Here is the code. The project references the API that is housed on Azure App Services which is why the cert issuer is from Azure.
using IdentityModel;
using IdentityModel.OidcClient;
using Microsoft.Extensions.Configuration;
using Microsoft.Extensions.Options;
using MyProject.Localization;
using MyProject.Maui.Oidc;
using Volo.Abp.Account.Localization;
using Volo.Abp.Autofac;
using Volo.Abp.Http.Client;
using Volo.Abp.Http.Client.IdentityModel;
using Volo.Abp.Identity.Localization;
using Volo.Abp.Localization;
using Volo.Abp.Modularity;
using Volo.Abp.Security.Claims;
using Volo.Abp.Validation.Localization;
using Volo.Saas.Localization;
using Volo.Abp.Maui.Client;
namespace MyProject.Maui;
[DependsOn(
typeof(AbpAutofacModule),
typeof(AbpMauiClientModule),
typeof(AbpHttpClientIdentityModelModule),
typeof(MyProjectHttpApiClientModule)
)]
public class MyProjectMauiModule : AbpModule
{
public override void PreConfigureServices(ServiceConfigurationContext context)
{
PreConfigure<AbpHttpClientBuilderOptions>(options =>
{
options.ProxyClientBuildActions.Add((_, clientBuilder) =>
{
clientBuilder.ConfigurePrimaryHttpMessageHandler(GetInsecureHandler);
});
});
}
public override void ConfigureServices(ServiceConfigurationContext context)
{
var configuration = context.Services.GetConfiguration();
MapClaimTypes();
ConfigureOidcClient(context, configuration);
ConfigureLocalization();
}
private void ConfigureOidcClient(ServiceConfigurationContext context, IConfiguration configuration)
{
Configure<OidcClientOptions>(configuration.GetSection("Oidc:Options"));
context.Services.AddTransient<OidcClient>(sp =>
{
var options = sp.GetRequiredService<IOptions<OidcClientOptions>>().Value;
options.Browser = sp.GetRequiredService<MauiAuthenticationBrowser>();
options.BackchannelHandler = GetInsecureHandler();
return new OidcClient(options);
});
}
private void ConfigureLocalization()
{
Configure<AbpLocalizationOptions>(options =>
{
options.Resources
.Get<Simul_BCFOResource>()
.AddBaseTypes(typeof(AbpValidationResource))
.AddBaseTypes(typeof(IdentityResource))
.AddBaseTypes(typeof(AccountResource))
.AddBaseTypes(typeof(SaasResource));
});
Configure<AbpLocalizationOptions>(options =>
{
options.Languages.Add(new LanguageInfo("ar", "ar", "العربية", "ae"));
options.Languages.Add(new LanguageInfo("cs", "cs", "Čeština"));
options.Languages.Add(new LanguageInfo("en", "en", "English"));
options.Languages.Add(new LanguageInfo("en-GB", "en-GB", "English (UK)"));
options.Languages.Add(new LanguageInfo("hu", "hu", "Magyar"));
options.Languages.Add(new LanguageInfo("fi", "fi", "Finnish", "fi"));
options.Languages.Add(new LanguageInfo("fr", "fr", "Français", "fr"));
options.Languages.Add(new LanguageInfo("hi", "hi", "Hindi", "in"));
options.Languages.Add(new LanguageInfo("it", "it", "Italiano", "it"));
options.Languages.Add(new LanguageInfo("pt-BR", "pt-BR", "Português"));
options.Languages.Add(new LanguageInfo("ru", "ru", "Русский", "ru"));
options.Languages.Add(new LanguageInfo("sk", "sk", "Slovak", "sk"));
options.Languages.Add(new LanguageInfo("tr", "tr", "Türkçe"));
options.Languages.Add(new LanguageInfo("zh-Hans", "zh-Hans", "简体中文"));
options.Languages.Add(new LanguageInfo("zh-Hant", "zh-Hant", "繁體中文"));
options.Languages.Add(new LanguageInfo("de-DE", "de-DE", "Deutsch", "de"));
options.Languages.Add(new LanguageInfo("es", "es", "Español"));
});
}
//https://docs.microsoft.com/en-us/xamarin/cross-platform/deploy-test/connect-to-local-web-services#bypass-the-certificate-security-check
private static HttpMessageHandler GetInsecureHandler()
{
#if ANDROID
var handler = new HttpClientHandler()
{
UseCookies = false
};
handler.ServerCertificateCustomValidationCallback = (message, cert, chain, errors) =>
{
if (cert is { Issuer: "CN=Microsoft Azure TLS Issuing CA 02, O=Microsoft Corporation, C=US" })
{
return true;
}
return errors == System.Net.Security.SslPolicyErrors.None;
};
return handler;
#elif IOS
var handler = new NSUrlSessionHandler
{
UseCookies = false,
TrustOverrideForUrl = (sender, url, trust) => url.StartsWith("https://simul")
};
return handler;
#elif WINDOWS || MACCATALYST
return new HttpClientHandler()
{
UseCookies = false
};
#else
throw new PlatformNotSupportedException("Only Android, iOS, MacCatalyst, and Windows supported.");
#endif
}
private static void MapClaimTypes()
{
AbpClaimTypes.UserName = JwtClaimTypes.PreferredUserName;
AbpClaimTypes.Name = JwtClaimTypes.GivenName;
AbpClaimTypes.SurName = JwtClaimTypes.FamilyName;
AbpClaimTypes.UserId = JwtClaimTypes.Subject;
AbpClaimTypes.Role = JwtClaimTypes.Role;
AbpClaimTypes.Email = JwtClaimTypes.Email;
}
}
I have tried everything suggested. I even updated to 8.0.5. I can't even run it in debug mode. I am getting a java.cert.certificateexception in this app and another app that are both built on abp.io commercial 8.0.5
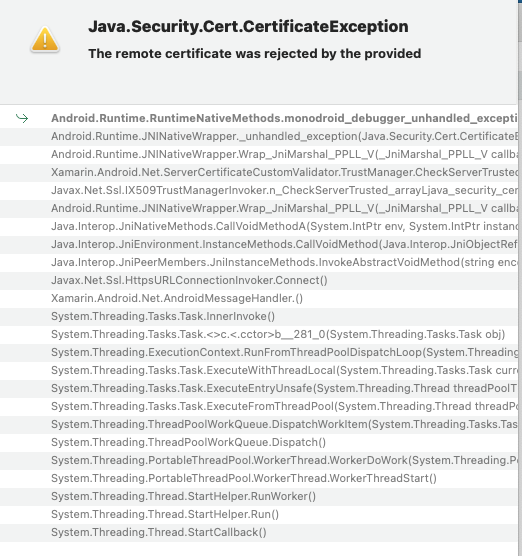
Again these apps run fine in iOS. I need to understand why these issues persist with this framework.
In the UpdatePermissions method I have removed the calls to AuthorizationService.IsGrantedAsync() and replaced them with just setting the properties to true as follows:
HasUsersPermission = true; // await AuthorizationService.IsGrantedAsync(IdentityPermissions.Users.Default); HasTenantsPermission = true; // await AuthorizationService.IsGrantedAsync(SaasHostPermissions.Tenants.Default);
As in my previous post, the app never gets past the splash screen.
These are the items in the MainApplication.cs file:
[assembly: UsesPermission(Android.Manifest.Permission.ReadExternalStorage, MaxSdkVersion = 32)]
[assembly: UsesPermission(Android.Manifest.Permission.ReadMediaAudio)]
[assembly: UsesPermission(Android.Manifest.Permission.ReadMediaImages)]
[assembly: UsesPermission(Android.Manifest.Permission.ReadMediaVideo)]
// Needed for Taking photo/video
[assembly: UsesPermission(Android.Manifest.Permission.Camera)]
[assembly: UsesPermission(Android.Manifest.Permission.WriteExternalStorage, MaxSdkVersion = 32)]
// Add these properties if you would like to filter out devices that do not have cameras, or set to false to make them optional
[assembly: UsesFeature("android.hardware.camera", Required = true)]
[assembly: UsesFeature("android.hardware.camera.autofocus", Required = true)]
This is the annotation for the MainActivity.cs:
[Activity(Theme = "@style/Maui.SplashTheme", MainLauncher = true, ConfigurationChanges = ConfigChanges.ScreenSize | ConfigChanges.Orientation | ConfigChanges.UiMode | ConfigChanges.ScreenLayout | ConfigChanges.SmallestScreenSize | ConfigChanges.Density)]
This is the annotations for the WebAuthenticatorCallbackActivity.cs
[Activity(NoHistory = true, LaunchMode = LaunchMode.SingleTop, Exported =true)]
[IntentFilter(new[] { Intent.ActionView },
Categories = new[] { Intent.CategoryDefault, Intent.CategoryBrowsable },
DataScheme = CALLBACK_SCHEME)]
In the MauiModule.cs file I am doing the following:
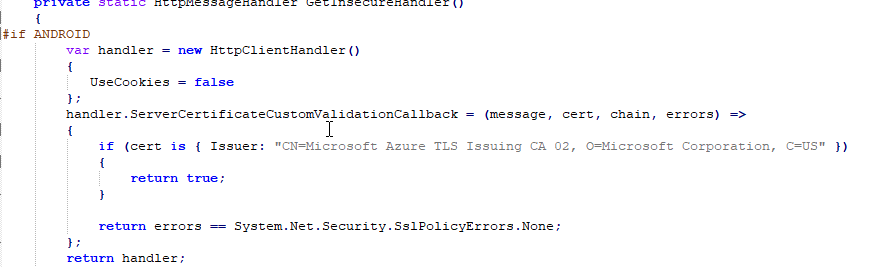
I didn't find anything in the link you sent me that gives any information about configuring the android portion of the project for using secure storage, and like I said, in the latest version that I tried I have removed the references that were originally giving the exception. Now I just get an "Application Not Responding" error.
Do you have any further suggestions or insights?
I updated the .csproj file to force the use of the interpreter in release mode for both the iOS and android versions of the app. Again, the iOS version runs successfully when deployed to TestFlight but the Android version now never gets past the splash screen. I've looked in SO for solutions but found none. Are you able to provide ANY assistance??
I followed the link you provided and added the exclusion file for the backup as suggested and the app now crashes immediately after showing the splash screen. Are there recommended settings in the manifest or other areas of the android app that I need to check? The iOS version of the app works fine.
Do you have any ideas on how to solve this???
I found the problem. I had the wrong values in both RedirectUri and the PostLoginRedirectUri. Once I changed those it worked.
I have a second MAUI app that was created with abp.io commercial 8.0.4 and it does the exact same thing when I attempt to login with the iOS app. There is no error in the log file, and it actually indicates that the call succeeds and returns a 200 status, but if fails in both the app and pasting the URL into a browser.
Both of these apps are fresh builds without any modifications to the MAUI project other than pointing them to the Azure web app service that hosts the web / api portion of the solution.
There is no error in the log file. The error happens when the result is sent back. It is a System.UriException: the Uri scheme is invalid. The rest of the message merely points to the call to this call:
var webAuthenticatorOptions = new WebAuthenticatorOptions
{
Url = new Uri(options.StartUrl),
CallbackUrl = new Uri(options.EndUrl),
PrefersEphemeralWebBrowserSession = true
};
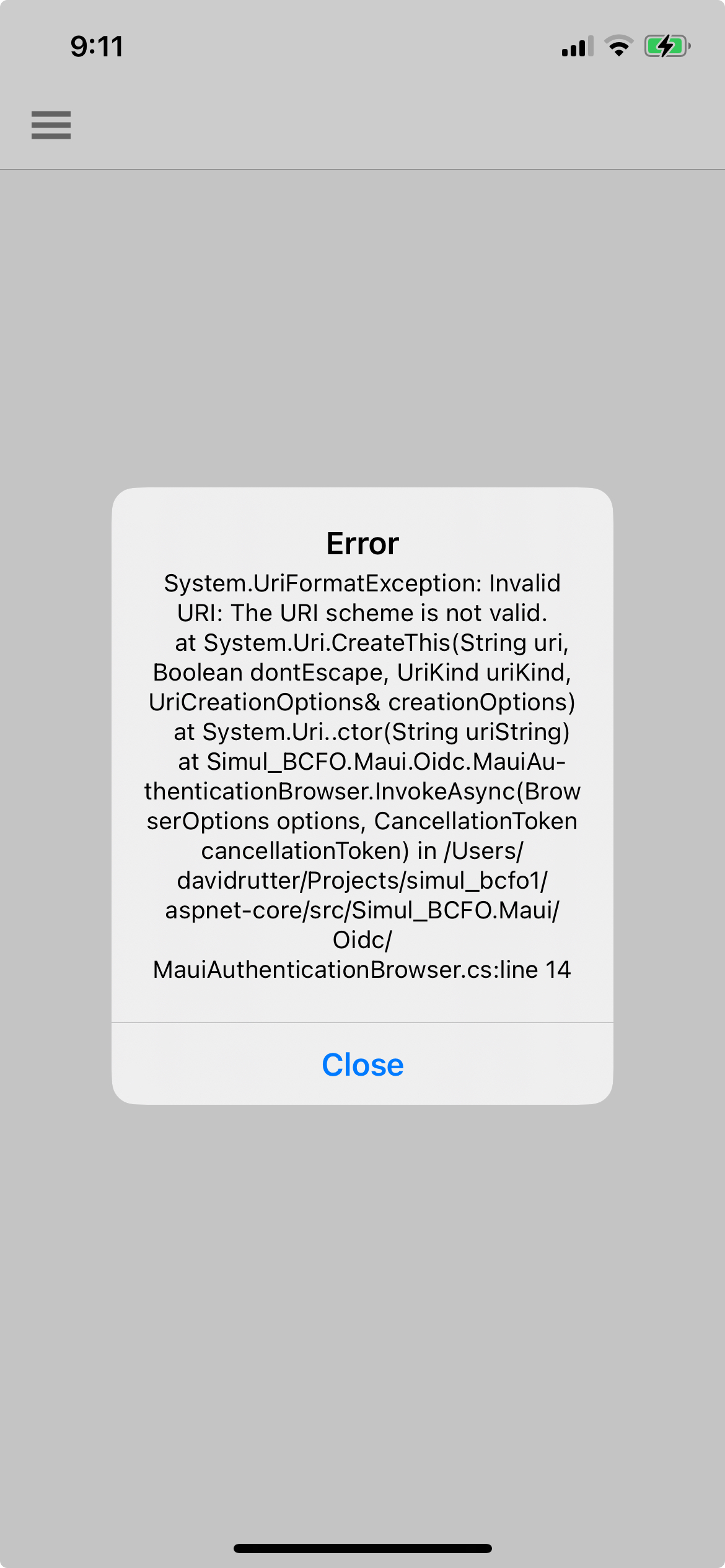
As I mentioned, If i copy the URL from the call into a browser I get a 400 error with no real information.
The only way I could get this to work was to put the code that is embedded in the call to AddProductionEncryptionAndSigningCertificate("openiddict.pfx", <passcode>) with the code that used to be in the WebModule.cs file and add the following additional parameters to the create certificate (X509KeyStorageFlags.PersistKeySet | X509KeyStorageFlags.MachineKeySet).
Because Azure seems to require those two flags on the new X509Certificate2() call, it would be nice if abp.io would go back to the previous way and let us add those parameters.

