- ABP Framework version: commercial v 5rc.1
- UI type: Angular
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): yes
I want to add external Idsrv4 to the abp Idsrv In Project "XXXX.IdentityServer.csproj" I added two Packages <PackageReference Include="Microsoft.AspNetCore.Authentication.OpenIdConnect" Version="6.0.0" /> <PackageReference Include="IdentityModel" Version="5.1.0" />
and I configure authentication, but still user can not login,
context.Services.AddAuthentication()
.AddJwtBearer(options =>
{
options.Authority = configuration["AuthServer:Authority"];
options.RequireHttpsMetadata = Convert.ToBoolean(configuration["AuthServer:RequireHttpsMetadata"]);
options.Audience = configuration["AuthServer:ApiName"];
}).AddOpenIdConnect("oidc", options =>
{
options.Authority = "https://localhost:44382/";
options.ClientId = "main_core_idsrv";
options.ClientSecret = "main_core_idsrv_secret_mvc";
options.ResponseType = OpenIdConnectResponseType.Code;
options.SaveTokens = true;
options.GetClaimsFromUserInfoEndpoint = true;
options.TokenValidationParameters = new TokenValidationParameters
{
ValidateAudience = false
};
options.Scope.Clear();
options.Scope.Add("openid");
options.Scope.Add("profile");
options.Scope.Add("ApiOne");
options.Scope.Add("offline_access");
options.Events = new OpenIdConnectEvents
{
OnTokenValidated = context =>
{
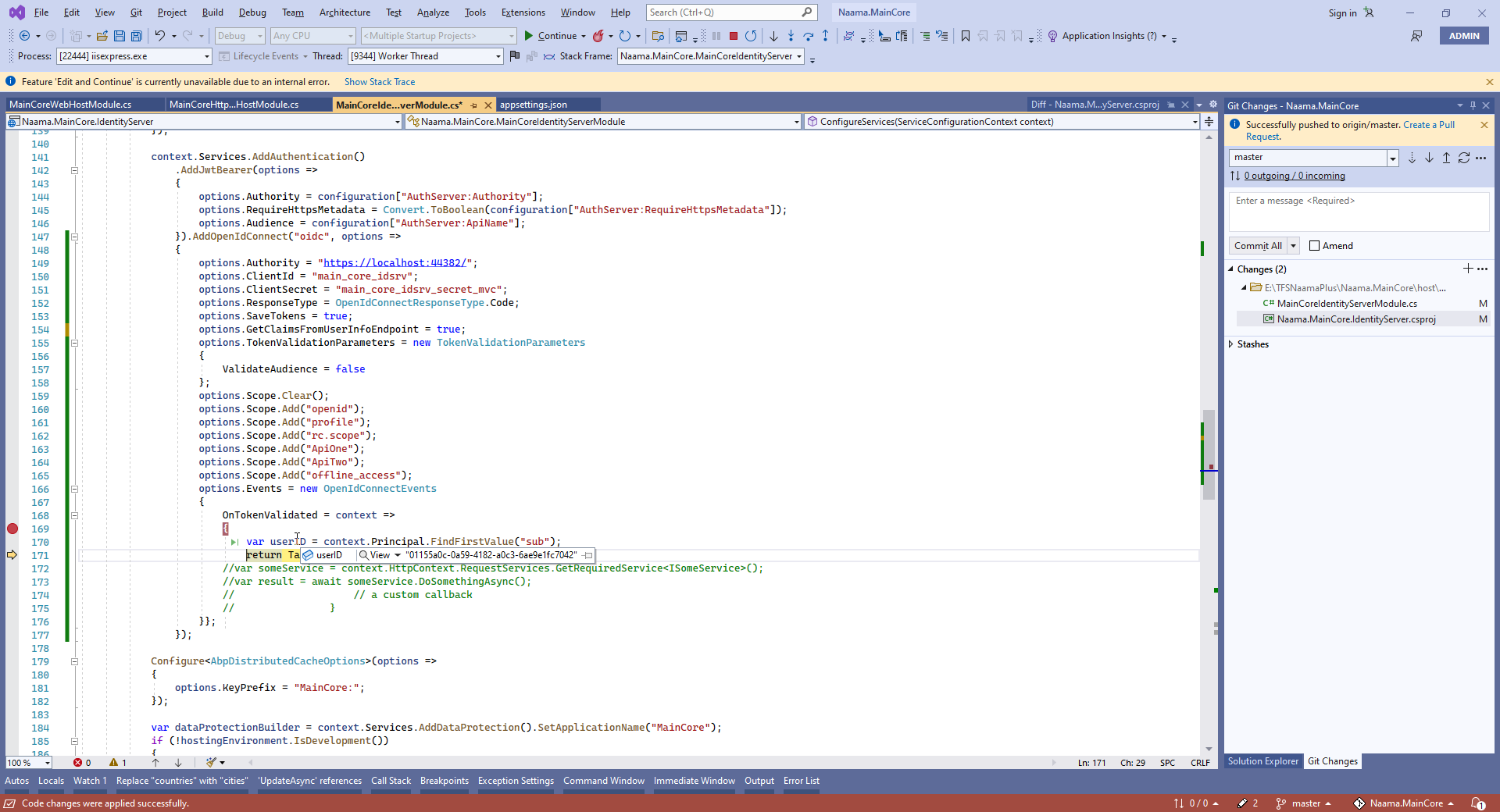
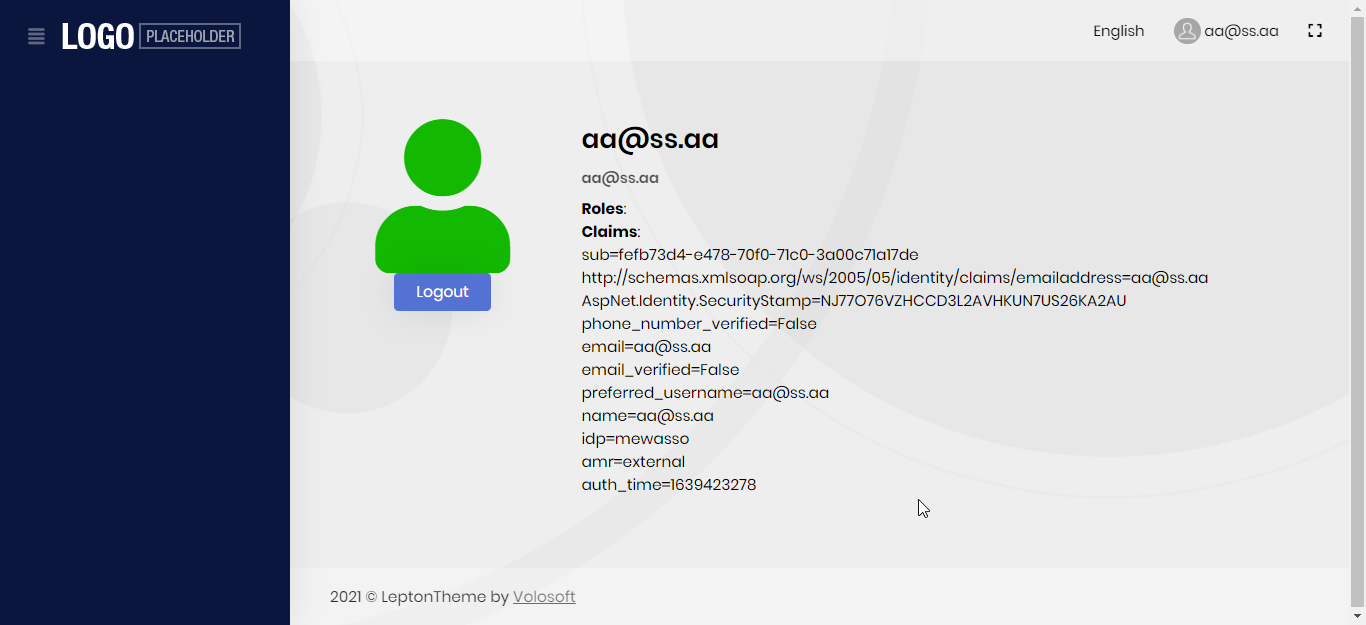
var userID = context.Principal.FindFirstValue("sub");
return Task.CompletedTask;
}};
});
19 Answer(s)
-
0
hi
Please check your app logs.
-
0
-
0
Are there any warnings from the browser console?
You can try
dotnet runinstead of IIS. -
0
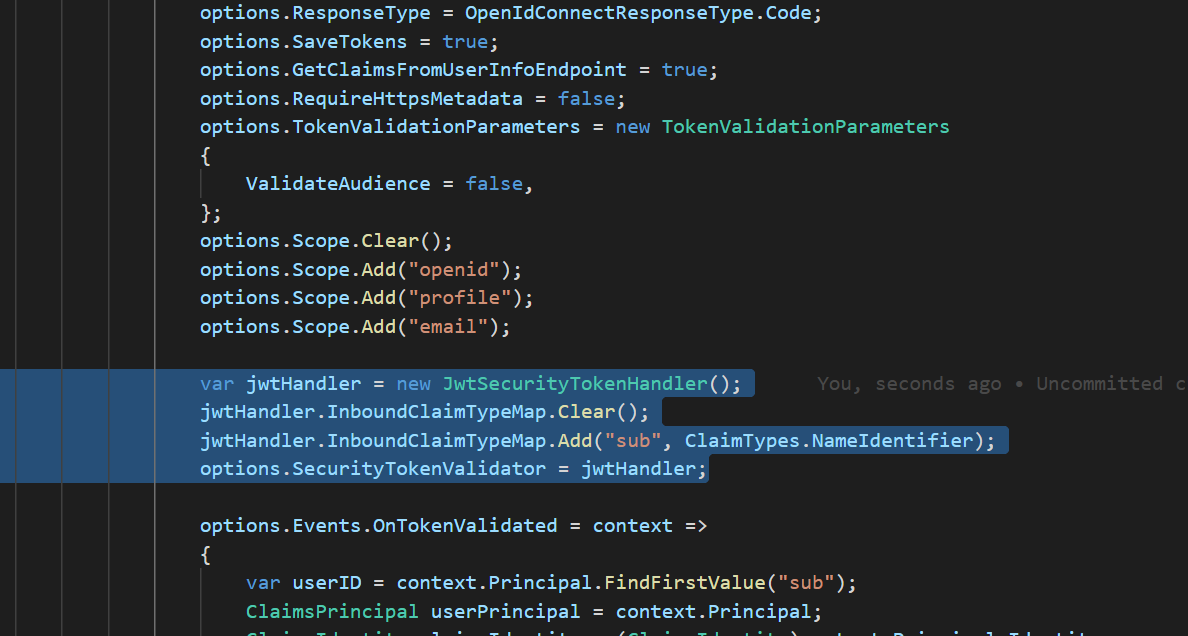
after adding these below lines, login success on MVC project but the angular application not working
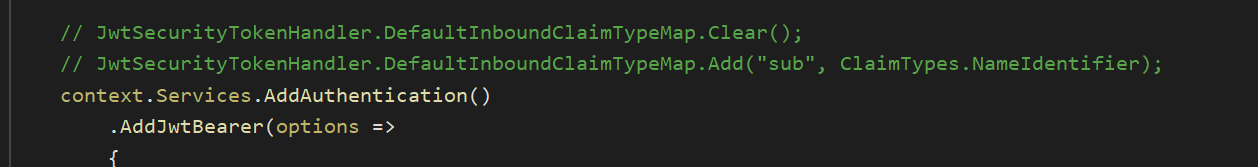
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear(); JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Add("sub", ClaimTypes.NameIdentifier);
https://stackoverflow.com/questions/38510592/is-sub-claim-part-of-openid-scope-or-profile-scope https://github.com/IdentityServer/IdentityServer4/issues/2968
https://support.abp.io/QA/Questions/695/Identity-Server-timeout-error-when-trying-to-login-with-external-authentication-provider
the angular application login not working after these changes.
-
0
hi
What's your
oAuthConfigof the angular app? -
0
Abp identity server host I don’t change any thing in angular template
-
0
hi
Is there any info in the logs?
-
0
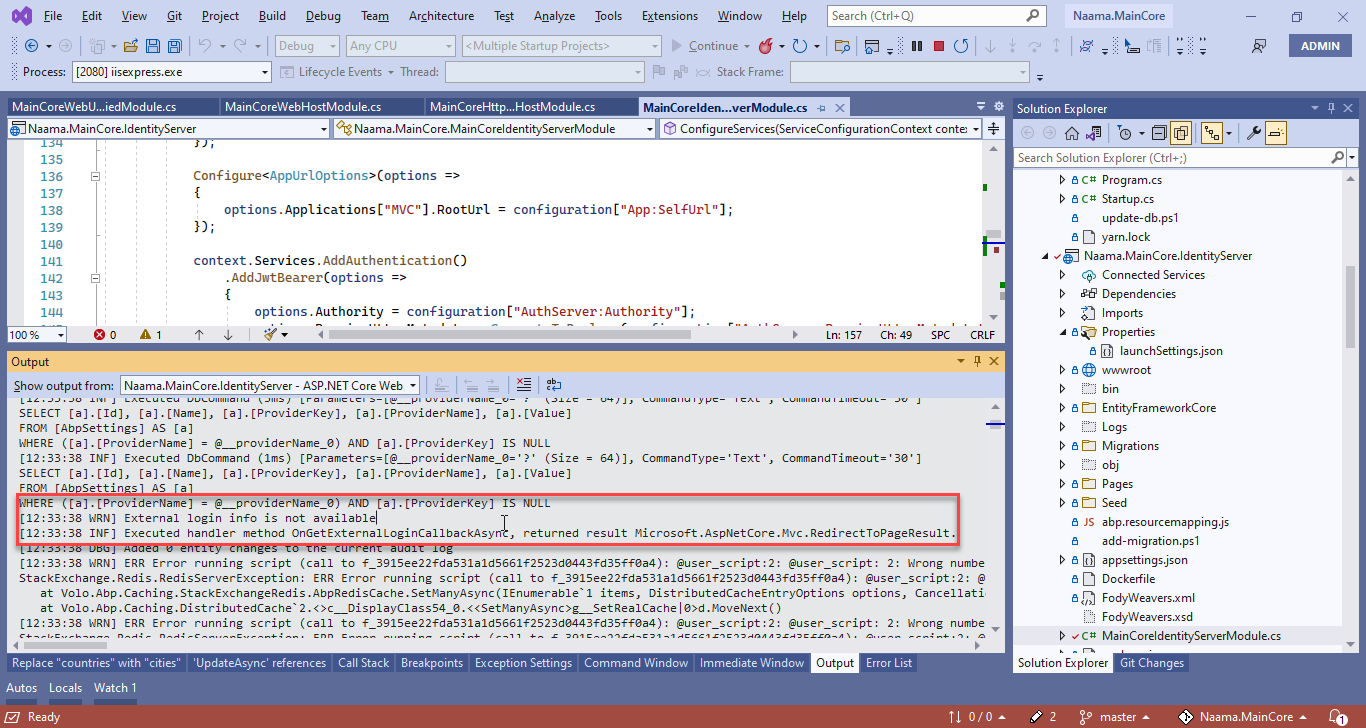
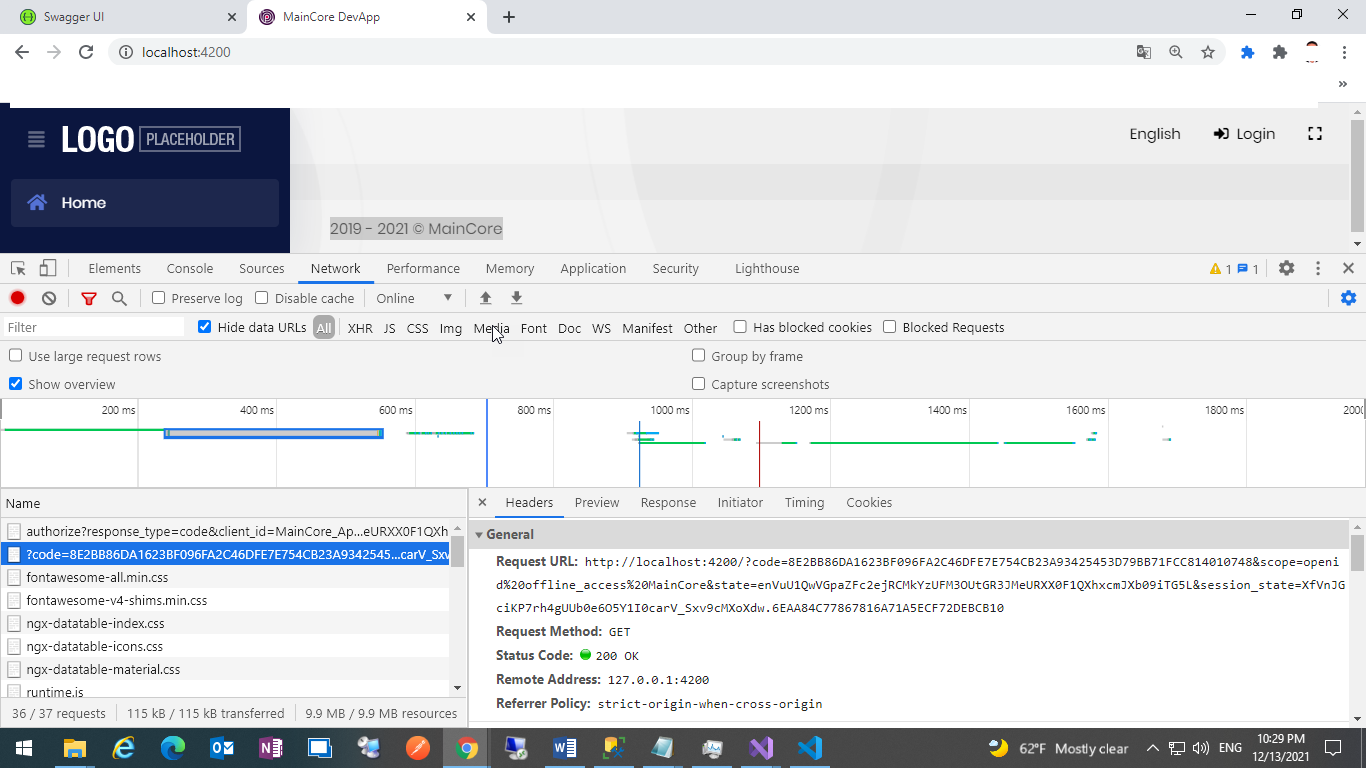
[07:19:09 INF] Request starting HTTP/2 GET https://localhost:44380/swagger/oauth2-redirect.html?code=B4C109813A665E6504AA9E6C40C39FCC6ED36FA4D1D1329AC1F5BEAA95F73FE1&scope=MainCore&state=VHVlIERlYyAxNCAyMDIxIDA3OjE5OjA5IEdNVCswMzAwIChBcmFiaWFuIFN0YW5kYXJkIFRpbWUp - - [07:19:10 INF] Sending file. Request path: '/oauth2-redirect.html'. Physical path: 'N/A' [07:19:10 INF] Request finished HTTP/2 GET https://localhost:44380/swagger/oauth2-redirect.html?code=B4C109813A665E6504AA9E6C40C39FCC6ED36FA4D1D1329AC1F5BEAA95F73FE1&scope=MainCore&state=VHVlIERlYyAxNCAyMDIxIDA3OjE5OjA5IEdNVCswMzAwIChBcmFiaWFuIFN0YW5kYXJkIFRpbWUp - - - 200 - text/html 69.9797ms [07:19:10 INF] Request starting HTTP/2 GET https://localhost:44380/_framework/aspnetcore-browser-refresh.js - - [07:19:10 INF] Request finished HTTP/2 GET https://localhost:44380/_framework/aspnetcore-browser-refresh.js - - - 200 11961 application/javascript;+charset=utf-8 3.0466ms [07:19:28 INF] Request starting HTTP/2 GET https://localhost:44380/abp/Swashbuckle/SetCsrfCookie - - [07:19:29 INF] Executing endpoint 'Volo.Abp.Swashbuckle.AbpSwashbuckleController.SetCsrfCookie (Volo.Abp.Swashbuckle)' [07:19:29 INF] Route matched with {area = "Abp", action = "SetCsrfCookie", controller = "AbpSwashbuckle", page = ""}. Executing controller action with signature Void SetCsrfCookie() on controller Volo.Abp.Swashbuckle.AbpSwashbuckleController (Volo.Abp.Swashbuckle). [07:19:29 INF] Executing action method Volo.Abp.Swashbuckle.AbpSwashbuckleController.SetCsrfCookie (Volo.Abp.Swashbuckle) - Validation state: Valid [07:19:29 INF] Executed action method Volo.Abp.Swashbuckle.AbpSwashbuckleController.SetCsrfCookie (Volo.Abp.Swashbuckle), returned result Microsoft.AspNetCore.Mvc.EmptyResult in 5.8642ms. [07:19:29 INF] Executed action Volo.Abp.Swashbuckle.AbpSwashbuckleController.SetCsrfCookie (Volo.Abp.Swashbuckle) in 75.6143ms [07:19:29 INF] Executed endpoint 'Volo.Abp.Swashbuckle.AbpSwashbuckleController.SetCsrfCookie (Volo.Abp.Swashbuckle)' [07:19:29 INF] Request finished HTTP/2 GET https://localhost:44380/abp/Swashbuckle/SetCsrfCookie - - - 204 - - 972.4942ms [07:19:29 INF] Request starting HTTP/2 GET https://localhost:44380/api/main-core/country - - [07:19:29 DBG] PermissionStore.GetCacheItemAsync: pn:U,pk:bcc71862-d28a-ea04-151c-3a00c9540629,n:MainCore.Countries [07:19:29 DBG] Not found in the cache: pn:U,pk:bcc71862-d28a-ea04-151c-3a00c9540629,n:MainCore.Countries [07:19:29 DBG] Getting all granted permissions from the repository for this provider name,key: U,bcc71862-d28a-ea04-151c-3a00c9540629 [07:19:29 INF] Entity Framework Core 6.0.0 initialized 'PermissionManagementDbContext' using provider 'Microsoft.EntityFrameworkCore.SqlServer:6.0.0' with options: QuerySplittingBehavior=SplitQuery [07:19:29 INF] Executed DbCommand (3ms) [Parameters=[@__ef_filter__p_0='?' (DbType = Boolean), @__providerName_0='?' (Size = 64), @__providerKey_1='?' (Size = 64)], CommandType='Text', CommandTimeout='30'] SELECT [a].[Id], [a].[Name], [a].[ProviderKey], [a].[ProviderName], [a].[TenantId] FROM [AbpPermissionGrants] AS [a] WHERE ((@__ef_filter__p_0 = CAST(1 AS bit)) OR [a].[TenantId] IS NULL) AND (([a].[ProviderName] = @__providerName_0) AND ([a].[ProviderKey] = @__providerKey_1)) [07:19:29 DBG] Setting the cache items. Count: 25 [07:19:29 DBG] Finished setting the cache items. Count: 25 [07:19:29 DBG] PermissionStore.GetCacheItemAsync: pn:C,pk:MainCore_Swagger,n:MainCore.Countries [07:19:29 DBG] Not found in the cache: pn:C,pk:MainCore_Swagger,n:MainCore.Countries [07:19:29 DBG] Getting all granted permissions from the repository for this provider name,key: C,MainCore_Swagger [07:19:29 INF] Entity Framework Core 6.0.0 initialized 'PermissionManagementDbContext' using provider 'Microsoft.EntityFrameworkCore.SqlServer:6.0.0' with options: QuerySplittingBehavior=SplitQuery [07:19:29 INF] Executed DbCommand (1ms) [Parameters=[@__ef_filter__p_0='?' (DbType = Boolean), @__providerName_0='?' (Size = 64), @__providerKey_1='?' (Size = 64)], CommandType='Text', CommandTimeout='30'] SELECT [a].[Id], [a].[Name], [a].[ProviderKey], [a].[ProviderName], [a].[TenantId] FROM [AbpPermissionGrants] AS [a] WHERE ((@__ef_filter__p_0 = CAST(1 AS bit)) OR [a].[TenantId] IS NULL) AND (([a].[ProviderName] = @__providerName_0) AND ([a].[ProviderKey] = @__providerKey_1)) [07:19:29 DBG] Setting the cache items. Count: 25 [07:19:29 DBG] Finished setting the cache items. Count: 25 [07:19:29 INF] Authorization failed. These requirements were not met: PermissionRequirement: MainCore.Countries [07:19:29 INF] AuthenticationScheme: Bearer was forbidden. [07:19:29 INF] Request finished HTTP/2 GET https://localhost:44380/api/main-core/country - - - 403 - - 79.0858ms
-
0
if remove two-line , every thing it's ok JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear(); JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Add("sub", ClaimTypes.NameIdentifier);
or if remove attr => [Authorize(MainCore.Countries)] => , every thing it's ok or change to [Authorize()] => , every thing it's ok
-
0
hi
Can you share a simple project with me? include the steps liming.ma@volosoft.com
-
0
Code shared
I have two problems Angular Login not working in API with login external user => AbpPermissionGrants on User not working, but AbpPermissionGrants on Role working fine
-
0
hi
http://10.250.1.170/MEWASSO
Is there a public internet IP address or domain?
-
0
hi
Please remove these code and try to configure the claims in the options delegate.
https://leastprivilege.com/2017/11/15/missing-claims-in-the-asp-net-core-2-openid-connect-handler/ https://docs.microsoft.com/en-us/aspnet/core/security/authentication/claims?view=aspnetcore-6.0#mapping-claims-using-openid-connect-authentication
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear(); JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Add("sub", ClaimTypes.NameIdentifier);
-
0
if remove these code external user not login
https://stackoverflow.com/questions/38510592/is-sub-claim-part-of-openid-scope-or-profile-scope https://github.com/IdentityServer/IdentityServer4/issues/2968
https://support.abp.io/QA/Questions/695/Identity-Server-timeout-error-when-trying-to-login-with-external-authentication-provider
-
0
I'm checking your project, wait a moment.
-
0
-
0
Another way is
options.ClaimActions.MapJsonKey(ClaimTypes.NameIdentifier, "sub"); -
0
thanks your support, I try these options.ClaimActions.MapJsonKey(ClaimTypes.NameIdentifier, "sub"); and working fine
-
0
Good to hear