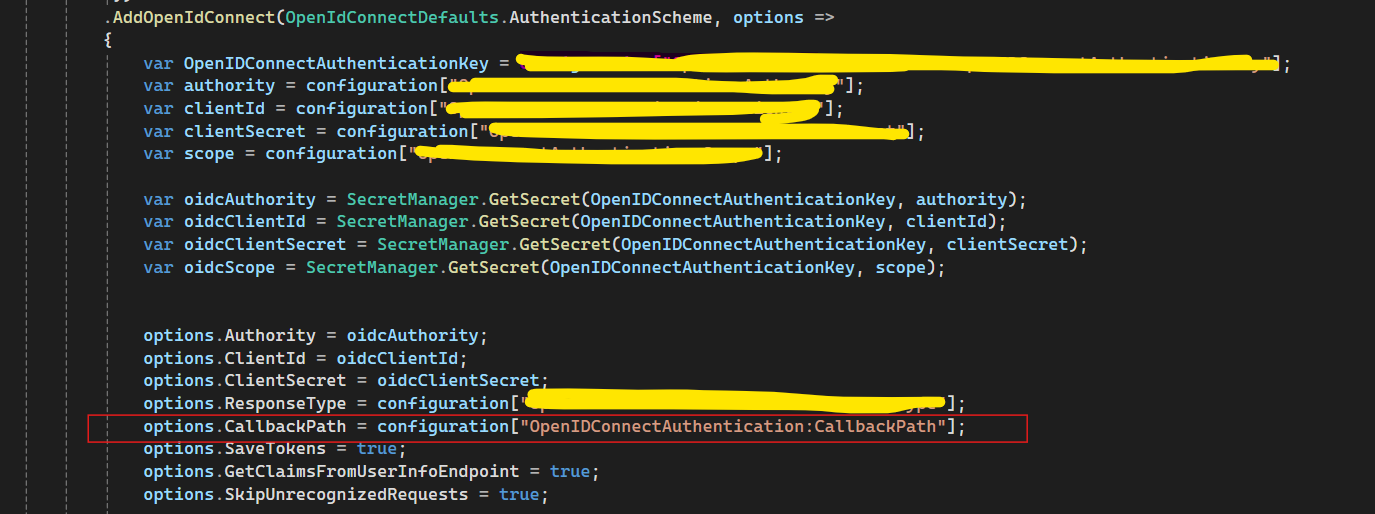
- ABP Framework version: 7.4.2
- UI Type: Angular
- Database System: EF Core (PostgreSQL)
- Tiered (for MVC) or Auth Server Separated (for Angular): yes
Subject :- SSO OIDC integration issue
Exception details :- In our microservices architecture, we handle internal API calls using HTTP, while external applications access our APIs over HTTPS. However, when setting up the callback URL, it automatically picks up the internal domain with HTTP, leading to issues when using HTTPS.
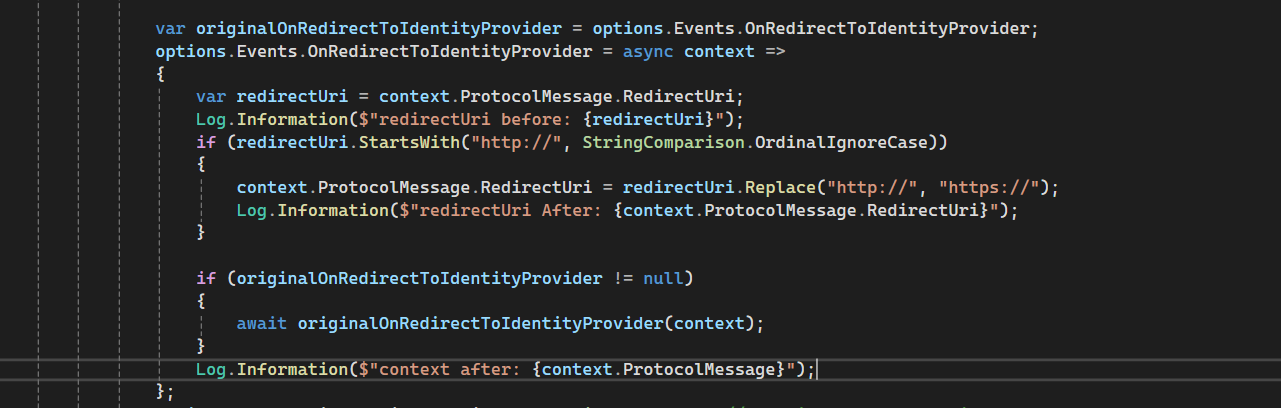
To address this, I added the following code to modify the redirect URI:
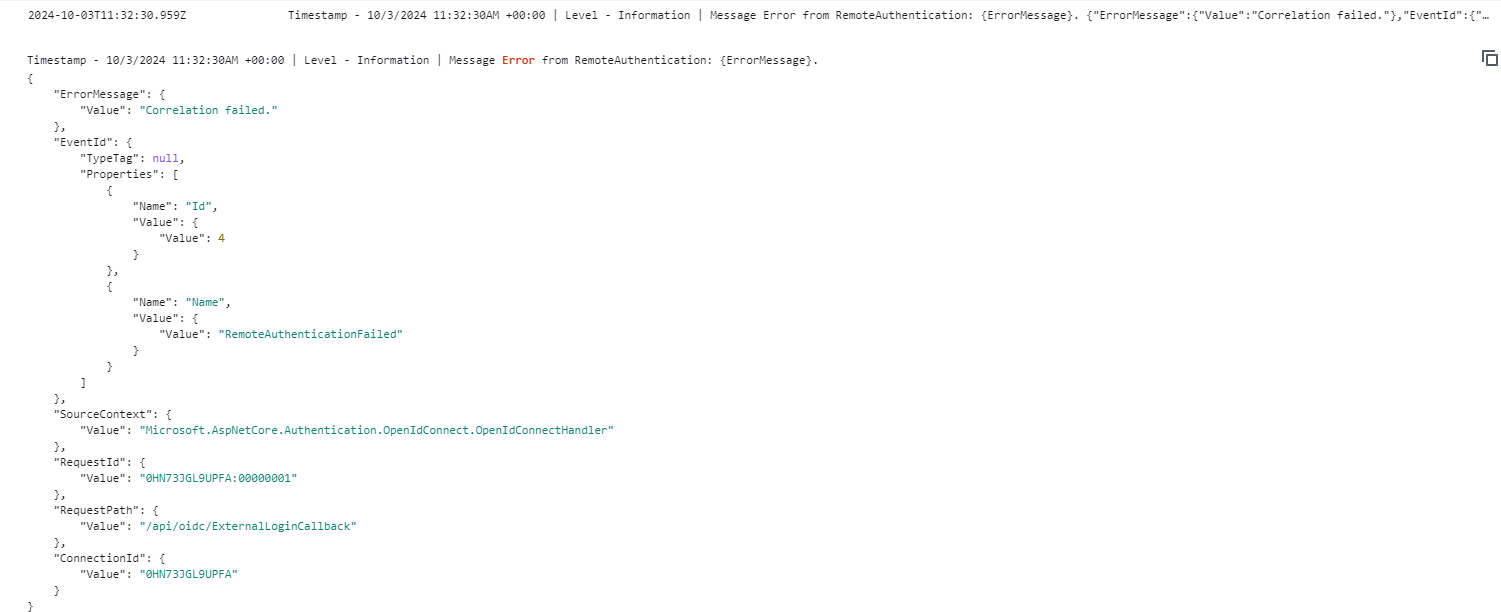
 After implementing this change, I started facing the "Correlation failed" error in the remote authentication process. I’ve applied some additional fixes to resolve this issue.
After implementing this change, I started facing the "Correlation failed" error in the remote authentication process. I’ve applied some additional fixes to resolve this issue.
I am currently facing an issue in my application, and I would greatly appreciate your assistance in resolving it.
27 Answer(s)
-
0
Any update ?
-
0
hi
However, when setting up the callback URL, it automatically picks up the internal domain with HTTP, leading to issues when using HTTPS.
What's the issue?
-
0
facing "Correlation failed" issue after redirect URL from SSO OpenID connect.
-
0
hi
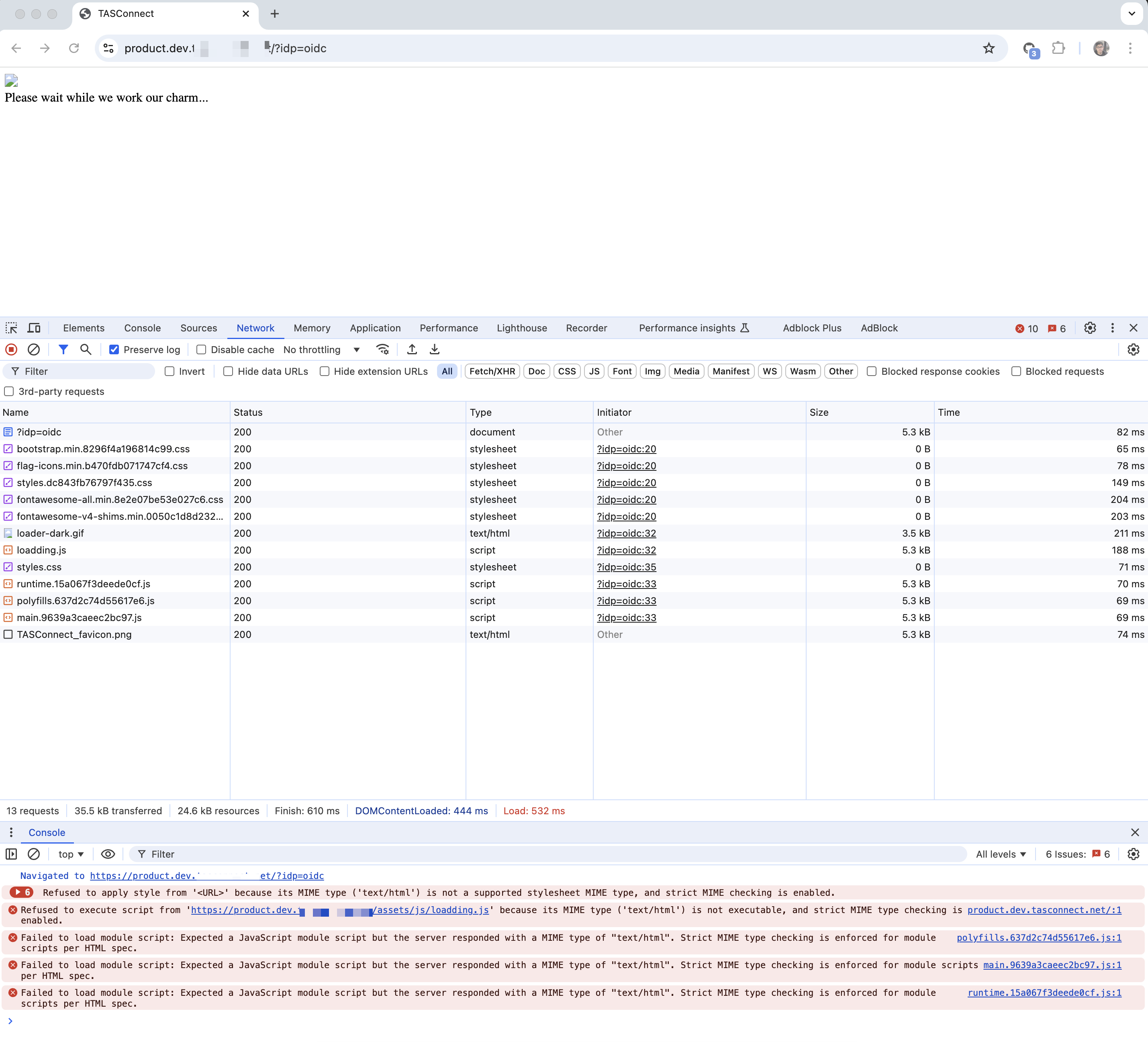
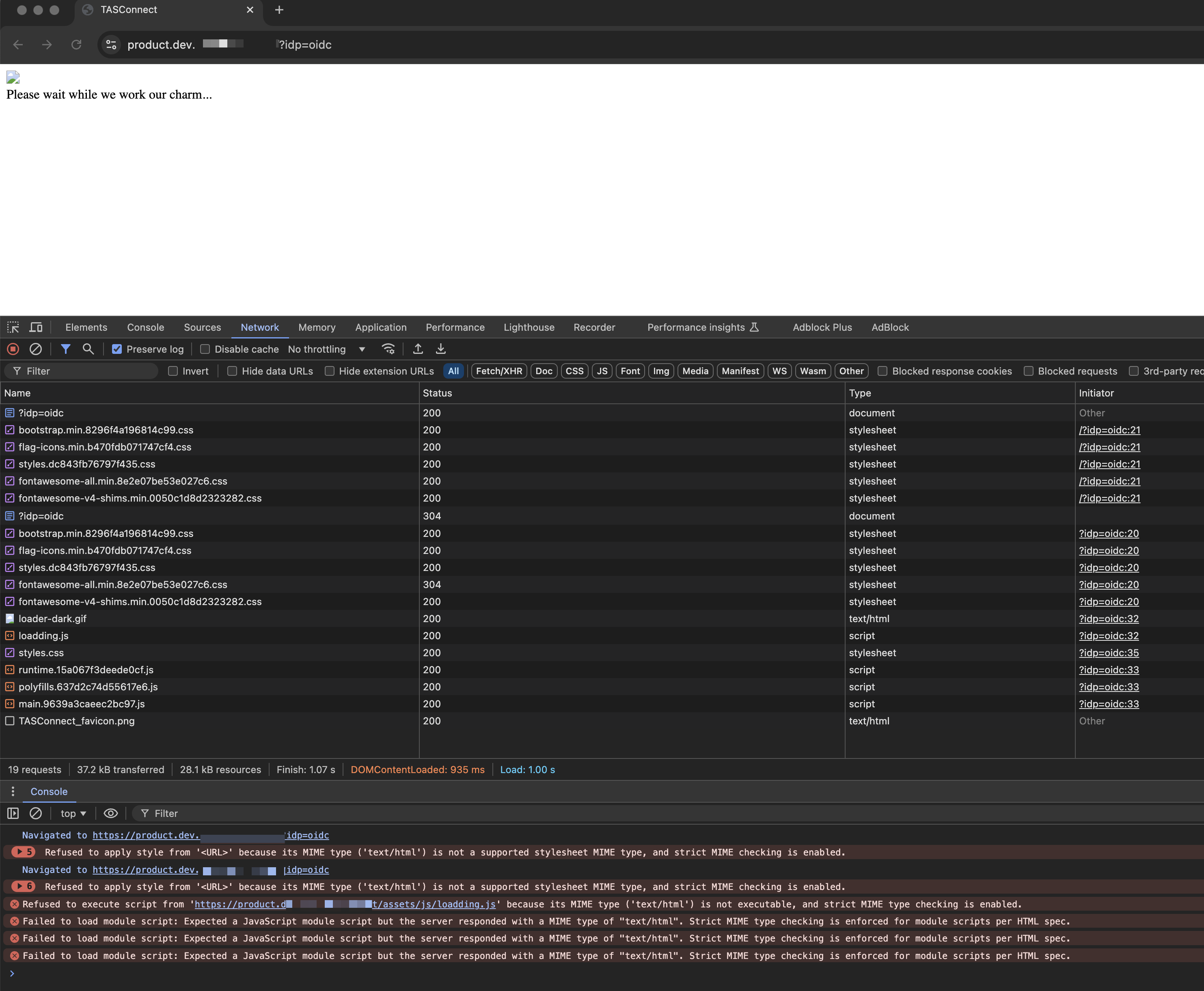
Can you share some screenshots and exception logs with https?
What I mean is you should not change https, maybe there are other solutions.
Thanks.
-
0
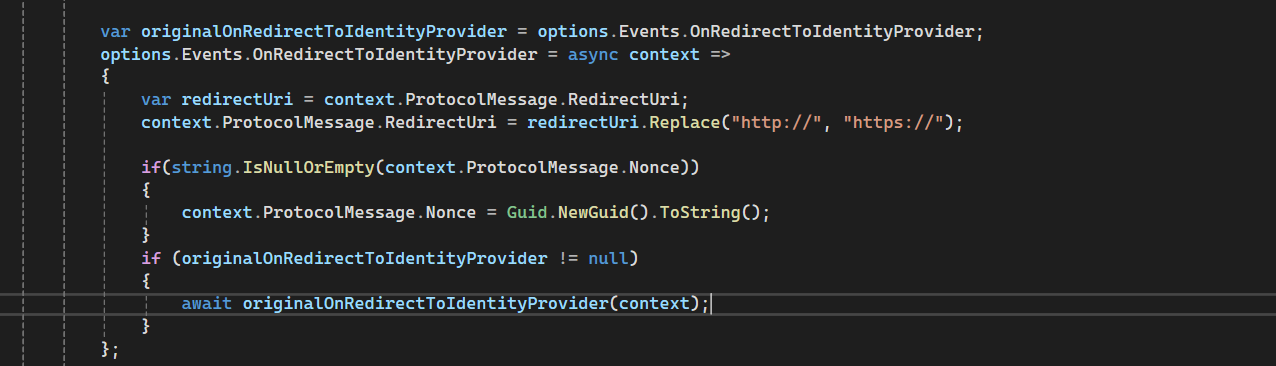
If I don't add the code below, it shows 'Connection Not Secure'., var originalOnRedirectToIdentityProvider = options.Events.OnRedirectToIdentityProvider; options.Events.OnRedirectToIdentityProvider = async context => { var redirectUri = context.ProtocolMessage.RedirectUri; Log.Information($"redirectUri 1: {context.ProtocolMessage.RedirectUri}"); context.ProtocolMessage.RedirectUri = redirectUri.Replace("http://", "https://"); Log.Information($"redirectUri 2: {context.ProtocolMessage.RedirectUri}"); if (string.IsNullOrEmpty(context.ProtocolMessage.Nonce)) { context.ProtocolMessage.Nonce = Guid.NewGuid().ToString(); } if (originalOnRedirectToIdentityProvider != null) { await originalOnRedirectToIdentityProvider(context); } };
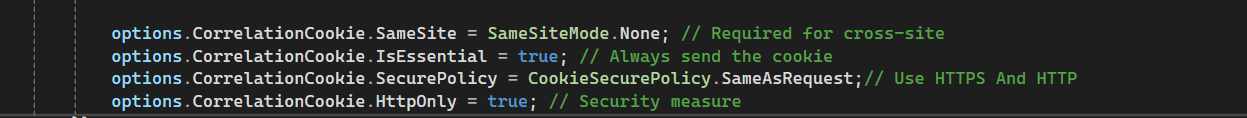
options.CorrelationCookie.SameSite = SameSiteMode.None; // Required for cross-site options.CorrelationCookie.IsEssential = true; // Always send the cookie options.CorrelationCookie.SecurePolicy = CookieSecurePolicy.SameAsRequest;// Use HTTPS And HTTP options.CorrelationCookie.HttpOnly = true; // Security measureIf I remove the above code, how should I handle the scenario? Could you please assist me?
Scenario Description :- In our environment, we have a set of microservices running within Docker containers (or Kubernetes), and these microservices communicate with each other over HTTP internally for performance and simplicity reasons. However, for external communication, specifically for handling OpenID Connect (OIDC) authentication callbacks, we need to ensure that HTTPS is used for secure communication, as these external calls require the use of HTTPS (e.g., OIDC authentication or third-party service integrations).
I have included a reference link for your consideration, as I was facing the same issue described there. https://github.com/dotnet/aspnetcore/issues/16924
-
0
ok, the
Correlation failedshould be the cookies problem. https://github.com/dotnet/aspnetcore/blob/release/9.0-rc1/src/Security/Authentication/Core/src/RemoteAuthenticationHandler.cs#L248-L280Please check the browser network/console panel to see the warning.
If you can share a online URL. I can check it.
-
0
can you please share your email id, I can share one-to-one with you.
-
0
liming.ma@volosoft.com
-
0
details have been shared over email, please check.
-
0
-
0
deployment is in progress. I will ping you once it done.
-
0
ok
-
0
pls check
-
0
-
0
-
0
pls remove above code from chat ; details screen shot have been shared over email, please check.
-
0
ok
-
0
Sorry for late reply, I just send logs over email please find.
-
0
hi
The problem is
Message '{CorrelationCookieName}' cookie not found.The cookie '{name}' has set 'SameSite=None' and must also set 'Secure'.by the way, You can check this article https://abp.io/community/articles/patch-for-chrome-login-issue-identityserver4-samesite-cookie-problem-weypwp3n
-
0
Thanks for update, let me try and get back to you.
-
0
: )
-
0
Hi,
I wanted to inform you that our microservices are running inside a container and communicate via HTTP. However, the callback URL we provide is formatted as follows:
options.CallbackPath = "/api/oidc/ExternalLoginCallback"
The domain name is automatically picked from the schema settings, resulting in the URL being:
http://{domain}/api/oidc/ExternalLoginCallback
However, the identity provider (IDP) expects the URL to be HTTPS:
https://{domain}/api/oidc/ExternalLoginCallback
Since our microservices are running on HTTP, the schema configuration defaults to the HTTP endpoint. If I forcefully replace HTTP with HTTPS, I encounter a "Correlation failed" error.
You provided a solution, and I would like to know if that will resolve this error, or if we need to implement additional solutions, such as configuring middleware to accept both HTTP and HTTPS requests.
Thank you!
-
0
I am not very familiar with Kubernetes, if the application in the container can use HTTPS, then all the problems will be solved.
https://learn.microsoft.com/en-us/aspnet/core/security/docker-https?view=aspnetcore-8.0
-
0
hi
The problem is
Message '{CorrelationCookieName}' cookie not found.The cookie '{name}' has set 'SameSite=None' and must also set 'Secure'.by the way, You can check this article https://abp.io/community/articles/patch-for-chrome-login-issue-identityserver4-samesite-cookie-problem-weypwp3n
Hi maliming,
The issue has been resolved; thank you!
-
0
hi
Can you share your solution?