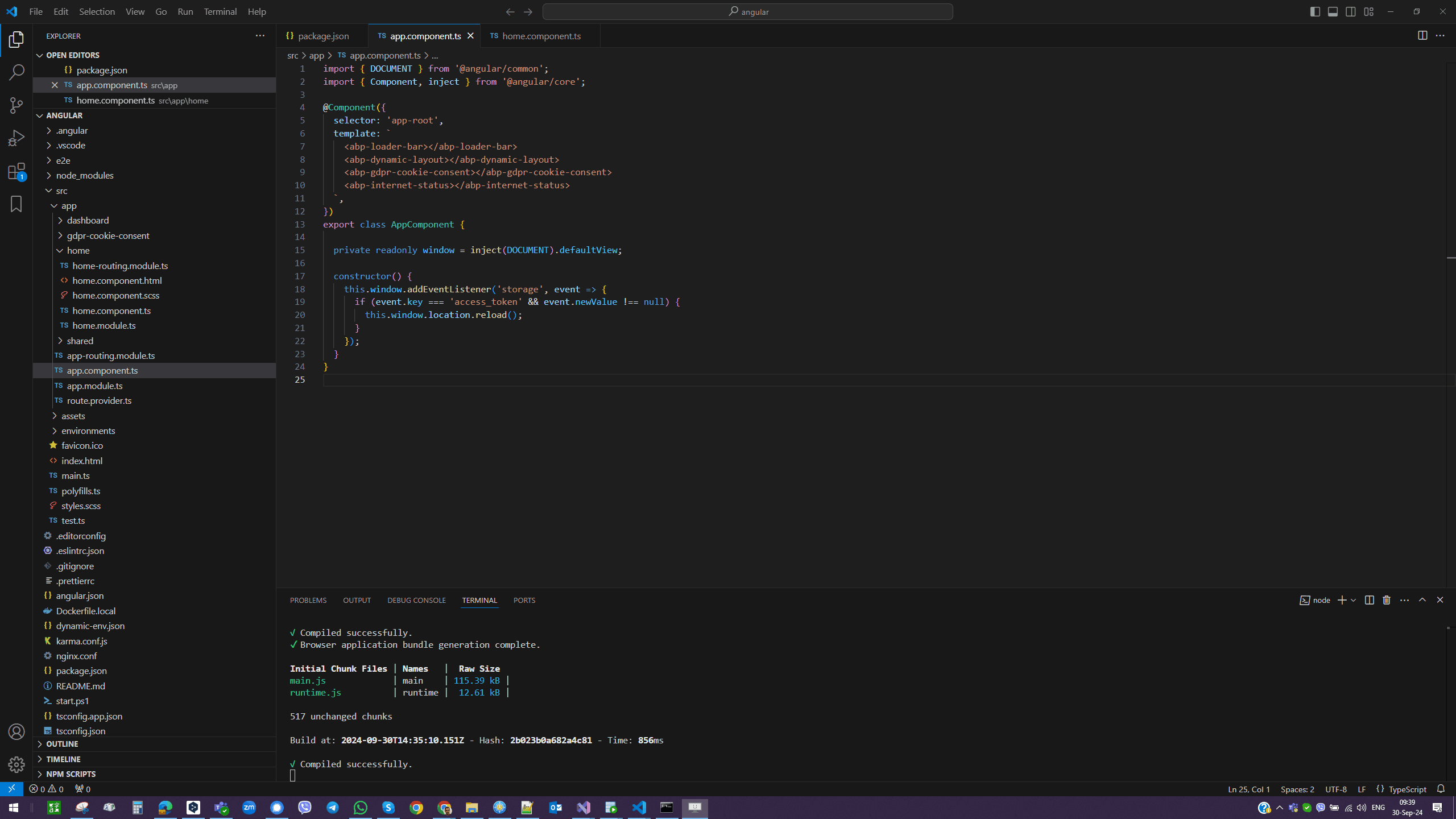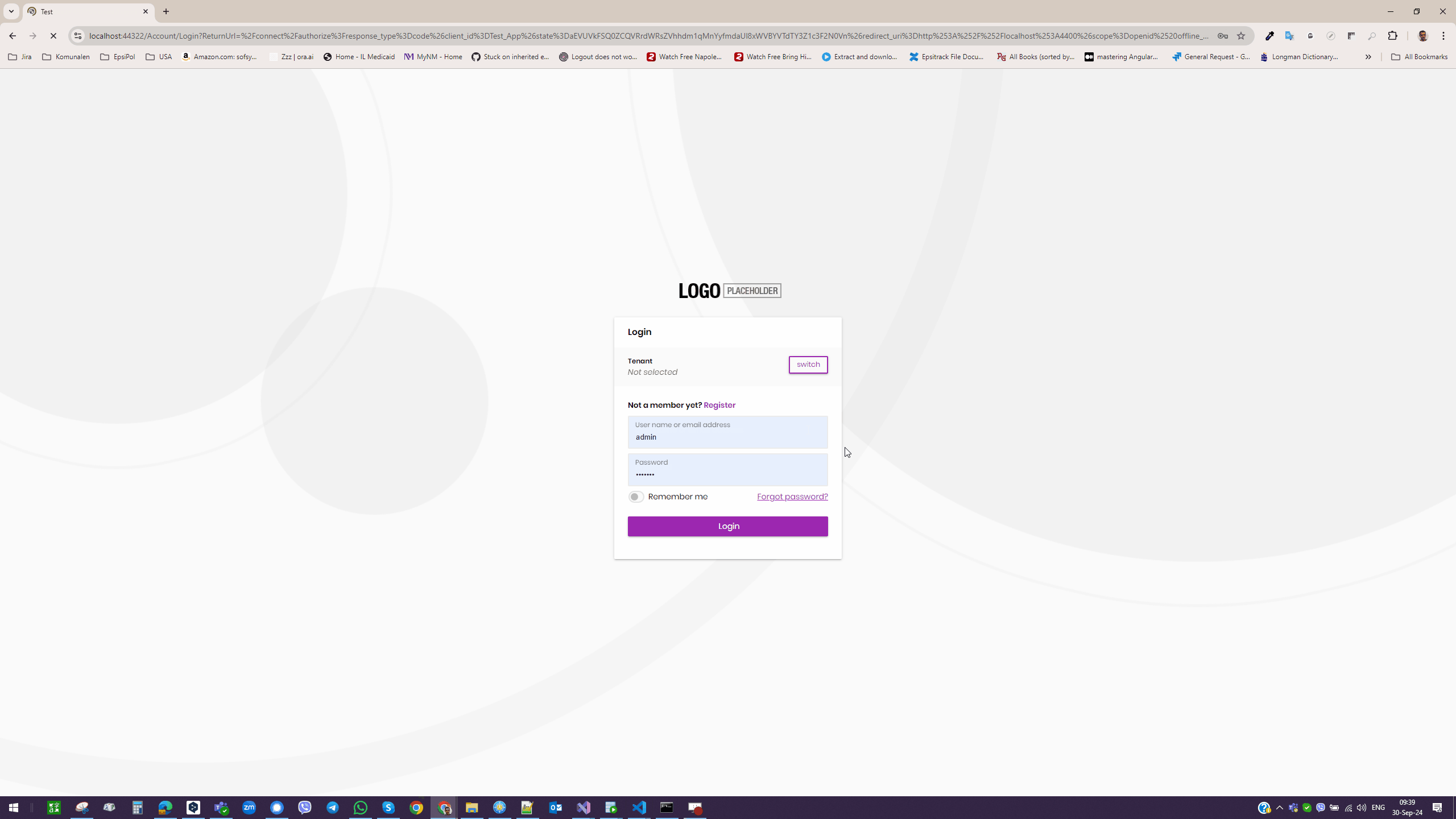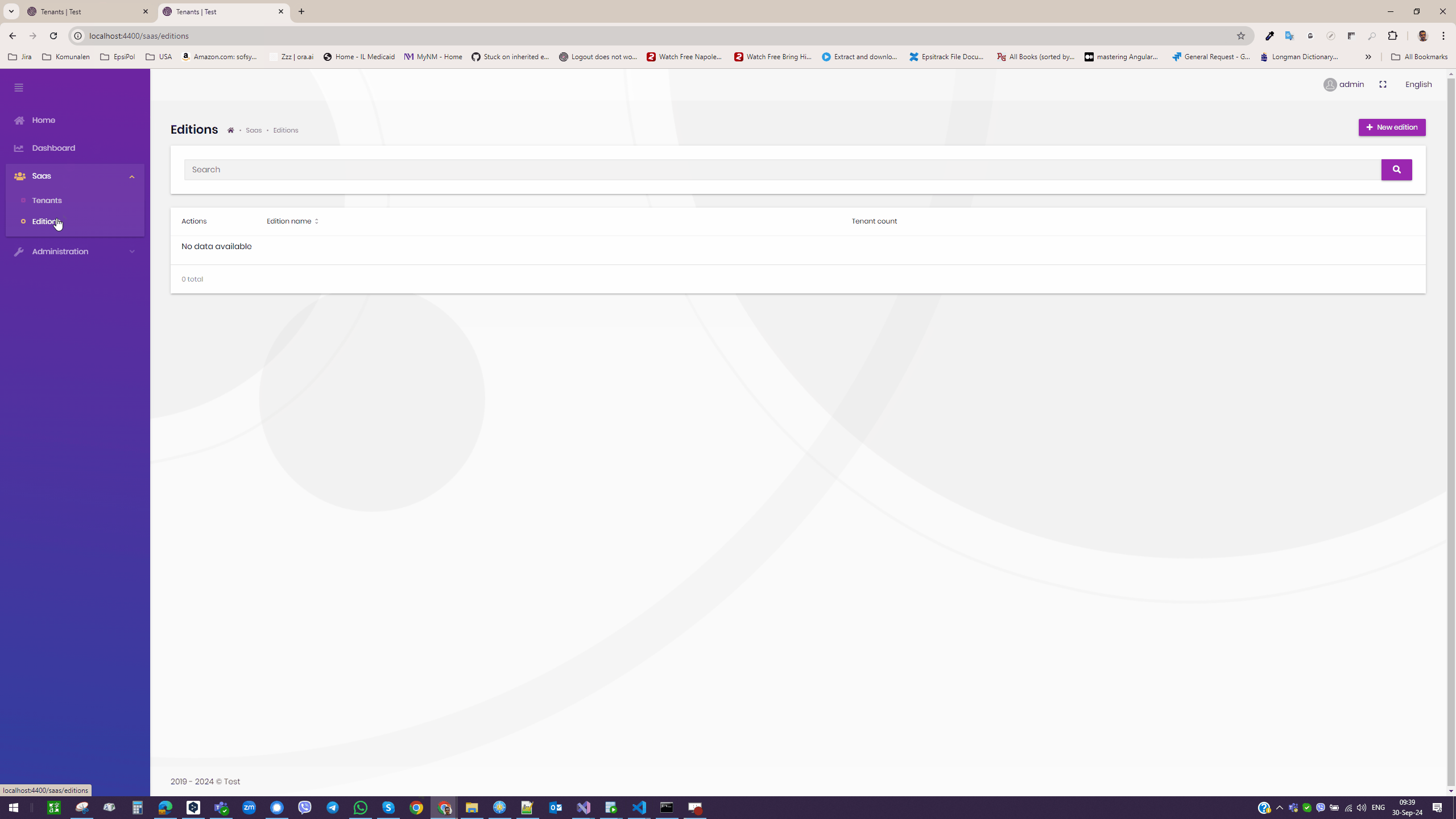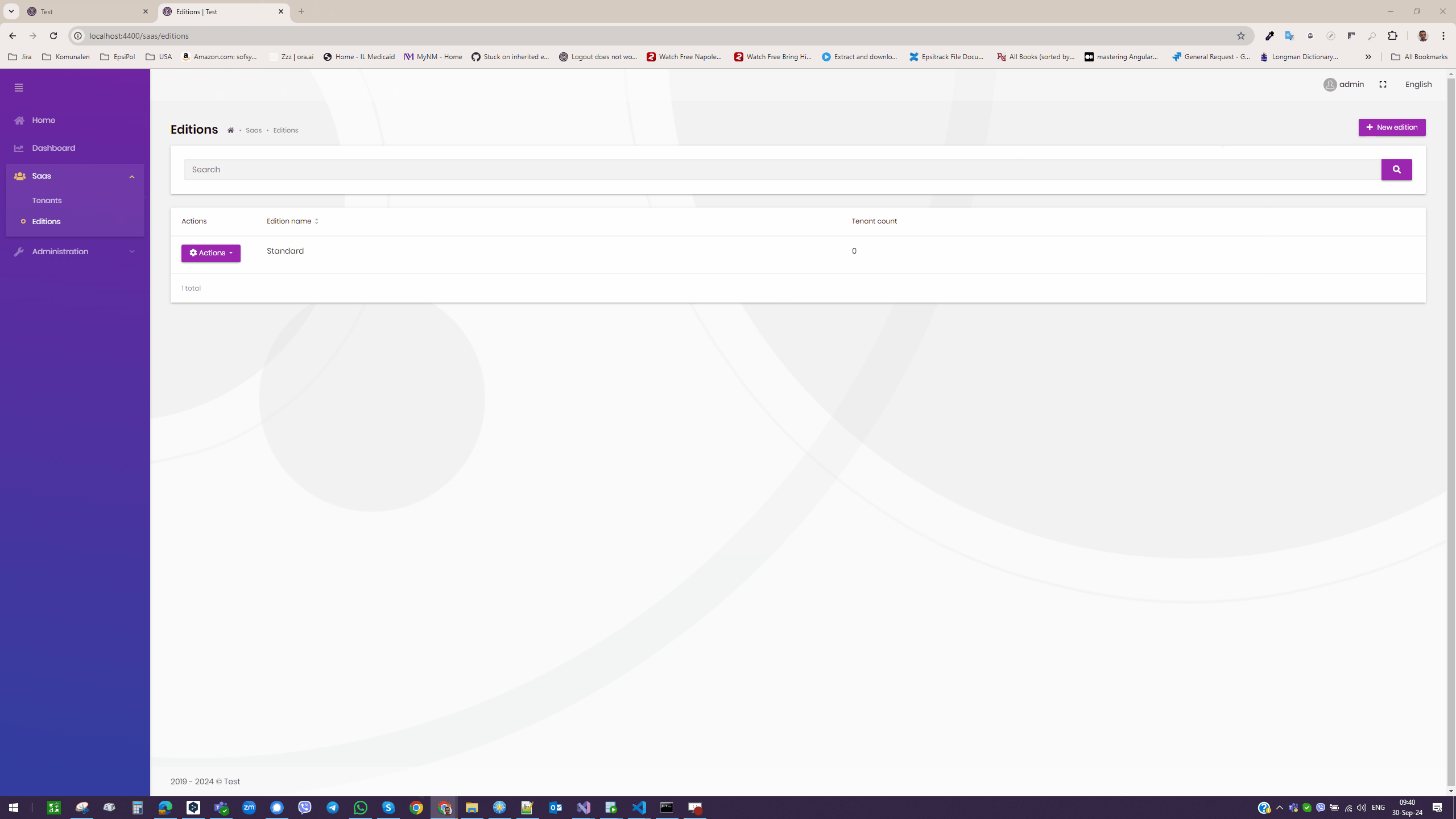
Hi. Thank you. I have the window load handler both in the OpenID server module added via AbpBundlingOptions and the same logic added via app.component.ts constructor like this (the load handler code DOES get triggered when I load Angular app pages):
this.document.defaultView.addEventListener('storage', event => {
if (event.key === 'access_token' && event.newValue === null) {
this.document.defaultView.location.reload();
}
});
const stateKey = 'authentication-state-id';
const onLoad = () => {
if (!this.currentUser.isAuthenticated) { // this.configStateService.getOne('currentUser')
localStorage.removeItem(stateKey);
}
else {
localStorage.setItem(stateKey, this.currentUser.id);
}
this.document.defaultView.addEventListener('storage', (event) => {
if (event.key !== stateKey || event.oldValue === event.newValue) {
return;
}
if (event.oldValue || !event.newValue) {
this.document.defaultView.location.reload();
}
else {
location.assign('/');
}
});
};
if (this.document.readyState === 'complete') {
onLoad();
}
else {
this.document.defaultView?.addEventListener('load', onLoad);
}
However, the error 400 is still there (with the same "The provided antiforgery token was meant for a different claims-based user than the current user." exception message): when I click "Login" button in OpenID server web page in the passive tab - neither code of authentication-state-listener.js is invoked (I put the breakpoints everywhere).
What am I doing wrong?
We have added a new js to refresh the page if authentication changes. You can add this js file to your 8.1.3 version.
I've tried this file and made sure that it has been added to the markup. The following piece of code has been added to OpenID AbpModule:
Configure<AbpBundlingOptions>(options =>
{
...
options.ScriptBundles.Configure(
StandardBundles.Scripts.Global,
bundle =>
{
bundle.AddFiles("/libs/abp/aspnetcore-mvc-ui-theme-shared/authentication-state/authentication-state-listener.js");
}
);
});
But it did not affect the issue in any way.
I've placed the breakpoints inside authentication-state-listener.js and its code has not been invoked during the login process in the passive tab (after a user has already logged-in in the active tab). I think this code is not relevant - instead, there has to be reaction on "Login" button click (i.e. redirect a user to Home page instead of trying to authenticate him), etc.
Please be noted that I had to retain the code you suggested in the very beginning to automatically redirect user to Login box in the passive tab (this is placed in the constructor of app.component.ts:
this.window.addEventListener('storage', event => {
if (event.key === 'access_token' && event.newValue === null) {
this.window.location.reload();
}
});
https://learn.microsoft.com/en-us/aspnet/core/security/anti-request-forgery?view=aspnetcore-8.0#multiple-browser-tabs-and-the-synchronizer-token-pattern
Ok - thank you for this link.
In our case the message is different - "Antiforgery token validation failed. The provided antiforgery token was meant for a different claims-based user than the current user. Microsoft.AspNetCore.Antiforgery.AntiforgeryValidationException: The provided antiforgery token was meant for a different claims-based user than the current user." - but I think it's due to the same issue.
So the site tells "Consider alternative CSRF protection patterns if this poses an issue." - but nothing specific.
I think in the given situation I could just redirect a user (already authenticated in the first tab) to the initial (home) page in the second tab, if such situation takes place instead of trying to log him in again. I just need the hint where I should place the corresponding check, please.
hi
You can try to configure the
AbpSystemTextJsonSerializerOptionsto set theJsonSerializerSettingshttps://abp.io/docs/latest/framework/infrastructure/json#abpsystemtextjsonserializeroptions
Are you sure it's JsonSerializerSettings, not JsonSerializerOptions? Because as far as I understand, JsonSerializerSettings is related to Newtonsoft.Json, not System.Text.Json from Microsoft. And the exception is related to the latter.
Besides, where do you suggest to place it?
public class MyHttpApiModule : AbpModule
{
public override void ConfigureServices(ServiceConfigurationContext context)
{
...
Configure<JsonOptions>(options =>
{
options.JsonSerializerOptions.Converters.Add(context.Services.GetRequiredService<IStringToNullableIntConverter>() as JsonConverter);
options.JsonSerializerOptions.Converters.Add(context.Services.GetRequiredService<IStringToNullableLongConverter>() as JsonConverter);
options.JsonSerializerOptions.ReferenceHandler = ReferenceHandler.IgnoreCycles; //Maybe this will help?
});
Configure<AbpSystemTextJsonSerializerOptions>(options =>
{
//The change is here?
});
}
}
Any update here?
Your screenshots are now consistent with mine. So scenarios 1) and 3) do not fit me. Because the "passive" tab does not redirect to login box. Scenario 2) is what I need. But in your screenshot you did not go further: you need to try to login in the "passive" tab too. In this case, you will get error 400 because of the "reused token" issue. This is what I am trying to avoid.
Sorry, but I easily reproduce the issues on the same test project. Please have a look below. I don't know how to explain it.
event.newValue !== null - the second tab does not redirect a user to Login page when I do logout from the first tab:
event.newValue === null - the second tab redirects a user to Login page when I do logout from the first tab, however the bug with a token is reproduced during logging in:
The test project link is already present in this thread. https://drive.google.com/open?id=1xYCu_NLl5O0YCn1h3ffv4FZd5UGkGK0B&usp=drive_fs
Hi. Sorry, I'm not sure I am following you here. The latest mentioned problem is reproduced on ABP generated test project. There's no our custom code there. So in this project i was trying to get the following behavior:
storage event was suggested by your colleague and it did work;null condition from === to !== in the event handler, but in this case (1) stops working - I'm not redirected to Login page in a passive tab anymore;
