If you want to build your image locally, see my answer for dockerfile.
dotnet dev-certs https -v -ep /app/identityserver.pfx -p 2D7AA457-5D33-48D6-936F-C48E5EF468ED
This doesn't work for production, it only generates certificate for localhost.
If you are publishing to Azure, you can use free azure HTTPS certificates. Or you can generate a self-signed certificate for your application. You can check how to generate self-signed certificate using openssl.
If you are publishing IdentityServer, you can check IdentityServer Deployment docs.
Here is a sample Dockerfile that works for local image creation:
Navigate to your application solution directory and run dotnet publish -c Release
FROM mcr.microsoft.com/dotnet/aspnet:6.0
COPY bin/Release/net6.0/publish/ app/
WORKDIR /app
ENTRYPOINT ["dotnet", "MyApplication.dll"]
To build the image, run docker build -t mycompany/myimage:$version .
Thanks for the information @chris.tune
Can you also share your middleware order if it can help others also? Can you also give information about your production environment like is it Kubernetes cluster, IIS etc?
You have an ANZ-Angular application which has its own token generation and validation within. You want to enable external login for ANZ-Angular application and use an ABP application identity server (tiered or non-tiered) as an openid provider.
The distributed system you are trying to achieve somewhat looks like below:
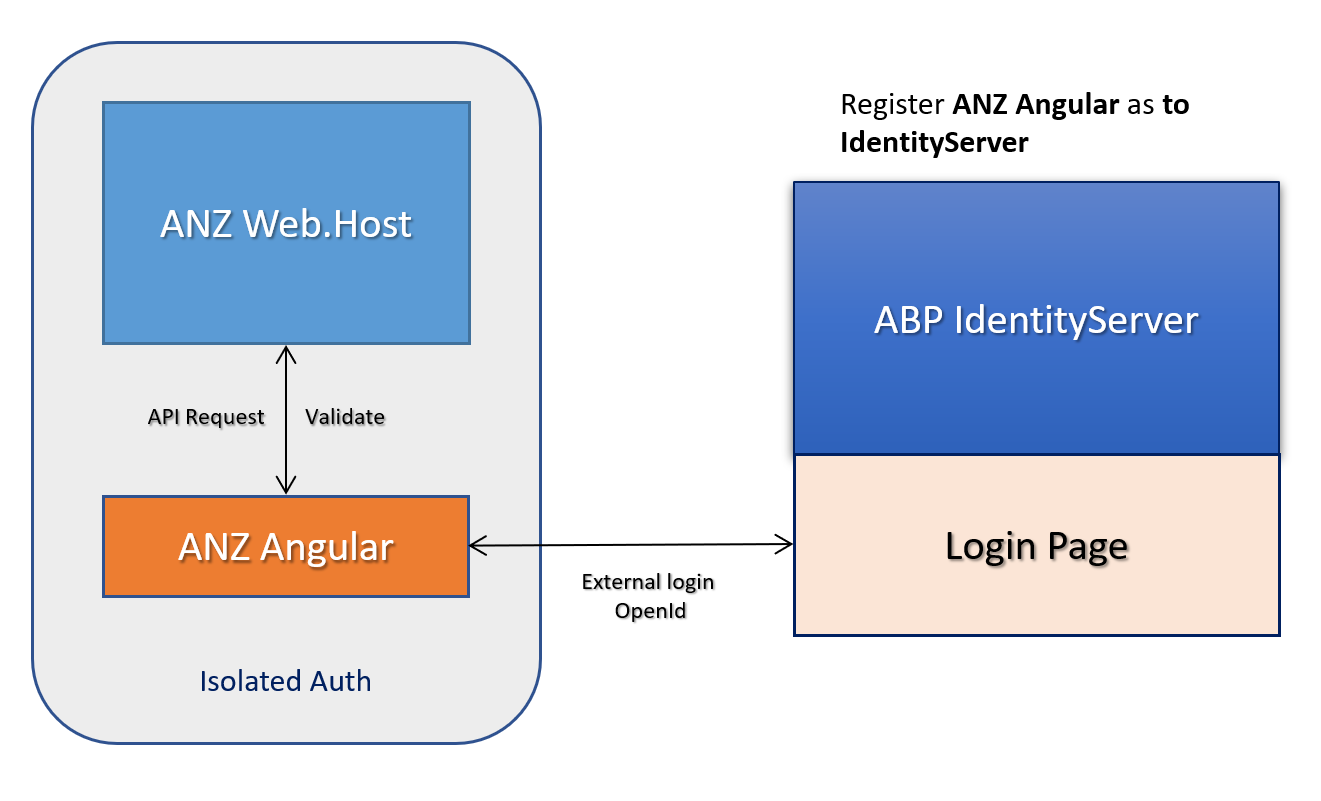
In this scenario, you are using ABP IdentityServer to externally login with ANZ-Angular application. You are not authorizing the ANZ-Web.Host, your access token is granted and validated only by ANZ-Web.Host not IdentityServer. To explain it shortly: you can not call ANZ-Web.Host from any extarnal application (ABP or not) because the SecureTokenServer is ANZ-Web.Host itself. Configuring IdentityServer for external login doesn't mean your STS is IdentityServer and will be validated by it. Anyways, that's a whole different consultancy on distributed systems story.
There are some steps to activate external login using OpenId between ABP and ANZ-Angular:
You can either use the ABP IdentityServer Management UI as you mentioned above or update the CreateClientsAsync method of the IdentityServerDataSeedContributor under DbMigrator project :
//Console Test / Angular Client
...
//Anz Angular Client - Add this client
var angular2 = configurationSection["AnzApp_App:ClientId"];
if (!angular2.IsNullOrWhiteSpace())
{
var webClientRootUrl = configurationSection["AnzApp_App:RootUrl"]?.TrimEnd('/');
await CreateClientAsync(
name: angular2,
scopes: commonScopes,
grantTypes: new[] { "password", "implicit" },
secret: (configurationSection["AnzApp_App:ClientSecret"] ?? "1q2w3e*").Sha256(),
requireClientSecret: false,
redirectUri: webClientRootUrl,
postLogoutRedirectUri: webClientRootUrl,
corsOrigins: new[] { webClientRootUrl.RemovePostFix("/") }
);
}
// Swagger Client
...
Note: Don't forget to add implicit grant type.
Update DbMigrator appsettings.json to add new configuration for this client:
"IdentityServer": {
"Clients": {
...
"AnzApp_App": {
"ClientId": "anz_client",
"RootUrl": "http://localhost:4201"
},
...
}
}
Note: I used port 4201 for ANZ-Angular application, enter whichever port you are using.
Navigate to WebHostModule.cs file under Startup folder and update the ConfigureExternalAuthProviders() method as below:
private void ConfigureExternalAuthProviders()
{
var externalAuthConfiguration = IocManager.Resolve<ExternalAuthConfiguration>();
if (bool.Parse(_appConfiguration["Authentication:OpenId:IsEnabled"]))
{
// Add this line to clear default ClaimsIdentity mapping
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear();
if (bool.Parse(_appConfiguration["Authentication:AllowSocialLoginSettingsPerTenant"]))
{
...
You can check JwtSecurityTokenHandler for detailed information about default claim mapping.
Navigate to appsettings.json and enable OpenId configuration:
"OpenId": {
"IsEnabled": "true",
"ClientId": "anz_client", // The client you have created in ABP IdentityServerDataSeedContributor
"Authority": "https://localhost:44312", // ABP IdentityServer url
"LoginUrl": "https://localhost:44312", // ABP IdentityServer url
"ValidateIssuer": "false",
"ClaimsMapping": [
]
},
Navigate to login.service.ts file under src/account/login folder. Find the getOpenIdConnectConfig(loginProvider: ExternalLoginProvider) method and update as below:
private getOpenIdConnectConfig(loginProvider: ExternalLoginProvider): AuthConfig {
let authConfig = new AuthConfig();
// Update login url
authConfig.loginUrl = loginProvider.additionalParams['LoginUrl'] +"/connect/authorize";
authConfig.issuer = loginProvider.additionalParams['Authority'];
authConfig.skipIssuerCheck = loginProvider.additionalParams['ValidateIssuer'] === 'false';
authConfig.clientId = loginProvider.clientId;
authConfig.responseType = 'id_token';
authConfig.redirectUri = window.location.origin + '/account/login';
// Add email scope
authConfig.scope = 'openid profile email';
authConfig.requestAccessToken = false;
return authConfig;
}
Known Issue:
There is a claim mapping issue on ANZ side with mapping username and email, resulting with creating a user with wrong username and email:
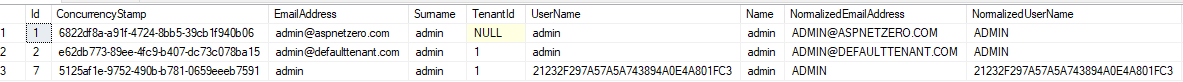
We'll fix it in next version of ANZ. For now, admin can update user information before activating the user.
We have investigated this issue. We need make some improvements to apis configuration since all the services need to be redirected to web gateway. However when this is the case, abp generate-proxy -t ng doesn't work because web gateway doesn't have the api definitions (gateways do not depend on microservice HTTP.API layers) since we are not using dynamic proxy any longer.
We'll try to decide on a subtle way to generate proxy with angular when using a gateway.
export const environment = {
production: false,
application: {
baseUrl,
name: 'PlatCloud',
},
oAuthConfig,
apis: {
default: {
url: 'https://localhost:44325',
rootNamespace: 'PlatCloud',
},
AbpAccountPublic: {
url: oAuthConfig.issuer,
rootNamespace: 'AbpAccountPublic',
},
ProductService: {
url: 'https://localhost:44361',
rootNamespace: 'PlatCloud',
},
},
} as Environment;
When you defined ProductService with its own address, it should generate the related proxies with abp generate-proxy -t ng. I will try it on 5.2.0 and let you know.
@enes.koroglu Can you give more information about:
@ronaksbhavsar
Did you tried to update (or downgrade) your application to see if it occurs again?
Hi @andmattia,
I'll try to reproduce this case and let you know. Can you verify that your ANZ version is 7.1.0 .Net Core 2.2?
Can you also ask this question to identityserver4 issues and StackOverflow to get faster response?
I didn't experience any error related to IdentityServerMiddleware similar to this issue. Also, this is not something we can reproduce.
Also, can you share your environment.ts file?
Errors seem to be related to the DTOs of AdministrationService, IdentityService, and SaasService.
Can you try adding to any of them explicitly as you have mentioned as a workaround to see if the error occurs again?

