- ABP Framework version: v8.3.4
- UI Type: Blazor Server
- Database System: EF Core (SQL Server)
- Tiered (for MVC) or Auth Server Separated (for Angular): no
- Exception message and full stack trace:
* System.InvalidOperationException: An invalid request URI was provided. Either the request URI must be an absolute URI or BaseAddress must be set.
at System.Net.Http.HttpClient.PrepareRequestMessage(HttpRequestMessage request)
at System.Net.Http.HttpClient.SendAsync(HttpRequestMessage request, HttpCompletionOption completionOption, CancellationToken cancellationToken)
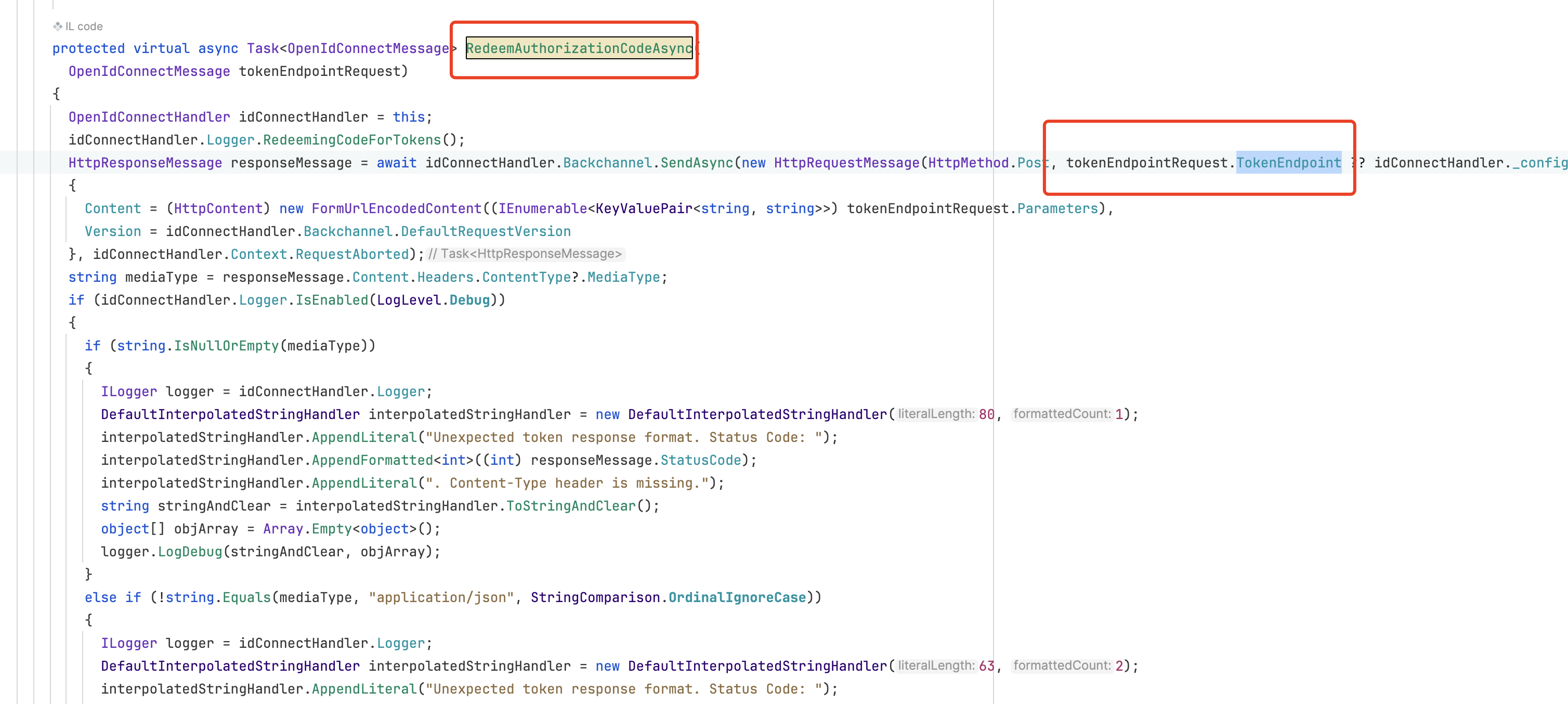
at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.RedeemAuthorizationCodeAsync(OpenIdConnectMessage tokenEndpointRequest)
at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.HandleRemoteAuthenticateAsync()
* Microsoft.AspNetCore.Authentication.AuthenticationFailureException: An error was encountered while handling the remote login.
---> System.InvalidOperationException: An invalid request URI was provided. Either the request URI must be an absolute URI or BaseAddress must be set.
at System.Net.Http.HttpClient.PrepareRequestMessage(HttpRequestMessage request)
at System.Net.Http.HttpClient.SendAsync(HttpRequestMessage request, HttpCompletionOption completionOption, CancellationToken cancellationToken)
at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.RedeemAuthorizationCodeAsync(OpenIdConnectMessage tokenEndpointRequest)
at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.HandleRemoteAuthenticateAsync()
--- End of inner exception stack trace ---
at Microsoft.AspNetCore.Authentication.RemoteAuthenticationHandler`1.HandleRequestAsync()
at Volo.Abp.Account.Public.Web.ExternalProviders.AbpAccountAuthenticationRequestHandler`2.HandleRequestAsync()
at Microsoft.AspNetCore.Authentication.AuthenticationMiddleware.Invoke(HttpContext context)
at Volo.Abp.AspNetCore.Security.AbpSecurityHeadersMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.InterfaceMiddlewareBinder.<>c__DisplayClass2_0.<<CreateMiddleware>b__0>d.MoveNext()
--- End of stack trace from previous location ---
at Volo.Abp.AspNetCore.Tracing.AbpCorrelationIdMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.InterfaceMiddlewareBinder.<>c__DisplayClass2_0.<<CreateMiddleware>b__0>d.MoveNext()
--- End of stack trace from previous location ---
at Microsoft.AspNetCore.Localization.RequestLocalizationMiddleware.Invoke(HttpContext context)
at Microsoft.AspNetCore.RequestLocalization.AbpRequestLocalizationMiddleware.InvokeAsync(HttpContext context, RequestDelegate next)
at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.InterfaceMiddlewareBinder.<>c__DisplayClass2_0.<<CreateMiddleware>b__0>d.MoveNext()
--- End of stack trace from previous location ---
at Microsoft.AspNetCore.Diagnostics.DeveloperExceptionPageMiddlewareImpl.Invoke(HttpContext context)
* **Steps to reproduce the issue**:
* Setup Azure AD connection
.AddOpenIdConnect("AzureOpenId", "Azure AD", options =>
{
options.ResponseType = OpenIdConnectResponseType.CodeIdToken;
options.RequireHttpsMetadata = false;
options.SaveTokens = false;
options.GetClaimsFromUserInfoEndpoint = false;
options.Scope.Add("email");
options.ClaimActions.MapJsonKey(ClaimTypes.NameIdentifier, "sub");
options.SignInScheme = IdentityConstants.ExternalScheme;
options.CallbackPath = "/callback";
options.TokenValidationParameters = new TokenValidationParameters
{
ValidateIssuer = false,
ValidateAudience = false,
// NameClaimType = "name",
ValidateIssuerSigningKey = false,
RequireSignedTokens = false,
SignatureValidator = delegate (string token, TokenValidationParameters parameters)
{
var jwt = new JsonWebToken(token);
return jwt;
}
};
})
.WithDynamicOptions<OpenIdConnectOptions, OpenIdConnectHandler>(
"AzureOpenId",
options =>
{
options.WithProperty(x => x.Authority);
options.WithProperty(x => x.ClientId);
options.WithProperty(x => x.ClientSecret, isSecret: true);
}
Exception occur after login and came back to Call back.
9 Answer(s)
-
0
at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.RedeemAuthorizationCodeAsync(OpenIdConnectMessage tokenEndpointRequest
I think this is a problem with your openid server, the TokenEndpoint is not a valid URL
could you provide a test project and credentials with me? I will check it. shiwei.liang@volosoft.com
-
0
What do you mean by "OpenID server" ? is it AUTH server or the Azure AD.
if Azure AD,. Azure AD configuration is correct and it has come to the callback correctly.
if Auth Server, we don't have separate Auth server. it is built in to blazer project. How do we configure TokenEndpoint in the project ?
We can give the sample project but Azure AD is belong to our customer and it is only allow inside Norway. And also it is enable multifactor authentication.
Do you have running sample with Azure AD ?
-
0
We have an article
https://abp.io/community/articles/how-to-setup-azure-active-directory-and-integrate-abp-angular-application-lyk87w5l
We can give the sample project but Azure AD is belong to our customer and it is only allow inside Norway. And also it is enable multifactor authentication.
sure, my email is shiwei.liang@volosoft.com
-
0
We already gone through this article and configured the system. But it is not explain about the exception.
I have emailed you a sample code. please configure your Azure AD setting in Administration Setting page. We have tested with our client credentials and we can't give those to you.
Regards, Wasantha.
-
0
-
0
https://drive.google.com/file/d/1_2IbW14is23。。。
please download it from here
-
0
Hi,
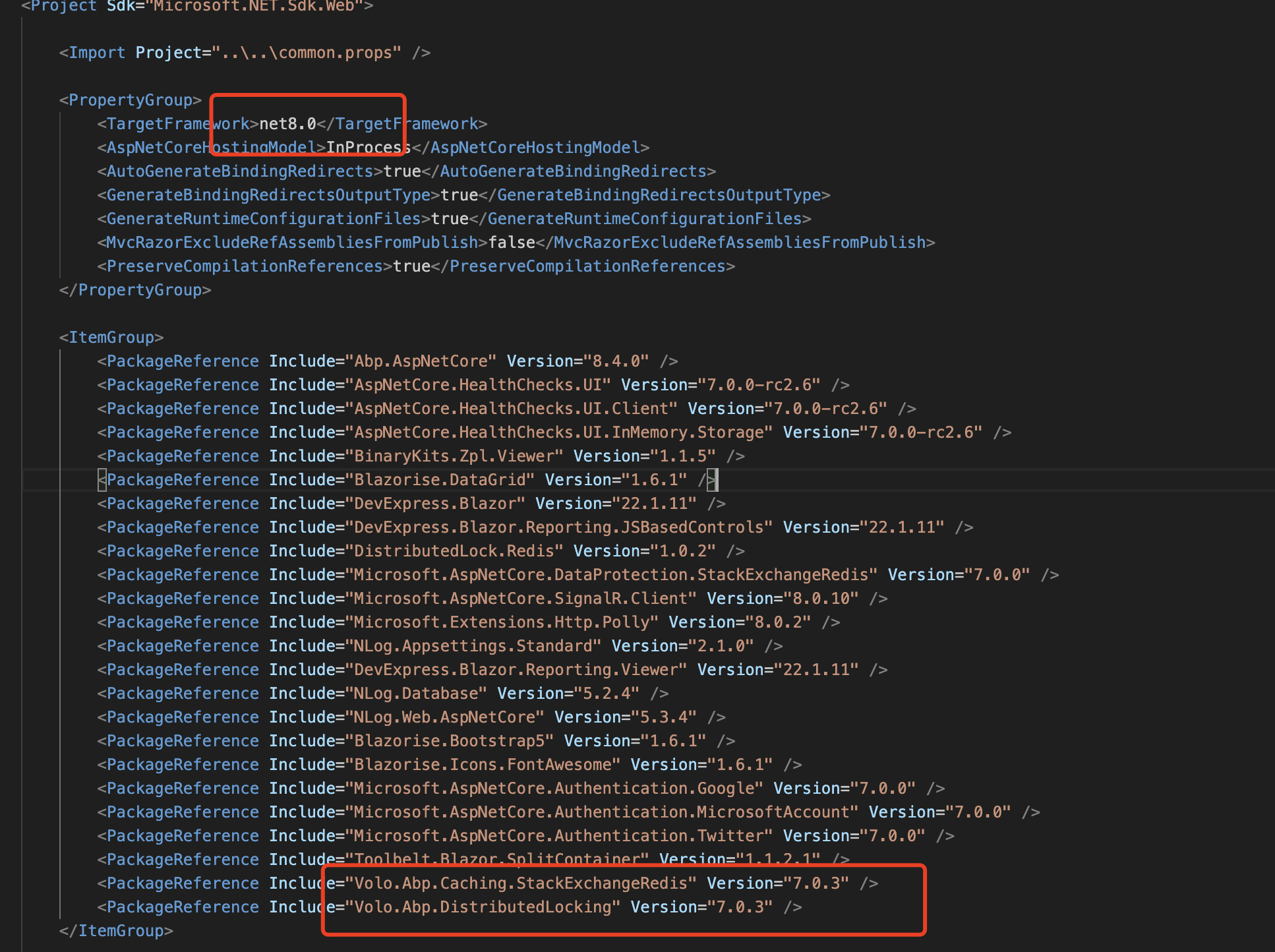
You can try to add those packages to Blazor project.
<PackageReference Include="Microsoft.AspNetCore.Authentication.OpenIdConnect" Version="7.4.0" /> <PackageReference Include="Microsoft.IdentityModel.Tokens" Version="7.4.0" /> <PackageReference Include="Microsoft.IdentityModel.Protocols.OpenIdConnect" Version="7.4.0" /> -
0
I have done this. But still getting the same issue.
-
0