- ABP Framework version: v6.0.0-rc.1
- UI type: MVC
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): no
- Exception message and stack trace:
Application '/LM/W3SVC/2/ROOT' with physical root 'D:\Domains\abp_beheer\httpdocs\' has exited from Program.Main with exit code = '1'. First 30KB characters of captured stdout and stderr logs:
[14:14:52 INF] Starting web host.
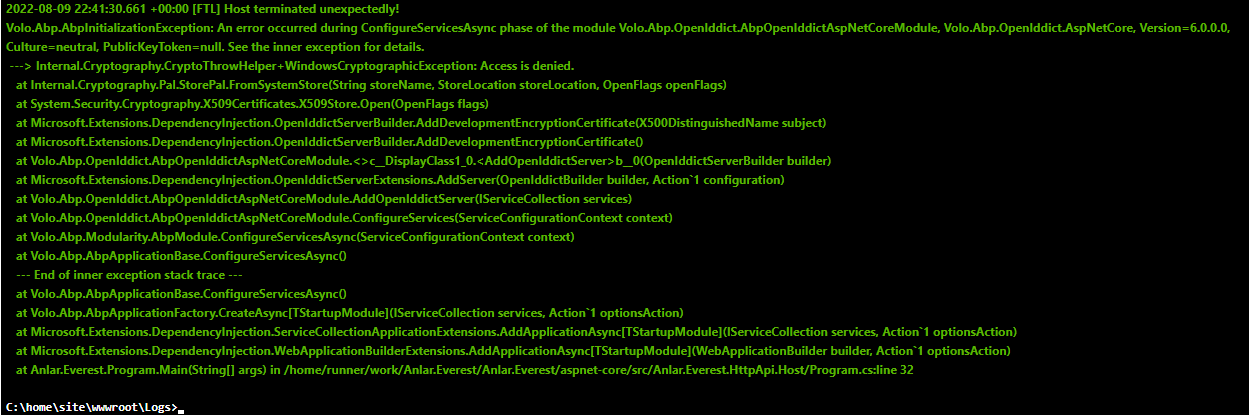
[14:14:53 FTL] Host terminated unexpectedly!
Volo.Abp.AbpInitializationException: An error occurred during ConfigureServicesAsync phase of the module Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule, Volo.Abp.OpenIddict.AspNetCore, Version=6.0.0.0, Culture=neutral, PublicKeyToken=null. See the inner exception for details.
---> Internal.Cryptography.CryptoThrowHelper+WindowsCryptographicException: Access is denied.
at Internal.Cryptography.Pal.StorePal.FromSystemStore(String storeName, StoreLocation storeLocation, OpenFlags openFlags)
at System.Security.Cryptography.X509Certificates.X509Store.Open(OpenFlags flags)
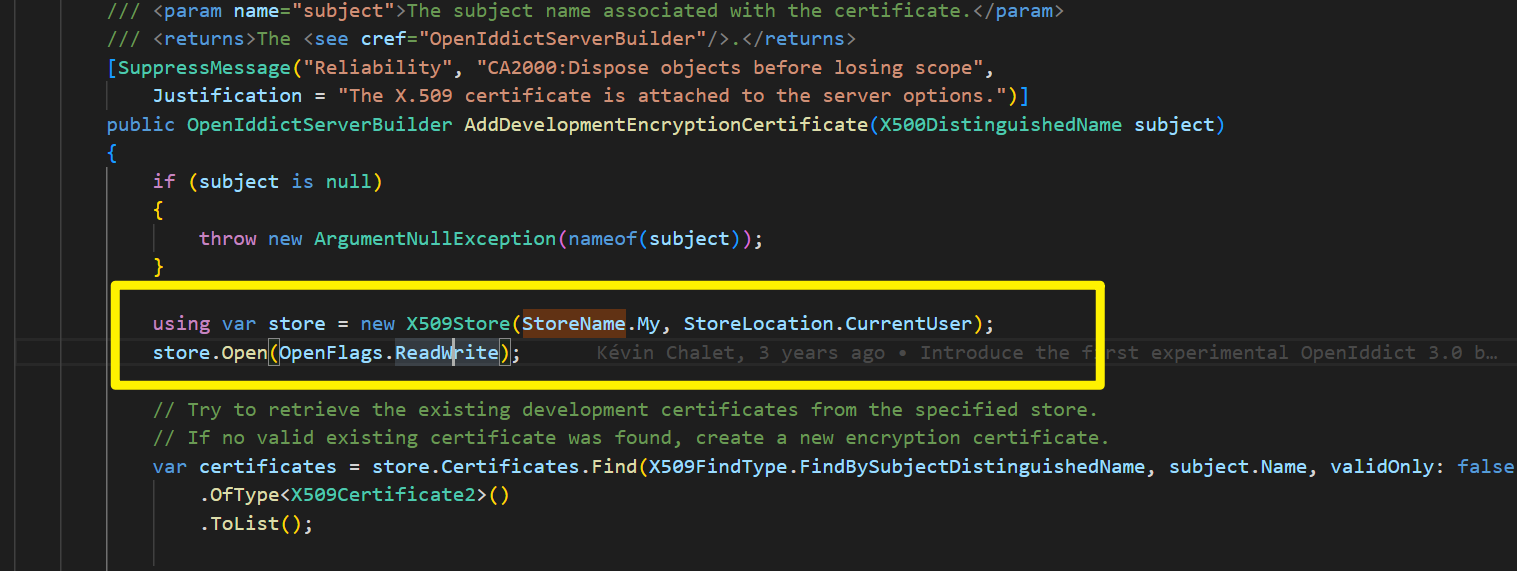
at Microsoft.Extensions.DependencyInjection.OpenIddictServerBuilder.AddDevelopmentEncryptionCertificate(X500DistinguishedName subject)
at Microsoft.Extensions.DependencyInjection.OpenIddictServerBuilder.AddDevelopmentEncryptionCertificate()
at Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule.<>c__DisplayClass1_0.<AddOpenIddictServer>b__0(OpenIddictServerBuilder builder)
at Microsoft.Extensions.DependencyInjection.OpenIddictServerExtensions.AddServer(OpenIddictBuilder builder, Action`1 configuration)
at Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule.AddOpenIddictServer(IServiceCollection services)
at Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule.ConfigureServices(ServiceConfigurationContext context)
at Volo.Abp.Modularity.AbpModule.ConfigureServicesAsync(ServiceConfigurationContext context)
at Volo.Abp.AbpApplicationBase.ConfigureServicesAsync()
--- End of inner exception stack trace ---
at Volo.Abp.AbpApplicationBase.ConfigureServicesAsync()
at Volo.Abp.AbpApplicationFactory.CreateAsync[TStartupModule](IServiceCollection services, Action`1 optionsAction)
at Microsoft.Extensions.DependencyInjection.ServiceCollectionApplicationExtensions.AddApplicationAsync[TStartupModule](IServiceCollection services, Action`1 optionsAction)
at Microsoft.Extensions.DependencyInjection.WebApplicationBuilderExtensions.AddApplicationAsync[TStartupModule](WebApplicationBuilder builder, Action`1 optionsAction)
at ABP_Beheer.Web.Program.Main(String[] args) in D:\BUILD02_Agent3\_work\730\s\src\ABP_Beheer.Web\Program.cs:line 36
- Steps to reproduce the issue:"
- dotnet tool install Volo.Abp.Cli -g --version 6.0.0-rc.1
- abp new BookStore --preview
- Run migrator & Open application & login with admin user
- Now release to a windows server 2022 server (install IIS+dotnet 6 webhosting bundle)
- Configure ABP there with Local IIS
- ApplicationPoolIdentity
- Add a ssl certificate in the Personal folder via "Manage computer certificates"
- After that, configure the SSL certificate, so that the IIS APPOOL has access to it (manage computer certificates> Personal > Certificates > right click certificate > All tasks > Manage private keys > Add iis appool user here)
- See https://github.com/dotnet/aspnetcore/issues/6840 for more info
- Add HTTPS binding of the ssl certificate, to the iis site
- Recycle app pool
- Go to the application, by browsering to it
We haven't had this issue with ABP in combination with Identity server. What am i doing wrong, in context of OpenIddict?
Thanks in advance.
9 Answer(s)
-
0
hi
Can you try to add a custom certificate instead of a development certificate?
https://documentation.openiddict.com/configuration/encryption-and-signing-credentials.html#registering-a-development-certificate
https://docs.abp.io/en/abp/6.0/Modules/OpenIddict#abpopeniddictaspnetcoreoptions
-
0
-
0
hi
https://github.com/abpframework/abp/issues/13633
-
0
-
0
-
1
For us it was a combination of
- 1. Development certificate
private void ConfigureOpenIddict() { Configure<AbpOpenIddictAspNetCoreOptions>(builder => { builder.AddDevelopmentEncryptionAndSigningCertificate = false; }); }{ ... ConfigureOpenIddict(); ... }Why not adding this code (maybe with env.IsDevelopment()) to the starter template? This might help a lot of people?
- 2. Setting Loading User Profile to true in IIS
Tnhx for the support!
-
1
I found this in the OpenIddict documentation. https://documentation.openiddict.com/configuration/encryption-and-signing-credentials.html. This should be included in the deployment documentation for the new version and referenced in the release notes.
-
3
I was able to resolve the issue for Azure App Service with the following code:
Added to PreConfigureServices in *HttpApiHostModule
#if RELEASE PreConfigure<AbpOpenIddictAspNetCoreOptions>(options => options.AddDevelopmentEncryptionAndSigningCertificate = false); string encryptionThumbprint = "******************"; string signingThumbprint = "**************"; var encryptionCertificate = GetX509Certificate2(encryptionThumbprint); var signingCertificate = GetX509Certificate2(signingThumbprint); PreConfigure<OpenIddictServerBuilder>(builder => { builder.AddEncryptionCertificate(encryptionCertificate); builder.AddSigningCertificate(signingCertificate); }); #endifhelper method referenced above
private X509Certificate2 GetX509Certificate2(string thumbprint) { bool validOnly = false; using var store = new X509Store(StoreName.My, StoreLocation.CurrentUser); store.Open(OpenFlags.ReadOnly); var collection = store.Certificates.Find(X509FindType.FindByThumbprint, thumbprint, validOnly); var certificate = collection.OfType<X509Certificate2>().FirstOrDefault(); store.Close(); return certificate ?? throw new Exception($"Cannot find certificate with thumbprint {thumbprint}"); }The self-signed certificates were generated based on the documentation available on https://documentation.openiddict.com/configuration/encryption-and-signing-credentials.html.
The certificates must be generated with a password instead of the empty password in the example in order for you to upload the PFX file to the Azure App Service.
You must also set the configuration setting for WEBSITE_LOAD_CERTIFICATES on the Azure App Service to either be * to load all certificates or have a comma separated list of certificates you want loaded.
-
0
Many thanks @scott7106