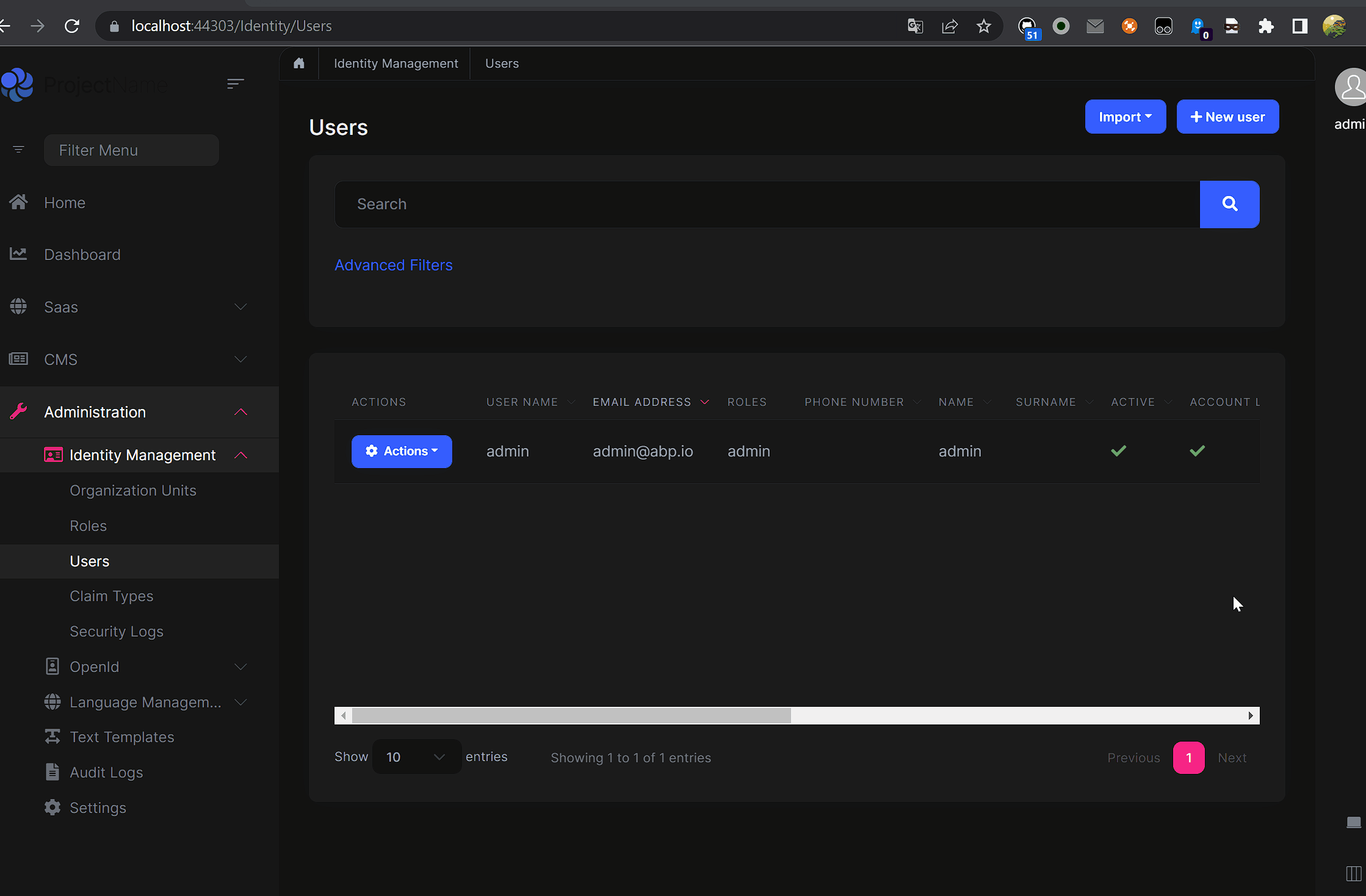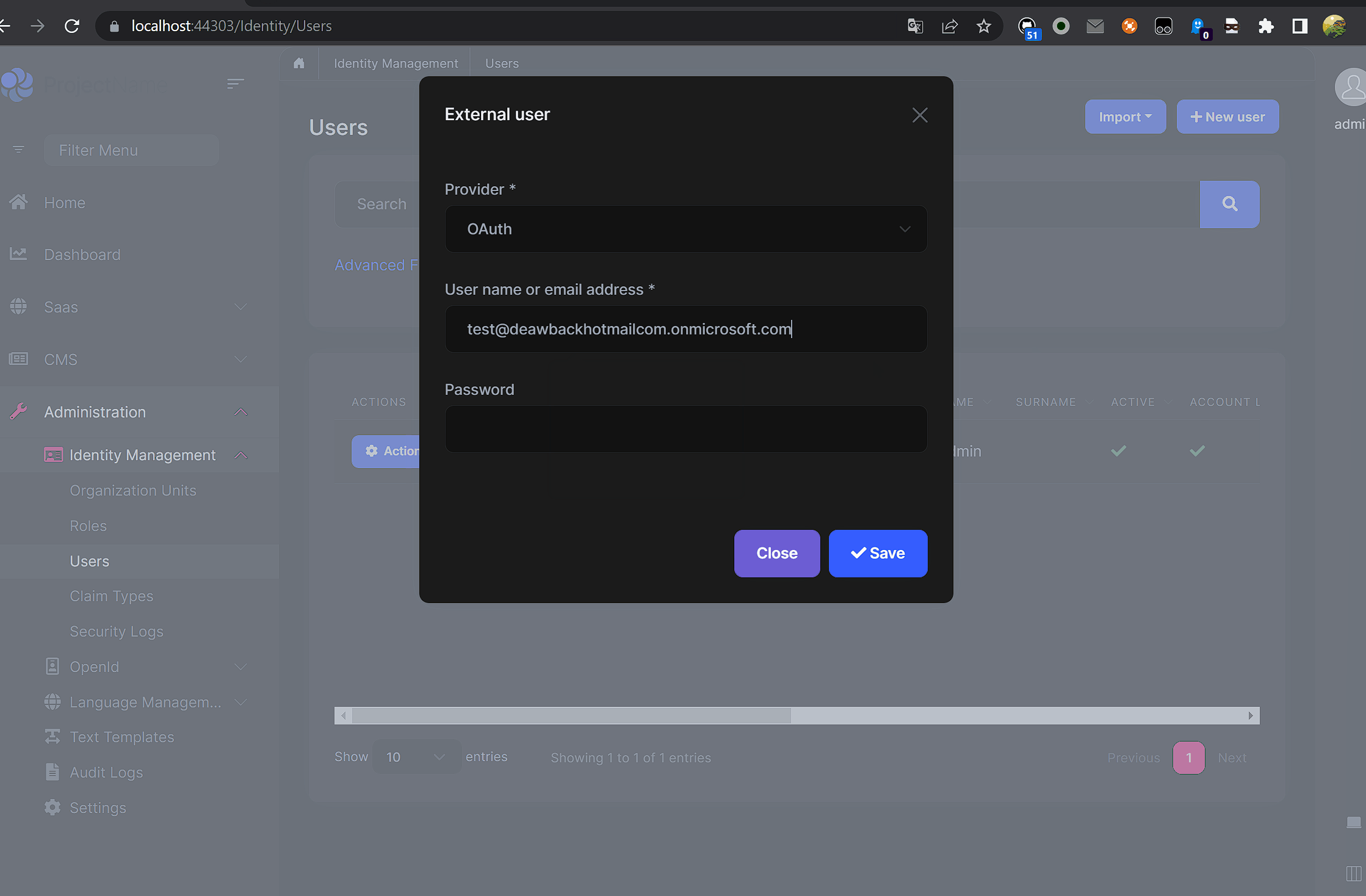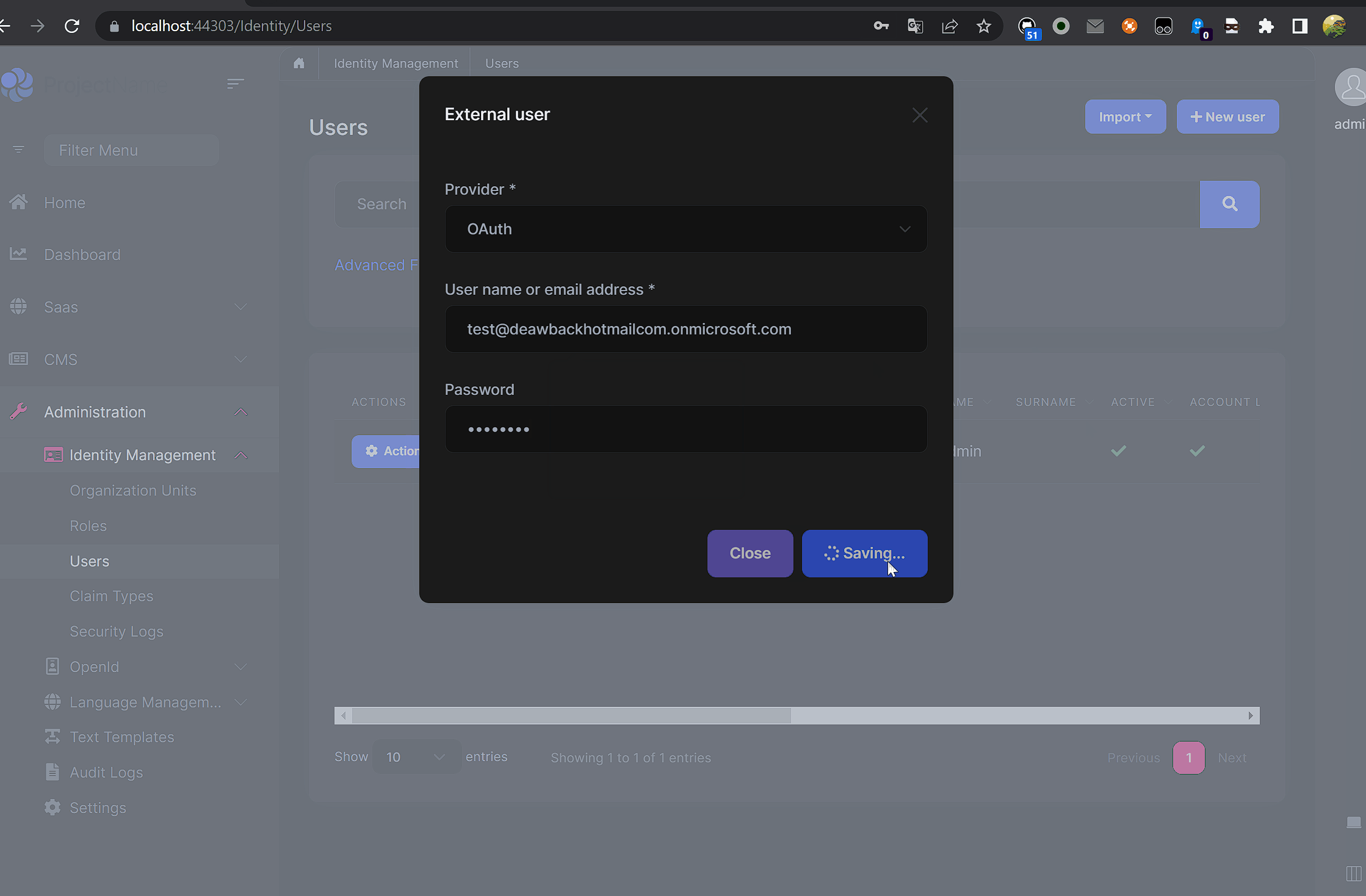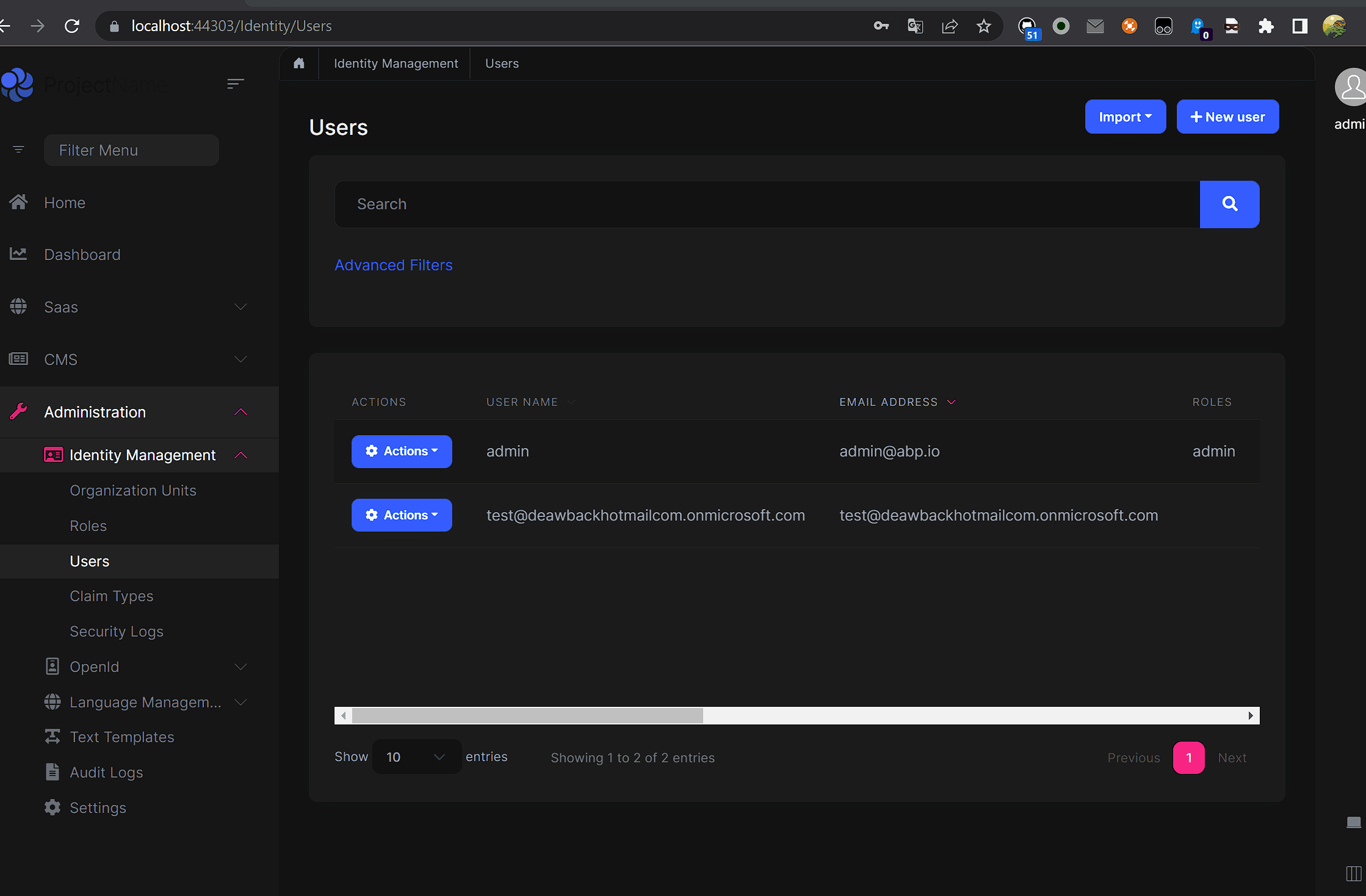
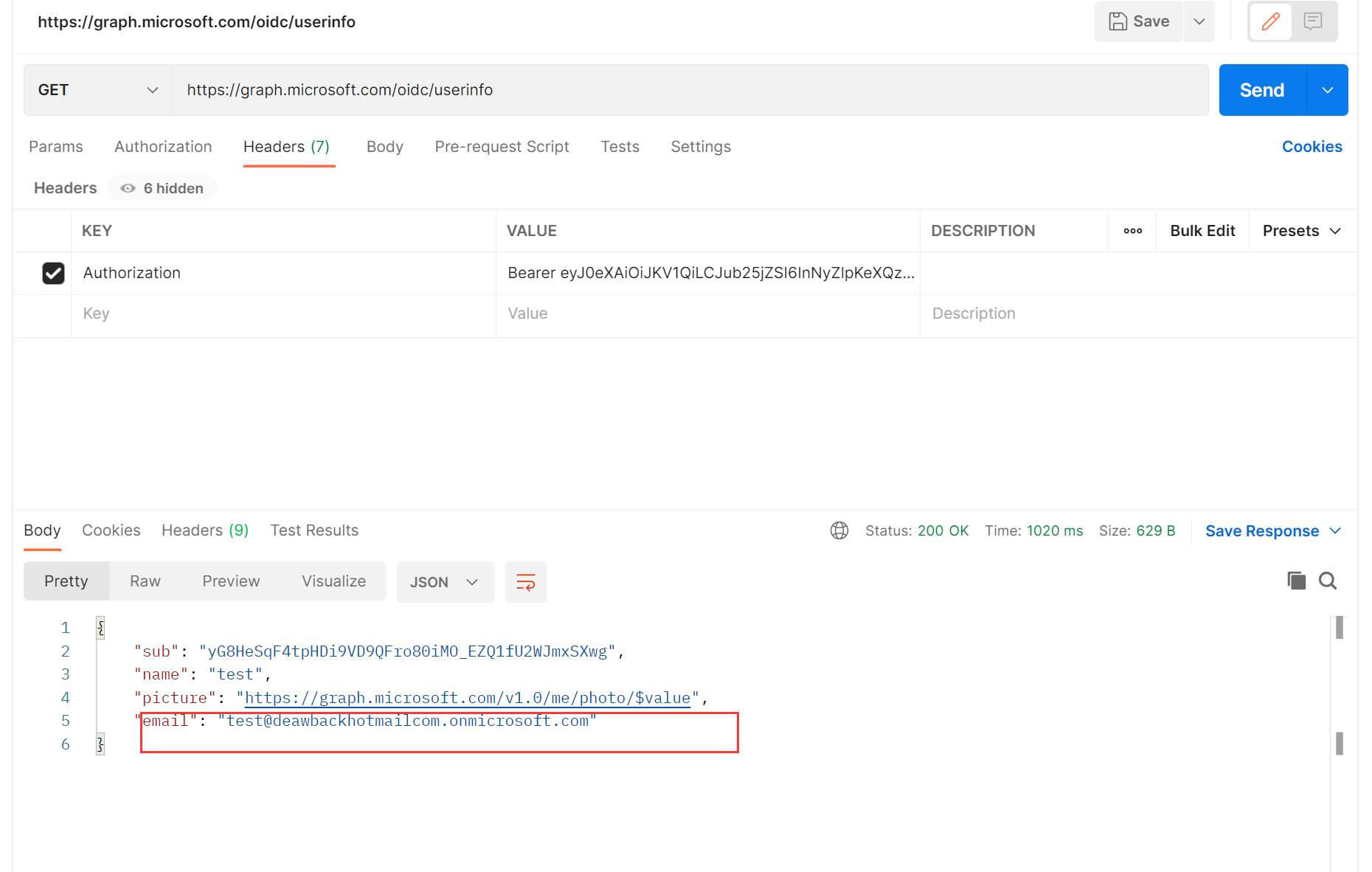
Hi all,
I am using ABP Commercial v6.0.0-rc.4, but I think there is not Bugs & Issues already open for it.
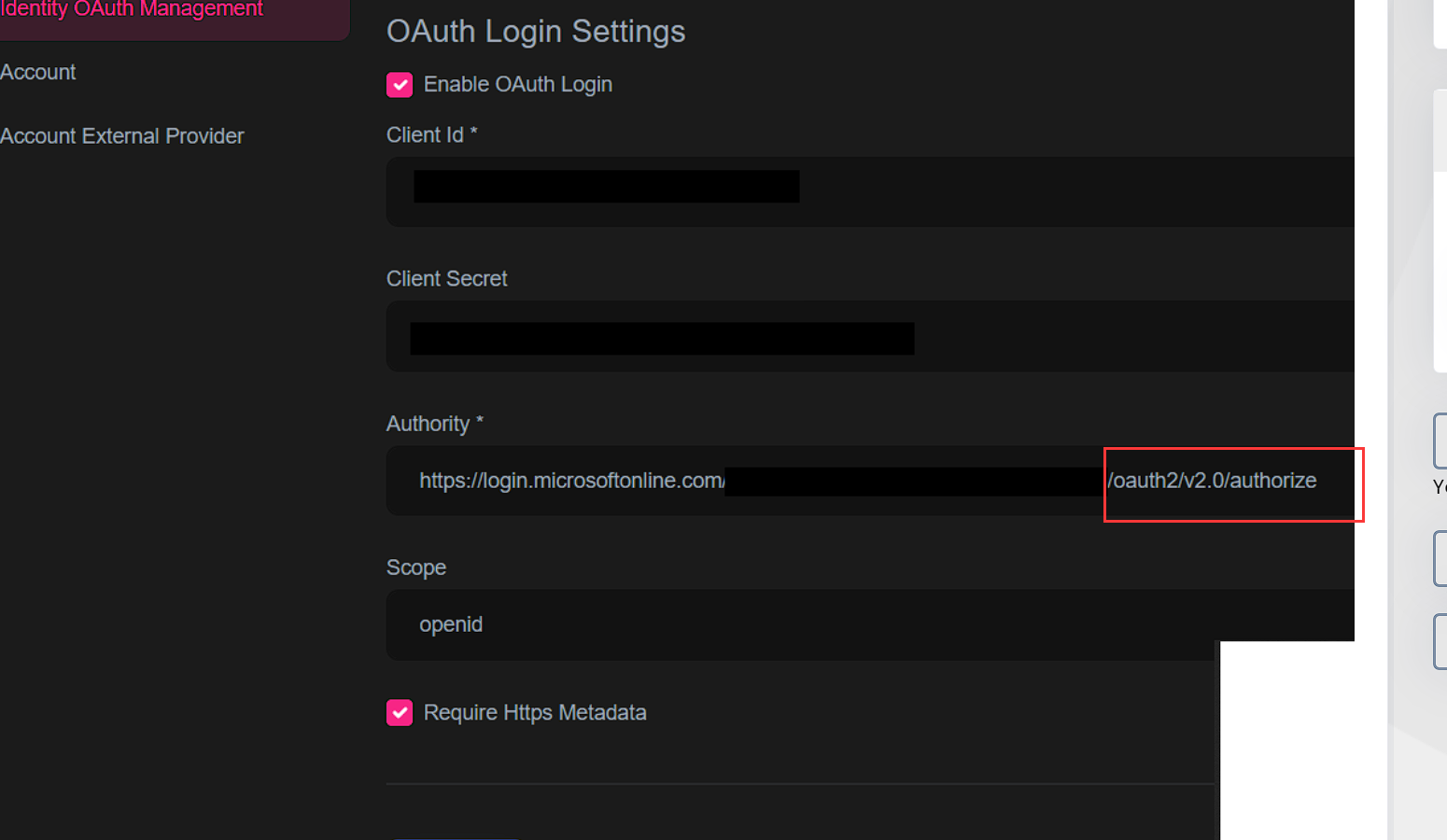
I am trying to enable OAuth external login via ABP Framework in order to be able to import users.
I followed the documentation https://docs.abp.io/en/commercial/latest/modules/identity/oauth-login to a enable OAuth. See my configuration below:
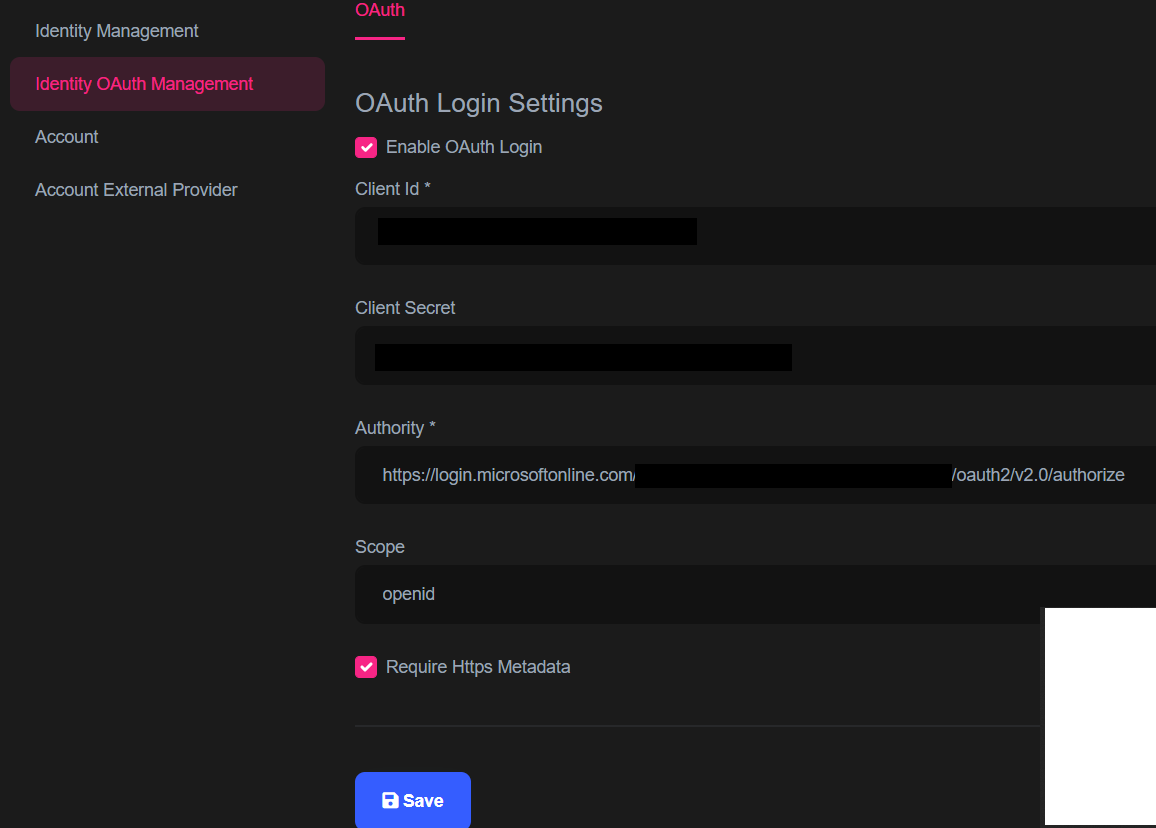
When I try to login using my Azure AD credentials or when I try import users I am getting "External provider authentication failed".
It is working via postman.
Thanks!
20 Answer(s)
-
0
-
0
Hi,
See: https://learn.microsoft.com/en-us/azure/active-directory/develop/v2-protocols-oidc#find-your-apps-openid-configuration-document-uri
The Authority should be
https://login.microsoftonline.com/{tenant}/v2.0Hi liangshiwei,
Thanks for you reply. Yes, I already tried
https://login.microsoftonline.com/{tenant}/v2.0and alsohttps://login.microsoftonline.com/{tenant}/oauth2/v2.0andhttps://login.microsoftonline.com/{tenant}All of the cases I get the same error message.
Like I said via postman it works.
-
0
Hi,
Let me explain how it works.
- First, ABP will send a request to the OpenID configuration document endpoint. (
$"{Authority}/.well-known/openid-configuration)
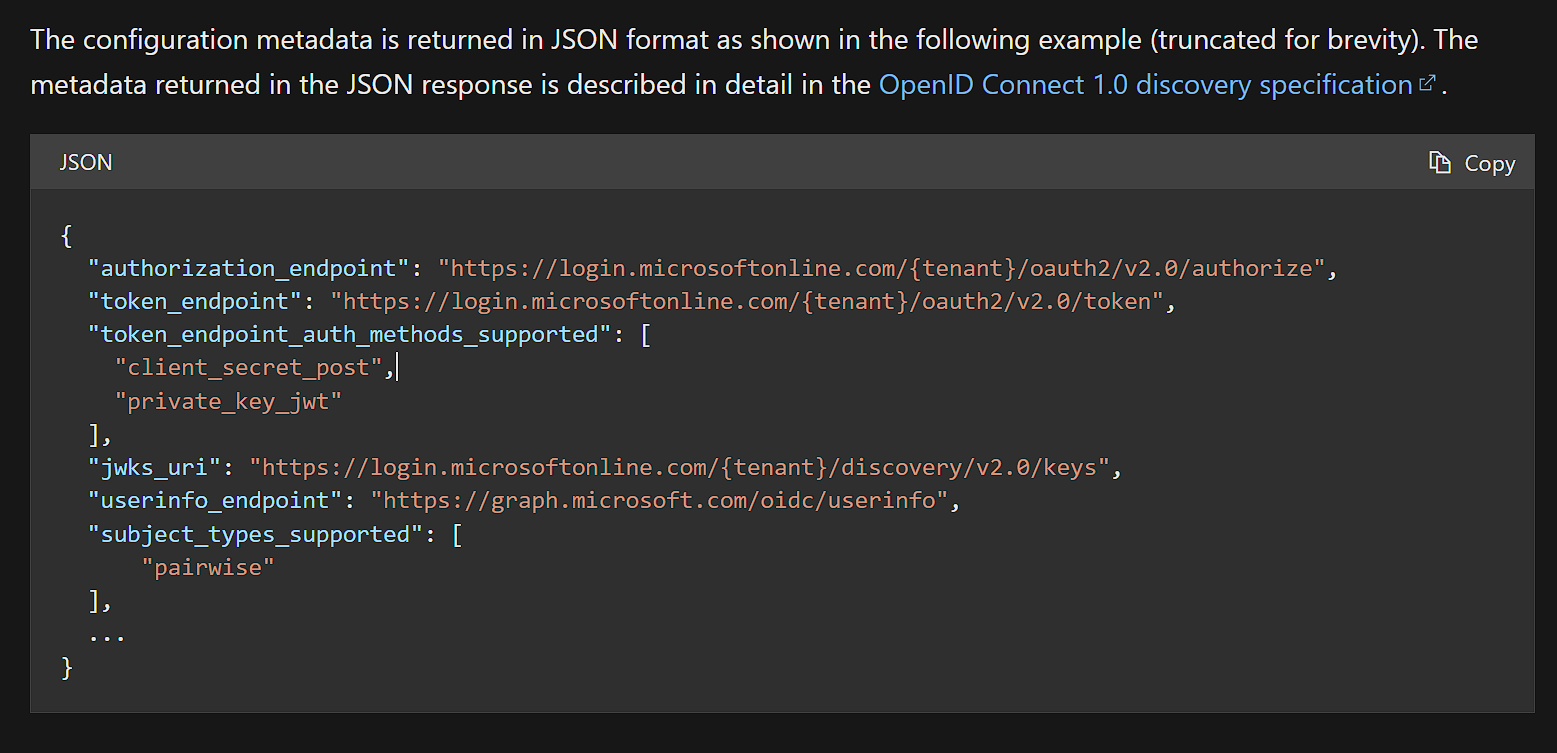
The configuration document endpoint will responsed:
- After that, ABP will use the
token_endpointto request access_token via resource-owner-password-flow
You can try access to
https://login.microsoftonline.com/{tenant}/v2.0.well-known/openid-configurationto check it.PS: Don't forget replace {tenant}.
- First, ABP will send a request to the OpenID configuration document endpoint. (
-
0
Hi,
Let me explain how it works.
- First, ABP will send a request to the OpenID configuration document endpoint. (
$"{Authority}/.well-known/openid-configuration)
The configuration document endpoint will responsed:
- After that, ABP will use the
token_endpointto request access_token via resource-owner-password-flow
You can try access to
https://login.microsoftonline.com/{tenant}/v2.0.well-known/openid-configurationto check it.PS: Don't forget replace {tenant}.
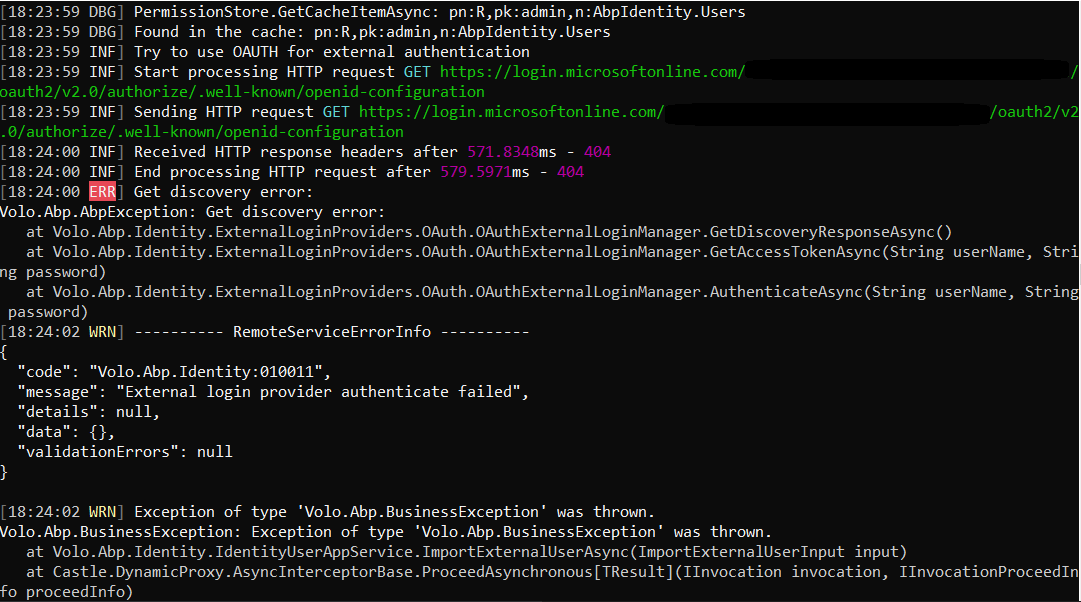
Yes, I know how openId connection works. Yes, I can access the openId configuration metadata for my tenant, also on the logs I can see the openId metadata. The error that I am getting is this:
at Volo.Abp.Identity.ExternalLoginProviders.OAuth.OAuthExternalLoginManager.GetDiscoveryResponseAsync() at Volo.Abp.Identity.ExternalLoginProviders.OAuth.OAuthExternalLoginManager.GetAccessTokenAsync(String userName, String password) at Volo.Abp.Identity.ExternalLoginProviders.OAuth.OAuthExternalLoginManager.AuthenticateAsync(String userName, String password) [11:08:22 WRN] ---------- RemoteServiceErrorInfo ---------- { "code": "Volo.Abp.Identity:010011", "message": "External login provider authenticate failed", "details": null, "data": {}, "validationErrors": null }
Once again, when I try openId connection on Postman it works.
- First, ABP will send a request to the OpenID configuration document endpoint. (
-
0
Yes, I can access the openId configuration metadata for my tenant, also on the logs I can see the openId metadata. The error that I am getting is this:
Please share the full logs, thanks.
-
0
Yes, I can access the openId configuration metadata for my tenant, also on the logs I can see the openId metadata. The error that I am getting is this:
Please share the full logs, thanks.
[11:08:19 DBG] Found in the cache: pn:R,pk:admin,n:AbpIdentity.Users [11:08:19 INF] Try to use OAUTH for external authentication [11:08:19 INF] Start processing HTTP request GET https://login.microsoftonline.com/{tenantId}/v2.0/.well-known/openid-configuration [11:08:19 INF] Sending HTTP request GET https://login.microsoftonline.com/{tenantId}/v2.0/.well-known/openid-configuration [11:08:20 INF] Received HTTP response headers after 697.5794ms - 200 [11:08:20 INF] End processing HTTP request after 697.8031ms - 200 [11:08:20 ERR] Get discovery error: {"token_endpoint":"https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/token","token_endpoint_auth_methods_supported":["client_secret_post","private_key_jwt","client_secret_basic"],"jwks_uri":"https://login.microsoftonline.com/{tenantId}/discovery/v2.0/keys","response_modes_supported":["query","fragment","form_post"],"subject_types_supported":["pairwise"],"id_token_signing_alg_values_supported":["RS256"],"response_types_supported":["code","id_token","code id_token","id_token token"],"scopes_supported":["openid","profile","email","offline_access"],"issuer":"https://login.microsoftonline.com/{tenantId}/v2.0","request_uri_parameter_supported":false,"userinfo_endpoint":"https://graph.microsoft.com/oidc/userinfo","authorization_endpoint":"https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/authorize","device_authorization_endpoint":"https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/devicecode","http_logout_supported":true,"frontchannel_logout_supported":true,"end_session_endpoint":"https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/logout","claims_supported":["sub","iss","cloud_instance_name","cloud_instance_host_name","cloud_graph_host_name","msgraph_host","aud","exp","iat","auth_time","acr","nonce","preferred_username","name","tid","ver","at_hash","c_hash","email"],"kerberos_endpoint":"https://login.microsoftonline.com/{tenantId}/kerberos","tenant_region_scope":"NA","cloud_instance_name":"microsoftonline.com","cloud_graph_host_name":"graph.windows.net","msgraph_host":"graph.microsoft.com","rbac_url":"https://pas.windows.net"} Volo.Abp.AbpException: Get discovery error: {"token_endpoint":"https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/token","token_endpoint_auth_methods_supported":["client_secret_post","private_key_jwt","client_secret_basic"],"jwks_uri":"https://login.microsoftonline.com/{tenantId}/discovery/v2.0/keys","response_modes_supported":["query","fragment","form_post"],"subject_types_supported":["pairwise"],"id_token_signing_alg_values_supported":["RS256"],"response_types_supported":["code","id_token","code id_token","id_token token"],"scopes_supported":["openid","profile","email","offline_access"],"issuer":"https://login.microsoftonline.com/{tenantId}/v2.0","request_uri_parameter_supported":false,"userinfo_endpoint":"https://graph.microsoft.com/oidc/userinfo","authorization_endpoint":"https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/authorize","device_authorization_endpoint":"https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/devicecode","http_logout_supported":true,"frontchannel_logout_supported":true,"end_session_endpoint":"https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/logout","claims_supported":["sub","iss","cloud_instance_name","cloud_instance_host_name","cloud_graph_host_name","msgraph_host","aud","exp","iat","auth_time","acr","nonce","preferred_username","name","tid","ver","at_hash","c_hash","email"],"kerberos_endpoint":"https://login.microsoftonline.com/{tenantId}/kerberos","tenant_region_scope":"NA","cloud_instance_name":"microsoftonline.com","cloud_graph_host_name":"graph.windows.net","msgraph_host":"graph.microsoft.com","rbac_url":"https://pas.windows.net"} at Volo.Abp.Identity.ExternalLoginProviders.OAuth.OAuthExternalLoginManager.GetDiscoveryResponseAsync() at Volo.Abp.Identity.ExternalLoginProviders.OAuth.OAuthExternalLoginManager.GetAccessTokenAsync(String userName, String password) at Volo.Abp.Identity.ExternalLoginProviders.OAuth.OAuthExternalLoginManager.AuthenticateAsync(String userName, String password) [11:08:22 WRN] ---------- RemoteServiceErrorInfo ---------- { "code": "Volo.Abp.Identity:010011", "message": "External login provider authenticate failed", "details": null, "data": {}, "validationErrors": null }
-
0
Hi,
I will check it out
-
0
Hi,
This is a problem, we will fix it in the 6.0 version., BTW, your ticket refunded.
For now, you can try:
[ExposeServices(typeof(OAuthExternalLoginManager))] public class MyOAuthExternalLoginManager : OAuthExternalLoginManager { public MyOAuthExternalLoginManager(IOAuthSettingProvider oAuthSettingProvider, IHttpClientFactory httpClientFactory) : base(oAuthSettingProvider, httpClientFactory) { } protected async override Task<DiscoveryDocumentResponse> GetDiscoveryResponseAsync() { using (var httpClient = HttpClientFactory.CreateClient(HttpClientName)) { var request = new DiscoveryDocumentRequest { Address = await OAuthSettingProvider.GetAuthorityAsync(), Policy = new DiscoveryPolicy { RequireHttps = await OAuthSettingProvider.GetRequireHttpsMetadataAsync(), ValidateEndpoints = false, ValidateIssuerName = false } }; var discoveryResponse = await httpClient.GetDiscoveryDocumentAsync(request); if (discoveryResponse.IsError) { throw discoveryResponse.Exception ?? new AbpException("Get discovery error: " + discoveryResponse.Raw); } return discoveryResponse; } } }``` -
0
Hi,
This is a problem, we will fix it in the 6.0 version., BTW, your ticket refunded.
For now, you can try:
Thanks!!
I am still getting an error but now it seems to be directly from the Azure Ad
12:28:37 ERR] Get access token error: {"error":"invalid_grant","error_description":"AADSTS50126: Error validating credentials due to invalid username or password.\r\nTrace ID: a7f3a95c-2848-4eac-a01f-4d0257db3d00\r\nCorrelation ID: 3000c73d-0b0d-48fb-9781-200178c2152a\r\nTimestamp: 2022-09-29 10:28:28Z","error_codes":[50126],"timestamp":"2022-09-29 10:28:28Z","trace_id":"a7f3a95c-2848-4eac-a01f-4d0257db3d00","correlation_id":"3000c73d-0b0d-48fb-9781-200178c2152a","error_uri":"https://login.microsoftonline.com/error?code=50126"} Volo.Abp.AbpException: Get access token error: {"error":"invalid_grant","error_description":"AADSTS50126: Error validating credentials due to invalid username or password.\r\nTrace ID: a7f3a95c-2848-4eac-a01f-4d0257db3d00\r\nCorrelation ID: 3000c73d-0b0d-48fb-9781-200178c2152a\r\nTimestamp: 2022-09-29 10:28:28Z","error_codes":[50126],"timestamp":"2022-09-29 10:28:28Z","trace_id":"a7f3a95c-2848-4eac-a01f-4d0257db3d00","correlation_id":"3000c73d-0b0d-48fb-9781-200178c2152a","error_uri":"https://login.microsoftonline.com/error?code=50126"} at Volo.Abp.Identity.ExternalLoginProviders.OAuth.OAuthExternalLoginManager.GetAccessTokenAsync(String userName, String password) at Volo.Abp.Identity.ExternalLoginProviders.OAuth.OAuthExternalLoginManager.AuthenticateAsync(String userName, String password)
Maybe it is missing pass the grant_type
-
0
Hi,
Get access token error: {"error":"invalid_grant","error_description":"AADSTS50126: Error validating credentials due to invalid username or password.\r\nTrace ID: a7f3a95c-2848-4eac-a01f-4d0257db3d00\r\nCorrelation ID.
I guess the username or password is incorrect, could you provide an azure ad test configuration with me via email? shiwei.liang@volosoft.com
I can check it and quickly fix it.
-
0
Hi,
Get access token error: {"error":"invalid_grant","error_description":"AADSTS50126: Error validating credentials due to invalid username or password.\r\nTrace ID: a7f3a95c-2848-4eac-a01f-4d0257db3d00\r\nCorrelation ID.
I guess the username or password is incorrect, could you provide an azure ad test configuration with me via email? shiwei.liang@volosoft.com
I can check it and quickly fix it.
The login works (when I login using my Azure Ad credentials). The error is just on the import users.
As the login works, I assume the setups for the OAuth are all good. Does that make sense?
-
0
Hi,
Did you provide the password when you import a user?
-
0
Hi,
Did you provide the password when you import a user?
I tried with and without, both the same error. it is a bit weird that I need to provide the password of the user that I am trying to import.
-
0
it is a bit weird that I need to provide the password of the user that I am trying to import.
Yes, but it's a limit of OAuth, we have to provide a username and password to check if the user is valid.
-
0
-
0
it is a bit weird that I need to provide the password of the user that I am trying to import.
Yes, but it's a limit of OAuth, we have to provide a username and password to check if the user is valid.
That means that I need to know the user password?!?!
-
0
After my check, it should work after https://support.abp.io/QA/Questions/3761#answer-3f02f82f-0c97-563c-cab8-3a069adc445c
I am using that change, but still not working for me.
Tips: ABP needs to get the email to create a user. you can check the user info endpoint.
I am not sure what you mean. I am trying to import uses that already exist on Azure Ad by using the email and the current password, but still not working for me. Am I doing something wrong?
-
0
Hi,
That means that I need to know the user password?!?!
Unfortunately, yes.
This is the resource-owner-password-flow rule.
I am trying to import uses that already exist on Azure Ad by using the email and the current password, but still not working for me. Am I doing something wrong?
Could you provide the azure ad configuration(clientid,secret... and a test account) to me via email? shiwei.liang@volosoft.com
-
0
Hi,
That means that I need to know the user password?!?!
Unfortunately, yes.
Sorry, but if to use the import external user feature it requires to know the user password, the feature is not really useful for us. I would like to import the user so before the user login he/she setting like role, for example, will be already set.
-
0
Hi,
This is a limit of OAuth: https://auth0.com/docs/get-started/authentication-and-authorization-flow/resource-owner-password-flow
I think the OAuth external login provider is not suite for you. you can custom your own provider.
Maybe Azure provides an HTTP API that can search users(I'm not sure.)
public class MyAzureAdExternalLoginProvider : ExternalLoginProviderBase, ITransientDependency { public const string Name = "AzureAd"; public MyAzureAdExternalLoginProvider() : base(....) { } public async override Task<bool> TryAuthenticateAsync(string userName, string plainPassword) { .... } public async override Task<bool> IsEnabledAsync() { ..... } protected async override Task<ExternalLoginUserInfo> GetUserInfoAsync(string userName) { //Use the username to send an HTTP request to Azure API to query a user. } } Configure<AbpIdentityOptions>(options => { options.ExternalLoginProviders.Add<MyAzureAdExternalLoginProvider>(MyAzureAdExternalLoginProvider.Name); });