Hi, I tried to add the hangfire background job to our identity server, but I encountered an issue that no active servers in the hangfire, below is the screenshot:
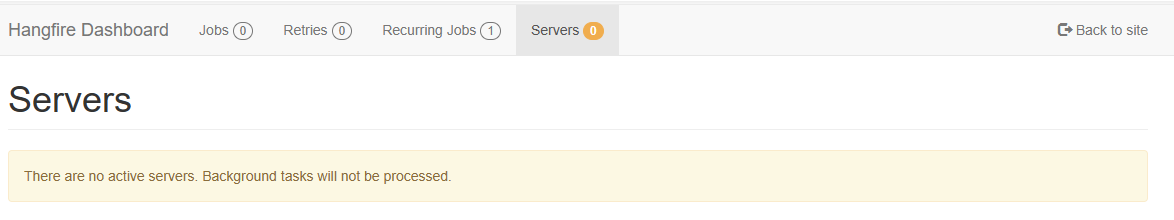
and here is the background job module:
[DependsOn(
typeof(AbpBackgroundJobsAbstractionsModule),
typeof(AbpBackgroundJobsHangfireModule)
)]
public class IdentityServerBackgroundJobsModule : AbpModule
{
public override void ConfigureServices(ServiceConfigurationContext context)
{
var configuration = context.Services.GetConfiguration();
var connectionString = configuration.GetConnectionString("Default");
context.Services.AddHangfire(config =>
{
config.UseSqlServerStorage(connectionString, new Hangfire.SqlServer.SqlServerStorageOptions()
{
SchemaName = "Hangfire"
});
});
}
public override void OnApplicationInitialization(ApplicationInitializationContext context)
{
var app = context.GetApplicationBuilder();
var configuration = context.GetConfiguration();
app.UseHangfireDashboard();
ConfireHangfireJobs(configuration);
}
private void ConfireHangfireJobs(IConfiguration configuration)
{
// remove all the jobs if exist
using (var connection = JobStorage.Current.GetConnection())
{
foreach (var recurringJob in StorageConnectionExtensions.GetRecurringJobs(connection))
{
RecurringJob.RemoveIfExists(recurringJob.Id);
}
}
// add new job
if (Convert.ToBoolean(configuration["RecurringJobs:HousekeepingJob:IsActive"]))
{
RecurringJob.AddOrUpdate<HousekeepingJob>(s => s.ExecuteAsync(), configuration["RecurringJobs:HousekeepingJob:CronSchedule"]);
}
}
}
Any help would be greatly appreciated.
Hi, We want to try the File Management module in ABP commercial demo site but the "Upload Files" does not response when I clicked it.
https://commercial-demo.abp.io/file-management
Anyone can help us check?
Hi, I managed to override it already. Thanks
Hi, we received a pen test finding indicating that we need to enable the 'Secure' flag for the '.AspNetCore.Culture' cookie:
I have tried to enable by adding this code but it does not work:
Configure<CookiePolicyOptions>(options =>
{
options.Secure = CookieSecurePolicy.Always;
});
Configure<AntiforgeryOptions>(options =>
{
options.Cookie.SecurePolicy = CookieSecurePolicy.Always;
});
could you please assist us on this request?
Hi @liangshiwei, sorry if my question confused you, but I want to know what cookies are created by this method in abp.js
abp.utils.setCookieValue = function (key, value, expireDate, path) {
var cookieValue = encodeURIComponent(key) + '=';
if (value) {
cookieValue = cookieValue + encodeURIComponent(value);
}
if (expireDate) {
cookieValue = cookieValue + "; expires=" + expireDate.toUTCString();
}
if (path) {
cookieValue = cookieValue + "; path=" + path;
}
document.cookie = cookieValue;
};
The purpose of using these cookies and do they contain any sensitive info?
Hi, we got a code scan finding on the method below in abp.js in identity server:
abp.utils.setCookieValue = function (key, value, expireDate, path) {
var cookieValue = encodeURIComponent(key) + '=';
if (value) {
cookieValue = cookieValue + encodeURIComponent(value);
}
if (expireDate) {
cookieValue = cookieValue + "; expires=" + expireDate.toUTCString();
}
if (path) {
cookieValue = cookieValue + "; path=" + path;
}
document.cookie = cookieValue;
};
The web application's function method creates a cookie, at line 623 of wwwroot/libs/abp/core/abp.js, and returns it in the response. However, the application is not configured to automatically set the cookie with the "httpOnly" attribute, and the code does not explicitly add this to the cookie.
I understand that the "HttpOnly" attribute cannot be set for a cookie using client-side JavaScript. However, I would like to request information about the cookies generated by the method in identity server, including their purpose and whether they contain any sensitive information.
Thank you.
Hi, what I want to achieve is instead of using RSA key, I want to use ECDSA key for signing credentials and encryption credentials. I find this is supported by OpenIddict in their documentation:
Encryption and signing credentials
To protect the tokens it issues, OpenIddict uses 2 types of credentials:
Signing credentials are used to protect against tampering. They can be either asymmetric (e.g a RSA or ECDSA key) or symmetric.
Encryption credentials are used to ensure the content of tokens cannot be read by malicious parties. They can be either asymmetric (e.g a RSA key) or symmetric.
but don't know why keep getting this error:
[09:54:04 DBG] An exception was thrown by OpenIddict.Server.OpenIddictServerHandlers+Protection+GenerateIdentityModelToken while handling the OpenIddict.Server.OpenIddictServerEvents+GenerateTokenContext event.
System.ArgumentNullException: IDX10000: The parameter 'privateKey' cannot be a 'null' or an empty object. (Parameter 'privateKey')
at Microsoft.IdentityModel.Tokens.EcdhKeyExchangeProvider..ctor(SecurityKey privateKey, SecurityKey publicKey, String alg, String enc)
Is there any sample code using ECDSA key instead of RSA key?
Hi @maliming, thanks, I managed to add the encryption key into JWKS URL but I got the below error when using Angular UI to login to retrieve the access token:
[09:54:04 DBG] An exception was thrown by OpenIddict.Server.OpenIddictServerHandlers+Protection+GenerateIdentityModelToken while handling the OpenIddict.Server.OpenIddictServerEvents+GenerateTokenContext event.
System.ArgumentNullException: IDX10000: The parameter 'privateKey' cannot be a 'null' or an empty object. (Parameter 'privateKey')
at Microsoft.IdentityModel.Tokens.EcdhKeyExchangeProvider..ctor(SecurityKey privateKey, SecurityKey publicKey, String alg, String enc)
Even the security key I put into EncryptingCredentials already had the private key, I have provided you the source code through email, able to help us check?
Hi @maliming, is there a way to override the handler?

