27 Answer(s)
-
0
hi
- Please share a test access_token
- Please share the Debug logs of your API call.
- Please set a breakpoint to see the current claims of the API call.
public class Program { public async static Task<int> Main(string[] args) { Log.Logger = new LoggerConfiguration() .MinimumLevel.Debug() .MinimumLevel.Override("Microsoft.EntityFrameworkCore", LogEventLevel.Warning) .Enrich.FromLogContext() .WriteTo.Async(c => c.File("Logs/logs.txt")) .WriteTo.Async(c => c.Console()) .CreateLogger();https://abp.io/community/articles/how-claim-type-works-in-asp-net-core-and-abp-framework-km5dw6g1
Thanks.
-
0
hi
Identity service logs
Please share a test access_token
Please set the log level as Debug and share full logs of
Identity service logs
public class Program { public async static Task<int> Main(string[] args) { Log.Logger = new LoggerConfiguration() .MinimumLevel.Debug() .MinimumLevel.Override("Microsoft.EntityFrameworkCore", LogEventLevel.Warning) .Enrich.FromLogContext() .WriteTo.Async(c => c.File("Logs/logs.txt")) .WriteTo.Async(c => c.Console()) .CreateLogger();```- Please set a breakpoint in
Identity serviceproject to see the current claims of theapi/identity-service/user-account/GetPAuthWithPermissioncall.
-
0
hi
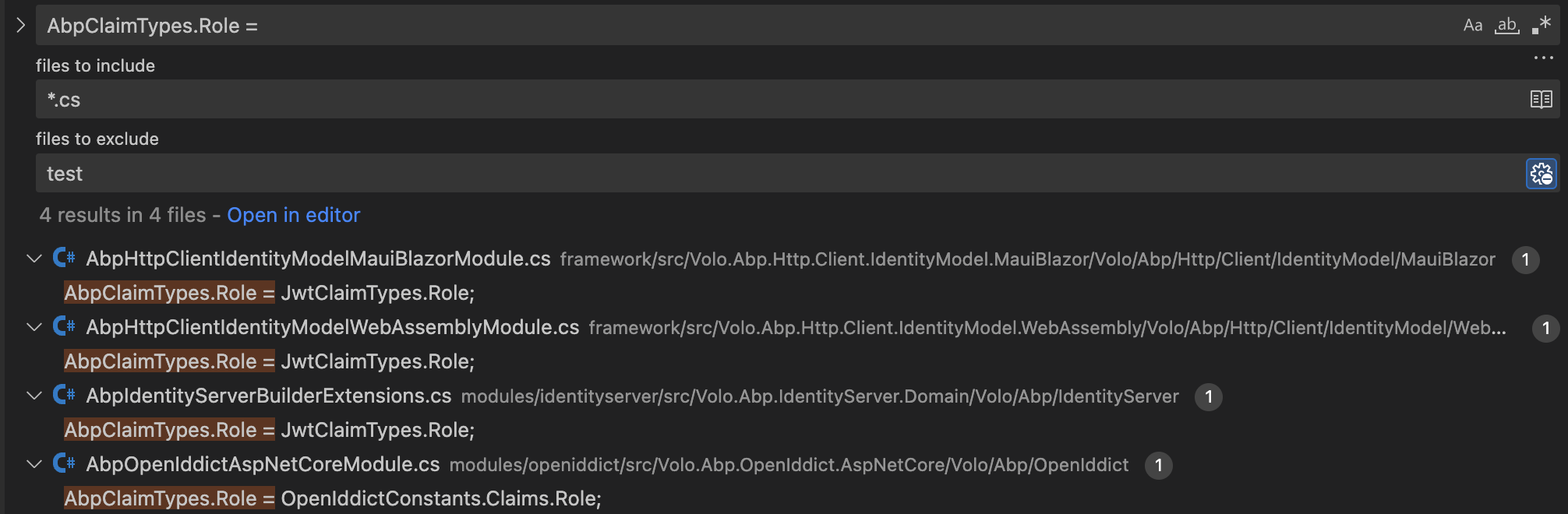
The
roletype in claims isClaimTypes.Role(http://schemas.microsoft.com/ws/2008/06/identity/claims/role)Please check the
typeValueofAbpClaimTypes.Rolevar typeValue = AbpClaimTypes.RoletypeValue should be http://schemas.microsoft.com/ws/2008/06/identity/claims/role{ "Type": "http://schemas.microsoft.com/ws/2008/06/identity/claims/role", "Value": "admin" }
If the
typeValueisrole, that's mean your claim type is incorrect.
Please also check the
RolesofCurrentUser, if theRolesis empty, it is also the problem of claim type.Thanks.
-
0
hi
Please share the content of
IdentityServicehost module. It may beIdentityServiceModuleorIdentityServiceHostModule -
0
liming.ma@volosoft.com
-
0
-
0
hi
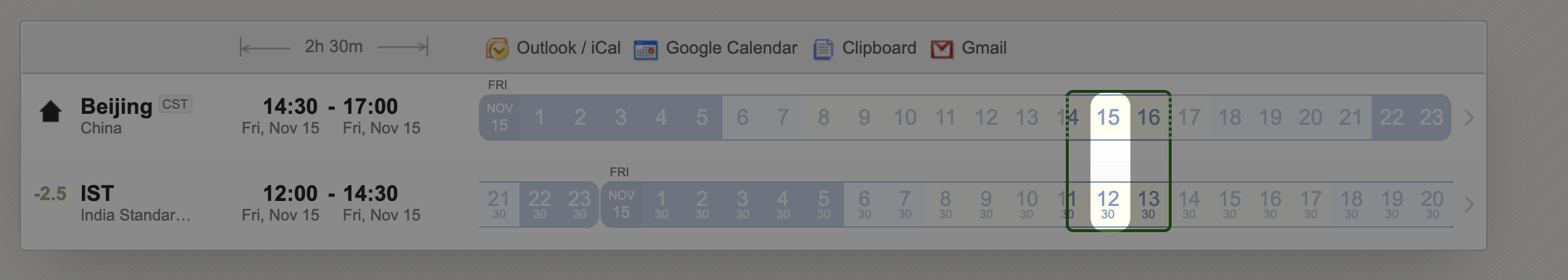
I can remote-check your app at https://www.worldtimebuddy.com/?qm=1&lid=1816670&h=1816670&date=2024-11-14&sln=10-17&hf=0
Please send your time to liming.ma@volosoft.com
I will share the zoom link.
-
0
hi
https://us05web.zoom.us/j/84770432055?pwd=u9f1aiz1EIE2beTZWXVLNpwOaWlz0j.1
-
0
-
0
maliming is inviting you to a scheduled Zoom meeting.
Topic: maliming's Zoom Meeting Time: Nov 15, 2024 15:00 Beijing, Shanghai
Join Zoom Meeting https://us05web.zoom.us/j/82434243267?pwd=utBSiIrsyBIXZbJDJnkfbwZ9MJBhZu.1
Meeting ID: 824 3424 3267 Passcode: 7Npsyq
-
0
hi
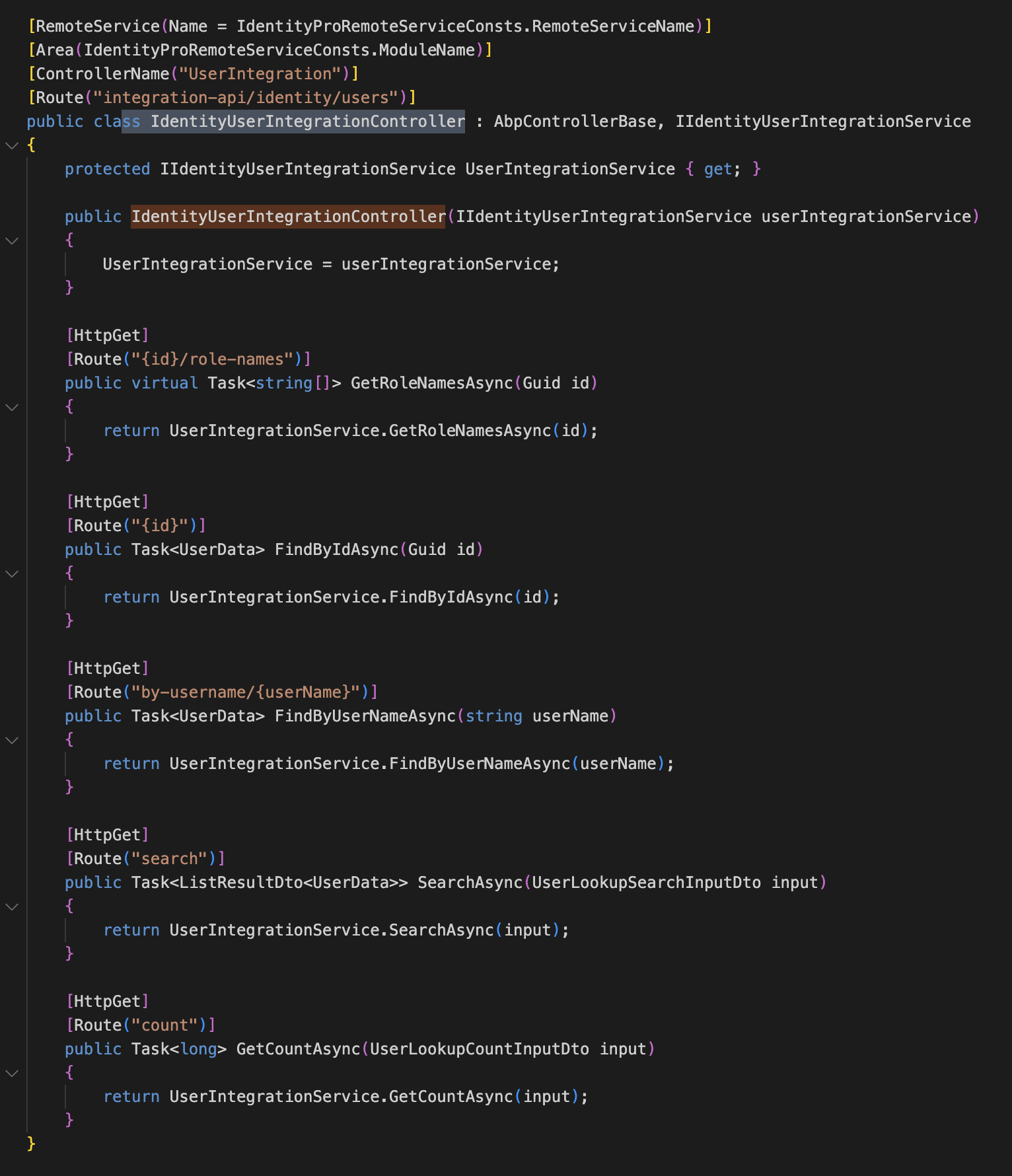
Autofac.Core.DependencyResolutionException: An exception was thrown while activating Volo.Abp.PermissionManagement.Identity.RolePermissionManagementProvider -> Volo.Abp.Identity.HttpClientUserRoleFinder. ---> Autofac.Core.DependencyResolutionException: None of the constructors found on type 'Volo.Abp.Identity.HttpClientUserRoleFinder' can be invoked with the available services and parameters: Cannot resolve parameter 'Volo.Abp.Identity.Integration.IIdentityUserIntegrationService userIntegrationService' of constructor 'Void .ctor(Volo.Abp.Identity.IIdentityUserAppService, Volo.Abp.Identity.Integration.IIdentityUserIntegrationService)'.To use
IIdentityUserIntegrationService, you have to depend onAbpIdentityApplicationModule -
0
hi
Can you get the full
Logs.txtfile of yourIdentityServiceHttpApiHostModule? then send it to liming.ma@volosoft.comThanks.
-
0
hi
Have you depended on
AbpIdentityHttpApiClientModulein youradministration-service?You shouldn't depend on
AbpIdentityHttpApiClientModule.Please share the full
logs.txtfile. liming.ma@volosoft.comYou can delete the
logs.txtfile. Then startadministration-serviceagain, reproduce the problem and share thelogs.txt.Thanks.
-
0
Please share the full logs.txt file. liming.ma@volosoft.com You can delete the logs.txt file. Then start administration-service again, reproduce the problem and share the logs.txt. Thanks.
-
0
hi
Your logs are not complete.
Please share the logs that include app starting.
I need the module load list logs.
-
0
hi Your
UrvinFinance.AdministrationService.AdministrationServiceHttpApiHostModuleis depending on theVolo.Abp.Identity.AbpIdentityHttpApiClientModule.Please check the code of
AdministrationServiceHttpApiHostModuleclass.{ "Timestamp":"2024-11-15T13:34:11.5610752+00:00", "Level":"Information", "MessageTemplate":" - Volo.Abp.Identity.AbpIdentityHttpApiClientModule", "RenderedMessage":" - Volo.Abp.Identity.AbpIdentityHttpApiClientModule", "Properties":{ "SourceContext":"Volo.Abp.AbpApplicationBase", "dd_span_id":"0", "dd_trace_id":"0", "dd_version":"", "dd_service":"UrvinFinance.AdministrationService.HttpApi.Host", "dd_env":"", "Application":"UrvinFinance.AdministrationService.HttpApi.Host" } }See the last line
---|Volo.Abp.Identity.AbpIdentityHttpApiClientModule:Starting UrvinFinance.AdministrationService.HttpApi.Host. Loaded ABP modules: UrvinFinance.AdministrationService.AdministrationServiceHttpApiHostModule ---|UrvinFinance.UrvinFinanceSharedLocalizationModule ---|---|Volo.Abp.Validation.AbpValidationModule ---|---|---|Volo.Abp.Validation.AbpValidationAbstractionsModule ---|---|---|Volo.Abp.Localization.AbpLocalizationModule ---|---|---|---|Volo.Abp.VirtualFileSystem.AbpVirtualFileSystemModule ---|---|---|---|Volo.Abp.Settings.AbpSettingsModule ---|---|---|---|---|Volo.Abp.Localization.AbpLocalizationAbstractionsModule ---|---|---|---|---|Volo.Abp.Security.AbpSecurityModule ---|---|---|---|---|Volo.Abp.Data.AbpDataModule ---|---|---|---|---|---|Volo.Abp.ObjectExtending.AbpObjectExtendingModule ---|---|---|---|---|---|Volo.Abp.Uow.AbpUnitOfWorkModule ---|---|---|---|---|---|Volo.Abp.EventBus.Abstractions.AbpEventBusAbstractionsModule ---|---|---|---|Volo.Abp.Threading.AbpThreadingModule ---|Volo.Abp.Http.Client.IdentityModel.Web.AbpHttpClientIdentityModelWebModule ---|---|Volo.Abp.Http.Client.IdentityModel.AbpHttpClientIdentityModelModule ---|---|---|Volo.Abp.Http.Client.AbpHttpClientModule ---|---|---|---|Volo.Abp.Http.AbpHttpModule ---|---|---|---|---|Volo.Abp.Http.AbpHttpAbstractionsModule ---|---|---|---|---|Volo.Abp.Json.AbpJsonModule ---|---|---|---|---|---|Volo.Abp.Json.SystemTextJson.AbpJsonSystemTextJsonModule ---|---|---|---|---|---|---|Volo.Abp.Json.AbpJsonAbstractionsModule ---|---|---|---|---|---|---|Volo.Abp.Timing.AbpTimingModule ---|---|---|---|---|Volo.Abp.Minify.AbpMinifyModule ---|---|---|---|Volo.Abp.Castle.AbpCastleCoreModule ---|---|---|---|Volo.Abp.MultiTenancy.AbpMultiTenancyModule ---|---|---|---|---|Volo.Abp.MultiTenancy.AbpMultiTenancyAbstractionsModule ---|---|---|---|Volo.Abp.ExceptionHandling.AbpExceptionHandlingModule ---|---|---|---|Volo.Abp.RemoteServices.AbpRemoteServicesModule ---|---|---|---|Volo.Abp.EventBus.AbpEventBusModule ---|---|---|---|---|Volo.Abp.Guids.AbpGuidsModule ---|---|---|---|---|Volo.Abp.BackgroundWorkers.AbpBackgroundWorkersModule ---|---|---|---|---|Volo.Abp.DistributedLocking.AbpDistributedLockingAbstractionsModule ---|---|---|Volo.Abp.IdentityModel.AbpIdentityModelModule ---|---|---|---|Volo.Abp.Caching.AbpCachingModule ---|---|---|---|---|Volo.Abp.Serialization.AbpSerializationModule ---|Volo.Abp.AspNetCore.Mvc.UI.MultiTenancy.AbpAspNetCoreMvcUiMultiTenancyModule ---|---|Volo.Abp.AspNetCore.Mvc.UI.Theme.Shared.AbpAspNetCoreMvcUiThemeSharedModule ---|---|---|Volo.Abp.AspNetCore.Mvc.UI.Bootstrap.AbpAspNetCoreMvcUiBootstrapModule ---|---|---|---|Volo.Abp.AspNetCore.Mvc.UI.AbpAspNetCoreMvcUiModule ---|---|---|---|---|Volo.Abp.AspNetCore.Mvc.AbpAspNetCoreMvcModule ---|---|---|---|---|---|Volo.Abp.AspNetCore.AbpAspNetCoreModule ---|---|---|---|---|---|---|Volo.Abp.Auditing.AbpAuditingModule ---|---|---|---|---|---|---|---|Volo.Abp.Auditing.AbpAuditingContractsModule ---|---|---|---|---|---|---|Volo.Abp.Authorization.AbpAuthorizationModule ---|---|---|---|---|---|---|---|Volo.Abp.Authorization.AbpAuthorizationAbstractionsModule ---|---|---|---|---|---|Volo.Abp.ApiVersioning.AbpApiVersioningAbstractionsModule ---|---|---|---|---|---|Volo.Abp.AspNetCore.Mvc.AbpAspNetCoreMvcContractsModule ---|---|---|---|---|---|---|Volo.Abp.Application.AbpDddApplicationContractsModule ---|---|---|---|---|---|Volo.Abp.UI.Navigation.AbpUiNavigationModule ---|---|---|---|---|---|---|Volo.Abp.UI.AbpUiModule ---|---|---|---|---|---|Volo.Abp.GlobalFeatures.AbpGlobalFeaturesModule ---|---|---|---|---|---|Volo.Abp.Application.AbpDddApplicationModule ---|---|---|---|---|---|---|Volo.Abp.Domain.AbpDddDomainModule ---|---|---|---|---|---|---|---|Volo.Abp.ObjectMapping.AbpObjectMappingModule ---|---|---|---|---|---|---|---|Volo.Abp.Specifications.AbpSpecificationsModule ---|---|---|---|---|---|---|---|Volo.Abp.Domain.AbpDddDomainSharedModule ---|---|---|---|---|---|---|Volo.Abp.Features.AbpFeaturesModule ---|---|---|Volo.Abp.AspNetCore.Mvc.UI.Packages.AbpAspNetCoreMvcUiPackagesModule ---|---|---|---|Volo.Abp.AspNetCore.Mvc.UI.Bundling.AbpAspNetCoreMvcUiBundlingAbstractionsModule ---|---|---|Volo.Abp.AspNetCore.Mvc.UI.Widgets.AbpAspNetCoreMvcUiWidgetsModule ---|---|---|---|Volo.Abp.AspNetCore.Mvc.UI.Bundling.AbpAspNetCoreMvcUiBundlingModule ---|---|Volo.Abp.AspNetCore.MultiTenancy.AbpAspNetCoreMultiTenancyModule ---|Volo.Abp.Identity.AbpIdentityHttpApiClientModule -
0
-
0
hi
Please share full logs again
Thanks.
-
0
hi
I have checked your logs. But there are no
error/exceptionlogs in it.Please share the logs that contains the
Internal Server ErrorThanks.
-
0
hi
The error:
An exception was thrown while activating UrvinFinance.IdentityService.User.UserController -> UrvinFinance.IdentityService.UserProfileSettings.UserProfileAppService. Cannot resolve parameter 'UrvinFinance.PaymentService.Subscriptions.ISubscriptionAppService subscriptionAppService'You should depend on the
ISubscriptionAppServiceimplement module.eg
XXXApplicationModule -
0
hi
The error is:
System.TypeLoadException: Method 'Handle' in type 'UrvinFinance.ImageService.Behaviour.ValidationBehavior2' from assembly 'UrvinFinance.ImageService.Application, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null' does not have an implementation. C:\Step2gen\urvinfinance\services\identity\src\UrvinFinance.IdentityService.HttpApi.Host\Program.cs:line 80Please check your
UrvinFinance.ImageService.Applicationproject.You can also try to run
abp cleancommand and build & run again.The error is not about abp framework.
Thanks.
-
0
hi
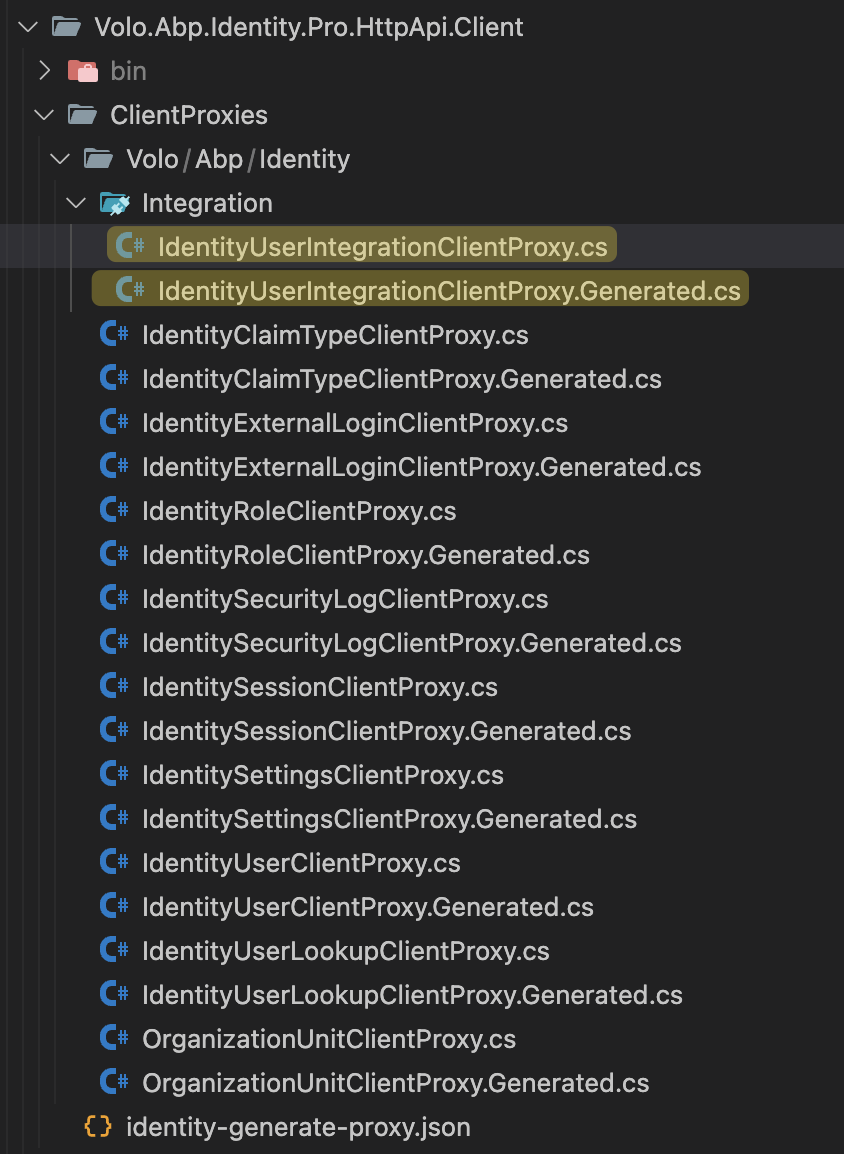
Try to pass the
-mto specify the module name.abp generate-proxy -t csharp -m identity --url http://localhost:44388/Remember to set
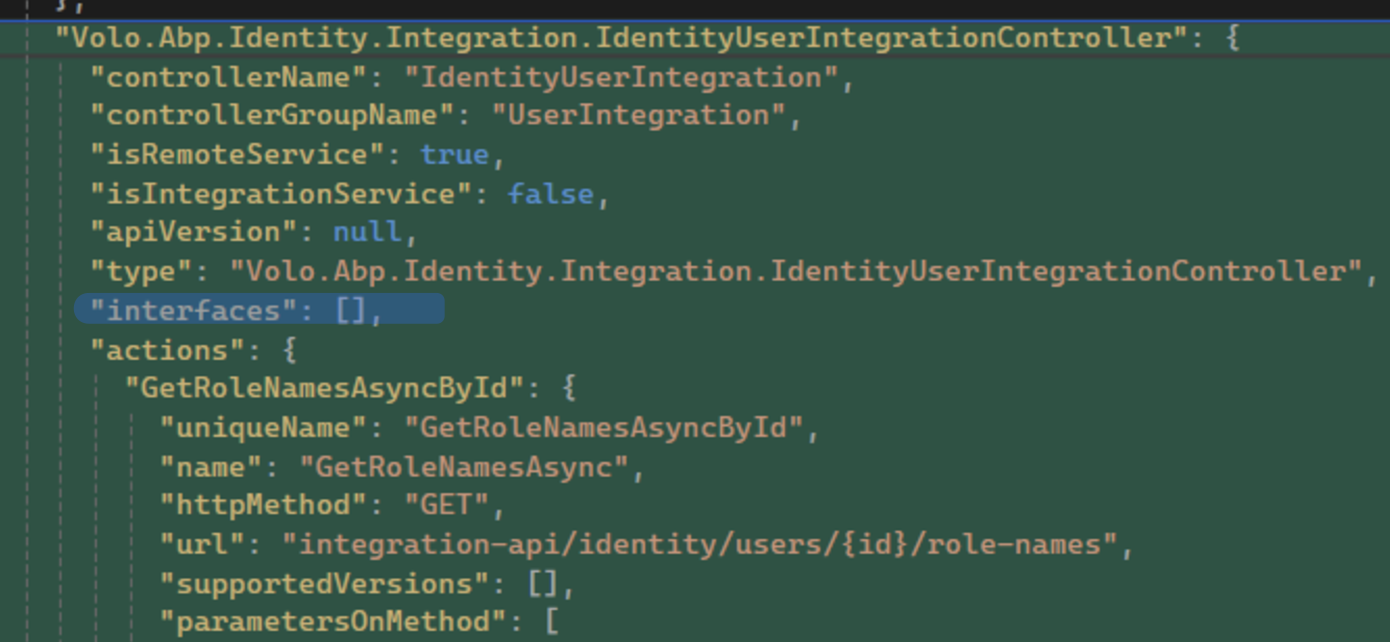
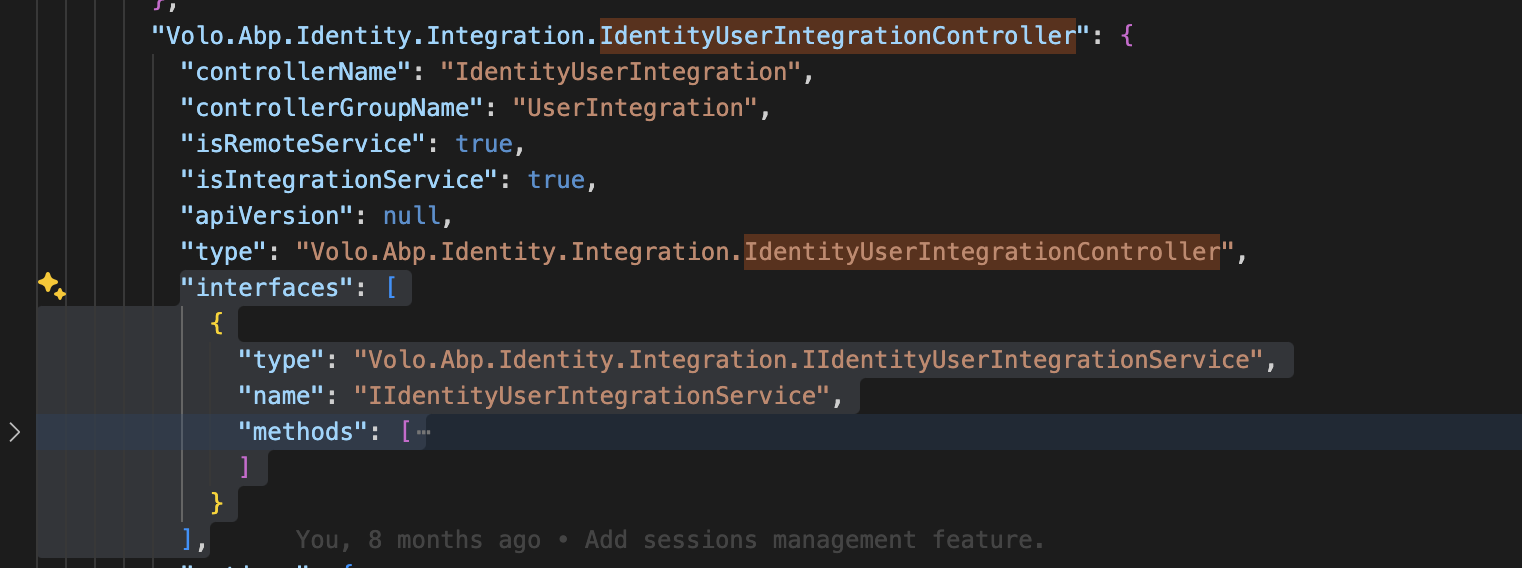
ExposeIntegrationServicestotrue.Configure<AbpAspNetCoreMvcOptions>(options => { options.ExposeIntegrationServices = true; });? That service is not exposed by default, unless you explicitly set ExposeIntegrationServices options (see the Exposing Integration Services section).
https://docs.abp.io/en/abp/latest/Integration-Services
-
0
-
0
Have you set
ExposeIntegrationServicestotrue? -
0