- ABP Framework version: v7.3.3
- UI Type: MVC and Angular
- Database System: EF Core (SQL Server)
- Tiered (for MVC) or Auth Server Separated (for Angular): yes
- Exception message and full stack trace:
- Steps to reproduce the issue:
Hi Team,
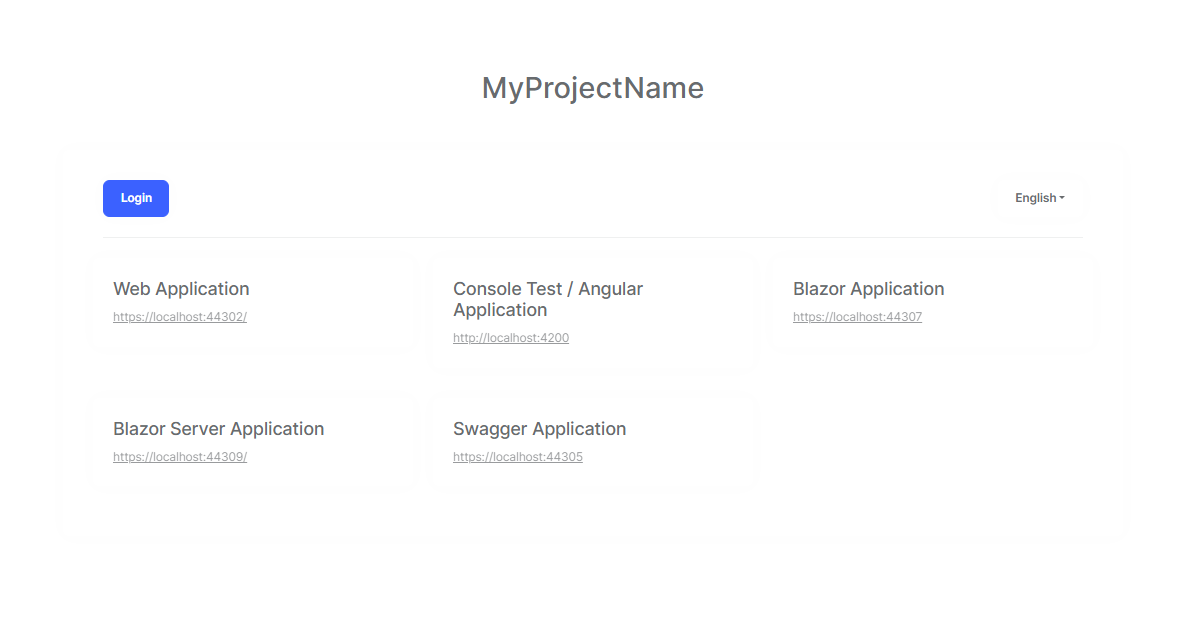
I have two applications in MVC and Angular and I like my users to use below AuthServer page as:
- User landed on the AuthServer page
- Login by clicking on the login button (already there)
- Once the user is logged in, I want my user to be allowed to click on the Applications link (either MVC or Angular) to redirect
- The user lands on the application as pre-authenticated.
Currently, when the user lands on MVC, it does not show authenticated but asks to log in by clicking the login button.
How can I redirect my users to MVC app from AuthServer page as pre-authenticated?
Many thx, Navneet
17 Answer(s)
-
0
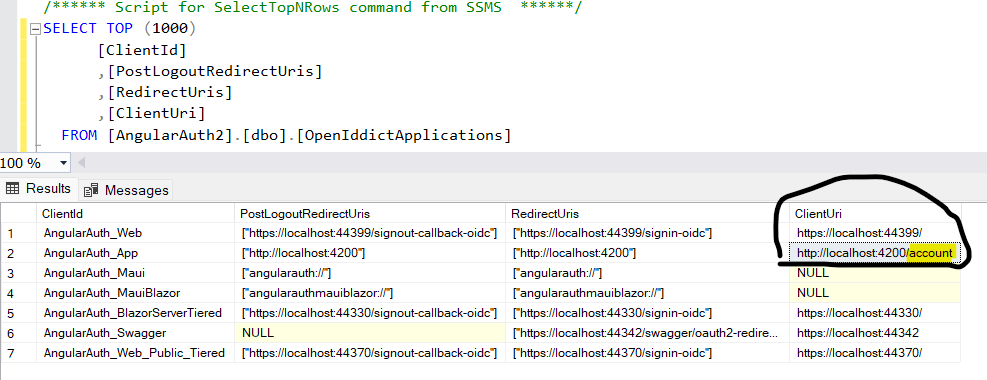
Hello Navneet@aol.com.au
Please try to add
/accountin your client uri ofOpenIddictApplicationstable for angular and MVC project.With the above update in table I was able to redirect to landing page of angular project as pre-authenticated
Please do let me know if it helps you.
Thank You Anjali
-
0
Thanks Anjali, I will try and come back to you
-
0
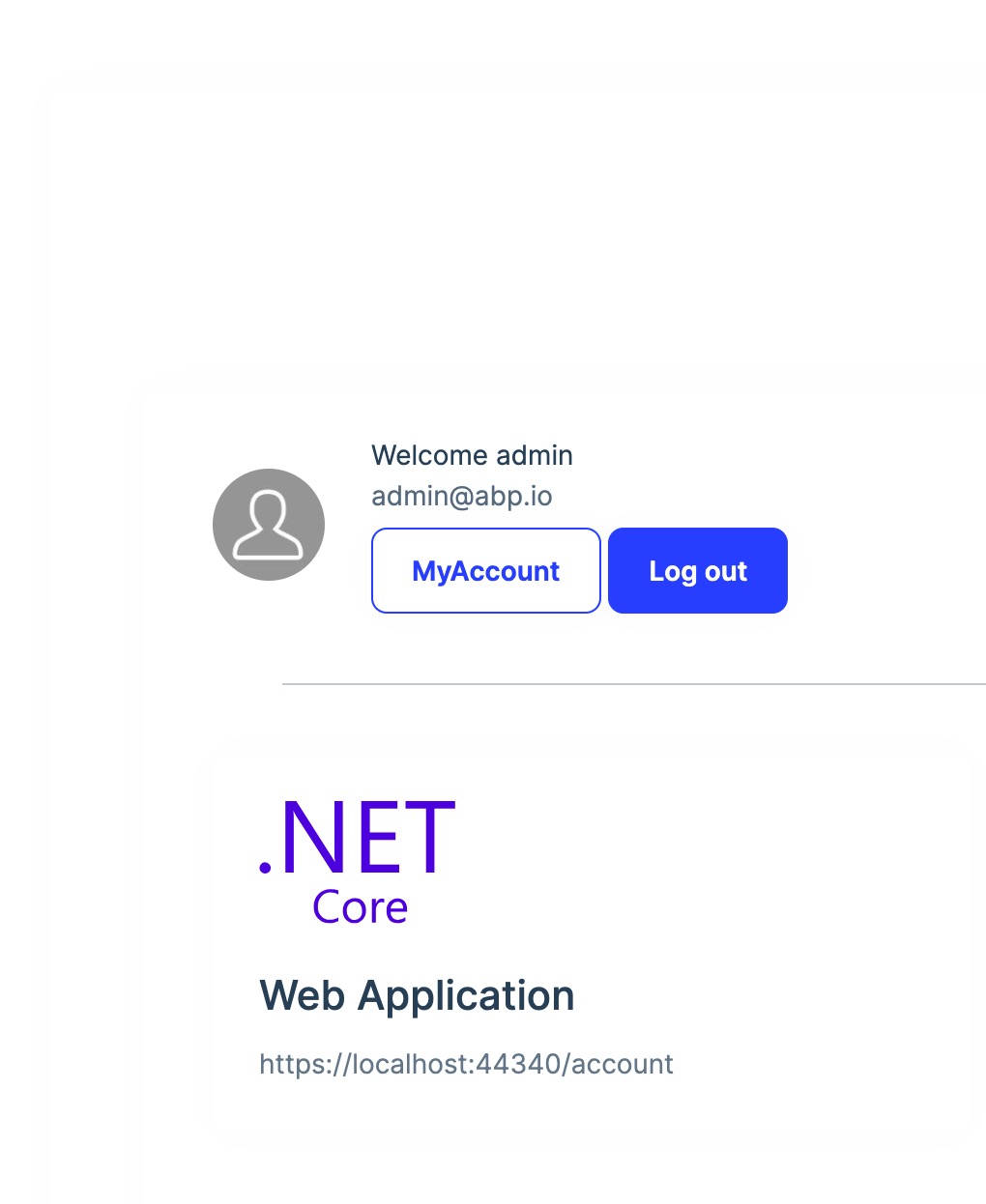
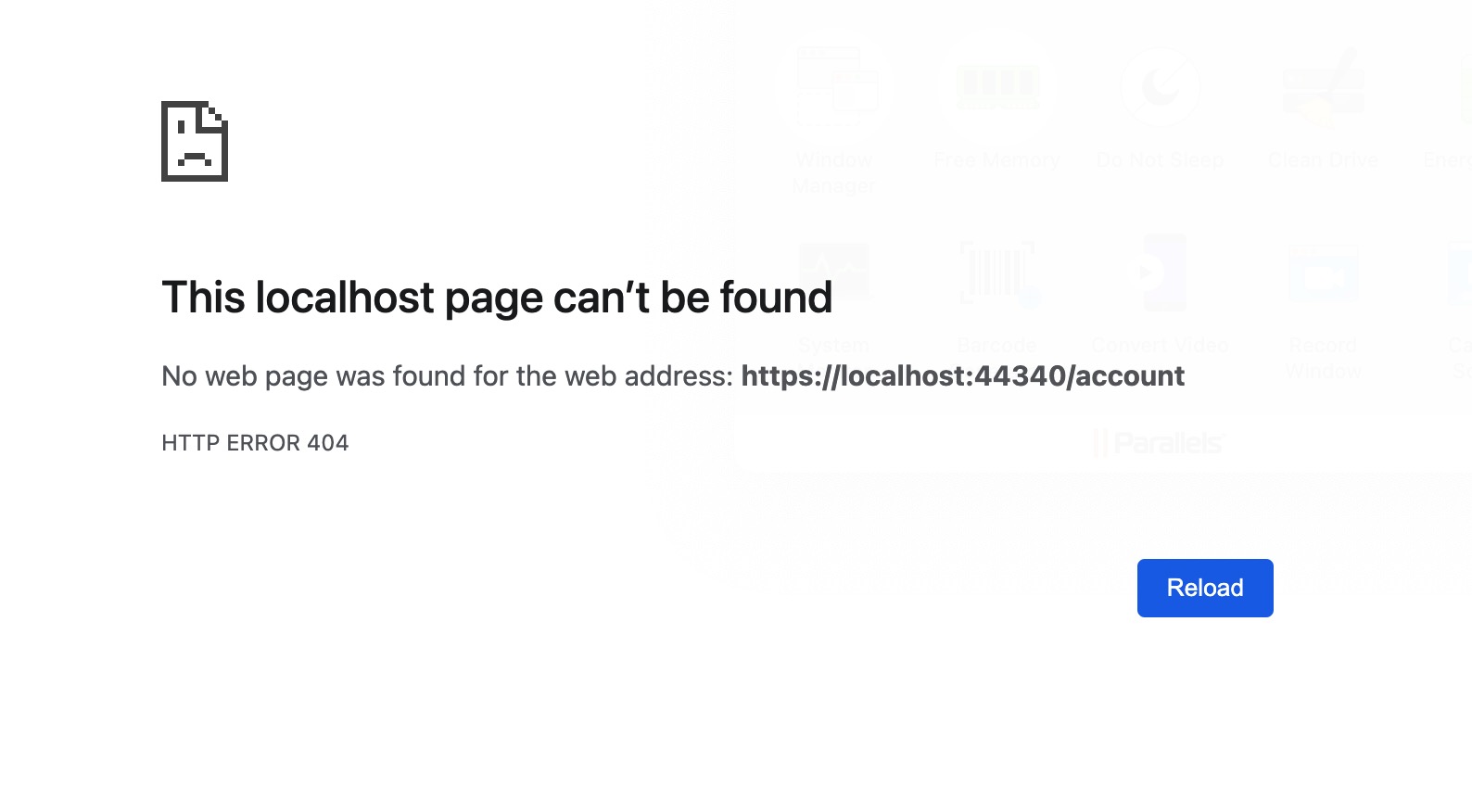
Hi Anjali,
It's not working with MVC, please see the attached screenshot
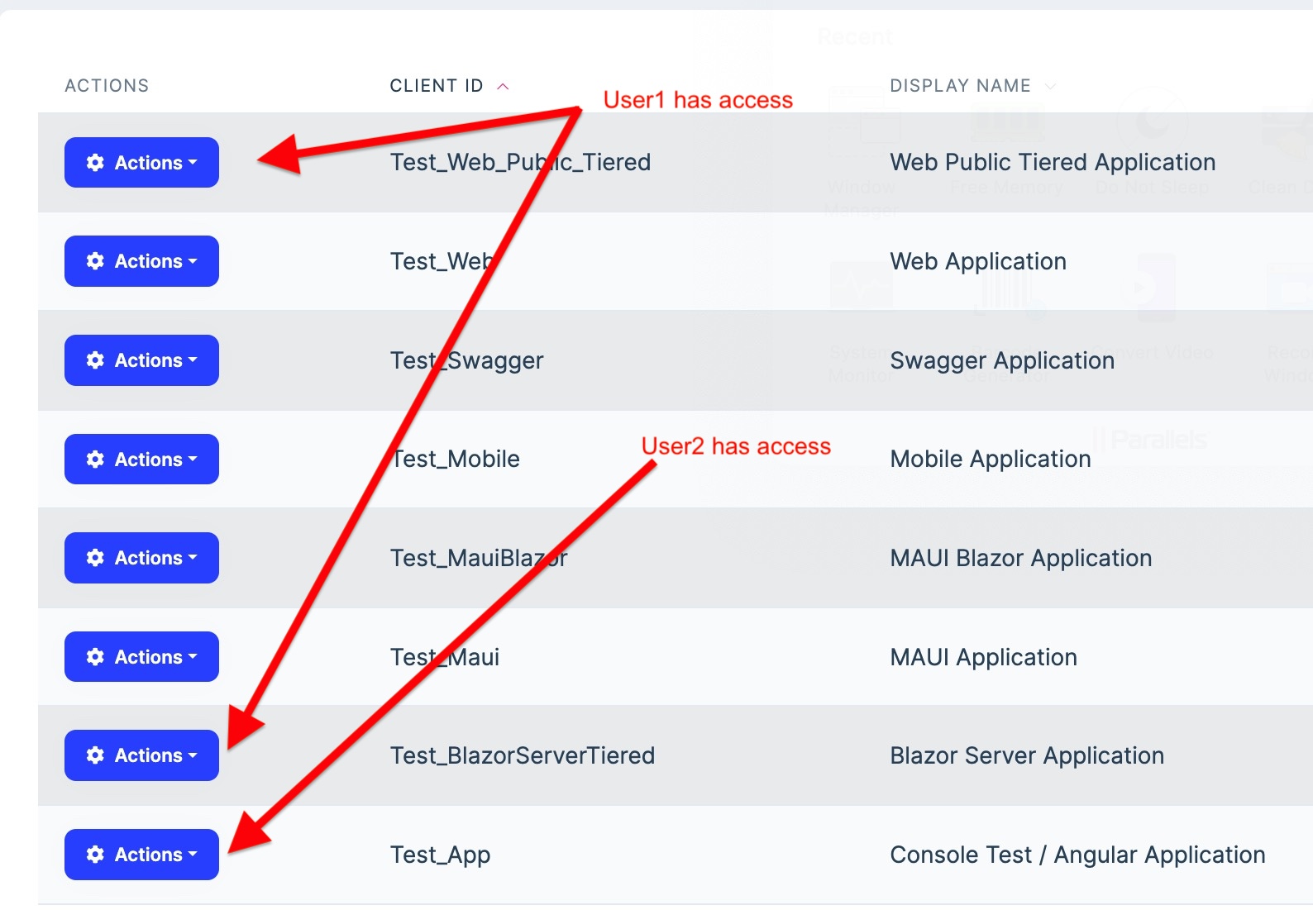
. . . By default, all users have access to all applications in the screenshot below, I want to restrict the access to applications and don't want them to get tokens as well when they use Postman https://localhost:44359/connect/token, how can I restrict the access by USER or ROLE management
Many thx, Navneet
-
0
Hi Anjali,
Any update?
Thx, Navneet
-
0
Hi Anjali, any update?
Thx, Navneet
-
0
Hi Navneet,
Apologize for late response I will check and get back to you asap
Thanks
-
0
Hi Anjali,
Just checking if there is any suggestion or help
Regards Navneet
-
0
Hi Anjali,
Hope you are doing well Any update on this
Thx, Navneet
-
0
There is no such thing like pre-authenticated.
You can put [Authorize] attribute to your MVC app Home/Index page (or whatever authorized page you want) and allow clicking to this link from AuthServer to initiate SSO process.
-
0
Hi gterdem,
Many thx for replying on behalf of Anjali, I will try your suggestions, however, I am still not sure how to pre-authenticated only selected users, if you look at the screenshot earlier, I want to control users' access to the application and in generating token via https://localhost:44359/connect/token
Regards, Navneet
-
0
Hello team,
Any update on my request please
Thx Navneet
-
0
Hi gterdem,
Many thx for replying on behalf of Anjali, I will try your suggestions, however, I am still not sure how to pre-authenticated only selected users, if you look at the screenshot earlier, I want to control users' access to the application and in generating token via https://localhost:44359/connect/token
Regards, Navneet
You can not pre-authenticate some selected users without initiating a signin process. Authentication flows are standards and shouldn't be altered.
When a user is signed into AuthServer and you want the user to login to one of the applications in the AuthServer environment without re-entering the credentials; you can simply put an
[Authorize]attribute to the Home/Index page of the application. When the signed-in user navigates to the authenticated Home/Index of the application, the SSO will kick in and the user will automatically login to the application without re-entering the credentials.If what you want to do is different than this and want to alter the authentication manually; it is not related to ABP and you can find better help on StackOverflow about changing the authentication flows of OpenIdConnect.
-
0
Hi gterdem,
Thanks for your response, after reading and researching your "You can not pre-authenticate" I now completely agree with you and apologise for this confusion.
Let me give you a little more info about what I am trying to achieve, I am working on a project for a client that has two WebApi for Stock Management and Currency Management designed in asp.net core (I cannot change and it is out of ABP Solution), so I have:
- I have created two Applications via UI CREATE APPLICATION
- I have created two Scopes via UI CREATE SCOPE
Everything is working fine, but I don't know how can I assign permission to users or roles to above-created application or scope so that not all users can access.
Can you please suggest which AppService or Domain Manager I can investigate or customize so that my clients can assign users/roles to scope/applications?
Regards, Bunty
-
0
Hi Bunty,
to achieve your goal to assign applications or scopes to users or roles you would need to implement a couple of custom components:
- An entity to store the assignments of users/roles to applications/scopes
- A domain manager to managing this entity
- A customer application service for crud operations for these assignments
- Custom ui for assigning users/roles to applications
With these points you just have the assignments. This wont affect any authentication flows or the applications shown on the Index-Page of the auth server.
To hide the applications, a user is not assigned to, on the Index-Page you would need to change the Index.cshtml logic to use your custom assignments and filter out applications not permitted to the user. The user would still be able to access the applications if he has the URLs.
If you really want to customize the signin flow for your applications you could override the SignInManager in the AuthServer Project and check if the user has access to the requested application by looking for an assignment to the application with your custom entity. Here is an example how to customize: https://github.com/abpframework/abp/blob/a1f521d5bf02ee54f2ee285cfdf54bd70b94d9e8/docs/en/Community-Articles/2020-04-19-Customize-the-SignIn-Manager/POST.md#L9 But as gterdem already stated: Authentication flows are standards and shouldn't be altered.
Hope this helps you.
Kind Regards Nico
-
0
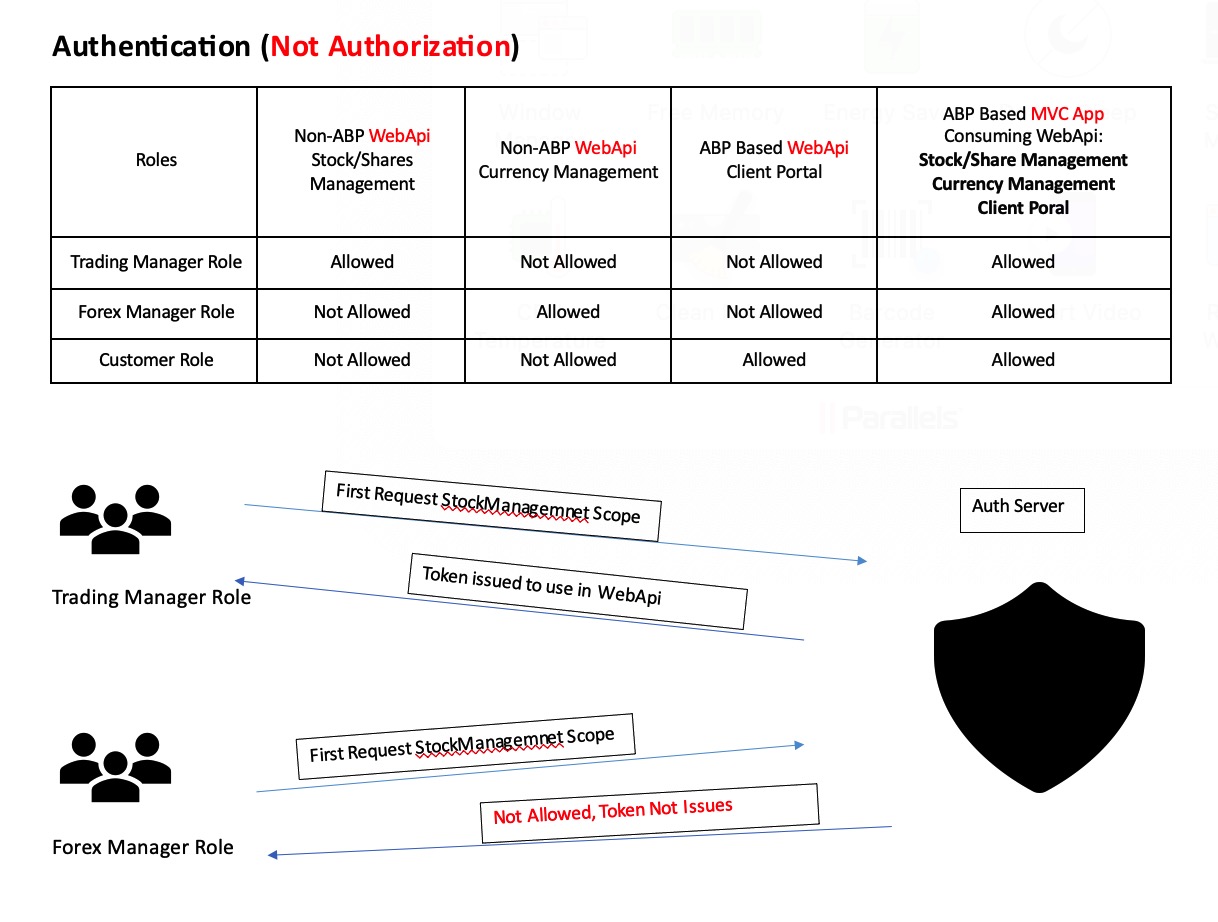
I will try to summarize the problem to define we're on the same page.
- You wan to add new non-ABP API's, namely Stock and Currency management, to your authentication environment so they can no longer be called anonymously.
- You want these non-ABP API's authorized by permissions and these permissions can be set from the ABP Permission Management UI.
Assuming you have an ABP application with all the administration etc and you want to consume these non-ABP apis from the ABP application. Correct me if I am missing anything here.
If that is the case; lets start with concluding that your issue is not related to LeptonX or AuthServer pages. Secondly, authentication and authorization are different concepts.
Authentication
This is related to your application making a request to a non-ABP API. So we start adding the API (resource) as a scope: Navigate to Administration->OpenId->Scopes and add a new scope:
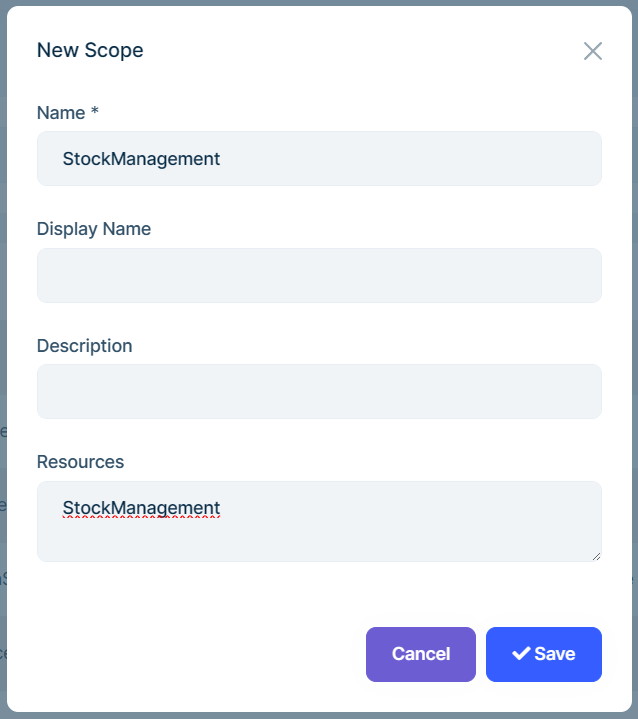
Define the HttpApi authentication:
context.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme) .AddJwtBearer(options => { options.Authority = https://myauthserver.url // your AuthServer url options.RequireHttpsMetadata = true; options.Audience = "StockManagement"; // This is the Resources section of your scope. Must be identical });After adding your new scope, update the application that will make request to this endpoint: Navigate to Administration->OpenId->Application and edit the application that will make the requests to this API:
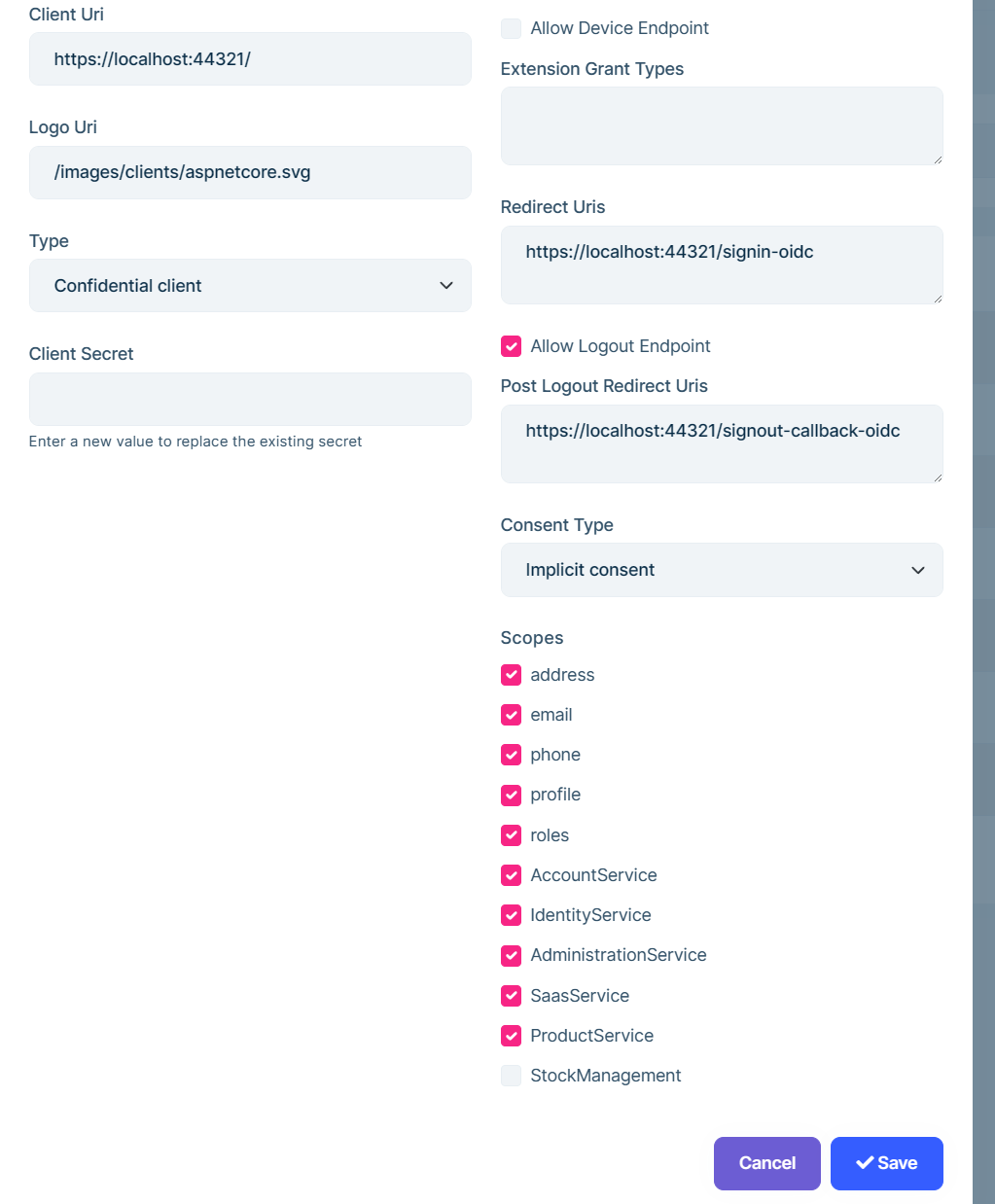 Select the StockManagement scope. This will make AuthServer to allow this application to be able make a request to the new resource.
Select the StockManagement scope. This will make AuthServer to allow this application to be able make a request to the new resource.Now, configure the application to request the new scope in the access_token by updating the application authentication configuration:
.AddAbpOpenIdConnect("oidc", options => { options.Authority = configuration["AuthServer:Authority"]; options.RequireHttpsMetadata = Convert.ToBoolean(configuration["AuthServer:RequireHttpsMetadata"]); options.ResponseType = OpenIdConnectResponseType.CodeIdToken; options.ClientId = configuration["AuthServer:ClientId"]; options.ClientSecret = configuration["AuthServer:ClientSecret"]; options.UsePkce = true; options.SaveTokens = true; options.GetClaimsFromUserInfoEndpoint = true; options.Scope.Add("roles"); options.Scope.Add("email"); options.Scope.Add("phone"); options.Scope.Add("TieredApp"); options.Scope.Add("StockManagement"); //The new scope name });Now, when the application sign-in process is completed, the token will be valid for the new resource and it will work with simple-authorization.
Authorization:
You can not add Policies to the api authorization and make them automatically permissions. What I mean by it is, adding something like
[Authorize("StockManagement.Create")] [HttpPost] [Route("/stock")] public Task<SomeDto> CreateStock(SomeInput input){ ... }will not make your non-ABP api endpoint authorized by permissions. In ABP, permissions are defined by the
PermissionDefinitionProviderand in a non-ABP application, you are not defining them. So, using the UI to set permissions for a non-ABP application is not possible. The easiest way can be using the simple authorization or maybe role-based authorization. I would give it a try for role-based authorization (like StockReader, CurrencyUpdater etc) so you can define roles from the UI.The Authentication and the Authorization for non-ABP applications/APIs are not related to the ABP framework.
Perhaps you want to use the Permission Management for a non-ABP API. It is not possible without making your app/api an ABP module. Please also see https://docs.abp.io/en/abp/latest/Authorization and https://docs.abp.io/en/abp/latest/Modules/Permission-Management for more information.
-
0
Hi gterdem and Nico,
Thank you both for giving me extensive help; it took me a little while to digest.
@gtendem: I agree with you that Authorization in Web API is not straight and after discussing with the client, we have decided that the client with handle Authorization by themself, I will be helping them only with Authentication. So, your above steps work perfectly to Authenticate.
@Nico: your suggestion to create an entity to assign User/Role to ~~Application or~~ Scope is perfect, as it supports the below scenario.
Is Controller right place to check if user/role has assigned scope?
Regards,
-
0
Yeah sure, you can use Controller or AppService, whichever suits for you.


 Limited Time Offer!
Limited Time Offer!