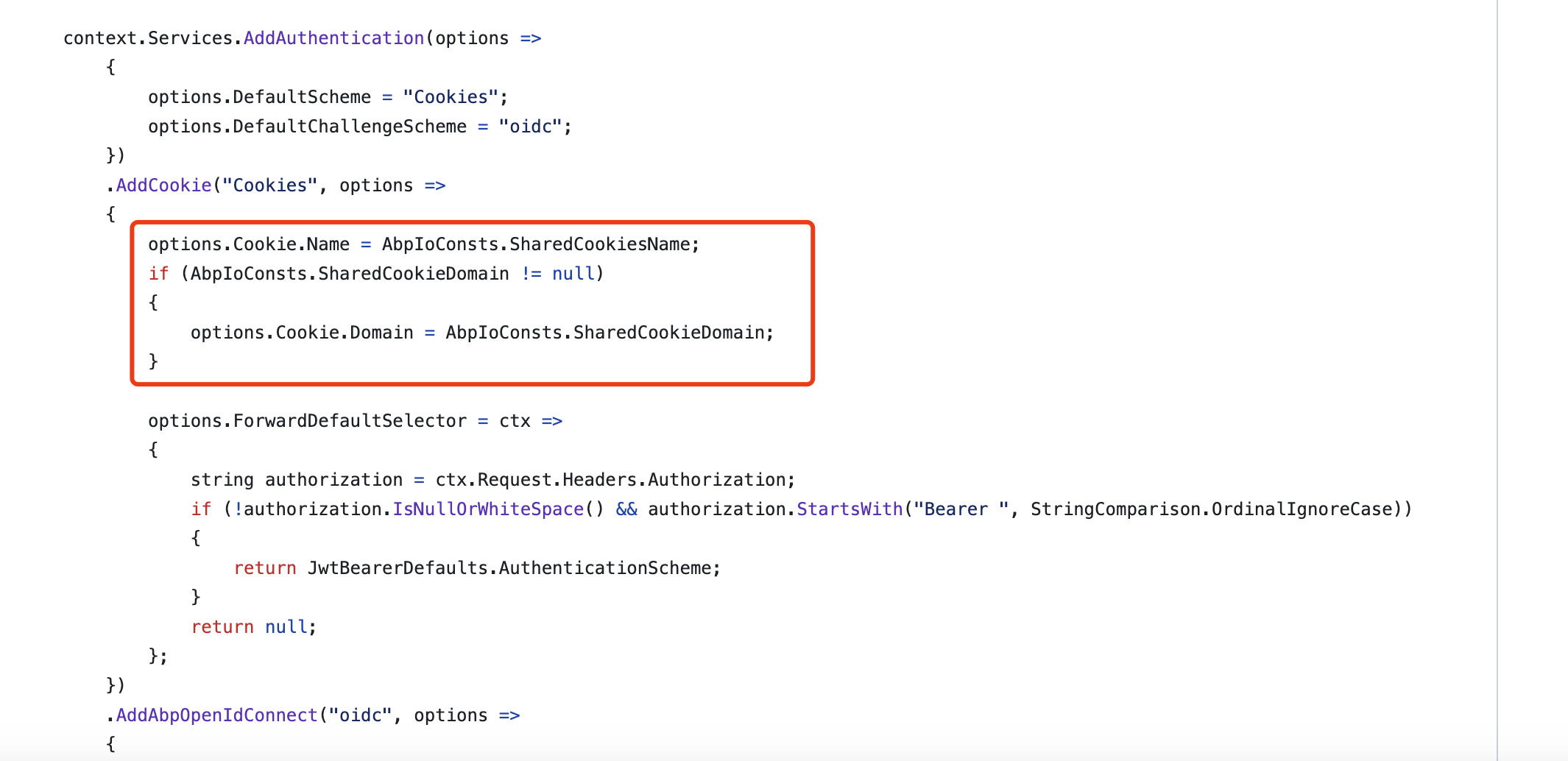
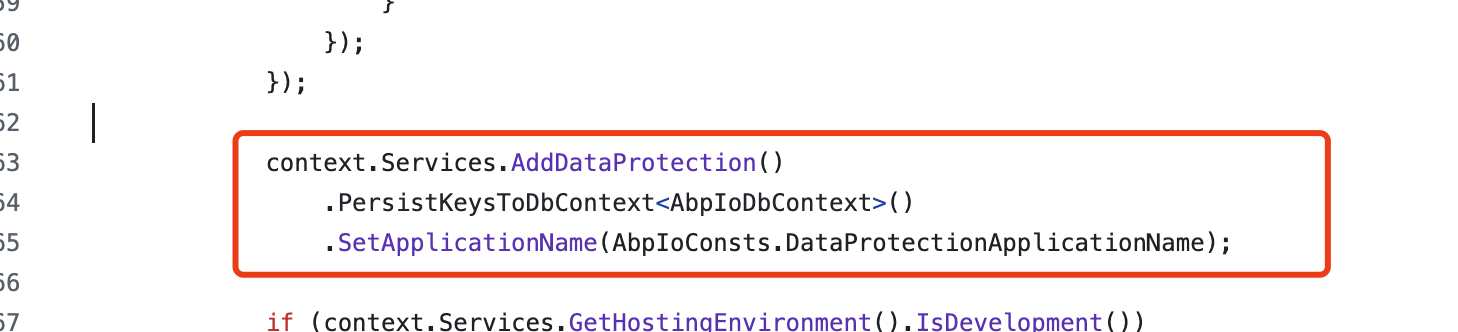
- ABP Framework version: 7.4.2
- UI Type: Angular
- Database System: EF Core (PostgreSQL)
- Tiered (for MVC) or Auth Server Separated (for Angular): yes
- Exception message and full stack trace:
- Steps to reproduce the issue:
- How to integrate SSO Integration Using OAuth2/OpenID Connect ?
- If above mentioned integrations possible with my current application, Could you please provide documentation/guides/steps to do the same.
However, I have added very high level analysis code please go thought it and let me know correct or not ?
Step 1: Add NuGet Packages
Ensure you have the following packages installed in our Gateway web project :
<PackageReference Include="Microsoft.AspNetCore.Authentication.OpenIdConnect" Version="5.0.0" />
<PackageReference Include="Microsoft.IdentityModel.Protocols.OpenIdConnect" Version="6.8.0" />
Step 2: Configure appsettings.json
Add the OpenIdConnect settings to gateway appsettings.json:
{
"Authentication": {
"OpenId": {
"Authority": "https://{yourOktaDomain}/oauth2/default",
"ClientId": "{yourClientId}",
"ClientSecret": "{yourClientSecret}",
"ResponseType": "code",
"SaveTokens": true,
"GetClaimsFromUserInfoEndpoint": true,
"Scope": "openid profile email"
}
}
}
3. Update the `ConfigureServices` and `Configure` methods to set up authentication:
//The code you provided configures authorization policies in your application,
specifically setting a default authorization policy that requires users to be authenticated
using either the primary JWT Bearer scheme or the OIDC JWT Bearer scheme.
private static void ConfigureAuthentication(ServiceConfigurationContext context, IConfiguration configuration)
{
context.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme)
.AddJwtBearer(JwtBearerDefaults.AuthenticationScheme, options =>
{
options.Authority = configuration["AuthServer:Authority"];
options.RequireHttpsMetadata = false;
options.Audience = configuration["AuthServer:ApiResource"];
})
.AddJwtBearer("OIDC", options =>
{
options.Audience = configuration["AuthServer:ApiResource"];
options.RequireHttpsMetadata = false;
options.Authority = configuration["AuthServer:Authority"];
});
Log.Information($"ApiResource: {configuration["AuthServer:ApiResource"]}");
// Authorization
context.Services.AddAuthorization(options =>
{
var defaultAuthorizationPolicyBuilder = new AuthorizationPolicyBuilder(
JwtBearerDefaults.AuthenticationScheme,
"OIDC");
defaultAuthorizationPolicyBuilder =
defaultAuthorizationPolicyBuilder.RequireAuthenticatedUser();
options.DefaultPolicy = defaultAuthorizationPolicyBuilder.Build();
});
}
public void ConfigureServices(IServiceCollection services)
{
need to discuss commented code
//services.AddAuthentication(options =>
// {
// options.DefaultScheme = CookieAuthenticationDefaults.AuthenticationScheme;
// options.DefaultChallengeScheme = OpenIdConnectDefaults.AuthenticationScheme;
//})
// .AddCookie()
.AddOpenIdConnect(OpenIdConnectDefaults.AuthenticationScheme, options =>
{
options.Authority = Configuration["Authentication:OpenId:Authority"];
options.ClientId = Configuration["Authentication:OpenId:ClientId"];
options.ClientSecret = Configuration["Authentication:OpenId:ClientSecret"];
options.ResponseType = Configuration["Authentication:OpenId:ResponseType"];
options.SaveTokens = Configuration["Authentication:OpenId:SaveTokens"];
options.GetClaimsFromUserInfoEndpoint = Configuration["Authentication:OpenId:GetClaimsFromUserInfoEndpoint"];
options.Scope.Add("openid");
options.Scope.Add("profile");
options.Scope.Add("email");
});
}
public override void OnApplicationInitialization(ApplicationInitializationContext context)
{
app.UseAuthentication();
app.UseAuthorization();
}
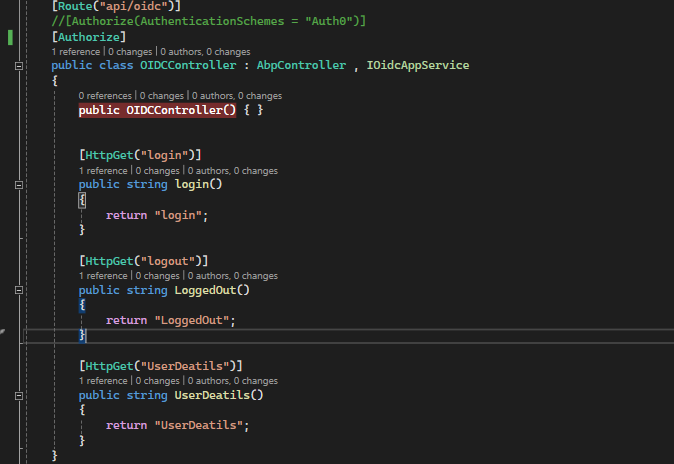
modules\Identity-core\src\Identity.HttpApi\Controllers\OIDC\OIDCController.cs
Note :- AuthenticationSchemes we can use Controllers or Method level as well
namespace Identity.Controllers.OIDC
{
[Route("api/OIDC")]
[Authorize(AuthenticationSchemes = "OIDC")]
public class OIDCController : AbpController, OIDCAppService
{
}
[Authorize("OIDC")]
public Task CreateAsync(CreateAuthorDto input)
{
}
all IDP end points.
}
12 Answer(s)
-
0
Hi,
To integrate SSO Integration, you need to share cookies between subdomains
see https://learn.microsoft.com/en-us/aspnet/core/security/cookie-sharing?view=aspnetcore-8.0
-
0
Thanks for response.
Above code i have mention is it correct way to implement for SSO. However, I'll add cookies code between subdomains.
-
0
Hi,
you don't need to add OAuth2 to the gateway.
-
0
Hi,
you don't need to add OAuth2 to the gateway.
But, Our identity server URL is configured in the API Gateway. Whenever I access any identity server API, I first redirect through the API Gateway, which then internally calls the identity server API.
However, If you have any references or step-by-step guidance on how to integrate OIDC SSO, could you please provide project link or details?
-
0
However, If you have any references or step-by-step guidance on how to integrate OIDC SSO, could you please provide project link or details?
To integrate SSO Integration, you basically only need to share cookies between subdomains
-
0
However, If you have any references or step-by-step guidance on how to integrate OIDC SSO, could you please provide project link or details?
To integrate SSO Integration, you basically only need to share cookies between subdomains
I am still confuse because as per below abp.io support ticket i have follow instruction. https://abp.io/support/questions/5427/HOW-TO-AUTHENTICATE-EXERNAL-SSO-TOKEN-WITH-ADMIN-APIS
You mentioned that the code I provided might not be necessary for handling SSO integration using cookies across subdomains. However, the step-by-step details are not clearly outlined. Could you provide a more detailed explanation or clarification? https://learn.microsoft.com/en-us/aspnet/core/security/cookie-sharing?view=aspnetcore-8.0
My requirement :- The users authenticated through an external SSO are not our application users; the only similarity is the email address. After the user is authenticated via SSO, authorization is managed within our application.
-
0
I am still confuse because as per below abp.io support ticket i have follow instruction. https://abp.io/support/questions/5427/HOW-TO-AUTHENTICATE-EXERNAL-SSO-TOKEN-WITH-ADMIN-APIS
here is talking about configure extra authentication. These are already configured by default in the abp template
You mentioned that the code I provided might not be necessary for handling SSO integration using cookies across subdomains. However, the step-by-step details are not clearly outlined. Could you provide a more detailed explanation or clarification? https://learn.microsoft.com/en-us/aspnet/core/security/cookie-sharing?view=aspnetcore-8.0
Here is abp.io how to configure SSO. You need to configure it for all applications
-
0
The users authenticated through an external SSO are not our application users; the only similarity is the email address. After the user is authenticated via SSO, authorization is managed within our application.
oh, you need to configure an external OIDC provider in the authserver project
https://abp.io/docs/latest/modules/account-pro#social-external-logins
-
0
The users authenticated through an external SSO are not our application users; the only similarity is the email address. After the user is authenticated via SSO, authorization is managed within our application.
oh, you need to configure an external OIDC provider in the authserver project
https://abp.io/docs/latest/modules/account-pro#social-external-logins
https://abp.io/support/questions/5427/HOW-TO-AUTHENTICATE-EXERNAL-SSO-TOKEN-WITH-ADMIN-APIS this support ticket also taking same right ?
-
0
https://abp.io/support/questions/5427/HOW-TO-AUTHENTICATE-EXERNAL-SSO-TOKEN-WITH-ADMIN-APIS this support ticket also taking same right ?
As i see, not same.
-
0
Hi Basically we have old abp.io template .NET core microservices. And i use below code in gateway as well as Identity server as well
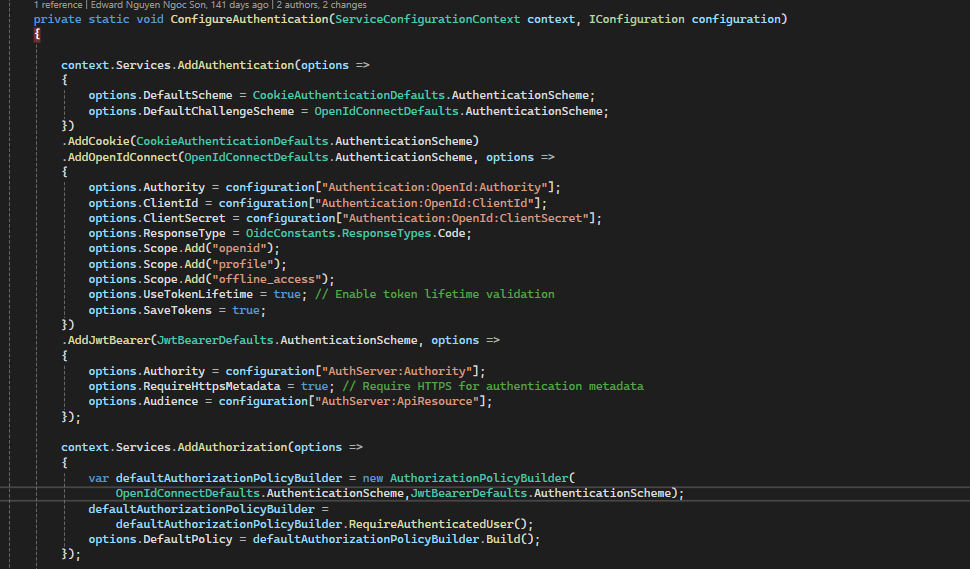
while access below end points facing issue
error System.InvalidOperationException: IDX20803: Unable to obtain configuration from: 'https://localhost:44350/.well-known/openid-configuration'. Will retry at '8/21/2024 8:41:25 AM +00:00'. Exception: 'System.TypeLoadException: Could not load type 'Microsoft.IdentityModel.Json.JsonConvert' from assembly 'Microsoft.IdentityModel.Tokens, Version=7.0.1.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35'. at Microsoft.IdentityModel.Protocols.OpenIdConnect.OpenIdConnectConfigurationRetriever.GetAsync(String address, IDocumentRetriever retriever, CancellationToken cancel) at System.Runtime.CompilerServices.AsyncMethodBuilderCore.Start[TStateMachine](TStateMachine& stateMachine) at Microsoft.IdentityModel.Protocols.OpenIdConnect.OpenIdConnectConfigurationRetriever.GetAsync(String address, IDocumentRetriever retriever, CancellationToken cancel) at Microsoft.IdentityModel.Protocols.OpenIdConnect.OpenIdConnectConfigurationRetriever.Microsoft.IdentityModel.Protocols.IConfigurationRetriever<Microsoft.IdentityModel.Protocols.OpenIdConnect.OpenIdConnectConfiguration>.GetConfigurationAsync(String address, IDocumentRetriever retriever, CancellationToken cancel) at Microsoft.IdentityModel.Protocols.ConfigurationManager
1.GetConfigurationAsync(CancellationToken cancel)'. ---> System.TypeLoadException: Could not load type 'Microsoft.IdentityModel.Json.JsonConvert' from assembly 'Microsoft.IdentityModel.Tokens, Version=7.0.1.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35'. at Microsoft.IdentityModel.Protocols.OpenIdConnect.OpenIdConnectConfigurationRetriever.GetAsync(String address, IDocumentRetriever retriever, CancellationToken cancel) at System.Runtime.CompilerServices.AsyncMethodBuilderCore.Start[TStateMachine](TStateMachine& stateMachine) at Microsoft.IdentityModel.Protocols.OpenIdConnect.OpenIdConnectConfigurationRetriever.GetAsync(String address, IDocumentRetriever retriever, CancellationToken cancel) at Microsoft.IdentityModel.Protocols.OpenIdConnect.OpenIdConnectConfigurationRetriever.Microsoft.IdentityModel.Protocols.IConfigurationRetriever<Microsoft.IdentityModel.Protocols.OpenIdConnect.OpenIdConnectConfiguration>.GetConfigurationAsync(String address, IDocumentRetriever retriever, CancellationToken cancel) at Microsoft.IdentityModel.Protocols.ConfigurationManager1.GetConfigurationAsync(CancellationToken cancel) --- End of inner exception stack trace --- at Microsoft.IdentityModel.Protocols.ConfigurationManager1.GetConfigurationAsync(CancellationToken cancel) at Microsoft.AspNetCore.Authentication.JwtBearer.JwtBearerHandler.HandleAuthenticateAsync() at Microsoft.AspNetCore.Authentication.JwtBearer.JwtBearerHandler.HandleAuthenticateAsync() at Microsoft.AspNetCore.Authentication.AuthenticationHandler1.AuthenticateAsync() at Microsoft.AspNetCore.Authentication.AuthenticationService.AuthenticateAsync(HttpContext context, String scheme) at Microsoft.AspNetCore.Authorization.Policy.PolicyEvaluator.AuthenticateAsync(AuthorizationPolicy policy, HttpContext context) at Microsoft.AspNetCore.Authorization.AuthorizationMiddleware.Invoke(HttpContext context) at Volo.Abp.AspNetCore.MultiTenancy.MultiTenancyMiddleware.InvokeAsync(HttpContext context, RequestDelegate next) at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext() --- End of stack trace from previous location --- at Microsoft.AspNetCore.Authentication.AuthenticationMiddleware.Invoke(HttpContext context) at SCV.Litmus.Shared.DecryptHttpHeadersMiddleware.InvokeAsync(HttpContext context, RequestDelegate next) in D:\Projects\core-platform-2\SCV.Litmus\aspnet-core\shared\SCV.Litmus.Shared\Middleware\DecryptHttpHeadersMiddleware.cs:line 51 at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext() --- End of stack trace from previous location --- at SCV.Litmus.Shared.DecryptHttpRequestMiddleware.InvokeAsync(HttpContext context, RequestDelegate next) in D:\Projects\core-platform-2\SCV.Litmus\aspnet-core\shared\SCV.Litmus.Shared\Middleware\DecryptHttpRequestMiddleware.cs:line 103 at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext() --- End of stack trace from previous location --- at SCV.Litmus.LitmusHttpApiHostModule.<>c.<<OnApplicationInitialization>b__12_0>d.MoveNext() in D:\Projects\core-platform-2\SCV.Litmus\aspnet-core\gateways\SCV.Litmus.HttpApi.Host\LitmusHttpApiHostModule.cs:line 683 --- End of stack trace from previous location --- at Microsoft.AspNetCore.Localization.RequestLocalizationMiddleware.Invoke(HttpContext context) at Microsoft.AspNetCore.RequestLocalization.AbpRequestLocalizationMiddleware.InvokeAsync(HttpContext context, RequestDelegate next) at Microsoft.AspNetCore.Builder.UseMiddlewareExtensions.<>c__DisplayClass6_1.<<UseMiddlewareInterface>b__1>d.MoveNext() --- End of stack trace from previous location --- at Microsoft.AspNetCore.Diagnostics.DeveloperExceptionPageMiddlewareImpl.Invoke(HttpContext context)How to fix this error
It's High priority task, However, can you please setup call, we can connect resolve this error.
-
0
System.TypeLoadException: Could not load type 'Microsoft.IdentityModel.Json.JsonConvert' from assembly 'Microsoft.IdentityModel.Tokens, Version=7.0.1.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35'.See https://github.com/AzureAD/azure-activedirectory-identitymodel-extensions-for-dotnet/issues/2346
you can reference to
Microsoft.IdentityModel.Json.JsonConvertdirectly