zYTBhMWIxODA5N2MiLCJwaG9uZV9udW1iZXJfdmVyaWZpZWQiOiJGYWxzZSIsImVtYWlsX3ZlcmlmaWVkIjoiRmFsc2UiLCJ1bmlxdWVfbmFtZSI6Im5kYW4iLCJvaV9wcnN0IjoiV2ViLkhlbG1IdHRwVGVzdGluZyIsImlzcyI6Imh0dHA6Ly9taGlicy1hdXRoc2VydmVyLyIsIm9pX2F1X2lkIjoiMGQyOGI1MjQtOTU4Ny00ZTQzLWYyMDMtM2EwYmY4M2NiYjcxIiwiY2xpZW50X2lkIjoiV2ViLkhlbG1IdHRwVGVzdGluZyIsIm9pX3Rrbl9pZCI6IjY5ZTEwZjk2LWMxNDMtNmZmZi01NWQ1LTNhMGM5ZWI0ODAwMSIsImF1ZCI6WyJBY2NvdW50U2VydmljZSIsIklkZW50aXR5U2VydmljZSIsIkFkbWluaXN0cmF0aW9uU2VydmljZSIsIlNhYXNTZXJ2aWNlIiwiQ29tbW9uU2VydmljZSIsIkN1c3RvbWVyU2VydmljZSIsIkpGU0FTZXJ2aWNlIiwiR2Jhc2VFVUNEYWlseVNlcnZpY2UiLCJWaXRhbERvd25sb2FkaW5nU2VydmljZSJdLCJzY29wZSI6Im9wZW5pZCBwcm9maWxlIHJvbGVzIGVtYWlsIHBob25lIEFjY291bnRTZXJ2aWNlIElkZW50aXR5U2VydmljZSBBZG1pbmlzdHJhdGlvblNlcnZpY2UgU2Fhc1NlcnZpY2UgQ29tbW9uU2VydmljZSBDdXN0b21lclNlcnZpY2UgSkZTQVNlcnZpY2UgR2Jhc2VFVUNEYWlseVNlcnZpY2UgVml0YWxEb3dubG9hZGluZ1NlcnZpY2UiLCJqdGkiOiJhOTc3OTlhNS0xMWNkLTQzMzMtYjFhMC00MTQ0MzI5MjVhNjMiLCJleHAiOjE2OTAzNjYyNDcsImlhdCI6MTY5MDI3OTg0N30.dqihhdf3eVmCcanCnDjA3RYR6gE0Sun173lvJlQrc-urHNAwbvWCOUZ-sqJZUgxpbWrtlf2ztakP3ddgaYHZl2e3vWgimNnw88vLrlK_eil1eALn2v6LCerKgtlPu96kmpoUc3q-Sh04IczKTKgD0G3_4KXZ8aoTeOa7xO8SkJk5UNwwfnkriaUqk4oXCQuczGuN_TmnPe5rfq-ND3bf0xEp-DlDKbEqi482S3LSX1PGojQl-u831L_NDK64Zt-98cCmFAgh6-KBv_PkAThSFsafil3ggKt7VJbNezDjAzd0xYtI9f7_zeDbrpzA87lpZ7_kqXkO9RCJFw2SWjD_Xg&userid=ba20d69e-c8c9-5284-2040-3a0c9e277061&state=CfDJ8HK8zmwAyDJBimnLTTpa4-dlY45W4YNpdPRq9ImwQvAJEyVjWQCZ6YcsypKSOgUtujVE_coJFn156F6kyOjZrB4e8KGC0-qHg1T-rkYcuApZwf9Xyb1HNlgZ0634vk7IUoWgZ1Bx7uIe22niaIoCohNJfl7-JGjYqnVCoRGc1GJISJHC81oOjDwe9EUSGPkLOeTOYJhxT5iNoddJ0SbyXQ1qpMrbetx0c-TC3dIf6y48rVD2cWbWUJSJSv9v023jCyZMUi2s8HkRO94szR7uwdKTkjKWFCIBpg2eZLkmj1avgSd98qtzcsfBH6OIBGhsYdI_cUMIJroP0b6I1X2R3JrF3zHfY7WnATk-M8CDNOQQxPlrMqHQ6lm073R3nCOOHQ&x-client-SKU=ID_NET6_0&x-client-ver=6.15.1.0 - - [10:12:09 INF] The request URI matched a server endpoint: Authorization. [10:12:09 INF] The authorization request was successfully extracted: { "client_id": "Web.HelmHttpTesting", "redirect_uri": "http://myapp-web/signin-oidc", "response_type": "code id_token", "scope": "openid profile roles email phone AccountService IdentityService AdministrationService SaasService CommonService CustomerService TestService", "response_mode": "form_post", "nonce": "638258767295213312.YmJhNjg4NzktMGEyYy00MjE4LThhY2ItMjk4NGM5NjFhZWZmZmZiNGExYmEtNGNkNC00MjFhLTgzMWQtZDJmMGM4NjZhNTVj", "access_token": "[redacted]", "userid": "ba20d69e-c8c9-5284-2040-3a0c9e277061", "state": "CfDJ8HK8zmwAyDJBimnLTTpa4-dlY45W4YNpdPRq9ImwQvAJEyVjWQCZ6YcsypKSOgUtujVE_coJFn156F6kyOjZrB4e8KGC0-qHg1T-rkYcuApZwf9Xyb1HNlgZ0634vk7IUoWgZ1Bx7uIe22niaIoCohNJfl7-JGjYqnVCoRGc1GJISJHC81oOjDwe9EUSGPkLOeTOYJhxT5iNoddJ0SbyXQ1qpMrbetx0c-TC3dIf6y48rVD2cWbWUJSJSv9v023jCyZMUi2s8HkRO94szR7uwdKTkjKWFCIBpg2eZLkmj1avgSd98qtzcsfBH6OIBGhsYdI_cUMIJroP0b6I1X2R3JrF3zHfY7WnATk-M8CDNOQQxPlrMqHQ6lm073R3nCOOHQ", "x-client-SKU": "ID_NET6_0", "x-client-ver": "6.15.1.0" }. [10:12:09 INF] The authorization request was successfully validated. [10:12:09 INF] Executing endpoint 'Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)' [10:12:09 INF] Route matched with {action = "Handle", controller = "Authorize", area = "", page = ""}. Executing controller action with signature System.Threading.Tasks.Task`1[Microsoft.AspNetCore.Mvc.IActionResult] HandleAsync() on controller Volo.Abp.OpenIddict.Controllers.AuthorizeController (Volo.Abp.OpenIddict.AspNetCore). [10:12:09 INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy [10:12:09 INF] Executing SignInResult with authentication scheme (OpenIddict.Server.AspNetCore) and the following principal: System.Security.Claims.ClaimsPrincipal. [10:12:09 INF] The authorization response was successfully returned to 'http://myapp-web/signin-oidc' using the form post response mode: { "code": "[redacted]", "id_token": "[redacted]", "state": "CfDJ8HK8zmwAyDJBimnLTTpa4-dlY45W4YNpdPRq9ImwQvAJEyVjWQCZ6YcsypKSOgUtujVE_coJFn156F6kyOjZrB4e8KGC0-qHg1T-rkYcuApZwf9Xyb1HNlgZ0634vk7IUoWgZ1Bx7uIe22niaIoCohNJfl7-JGjYqnVCoRGc1GJISJHC81oOjDwe9EUSGPkLOeTOYJhxT5iNoddJ0SbyXQ1qpMrbetx0c-TC3dIf6y48rVD2cWbWUJSJSv9v023jCyZMUi2s8HkRO94szR7uwdKTkjKWFCIBpg2eZLkmj1avgSd98qtzcsfBH6OIBGhsYdI_cUMIJroP0b6I1X2R3JrF3zHfY7WnATk-M8CDNOQQxPlrMqHQ6lm073R3nCOOHQ", "iss": "http://myapp-authserver/" }. [10:12:09 INF] Executed action Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore) in 146.6306ms [10:12:09 INF] Executed endpoint 'Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)' [10:12:09 INF] Request finished HTTP/1.1 GET http://myapp-authserver/connect/authorize?client_id=Web.HelmHttpTesting&redirect_uri=http%3A%2F%2Fmyapp-web%2Fsignin-oidc&response_type=code%20id_token&scope=openid%20profile%20roles%20email%20phone%20AccountService%20IdentityService%20AdministrationService%20SaasService%20CommonService%20CustomerService%20TestService&response_mode=form_post&nonce=638258767295213312.YmJhNjg4NzktMGEyYy00MjE4LThhY2ItMjk4NGM5NjFhZWZmZmZiNGExYmEtNGNkNC00MjFhLTgzMWQtZDJmMGM4NjZhNTVj&access_token=eyJhbGciOiJSUzI1NiIsImtpZCI6IkVBMTg0ODJFQjg0QUNCRjZCRkVCQ0FFMjRCQ0NFNjg0MURBQzVBRTEiLCJ4NXQiOiI2aGhJTHJoS3lfYV82OHJpUzh6bWhCMnNXdUUiLCJ0eXAiOiJhdCtqd3QifQ.eyJzdWIiOiI0ZjFkYWIzYS1iMTVmLTUwYjMtMjQ0MC0zYTBiZWY4YTJjNWIiLCJwcmVmZXJyZWRfdXNlcm5hbWUiOiJuZGFuIiwiZW1haWwiOiJuZGFuQGRldm1oY2JobmkubmV0Iiwicm9sZSI6ImFkbWluIiwidGVuYW50aWQiOiJlZTJiM2YxOS0wZTJlLTAyNWItMjg3OS0zYTBhMWIxODA5N2MiLCJwaG9uZV9udW1iZXJfdmVyaWZpZWQiOiJGYWxzZSIsImVtYWlsX3ZlcmlmaWVkIjoiRmFsc2UiLCJ1bmlxdWVfbmFtZSI6Im5kYW4iLCJvaV9wcnN0IjoiV2ViLkhlbG1IdHRwVGVzdGluZyIsImlzcyI6Imh0dHA6Ly9taGlicy1hdXRoc2VydmVyLyIsIm9pX2F1X2lkIjoiMGQyOGI1MjQtOTU4Ny00ZTQzLWYyMDMtM2EwYmY4M2NiYjcxIiwiY2xpZW50X2lkIjoiV2ViLkhlbG1IdHRwVGVzdGluZyIsIm9pX3Rrbl9pZCI6IjY5ZTEwZjk2LWMxNDMtNmZmZi01NWQ1LTNhMGM5ZWI0ODAwMSIsImF1ZCI6WyJBY2NvdW50U2VydmljZSIsIklkZW50aXR5U2VydmljZSIsIkFkbWluaXN0cmF0aW9uU2VydmljZSIsIlNhYXNTZXJ2aWNlIiwiQ29tbW9uU2VydmljZSIsIkN1c3RvbWVyU2VydmljZSIsIkpGU0FTZXJ2aWNlIiwiR2Jhc2VFVUNEYWlseVNlcnZpY2UiLCJWaXRhbERvd25sb2FkaW5nU2VydmljZSJdLCJzY29wZSI6Im9wZW5pZCBwcm9maWxlIHJvbGVzIGVtYWlsIHBob25lIEFjY291bnRTZXJ2aWNlIElkZW50aXR5U2VydmljZSBBZG1pbmlzdHJhdGlvblNlcnZpY2UgU2Fhc1NlcnZpY2UgQ29tbW9uU2VydmljZSBDdXN0b21lclNlcnZpY2UgSkZTQVNlcnZpY2UgR2Jhc2VFVUNEYWlseVNlcnZpY2UgVml0YWxEb3dubG9hZGluZ1NlcnZpY2UiLCJqdGkiOiJhOTc3OTlhNS0xMWNkLTQzMzMtYjFhMC00MTQ0MzI5MjVhNjMiLCJleHAiOjE2OTAzNjYyNDcsImlhdCI6MTY5MDI3OTg0N30.dqihhdf3eVmCcanCnDjA3RYR6gE0Sun173lvJlQrc-urHNAwbvWCOUZ-sqJZUgxpbWrtlf2ztakP3ddgaYHZl2e3vWgimNnw88vLrlK_eil1eALn2v6LCerKgtlPu96kmpoUc3q-Sh04IczKTKgD0G3_4KXZ8aoTeOa7xO8SkJk5UNwwfnkriaUqk4oXCQuczGuN_TmnPe5rfq-ND3bf0xEp-DlDKbEqi482S3LSX1PGojQl-u831L_NDK64Zt-98cCmFAgh6-KBv_PkAThSFsafil3ggKt7VJbNezDjAzd0xYtI9f7_zeDbrpzA87lpZ7_kqXkO9RCJFw2SWjD_Xg&userid=ba20d69e-c8c9-5284-2040-3a0c9e277061&state=CfDJ8HK8zmwAyDJBimnLTTpa4-dlY45W4YNpdPRq9ImwQvAJEyVjWQCZ6YcsypKSOgUtujVE_coJFn156F6kyOjZrB4e8KGC0-qHg1T-rkYcuApZwf9Xyb1HNlgZ0634vk7IUoWgZ1Bx7uIe22niaIoCohNJfl7-JGjYqnVCoRGc1GJISJHC81oOjDwe9EUSGPkLOeTOYJhxT5iNoddJ0SbyXQ1qpMrbetx0c-TC3dIf6y48rVD2cWbWUJSJSv9v023jCyZMUi2s8HkRO94szR7uwdKTkjKWFCIBpg2eZLkmj1avgSd98qtzcsfBH6OIBGhsYdI_cUMIJroP0b6I1X2R3JrF3zHfY7WnATk-M8CDNOQQxPlrMqHQ6lm073R3nCOOHQ&x-client-SKU=ID_NET6_0&x-client-ver=6.15.1.0 - - - 200 2160 text/html;charset=UTF-8 239.4523ms [10:12:09 INF] Request starting HTTP/1.1 POST http://myapp-authserver/connect/token application/x-www-form-urlencoded 182 [10:12:09 INF] The request URI matched a server endpoint: Token. [10:12:09 INF] The token request was successfully extracted: { "client_id": "Web.HelmHttpTesting", "client_secret": "[redacted]", "code": "[redacted]", "grant_type": "authorization_code", "redirect_uri": "http://myapp-web/signin-oidc" }. [10:12:09 INF] The token request was successfully validated. [10:12:09 INF] Executing endpoint 'Volo.Abp.OpenIddict.Controllers.TokenController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)' [10:12:09 INF] Route matched with {action = "Handle", controller = "Token", area = "", page = ""}. Executing controller action with signature System.Threading.Tasks.Task`1[Microsoft.AspNetCore.Mvc.IActionResult] HandleAsync() on controller Volo.Abp.OpenIddict.Controllers.TokenController (Volo.Abp.OpenIddict.AspNetCore). [10:12:09 INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy [10:12:09 INF] Executing SignInResult with authentication scheme (OpenIddict.Server.AspNetCore) and the following principal: System.Security.Claims.ClaimsPrincipal. [10:12:09 INF] The token '960d5798-e9b5-f264-f0e8-3a0c9eb5bf71' was successfully marked as redeemed. [10:12:09 INF] The response was successfully returned as a JSON document: { "access_token": "[redacted]", "token_type": "Bearer", "expires_in": 86399, "scope": "openid profile roles email phone AccountService IdentityService AdministrationService SaasService CommonService CustomerService TestService", "id_token": "[redacted]" }. [10:12:09 INF] Executed action Volo.Abp.OpenIddict.Controllers.TokenController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore) in 65.6186ms [10:12:09 INF] Executed endpoint 'Volo.Abp.OpenIddict.Controllers.TokenController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)' [10:12:09 INF] Request finished HTTP/1.1 POST http://myapp-authserver/connect/token application/x-www-form-urlencoded 182 - 200 3248 application/json;charset=UTF-8 114.1058ms [10:12:09 INF] Request starting HTTP/1.1 GET http://myapp-authserver/connect/userinfo - - [10:12:09 INF] The request URI matched a server endpoint: Userinfo. [10:12:09 INF] The userinfo request was successfully extracted: { "access_token": "[redacted]" }. [10:12:09 INF] The userinfo request was successfully validated. [10:12:09 INF] Executing endpoint 'Volo.Abp.OpenIddict.Controllers.UserInfoController.Userinfo (Volo.Abp.OpenIddict.AspNetCore)' [10:12:09 INF] Route matched with {action = "Userinfo", controller = "UserInfo", area = "", page = ""}. Executing controller action with signature System.Threading.Tasks.Task`1[Microsoft.AspNetCore.Mvc.IActionResult] Userinfo() on controller Volo.Abp.OpenIddict.Controllers.UserInfoController (Volo.Abp.OpenIddict.AspNetCore). [10:12:09 INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy [10:12:09 INF] Executing OkObjectResult, writing value of type 'System.Collections.Generic.Dictionary`2[[System.String, System.Private.CoreLib, Version=7.0.0.0, Culture=neutral, PublicKeyToken=7cec85d7bea7798e],[System.Object, System.Private.CoreLib, Version=7.0.0.0, Culture=neutral, PublicKeyToken=7cec85d7bea7798e]]'. [10:12:09 INF] Executed action Volo.Abp.OpenIddict.Controllers.UserInfoController.Userinfo (Volo.Abp.OpenIddict.AspNetCore) in 25.3332ms [10:12:09 INF] Executed endpoint 'Volo.Abp.OpenIddict.Controllers.UserInfoController.Userinfo (Volo.Abp.OpenIddict.AspNetCore)' [10:12:09 INF] Request finished HTTP/1.1 GET http://myapp-authserver/connect/userinfo - - - 200 - application/json;+charset=utf-8 42.7677ms [10:12:10 INF] Request starting HTTP/1.1 GET http://myapp-authserver/api/account/profile-picture-file/4f1dab3a-b15f-50b3-2440-3a0bef8a2c5b?api-version=1.0 - - [10:12:10 INF] Executing endpoint 'Volo.Abp.Account.AccountController.GetProfilePictureFileAsync (Volo.Abp.Account.Pro.Public.HttpApi)' [10:12:10 INF] Route matched with {area = "account", action = "GetProfilePictureFile", controller = "Account", page = ""}. Executing controller action with signature System.Threading.Tasks.Task`1[Volo.Abp.Content.IRemoteStreamContent] GetProfilePictureFileAsync(System.Guid) on controller Volo.Abp.Account.AccountController (Volo.Abp.Account.Pro.Public.HttpApi). [10:12:10 INF] Executing ObjectResult, writing value of type 'Volo.Abp.Content.RemoteStreamContent'. [10:12:10 INF] Executed action Volo.Abp.Account.AccountController.GetProfilePictureFileAsync (Volo.Abp.Account.Pro.Public.HttpApi) in 38.0525ms [10:12:10 INF] Executed endpoint 'Volo.Abp.Account.AccountController.GetProfilePictureFileAsync (Volo.Abp.Account.Pro.Public.HttpApi)' [10:12:10 INF] Request finished HTTP/1.1 GET http://myapp-authserver/api/account/profile-picture-file/4f1dab3a-b15f-50b3-2440-3a0bef8a2c5b?api-version=1.0 - - - 200 230348 image/jpeg 45.8526ms -
0
- I found differency on svg data source, but I don't know why. You can see below.
Can you share a website so I can check it online?
2
Can you share
logs.txtof all apps? -
0
Hi,
Sorry, because of our policy, there is no way to check online. Do you have any suggestion why url path was changed? I will check based on your suggestions?
-
0
Can you reproduce this in a new template project? also, share your k8s configuration.
We will try it in the local environment.
-
0
Hi,
I saved as the svg into a .svg file and use global css to override the rule and it works. I guest this issue related to bundling process because I tried to copy Themes folder of your LeptonX source code to my AuthServer project and modify layout-bundle.css but no luck, all my changes didn't be reflected when deploying on K8s.
Issue 2 & 3 are not important with me at this moment. If I have time, I will try again.
-
0
hi
You can run
abp install-libsto install the front assets.



