Check the docs before asking a question: https://docs.abp.io/en/commercial/latest/ Check the samples, to see the basic tasks: https://docs.abp.io/en/commercial/latest/samples/index The exact solution to your question may have been answered before, please use the search on the homepage.
If you're creating a bug/problem report, please include followings:
- ABP Framework version: v5.2.2
- UI type: Angular
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): yes
- Exception message and stack trace:
- Steps to reproduce the issue: 'yarn install' then 'yarn start' the angular project
Hi There,
I am having an issue with the login button on the Angular project, it does not work in production mode as it does not redirect me to the AuthServer login page and it looks like it is not firing any events either.
There is no errors being thrown by any of the services (Auth, Identity, Saas, Admin etc). Please send me your email address so that I can share the environment.prod.ts file and also send you the URL of the site so you can see the issue at play.
5 Answer(s)
-
0
Hello,
Can you send
/.well-known/openid-configurationendpoint response? -
0
Hi,
Here is my /.well-known/openid-configuration
{ "issuer": "http://xxx-authserver.conlog.com/", "authorization_endpoint": "http://xxx-authserver.conlog.com/connect/authorize", "token_endpoint": "http://xxx-authserver.conlog.com/connect/token", "introspection_endpoint": "http://xxx-authserver.conlog.com/connect/introspect", "end_session_endpoint": "http://xxx-authserver.conlog.com/connect/logout", "revocation_endpoint": "http://xxx-authserver.conlog.com/connect/revocat", "userinfo_endpoint": "http://xxx-authserver.conlog.com/connect/userinfo", "device_authorization_endpoint": "http://xxx-authserver.conlog.com/device", "jwks_uri": "http://xxx-authserver.conlog.com/.well-known/jwks", "grant_types_supported": [ "authorization_code", "implicit", "password", "client_credentials", "refresh_token", "urn:ietf:params:oauth:grant-type:device_code", "LinkLogin", "Impersonation" ], "response_types_supported": [ "code", "code id_token", "code id_token token", "code token", "id_token", "id_token token", "token", "none" ], "response_modes_supported": [ "form_post", "fragment", "query" ], "scopes_supported": [ "openid", "offline_access", "email", "profile", "phone", "roles", "address" ], "claims_supported": [ "aud", "exp", "iat", "iss", "sub" ], "id_token_signing_alg_values_supported": [ "RS256" ], "code_challenge_methods_supported": [ "S256" ], "subject_types_supported": [ "public" ], "token_endpoint_auth_methods_supported": [ "client_secret_basic", "client_secret_post" ], "introspection_endpoint_auth_methods_supported": [ "client_secret_basic", "client_secret_post" ], "revocation_endpoint_auth_methods_supported": [ "client_secret_basic", "client_secret_post" ], "claims_parameter_supported": false, "request_parameter_supported": false, "request_uri_parameter_supported": false }
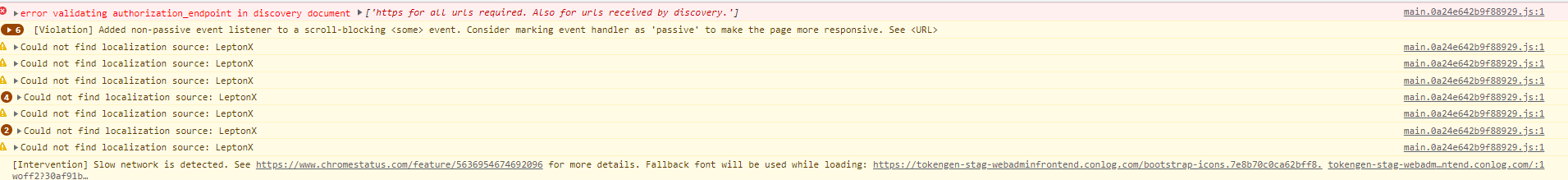
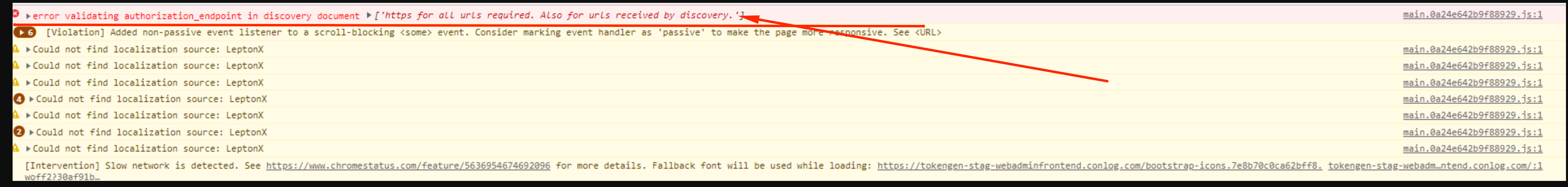
<br> I have noticed that the discovery document is returning urls in http rather than https.
In the angular project, my issuer is set to use https: const oAuthConfig = { issuer: 'https://xxx-stag-authserver.conlog.com', redirectUri: baseUrl, clientId: 'TokenGen_Angular', responseType: 'code', scope: 'offline_access openid profile email phone AuthServer AccountService IdentityService AdministrationService SaasService ProductService StsApiService', strictDiscoveryDocumentValidation: false, skipIssuerCheck: true, requireHttps: true, };
-
0
Hi
Since we don't know anything about your environment, I can't say something clearly. But it seems it's related to your deployment scenario.
I can only suggest this method in microsoft's document: https://learn.microsoft.com/en-us/aspnet/core/host-and-deploy/proxy-load-balancer?view=aspnetcore-7.0#when-it-isnt-possible-to-add-forwarded-headers-and-all-requests-are-secure
Also the following article may make easy to understand the situation that you faced: https://codeopinion.com/configuring-asp-net-core-behind-a-load-balancer/
-
0
Hi,
Here is my /.well-known/openid-configuration
{ "issuer": "http://xxx-authserver.conlog.com/", "authorization_endpoint": "http://xxx-authserver.conlog.com/connect/authorize", "token_endpoint": "http://xxx-authserver.conlog.com/connect/token", "introspection_endpoint": "http://xxx-authserver.conlog.com/connect/introspect", "end_session_endpoint": "http://xxx-authserver.conlog.com/connect/logout", "revocation_endpoint": "http://xxx-authserver.conlog.com/connect/revocat", "userinfo_endpoint": "http://xxx-authserver.conlog.com/connect/userinfo", "device_authorization_endpoint": "http://xxx-authserver.conlog.com/device", "jwks_uri": "http://xxx-authserver.conlog.com/.well-known/jwks", "grant_types_supported": [ "authorization_code", "implicit", "password", "client_credentials", "refresh_token", "urn:ietf:params:oauth:grant-type:device_code", "LinkLogin", "Impersonation" ], "response_types_supported": [ "code", "code id_token", "code id_token token", "code token", "id_token", "id_token token", "token", "none" ], "response_modes_supported": [ "form_post", "fragment", "query" ], "scopes_supported": [ "openid", "offline_access", "email", "profile", "phone", "roles", "address" ], "claims_supported": [ "aud", "exp", "iat", "iss", "sub" ], "id_token_signing_alg_values_supported": [ "RS256" ], "code_challenge_methods_supported": [ "S256" ], "subject_types_supported": [ "public" ], "token_endpoint_auth_methods_supported": [ "client_secret_basic", "client_secret_post" ], "introspection_endpoint_auth_methods_supported": [ "client_secret_basic", "client_secret_post" ], "revocation_endpoint_auth_methods_supported": [ "client_secret_basic", "client_secret_post" ], "claims_parameter_supported": false, "request_parameter_supported": false, "request_uri_parameter_supported": false }
<br> I have noticed that the discovery document is returning urls in http rather than https.
In the angular project, my issuer is set to use https: const oAuthConfig = { issuer: 'https://xxx-stag-authserver.conlog.com', redirectUri: baseUrl, clientId: 'TokenGen_Angular', responseType: 'code', scope: 'offline_access openid profile email phone AuthServer AccountService IdentityService AdministrationService SaasService ProductService StsApiService', strictDiscoveryDocumentValidation: false, skipIssuerCheck: true, requireHttps: true, };
By default, the Openiddict accepts only accepts HTTPS requests. It seems the problem is this.
you can disabled the "https required rule" https://support.abp.io/QA/Questions/3816/How-to-disable-https-in-openiddict
-
0
Hi,
Thank you for the support. I have managed to sort out the issue by adding the below in my auth and identity service.
app.Use((context, next) => { context.Request.Scheme = "https"; return next(context); });