Potentially sensitive application claims were excluded from the introspection response as the client 'EAP' was not explicitly listed as an audience.
[OpenIddict.Server.OpenIddictServerDispatcher] The response was successfully returned as a JSON document: {
"active": false
}.
The access_token is not active.
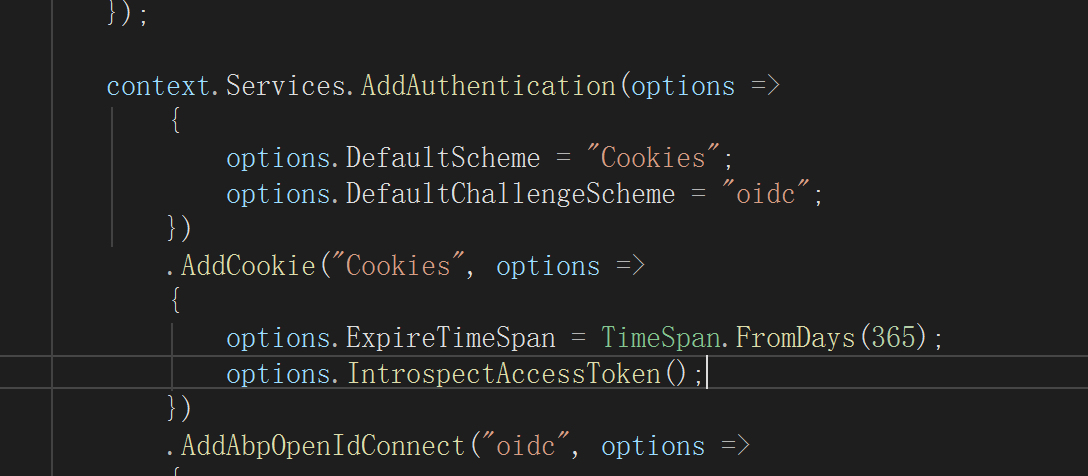
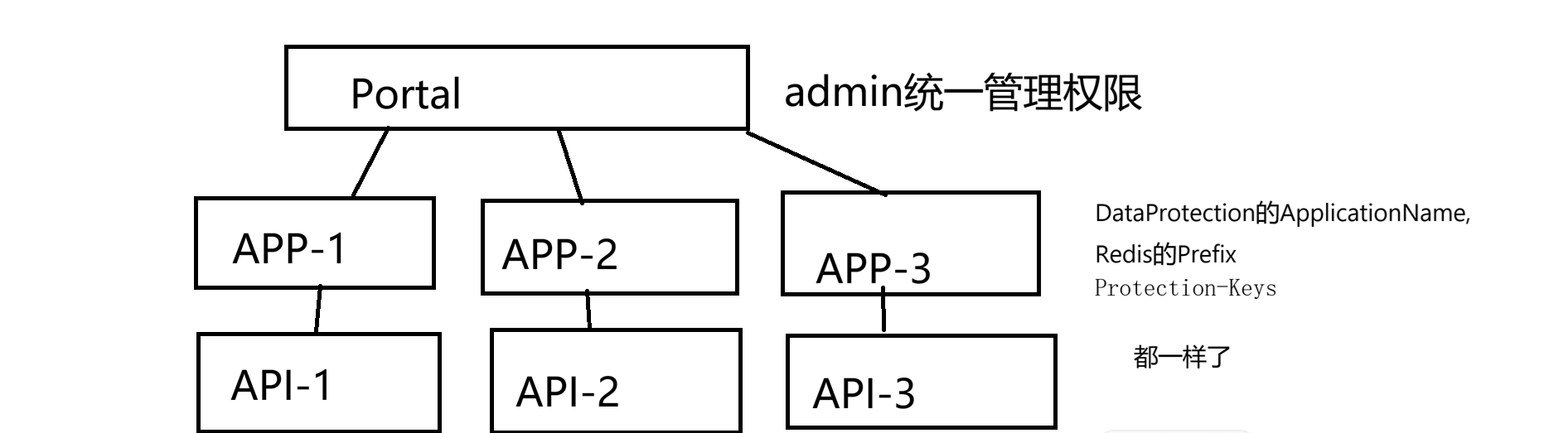 IntrospectAccessToken 在什么情况下使用
IntrospectAccessToken 在什么情况下使用
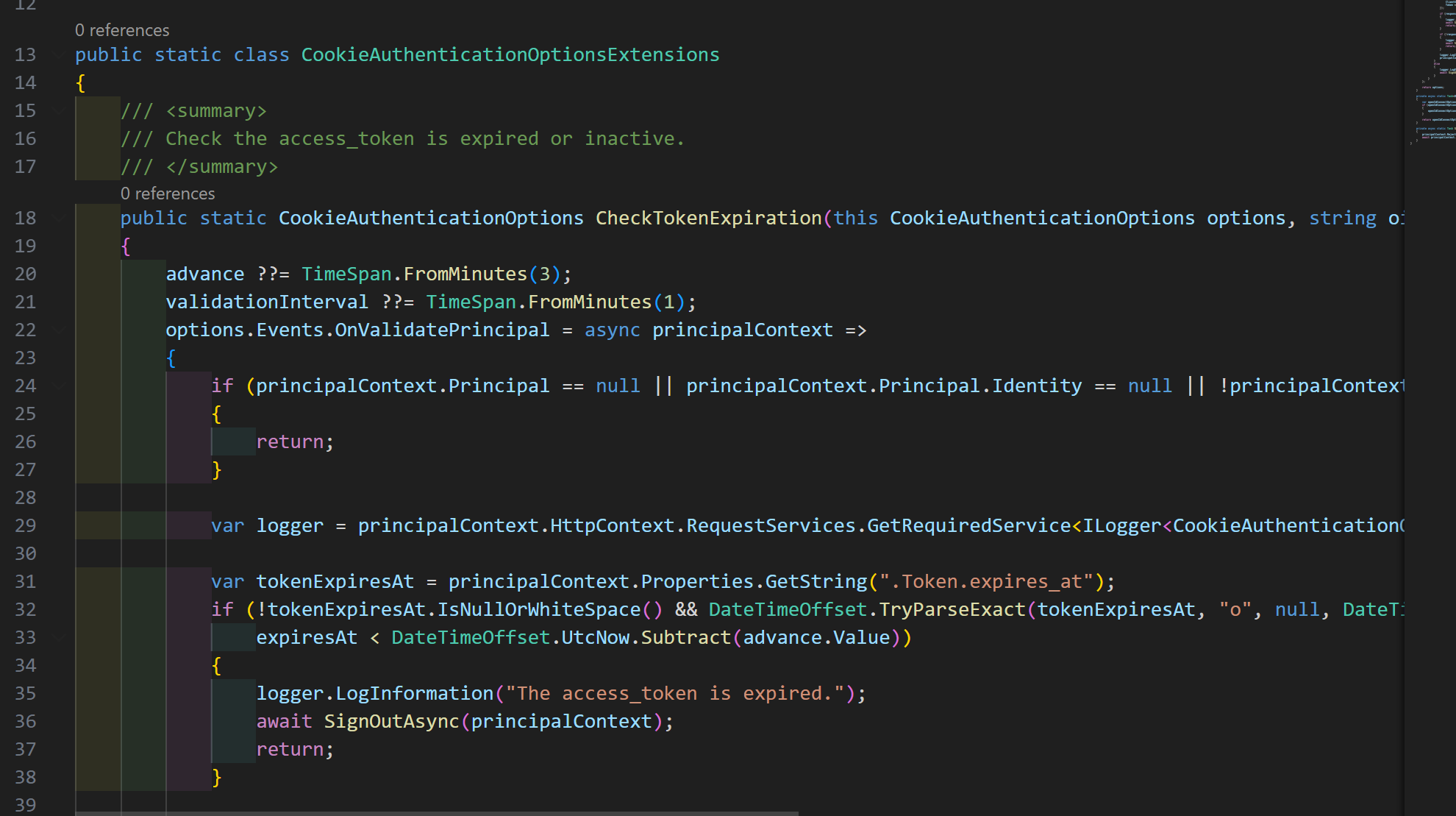 v8.3.4 project template ,use \framework\src\Volo.Abp.AspNetCore.Components.Server\Microsoft\AspNetCore\Authentication\Cookies\CookieAuthenticationOptionsExtensions.cs
v8.3.4 project template ,use \framework\src\Volo.Abp.AspNetCore.Components.Server\Microsoft\AspNetCore\Authentication\Cookies\CookieAuthenticationOptionsExtensions.cs

2.GetAsync(TCacheKey key, Nullable1 hideErrors, Boolean considerUow, CancellationToken token)
[2025-12-18 14:00:02.801 +08:00] [WRN] [Volo.Abp.Caching.DistributedCache] ---------- Exception Data ----------
Redis-Message = HMGET c:Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ApplicationConfigurationDto,k:vSkysoft:ApplicationConfiguration_Anonymous_zh-Hans
Redis-Message-Next = HMGET c:Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ApplicationConfigurationDto,k:vSkysoft:ApplicationConfiguration_77ea1cc56a3e9b7aecee3a15e9cea1f5_zh-Hans
Redis-OpsSinceLastHeartbeat = 0
Redis-Queue-Awaiting-Write = 0
Redis-Queue-Awaiting-Response = 8
Redis-Active-Writer = False
Redis-Backlog-Writer = SpinningDown
Redis-Read-State = ReadAsync
Redis-Write-State = Idle
Redis-Inbound-Bytes = 87304
Redis-Inbound-Pipe-Bytes = 0
Redis-Outbound-Pipe-Bytes = 0
Redis-Last-Result-Bytes = 0
Redis-Inbound-Buffer-Bytes = 0
Redis-Sync-Ops = 18
Redis-Async-Ops = 4395440
Redis-Server-Endpoint = 10.166.0.97:6379
Redis-Server-Connected-Seconds = 770.75
Redis-Abort-On-Connect = 0
Redis-Multiplexer-Connects = 1/1/0
Redis-Manager = 10 of 10 available
Redis-Client-Name = 2623c49bb095(SE.Redis-v2.7.27.49176)
Redis-ThreadPool-IO-Completion = (Busy=0,Free=1000,Min=1,Max=1000)
Redis-ThreadPool-Workers = (Busy=99,Free=32668,Min=16,Max=32767)
Redis-ThreadPool-Items = (Threads=99,QueuedItems=30,CompletedItems=89914679,Timers=26)
Redis-Busy-Workers = 99
Redis-Version = 2.7.27.49176
redis-command = HMGET c:Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ApplicationConfigurationDto,k:vSkysoft:ApplicationConfiguration_Anonymous_zh-Hans
request-sent-status = Sent
redis-server = 10.166.0.97:6379 Configure<PermissionManagementOptions>(options =>
{
options.ISaveStaticPermissionsToDatabase= true; options.IsDynamicPermissionStoreEnabled = false; });
ABP 7.2.2 Cannot find Volo.Abp.Ddd.Domain.Shared 7.2.2 nuget package. I use abp 7.2.2 but the package was not found.
warning when building: MyModule.Domain.Shared.csproj: Warning NU1603 : MyModule.Domain.Shared depends on Volo.Abp.Ddd.Domain.Shared (>= 7.2.2) but Volo.Abp.Ddd.Domain.Shared 7.2.2 was not found. Volo.Abp.Ddd.Domain.Shared 7.3.0 was resolved instead.

