Activities of "treggon@gmail.com"
- ABP Framework version: v7.3.3
- UI Type: Blazor Server
- Database System:SQL Server on Azure
- Tiered (for MVC) or Auth Server Separated (for Angular): no
- Exception message and full stack trace: This page isn’t working
- Steps to reproduce the issue: Publish an app to Azure App Service and try to login using OpenID
Example.... https://app.juriseconomics.com/Account/Login is not working as the certificate is not loading correctly.
I have been following the OpenID information that I found on their website directly: https://documentation.openiddict.com/configuration/encryption-and-signing-credentials.html#registering-a-certificate-recommended-for-production-ready-scenarios and have followed some of the tutorials https://brianmeeker.me/2022/08/29/setting-up-abp-with-openiddict-on-azure-app-services/
And I had it working for a long time, but something I am doing is now wrong. It works fine locally with the development certificates on localhost, but when I publish, anything that requires the MultiTenancy basically will fail, so I have a fallback page. Here is a screenshot of the comma delaminated list of certs to load in configuration.
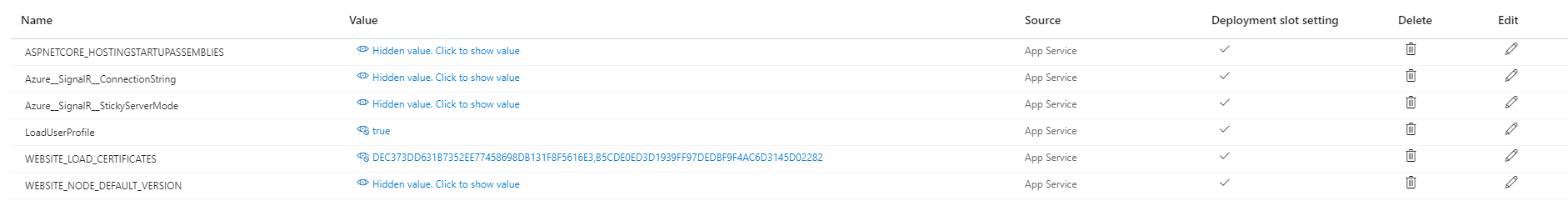
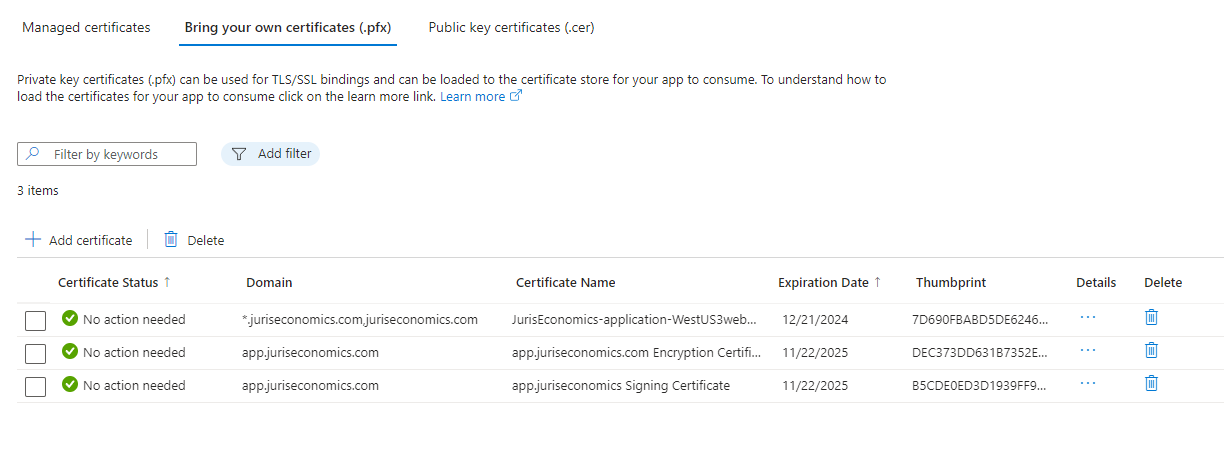 `if (hostingEnvironment.IsProduction())
{
PreConfigure
`if (hostingEnvironment.IsProduction())
{
PreConfigure
});
PreConfigure<OpenIddictServerBuilder>(builder =>
{
// Load from Thumprint
var SigningCert = GetSigningCertificate(hostingEnvironment, configuration, configuration["AuthServer:SigningCertificateThumbprint"]);
var EncryptionCert = GetEncryptionCertificate(hostingEnvironment, configuration, configuration["AuthServer:EncryptionCertificateThumbprint"]);
builder.AddSigningCertificate(SigningCert);
builder.AddEncryptionCertificate(EncryptionCert);
// Load from files
//builder.AddSigningCertificate(LoadCertificate(configuration["AuthServer:SigningCertificateThumbprint"]));
//builder.AddEncryptionCertificate(LoadCertificate(configuration["AuthServer:EncryptionCertificateThumbprint"]));
builder.SetIssuer(new Uri(configuration["AuthServer:Authority"]));
});
}This is the code I used to generate the certs that were uploaded. public void CreateEncryptionCert()
{
using var algorithm = RSA.Create(keySizeInBits: 2048);
var subject = new X500DistinguishedName("CN=app.juriseconomics.com");
var request = new CertificateRequest(subject, algorithm, HashAlgorithmName.SHA256, RSASignaturePadding.Pkcs1);
request.CertificateExtensions.Add(new X509KeyUsageExtension(X509KeyUsageFlags.KeyEncipherment, critical: true));
var certificate = request.CreateSelfSigned(DateTimeOffset.UtcNow, DateTimeOffset.UtcNow.AddYears(2));
System.IO.File.WriteAllBytes("wwwroot/encryption-certificate.pfx", certificate.Export(X509ContentType.Pfx, "XXXX"));
}
public void CreateSigningCert()
{
using var algorithm = RSA.Create(keySizeInBits: 2048);
var subject = new X500DistinguishedName("CN=app.juriseconomics.com");
var request = new CertificateRequest(subject, algorithm, HashAlgorithmName.SHA256, RSASignaturePadding.Pkcs1);
request.CertificateExtensions.Add(new X509KeyUsageExtension(X509KeyUsageFlags.DigitalSignature, critical: true));
var certificate = request.CreateSelfSigned(DateTimeOffset.UtcNow, DateTimeOffset.UtcNow.AddYears(2));
System.IO.File.WriteAllBytes("wwwroot/signing-certificate.pfx", certificate.Export(X509ContentType.Pfx, "XXXX"));
}`
The following is code that I used to get the certs.... private X509Certificate2 GetSigningCertificate(IWebHostEnvironment hostingEnv, IConfiguration configuration, string thumbprint) {
using (X509Store certStore = new X509Store(StoreName.My, StoreLocation.CurrentUser))
{
certStore.Open(OpenFlags.ReadOnly);
string certThumbprint = thumbprint; // 7D690FBABD5DE6246422E81836D16B22CF57D49F,98CEE0FD7F6ACD62C7C81784EDE5E78F86A83F1C,400B611BC5CF693DACAB6ABACE21DD31790D4A90,2EB0F42C5107C4E8C07BD6CE4D53F853F03AADA1
bool validOnly = false;
X509Certificate2Collection certCollection = certStore.Certificates.Find(
X509FindType.FindByThumbprint,
// Replace below with your certificate's thumbprint
certThumbprint,
validOnly);
// Get the first cert with the thumbprint
X509Certificate2 cert = certCollection.OfType<X509Certificate2>().FirstOrDefault();
if (cert is null)
throw new Exception($"Certificate with thumbprint {certThumbprint} was not found");
// Use certificate
Console.WriteLine(cert.FriendlyName);
// Consider to call Dispose() on the certificate after it's being used, available in .NET 4.6 and later
return cert;
}
} private X509Certificate2 GetEncryptionCertificate(IWebHostEnvironment hostingEnv, IConfiguration configuration, string thumbprint) {
using (X509Store certStore = new X509Store(StoreName.My, StoreLocation.CurrentUser))
{
certStore.Open(OpenFlags.ReadOnly);
string certThumbprint = thumbprint; // 7D690FBABD5DE6246422E81836D16B22CF57D49F,98CEE0FD7F6ACD62C7C81784EDE5E78F86A83F1C,400B611BC5CF693DACAB6ABACE21DD31790D4A90,2EB0F42C5107C4E8C07BD6CE4D53F853F03AADA1
bool validOnly = false;
X509Certificate2Collection certCollection = certStore.Certificates.Find(
X509FindType.FindByThumbprint,
// Replace below with your certificate's thumbprint
certThumbprint,
validOnly);
// Get the first cert with the thumbprint
X509Certificate2 cert = certCollection.OfType<X509Certificate2>().FirstOrDefault();
if (cert is null)
throw new Exception($"Certificate with thumbprint {certThumbprint} was not found");
// Use certificate
Console.WriteLine(cert.FriendlyName);
// Consider to call Dispose() on the certificate after it's being used, available in .NET 4.6 and later
return cert;
}
}
HELP!