In Abp MicroSerivce projects, if an API call triggered by UI to MicroService A Method1, and Method1 call Method2 in MicroService B. In Method2, if access CurrentTenant property, would it get the same value in Method1? This is the TenantId, CurrentUser penetrate issue across micro-services.
Thanks
- ABP Framework version: v7.3.2
- UI Type: Angular / MVC / Blazor WASM / Blazor Server
- Database System: EF Core (SQL Server, Oracle, MySQL, PostgreSQL, etc..) / MongoDB
- Tiered (for MVC) or Auth Server Separated (for Angular): yes/no
- Exception message and full stack trace:
- Steps to reproduce the issue:
6 Answer(s)
-
0
-
0
if access CurrentTenant property, would it get the same value in Method1
I think that's fine, ABP will add the current tenant parameters when sending an internal request
-
0
if access CurrentTenant property, would it get the same value in Method1
I think that's fine, ABP will add the current tenant parameters when sending an internal request
Tenant Id currently is in Request header or in access token? I believe UserId are in access token.
-
0
Hi,
Tenant Id is in Request header.
I believe UserId are in access token.
https://support.abp.io/QA/Questions/6765/CurrentTenant-across-MicroService#answer-3a1109b6-885c-2f65-240c-f25e8d5cd039
-
0
This is a temporary solution, it should be able to pass the current user's credentials
You can try override the
HttpContextAbpAccessTokenProvider[Dependency(ReplaceServices = true)] [ExposeServices(typeof(HttpContextAbpAccessTokenProvider), typeof(IAbpAccessTokenProvider))] public class MyHttpContextAbpAccessTokenProvider : HttpContextAbpAccessTokenProvider { ... public virtual async Task<string?> GetTokenAsync() { var httpContext = HttpContextAccessor?.HttpContext; if (httpContext == null) { return null; } var token = await httpContext.GetTokenAsync("access_token"); if (token != null) { return token; } token = httpContext.Request.Headers["Authorization"]; if (!token.IsNullOrWhiteSpace() && token.Contains("Bearer ")) { return token.Replace("Bearer ", ""); } return null; } } -
0
We have an internal issue with this, may be available in next version
We decided to cancel this because of the following reasons
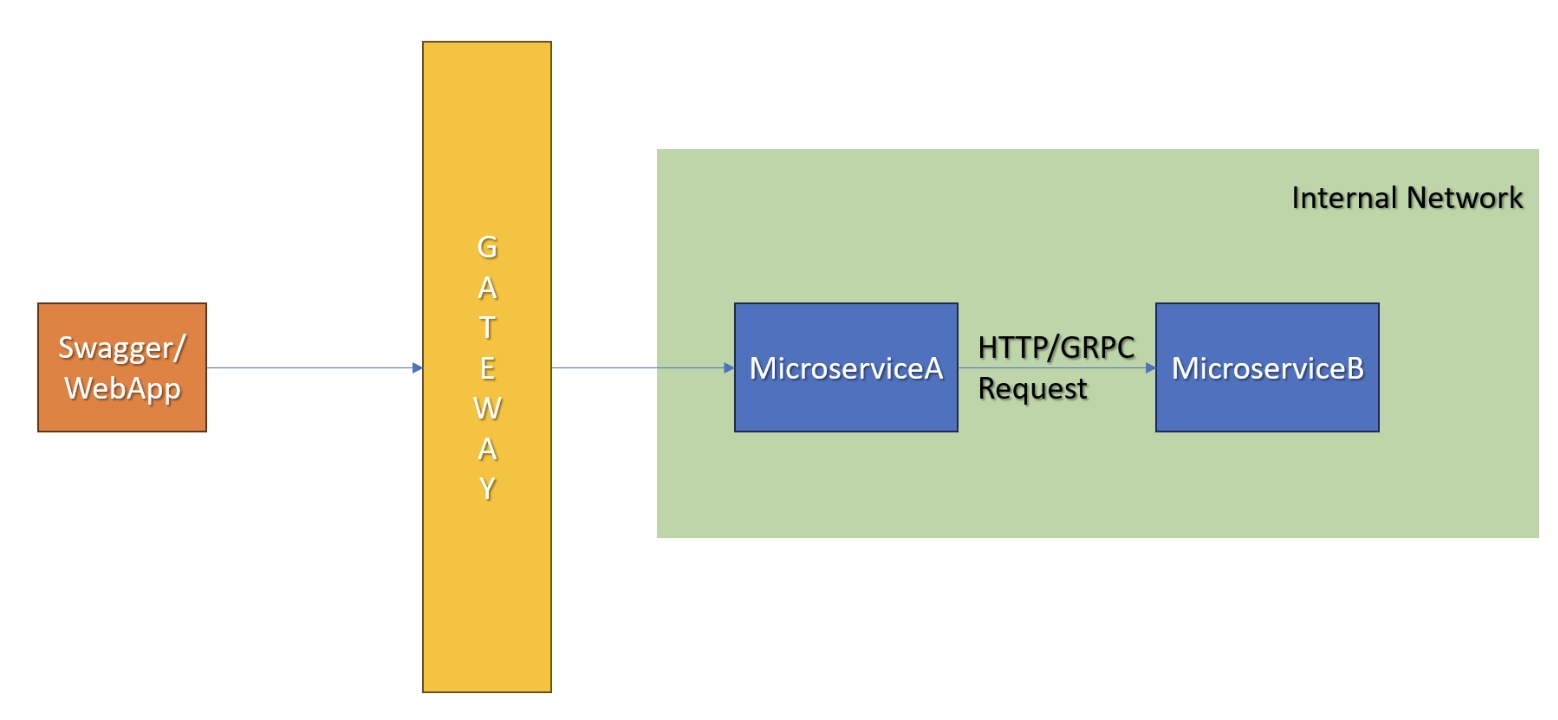
This is a request flow as you mentioned:
Assuming WebApp/SwaggerUI is authenticated and got an access_token and making a request to an endpoint at gateway that automatically redirects to the related microservice (MicroserviceA). In this request, MicroserviceA makes a request to the MicroserviceB using HttpApi.Client and client proxy (or gRPC).
The problem:
- The request is done by a user, since it is coming from Web; it is either Hybrid flow or AuthorizationCode flow. What if the user with the permission to make a request to MicroserviceA doesn't have permission for the MicroserviceB? If you grant permission to user (or role the user has), it will cause different problems on the UI.
Microservice terminology:
Apart from my explanation to this specific approach, the request flow we are discussing is not Synchronous Communication between Microservices
This is the synchronous communication between microservices:
No UI, no user information; two servers talking to each other.
We assume, think or design that microservice with authorization. The oidc standarts for this kind interactions should use client_credentials flow. We have related ABP packages to make it easy to use (Abp.IdentityModel) for it. The problem with authorization is Client_Credentials permission type was in the IdentityServer package which shouldn't be specific to IdentityServer. Client_Credentials is valid for all OIDC providers, so we can simply add it to OpenIddict aswell and keep using it.
Why do we need
access_tokenin the first place?Since the synchronous communication between microservices happens in an internal network and moreover, the microservice-to-microservice request maybe slightly or completely different from a UI request; it is better to use Integration Services without caring about authentication. It will be created for the only purpose to server internal requests.