- ABP Framework version: v3.2
- UI type: Angular
- DB provider: EF Core / MongoDB
- Tiered (MVC) or Identity Server Separated (Angular): yes
- Exception message and stack trace:
- Steps to reproduce the issue:
- I used Keycloak with SSO, code as:
{
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear();
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Add("sub", ClaimTypes.NameIdentifier);
context.Services.AddAuthentication()
.AddIdentityServerAuthentication(options =>
{
options.Authority = configuration["AuthServer:Authority"];
options.RequireHttpsMetadata = false;
options.ApiName = "newPMS";
options.JwtBackChannelHandler = new HttpClientHandler()
{
ServerCertificateCustomValidationCallback = HttpClientHandler.DangerousAcceptAnyServerCertificateValidator
};
})
.AddOpenIdConnect("KeyCloakOpenId", "Ord key cloak", options =>
{
// options.SignInScheme = IdentityConstants.ExternalScheme;
options.Authority = configuration["Authentication:KeyCloak:Authority"];
options.ClientId = configuration["Authentication:KeyCloak:ClientId"];
options.ResponseType = OpenIdConnectResponseType.CodeIdToken;
options.CallbackPath = "/signin-oidc";
options.SignedOutRedirectUri = configuration["App:SelfUrl"];
options.ClientSecret = configuration["Authentication:KeyCloak:ClientSecret"];
options.RequireHttpsMetadata = false;
options.GetClaimsFromUserInfoEndpoint = true;
options.SaveTokens = true;
options.Scope.Add("offline_access email");
});
}
- I custom file LoggedOutModel
[Dependency(ReplaceServices = true)]
[ExposeServices(typeof(LoggedOutModel))]
public class CustomLogoutModel : LoggedOutModel
{
private readonly IConfiguration _configuration;
public CustomLogoutModel(IConfiguration configuration)
{
_configuration = configuration;
}
public override async Task<IActionResult> OnGetAsync()
{
await HttpContext.SignOutAsync("KeyCloakOpenId", new AuthenticationProperties()
{
RedirectUri = "/"
});
await base.OnGetAsync();
return Redirect("/");
}
}
6 Answer(s)
-
0
I think you need to configure Identity Server for front channel logout. I'll share you a link which is similar to your requirement https://support.aspnetzero.com/QA/Questions/9809/How-do-I-implement-logout-all-client-with-Identity-Server-4#answer-7d351498-32de-92e6-a92b-39f8bf30a871
-
0
-
0
-
0
Hi @maliming please give me the link! Thank!
-
0
HI
The link is the alper shared. But you said you can't access it.
https://support.aspnetzero.com/QA/Questions/9809/How-do-I-implement-logout-all-client-with-Identity-Server-4#answer-7d351498-32de-92e6-a92b-39f8bf30a871
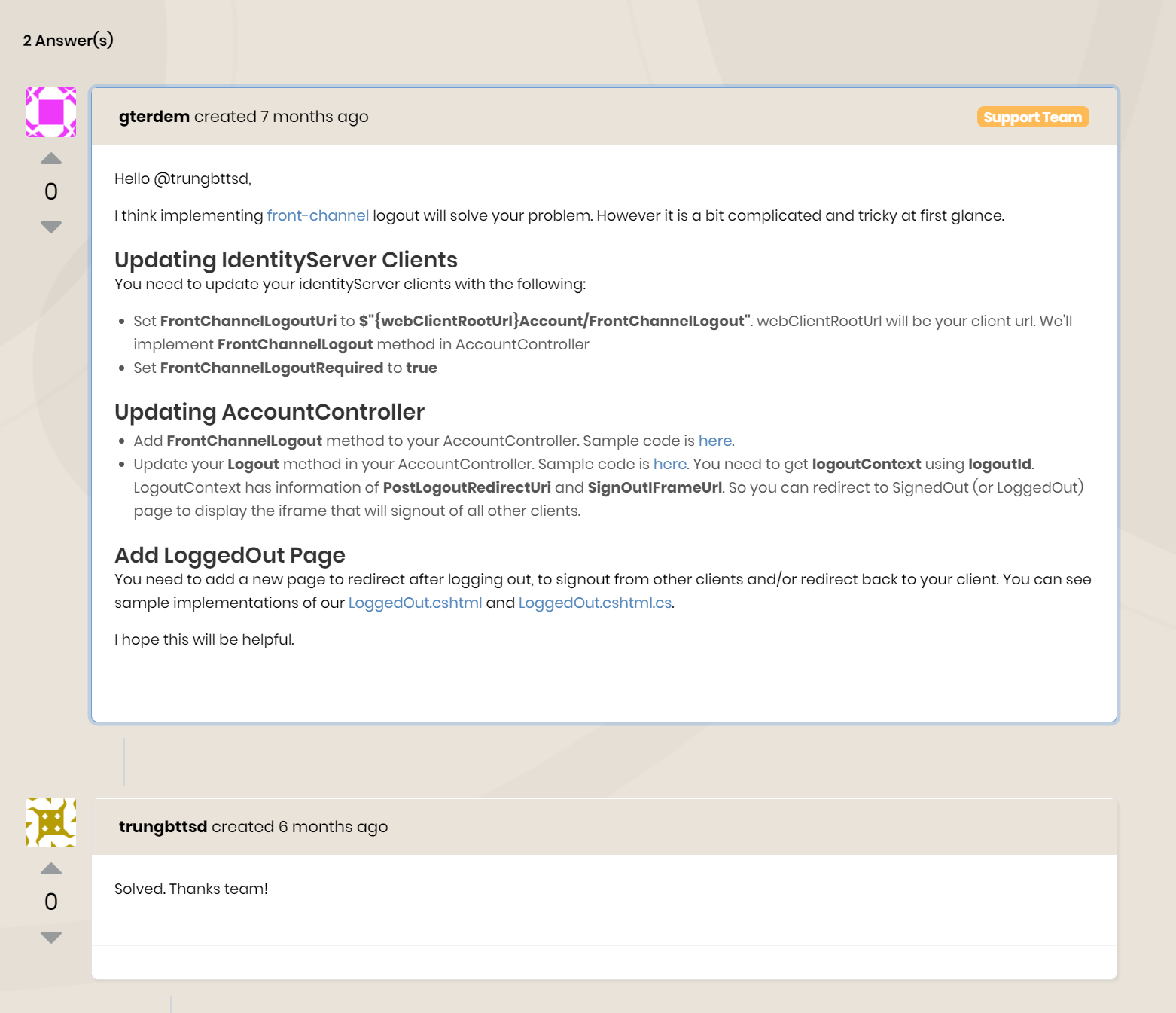
Hello @trungbttsd,
I think implementing front-channel logout will solve your problem. However it is a bit complicated and tricky at first glance.
Updating IdentityServer Clients
You need to update your identityServer clients with the following:
- Set FrontChannelLogoutUri to $"{webClientRootUrl}Account/FrontChannelLogout". webClientRootUrl will be your client url. We'll implement FrontChannelLogout method in AccountController
- Set FrontChannelLogoutRequired to true
Updating AccountController
- Add FrontChannelLogout method to your AccountController. Sample code is here.
- Update your Logout method in your AccountController. Sample code is here. You need to get logoutContext using logoutId. LogoutContext has information of PostLogoutRedirectUri and SignOutIFrameUrl. So you can redirect to SignedOut (or LoggedOut) page to display the iframe that will signout of all other clients.
Add LoggedOut Page
You need to add a new page to redirect after logging out, to signout from other clients and/or redirect back to your client. You can see sample implementations of our LoggedOut.cshtml and LoggedOut.cshtml.cs.
I hope this will be helpful.
-
0
Thanks team! Solved