I will try to summarize the problem to define we're on the same page.
Assuming you have an ABP application with all the administration etc and you want to consume these non-ABP apis from the ABP application. Correct me if I am missing anything here.
If that is the case; lets start with concluding that your issue is not related to LeptonX or AuthServer pages. Secondly, authentication and authorization are different concepts.
This is related to your application making a request to a non-ABP API. So we start adding the API (resource) as a scope:
Navigate to Administration->OpenId->Scopes and add a new scope:
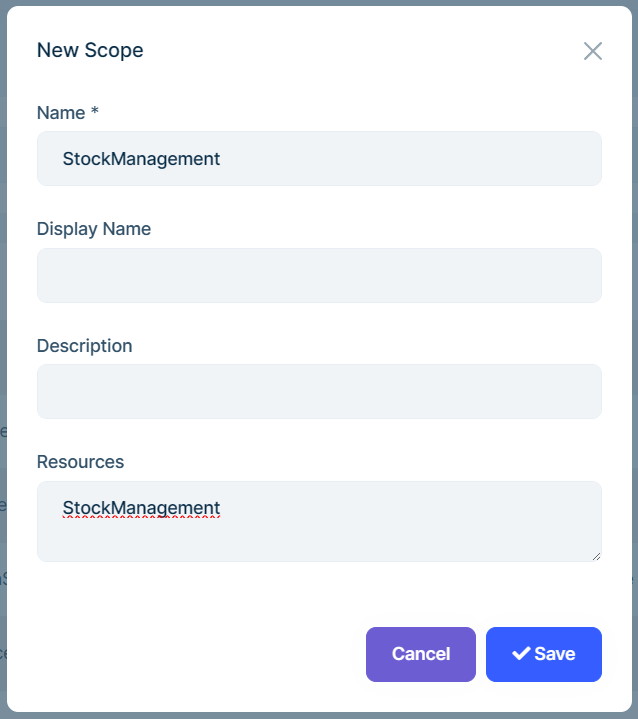
Define the HttpApi authentication:
context.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme)
.AddJwtBearer(options =>
{
options.Authority = https://myauthserver.url // your AuthServer url
options.RequireHttpsMetadata = true;
options.Audience = "StockManagement"; // This is the Resources section of your scope. Must be identical
});
After adding your new scope, update the application that will make request to this endpoint:
Navigate to Administration->OpenId->Application and edit the application that will make the requests to this API:
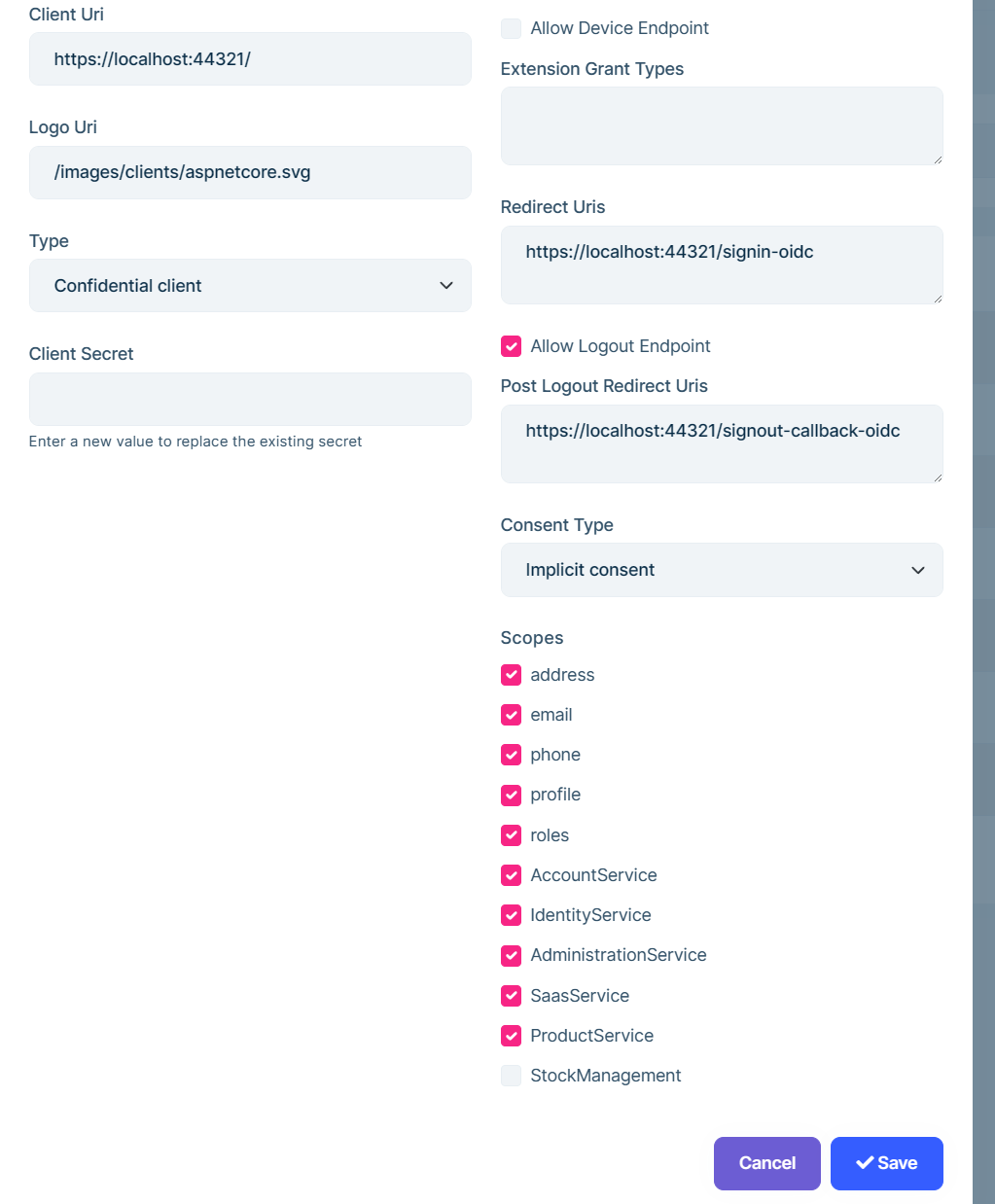 Select the StockManagement scope. This will make AuthServer to allow this application to be able make a request to the new resource.
Select the StockManagement scope. This will make AuthServer to allow this application to be able make a request to the new resource.
Now, configure the application to request the new scope in the access_token by updating the application authentication configuration:
.AddAbpOpenIdConnect("oidc", options =>
{
options.Authority = configuration["AuthServer:Authority"];
options.RequireHttpsMetadata = Convert.ToBoolean(configuration["AuthServer:RequireHttpsMetadata"]);
options.ResponseType = OpenIdConnectResponseType.CodeIdToken;
options.ClientId = configuration["AuthServer:ClientId"];
options.ClientSecret = configuration["AuthServer:ClientSecret"];
options.UsePkce = true;
options.SaveTokens = true;
options.GetClaimsFromUserInfoEndpoint = true;
options.Scope.Add("roles");
options.Scope.Add("email");
options.Scope.Add("phone");
options.Scope.Add("TieredApp");
options.Scope.Add("StockManagement"); //The new scope name
});
Now, when the application sign-in process is completed, the token will be valid for the new resource and it will work with simple-authorization.
You can not add Policies to the api authorization and make them automatically permissions. What I mean by it is, adding something like
[Authorize("StockManagement.Create")]
[HttpPost]
[Route("/stock")]
public Task<SomeDto> CreateStock(SomeInput input){
...
}
will not make your non-ABP api endpoint authorized by permissions. In ABP, permissions are defined by the PermissionDefinitionProvider and in a non-ABP application, you are not defining them. So, using the UI to set permissions for a non-ABP application is not possible.
The easiest way can be using the simple authorization or maybe role-based authorization. I would give it a try for role-based authorization (like StockReader, CurrencyUpdater etc) so you can define roles from the UI.
The Authentication and the Authorization for non-ABP applications/APIs are not related to the ABP framework.
Perhaps you want to use the Permission Management for a non-ABP API. It is not possible without making your app/api an ABP module. Please also see https://docs.abp.io/en/abp/latest/Authorization and https://docs.abp.io/en/abp/latest/Modules/Permission-Management for more information.
We've created internal issue related to this. It will be fixed in the next minor or major patch based on Angular team's workload.
I've refunded your credit.
Thank you.
Thank you very much for your help. Really appreciate it. Can you explain the problem a bit? I see you didn't event look at our repo. Maybe there is some temporary workaround while you release commercial fix?
This seems directly related to Angular application in the microservice template. One of our friends from the Angular team will be working on it since I don't have enough knowledge about the Angular. Hence, I don't know about the workaround either.
Hi gterdem,
Many thx for replying on behalf of Anjali, I will try your suggestions, however, I am still not sure how to pre-authenticated only selected users, if you look at the screenshot earlier, I want to control users' access to the application and in generating token via https://localhost:44359/connect/token
Regards, Navneet
You can not pre-authenticate some selected users without initiating a signin process. Authentication flows are standards and shouldn't be altered.
When a user is signed into AuthServer and you want the user to login to one of the applications in the AuthServer environment without re-entering the credentials; you can simply put an [Authorize] attribute to the Home/Index page of the application. When the signed-in user navigates to the authenticated Home/Index of the application, the SSO will kick in and the user will automatically login to the application without re-entering the credentials.
If what you want to do is different than this and want to alter the authentication manually; it is not related to ABP and you can find better help on StackOverflow about changing the authentication flows of OpenIdConnect.
We've created internal issue related to this. It will be fixed in the next minor or major patch based on Angular team's workload.
I've refunded your credit.
Thank you.
Did you try the LichArnold's solution at https://support.abp.io/QA/Questions/5638/How-to-enable-ABP-Commercial-host-tenant-mapping-feature-in-ABP-commercial-microservices-solution#answer-3a0d8f61-d8d7-8289-06cd-6c106915fe24 ?
@mahmut.gundogdu Did we have updates on v7.4 based on this issue?
I did not try no. I believe it supposed to work out of the box? My thought was because of lack of samples and documentation maybe i misconfigured feature.
I created a separate github repo where i can reproduce the issue for this feature.
Please do share the github repository if its non-commercial or you can add galiperdem@gmail.com if it is commercial and private repository.
We've fixed the problem and will be available in the next patch.
I've refunded your ticket, thank you.
There is no such thing like pre-authenticated.
You can put [Authorize] attribute to your MVC app Home/Index page (or whatever authorized page you want) and allow clicking to this link from AuthServer to initiate SSO process.
iFrame is not a suggested component for any Authentication process because of security reasons and blocked by browsers reasons mainly based on phishing attacks.
Thank you, I'll try it with the v7.4 microservice template and let you know.

