- ABP Framework version: v8.2.1
- UI Type: Angular
- Database System: EF Core (MySQL)
- Tiered (for MVC) or Auth Server Separated (for Angular): yes, Angular with Microservice Architecture
- Exception message and full stack trace:
- Steps to reproduce the issue:
Hello Team,
We have a microservices based architecture solution for our project. We don't want to use the TenantId in the AbpUsers and AbpRoles tables as per our requirements. For that what we have done is, we have kept separate tables (UserTenantAssociation and RoleTenantAssociation), using these tables we will determine which user belongs to which Tenant. And for the Roles, we will have all the Roles in the AbpRoles table with all records having TenantId as NULL, which implies the Roles will be created only in the Host Tenant and not any other Tenant. The other Tenants will be using the same Roles as Host, and which Tenants have which specific Roles to use in their tenant, that will be determined using our custom RoleTenantAssociation table where RoleId (the Id of the role from the host tenant) and the TenantId of that Tenant will be stored).
Now, displaying the list of Roles and Users on the UI doesn't seem to be a problem as we have already done necessary changes in the Users and Roles repositories in the IdentityService to achiever this feat. But the problem arises when the User logs into the Tenants.
Let's say I have a User which belongs to a Tenant, and the User has a role assigned to it as "admin", now in the AbpUserRoles table, the UserId will be the Id of the User from AbpUsers table, TenantId will be TenantId of the Tenant in which the user is trying to log into and the RoleId will be the Id of the Role "admin" from AbpRoles table but it will have TenantId as NULL as the Role belongs to the Host and the same Role should be used by all the Tenants.
Now if we run the application and when the user logs into a Tenant, it doesn't have any Roles assigned to it in the CurrentUser class, and also the GrantedPolicies will also be empty since there are no roles assigned to the user in the currentUser section of application configuration api call.
I tried to check how the values are assigned to the CurrentUser, and I came to know that it gets the values from the Claims generated during the Authentication and are passed to JWT Token during the authentication.
https://github.com/abpframework/abp/blob/8e20aab617205936c299ed5c3c40e0c529a3f06b/modules/identity/src/Volo.Abp.Identity.Domain/Volo/Abp/Identity/AbpUserClaimsPrincipalFactory.cs#L14
this is the code I tried :
public class AbpUserClaimsPrincipalFactory : UserClaimsPrincipalFactory<IdentityUser, IdentityRole>, ITransientDependency { public AbpUserClaimsPrincipalFactory( UserManager<IdentityUser> userManager, RoleManager<IdentityRole> roleManager, IOptions<IdentityOptions> options) : base( userManager, roleManager, options) { }
[UnitOfWork]
public override async Task<ClaimsPrincipal> CreateAsync(IdentityUser user)
{
var principal = await base.CreateAsync(user).ConfigureAwait(false);
if (user.TenantId.HasValue)
{
principal.Identities
.First()
.AddClaim(new Claim(AbpClaimTypes.TenantId, user.TenantId.ToString()));
}
return principal;
}
}
(I tried this code in Administration Service Domain project)
but when using it, the login page will just stay there even after clicking the login button with correct credentials, it doesn't redirect to the angular app.
I want to know how exactly the CurrentUser is assigned these values and I want to override it because we have different logic of fetching the roles (from our custom table). I specifically want to know how the roles are assigned to the current user.
Right now, what I have done is, I have manually updated the value of the RoleId in the AbpUserRoles table, I have updated the RoleId with the one which belongs to the host. And because of that when the user logs into the application, there in, the api/abp/application-configuration?includeLocalizationResources=false api is called and in response of that API call, the grantedPolicies in the "auth" section is an empty array and in the "currentUser" section the roles is an empty array.
example : { "auth": { "grantedPolicies": [] }, "currentUser": { "roles": [], }, } So, given the scenario, how exactly can I set these granted policies and the currentUser values in the application when the user logs in?
94 Answer(s)
-
0
hi
So, given the scenario, how exactly can I set these granted policies and the currentUser values in the application when the user logs in?
Can you set a breakpoint after
Authenticationto check the claims of theHttpContext.Userfirst?app.UseAuthentication(); app.UseAbpOpenIddictValidation(); app.Use(async (ctx, next) => { //check the claims of the HttpContext.User await next(ctx); });The values of
currentUsercome from the claims.https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.Security/Volo/Abp/Users/CurrentUser.cs#L14-L34
https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.AspNetCore/Volo/Abp/AspNetCore/Security/Claims/HttpContextCurrentPrincipalAccessor.cs
-
0
I saved the Claims in a txt file, this is what I got :
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: iss ValueType: http://www.w3.org/2001/XMLSchema#string Value: https://test2dev.localhost:44322/ OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: exp ValueType: http://www.w3.org/2001/XMLSchema#integer64 Value: 1726205828 OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: iat ValueType: http://www.w3.org/2001/XMLSchema#integer64 Value: 1726202228 OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: AccountService OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: IdentityService OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: AdministrationService OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: SaasService OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: ProductService OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: ClinicService OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: AppointmentService OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: FormsService OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: scope ValueType: http://www.w3.org/2001/XMLSchema#string Value: offline_access openid profile email phone AccountService IdentityService AdministrationService SaasService ProductService ClinicService AppointmentService FormsService OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: jti ValueType: http://www.w3.org/2001/XMLSchema#string Value: 97cbc847-f151-4a24-b637-898808040e38 OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: sub ValueType: http://www.w3.org/2001/XMLSchema#string Value: 3a0daa97-5fba-2079-563c-3e26309bdc81 OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: tenantid ValueType: http://www.w3.org/2001/XMLSchema#string Value: 3a0daa97-5b6d-e661-4f00-22309be7478d OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: session_id ValueType: http://www.w3.org/2001/XMLSchema#string Value: e37331a7-978c-43ea-ab51-a4a24587245f OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: unique_name ValueType: http://www.w3.org/2001/XMLSchema#string Value: admin OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: oi_prst ValueType: http://www.w3.org/2001/XMLSchema#string Value: Angular OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: oi_au_id ValueType: http://www.w3.org/2001/XMLSchema#string Value: 3a14ecaf-dae0-d535-4201-7197e6e3092e OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: preferred_username ValueType: http://www.w3.org/2001/XMLSchema#string Value: admin OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: given_name ValueType: http://www.w3.org/2001/XMLSchema#string Value: admin OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: email ValueType: http://www.w3.org/2001/XMLSchema#string Value: safwan@gmail.com OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: email_verified ValueType: http://www.w3.org/2001/XMLSchema#string Value: False OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: phone_number_verified ValueType: http://www.w3.org/2001/XMLSchema#string Value: False OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: client_id ValueType: http://www.w3.org/2001/XMLSchema#string Value: Angular OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: https://test2dev.localhost:44322/ Type: oi_tkn_id ValueType: http://www.w3.org/2001/XMLSchema#string Value: 3a14fbd8-86fd-8c6a-7c4a-471d72770d1f OriginalIssuer: https://test2dev.localhost:44322/ Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_tkn_typ ValueType: http://www.w3.org/2001/XMLSchema#string Value: access_token OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_crt_dt ValueType: http://www.w3.org/2001/XMLSchema#string Value: Fri, 13 Sep 2024 04:37:08 GMT OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_exp_dt ValueType: http://www.w3.org/2001/XMLSchema#string Value: Fri, 13 Sep 2024 05:37:08 GMT OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: AccountService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: IdentityService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: AdministrationService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: SaasService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: ProductService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: ClinicService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: AppointmentService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_aud ValueType: http://www.w3.org/2001/XMLSchema#string Value: FormsService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: offline_access OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: openid OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: profile OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: email OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: phone OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: AccountService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: IdentityService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: AdministrationService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: SaasService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: ProductService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: ClinicService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: AppointmentService OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: oi_scp ValueType: http://www.w3.org/2001/XMLSchema#string Value: FormsService OriginalIssuer: LOCAL AUTHORITY Properties:
-
0
The values of currentUser come from the claims.
https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.Security/Volo/Abp/Users/CurrentUser.cs#L14-L34
https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.AspNetCore/Volo/Abp/AspNetCore/Security/Claims/HttpContextCurrentPrincipalAccessor.cs
Based on your claim type, you can set
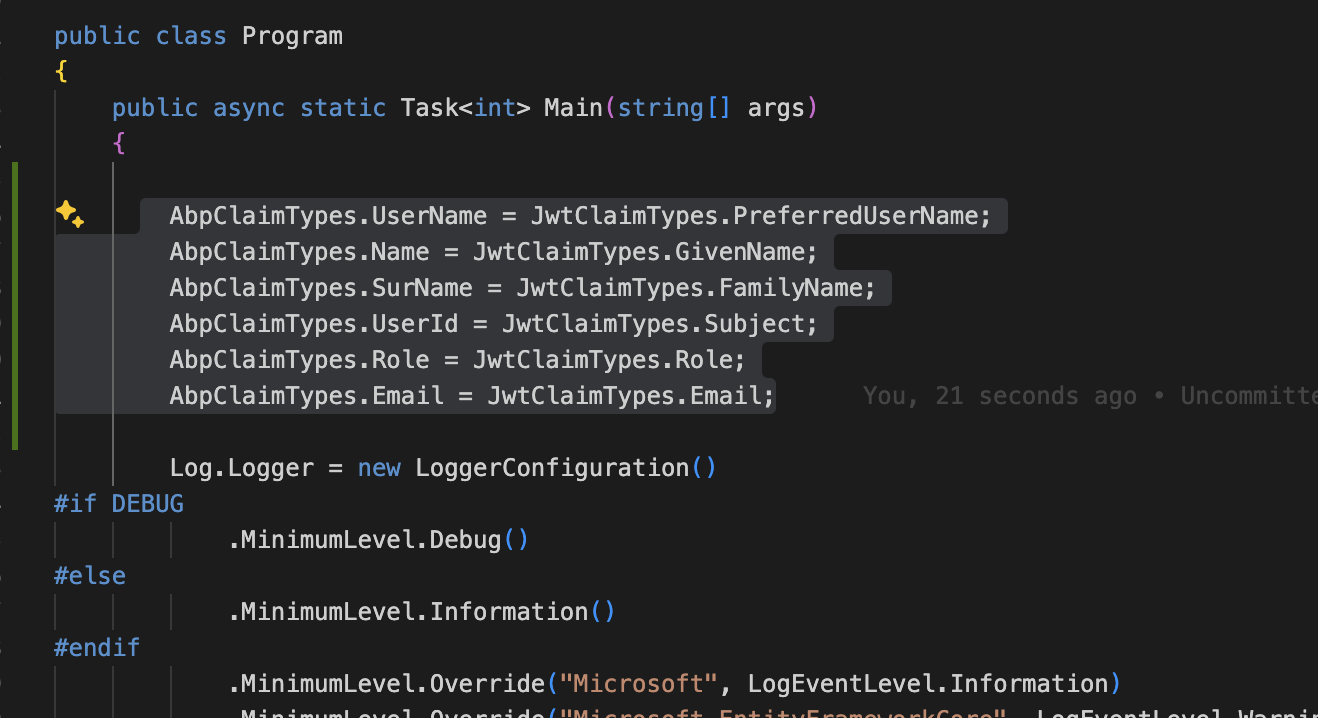
AbpClaimTypeslike below:AbpClaimTypes.UserName = JwtClaimTypes.PreferredUserName; AbpClaimTypes.Name = JwtClaimTypes.GivenName; AbpClaimTypes.SurName = JwtClaimTypes.FamilyName; AbpClaimTypes.UserId = JwtClaimTypes.Subject; AbpClaimTypes.Role = JwtClaimTypes.Role; AbpClaimTypes.Email = JwtClaimTypes.Email;I have an article you can check https://abp.io/community/articles/how-claim-type-works-in-asp-net-core-and-abp-framework-km5dw6g1
-
0
I have 2 tenants with which I am working, one is using the typical ABP Framework functionalities where I am not configuring anything for Roles and Users and another tenant where I am using the functionality for Roles and User which I mentioned earlier (custom tables for Roles and Users). I logged in with the admin users in both the tenants one by one and I took the bearer tokens from the API calls for both.
I then decoded both the tokens on jwt.io, and this is what I got :
Tenant without any configurations :
{ "iss": "https://testdev.localhost:44322/", "exp": 1726231353, "iat": 1726227753, "aud": [ "AccountService", "IdentityService", "AdministrationService", "SaasService", "ProductService", "ClinicService", "AppointmentService", "FormsService" ], "scope": "offline_access openid profile email phone AccountService IdentityService AdministrationService SaasService ProductService ClinicService AppointmentService FormsService", "jti": "66a31ba9-3f34-4b08-99eb-1af568b2f9aa", "sub": "3a104ca8-2d0b-0494-3653-5e7e48633bd5", "tenantid": "3a104ca8-1855-db3b-b3ff-111fbf324753", "session_id": "8f3fd4b7-af95-4010-84c6-ae1f3ee5c927", "unique_name": "admin", "oi_prst": "Angular", "oi_au_id": "3a104cb2-5231-d25e-fb31-c2164327d46f", "preferred_username": "admin", "given_name": "admin", "role": [ "viewProfile", "admin" ], "email": "admin@cureandcare.com", "email_verified": "False", "phone_number_verified": "False", "client_id": "Angular", "oi_tkn_id": "3a14fd5e-03f3-c2ee-dee4-f8748f5e4497" }
Tenant with my overridden configurations for Roles and Users :
{ "iss": "https://test2dev.localhost:44322/", "exp": 1726231274, "iat": 1726227674, "aud": [ "AccountService", "IdentityService", "AdministrationService", "SaasService", "ProductService", "ClinicService", "AppointmentService", "FormsService" ], "scope": "offline_access openid profile email phone AccountService IdentityService AdministrationService SaasService ProductService ClinicService AppointmentService FormsService", "jti": "cccb1c53-8fa5-499a-93c9-3f432a7af6a1", "sub": "3a0daa97-5fba-2079-563c-3e26309bdc81", "tenantid": "3a0daa97-5b6d-e661-4f00-22309be7478d", "session_id": "07e566b7-b6f9-4415-8c16-681606f245a4", "unique_name": "admin", "oi_prst": "Angular", "oi_au_id": "3a14ecaf-dae0-d535-4201-7197e6e3092e", "preferred_username": "admin", "given_name": "admin", "email": "safwan@gmail.com", "email_verified": "False", "phone_number_verified": "False", "client_id": "Angular", "oi_tkn_id": "3a14fd5c-cdc9-8b1a-c475-2c611fd52277" }
If you notice here, the token in which I did my configurations is missing the "roles" property, so conclusively, the roles aren't getting passed at first place when the JWT token creation is occurring. How do I deal with that? Where can I check what roles are being passed when the token is created?
-
0
Any updates?
-
0
Hi Team, I tried one method to update the roles of the User in the Claims.
What I did is I added this class in my AuthServer
using G1.health.ClinicService.ClinicSetup; using G1.health.IdentityService.Users; using Microsoft.AspNetCore.Identity; using Microsoft.Extensions.Options; using System.Security.Claims; using System.Threading.Tasks; using Volo.Abp.DependencyInjection; using Volo.Abp.Security.Claims; using Volo.Abp.Uow;
namespace G1.health.AuthServer;
public class AbpUserClaimsPrincipalFactory : UserClaimsPrincipalFactory<Volo.Abp.Identity.IdentityUser, Volo.Abp.Identity.IdentityRole>, ITransientDependency { protected ICurrentPrincipalAccessor CurrentPrincipalAccessor { get; } protected IAbpClaimsPrincipalFactory AbpClaimsPrincipalFactory { get; } protected IdentityUserManager IdentityUserManager { get; }
public AbpUserClaimsPrincipalFactory( UserManager<Volo.Abp.Identity.IdentityUser> userManager, RoleManager<Volo.Abp.Identity.IdentityRole> roleManager, IOptions<IdentityOptions> options, ICurrentPrincipalAccessor currentPrincipalAccessor, IAbpClaimsPrincipalFactory abpClaimsPrincipalFactory, IdentityUserManager identityUserManager) : base( userManager, roleManager, options) { CurrentPrincipalAccessor = currentPrincipalAccessor; AbpClaimsPrincipalFactory = abpClaimsPrincipalFactory; IdentityUserManager = identityUserManager; } [UnitOfWork] protected override async Task<ClaimsIdentity> GenerateClaimsAsync(Volo.Abp.Identity.IdentityUser user) { var id = await base.GenerateClaimsAsync(user).ConfigureAwait(false); if (UserManager.SupportsUserRole) { -- the next line is my code which I have written to fetch the roles for the user var roles = await IdentityUserManager.GetRoleNamesAsync(user).ConfigureAwait(false); foreach (var roleName in roles) { id.AddClaim(new Claim(Options.ClaimsIdentity.RoleClaimType, roleName)); if (RoleManager.SupportsRoleClaims) { var role = await RoleManager.FindByNameAsync(roleName).ConfigureAwait(false); if (role != null) { id.AddClaims(await RoleManager.GetClaimsAsync(role).ConfigureAwait(false)); } } } } return id; }}
And added the pre-configuration of this class in my module.cs class of AuthServer:
public override void PreConfigureServices(ServiceConfigurationContext context) { --- other configuration --- PreConfigure<IdentityBuilder>(builder => { builder.AddClaimsPrincipalFactory<AbpUserClaimsPrincipalFactory>(); }); }And I again checked the claims of the current user as you mentioned earlier and I got "admin" as a "role" claim for the user I am trying to log in with, but after clicking on the Login button, it would just stay on the same login page and it won't redirect to the angular app.
-
0
hi
var roles = await IdentityUserManager.GetRoleNamesAsync(user).ConfigureAwait(false);Does the
roleshave any values?Please share the
Logsduring your login process. -
0
Yes, the roles has value as a list, which has one value in it, which is "admin"
-
0
ok, Please share the Debug Logs during your login process.
-
0
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: sub ValueType: http://www.w3.org/2001/XMLSchema#string Value: 3a0daa97-5fba-2079-563c-3e26309bdc81 OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: preferred_username ValueType: http://www.w3.org/2001/XMLSchema#string Value: admin OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: email ValueType: http://www.w3.org/2001/XMLSchema#string Value: safwan@gmail.com OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: AspNet.Identity.SecurityStamp ValueType: http://www.w3.org/2001/XMLSchema#string Value: 6DCVHJYKEIHLAYOAR3SQBAPWS23CADJ5 OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: role ValueType: http://www.w3.org/2001/XMLSchema#string Value: admin OriginalIssuer: LOCAL AUTHORITY Properties:
Subject: System.Security.Claims.ClaimsIdentity Issuer: LOCAL AUTHORITY Type: amr ValueType: http://www.w3.org/2001/XMLSchema#string Value: pwd OriginalIssuer: LOCAL AUTHORITY Properties:
I got this as the claims when ran this
app.Use(async (ctx, next) => { //check the claims of the HttpContext.User // I have captured the values in a txt file here await next(ctx); });
-
0
Have you set claim types?
AbpClaimTypes.UserName = JwtClaimTypes.PreferredUserName; AbpClaimTypes.Name = JwtClaimTypes.GivenName; AbpClaimTypes.SurName = JwtClaimTypes.FamilyName; AbpClaimTypes.UserId = JwtClaimTypes.Subject; AbpClaimTypes.Role = JwtClaimTypes.Role; AbpClaimTypes.Email = JwtClaimTypes.Email; -
0
No I am not doing this manually anywhere
-
0
You can try to add it to the
Program.csclass. Then check theICurrentUser. -
0
Can you show me an example, how can I do that?
-
0
-
0
I tried this, and the CurrentUser is getting updated with the current values, the Roles property is also coming as expected, but when clicking on Login button, it stays on the same login page instead of redirecting to the angular page. And even for the first time, it does redirect to the angular, but it returns back to the login page, I tried to debug it, and I understood that the ReturnUrl property is coming in as NULL.
-
0
hi
but when clicking on Login button, it stays on the same login page instead of redirecting to the angular page.
Please share the Debug logs for these requests.
liming.ma@volosoft.com
-
0
2024-09-17 11:35:43.906 +05:30 [INF] Request starting HTTP/2 POST https://test2dev.localhost:44322/Account/Login - application/x-www-form-urlencoded 2272 2024-09-17 11:35:43.921 +05:30 [INF] CORS policy execution failed. 2024-09-17 11:35:43.921 +05:30 [INF] Request origin https://test2dev.localhost:44322 does not have permission to access the resource. 2024-09-17 11:35:43.922 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri. 2024-09-17 11:35:43.922 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri. 2024-09-17 11:35:43.922 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType. 2024-09-17 11:35:43.922 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType. 2024-09-17 11:35:43.922 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement. 2024-09-17 11:35:43.922 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader. 2024-09-17 11:35:43.925 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ValidateHostHeader. 2024-09-17 11:35:43.925 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+EvaluateValidatedTokens. 2024-09-17 11:35:43.925 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromAuthorizationHeader. 2024-09-17 11:35:43.932 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromBodyForm. 2024-09-17 11:35:43.932 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ExtractAccessTokenFromQueryString. 2024-09-17 11:35:43.932 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens. 2024-09-17 11:35:43.932 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessAuthenticationContext was marked as rejected by OpenIddict.Validation.OpenIddictValidationHandlers+ValidateRequiredTokens. 2024-09-17 11:35:43.932 +05:30 [DBG] AuthenticationScheme: OpenIddict.Validation.AspNetCore was not authenticated. 2024-09-17 11:35:43.935 +05:30 [INF] Executing endpoint '/Account/Login' 2024-09-17 11:35:43.935 +05:30 [INF] Route matched with {page = "/Account/Login", area = "", action = "", controller = ""}. Executing page /Account/Login 2024-09-17 11:35:43.935 +05:30 [INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy 2024-09-17 11:35:43.976 +05:30 [INF] Executing handler method G1.health.AuthServer.Pages.Account.LoginModel.OnPostAsync - ModelState is "Valid" 2024-09-17 11:35:44.006 +05:30 [INF] Start processing HTTP request POST https://www.google.com/recaptcha/api/siteverify 2024-09-17 11:35:44.007 +05:30 [INF] Sending HTTP request POST https://www.google.com/recaptcha/api/siteverify 2024-09-17 11:35:44.249 +05:30 [INF] Received HTTP response headers after 239.074ms - 200 2024-09-17 11:35:44.250 +05:30 [INF] End processing HTTP request after 245.845ms - 200 2024-09-17 11:35:46.461 +05:30 [ERR] SessionId is null. It's not possible to save the session. 2024-09-17 11:35:46.462 +05:30 [INF] AuthenticationScheme: Identity.Application signed in. 2024-09-17 11:35:47.316 +05:30 [DBG] Added 0 entity changes to the current audit log 2024-09-17 11:35:47.341 +05:30 [DBG] Added 0 entity changes to the current audit log 2024-09-17 11:35:47.445 +05:30 [INF] Executed handler method OnPostAsync, returned result Microsoft.AspNetCore.Mvc.RedirectResult. 2024-09-17 11:35:47.450 +05:30 [DBG] Added 0 entity changes to the current audit log 2024-09-17 11:35:47.452 +05:30 [INF] Executing RedirectResult, redirecting to /. 2024-09-17 11:35:47.453 +05:30 [INF] Executed page /Account/Login in 3517.0862ms 2024-09-17 11:35:47.453 +05:30 [INF] Executed endpoint '/Account/Login' 2024-09-17 11:35:47.455 +05:30 [DBG] Added 0 entity changes to the current audit log 2024-09-17 11:35:48.117 +05:30 [DBG] Added 0 entity changes to the current audit log 2024-09-17 11:35:48.124 +05:30 [DBG] Added 0 entity changes to the current audit log 2024-09-17 11:35:48.176 +05:30 [INF] Request finished HTTP/2 POST https://test2dev.localhost:44322/Account/Login - 302 null null 4269.0396ms 2024-09-17 11:35:48.191 +05:30 [INF] Request starting HTTP/2 GET https://test2dev.localhost:44322/ - null null 2024-09-17 11:35:48.200 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri. 2024-09-17 11:35:48.200 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri. 2024-09-17 11:35:48.201 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType. 2024-09-17 11:35:48.201 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType. 2024-09-17 11:35:48.201 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement. 2024-09-17 11:35:48.201 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader. 2024-09-17 11:35:48.220 +05:30 [INF] Executing endpoint '/Index' 2024-09-17 11:35:48.220 +05:30 [INF] Route matched with {page = "/Index", area = "", action = "", controller = ""}. Executing page /Index 2024-09-17 11:35:48.220 +05:30 [INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy 2024-09-17 11:35:48.223 +05:30 [INF] Executing handler method G1.health.AuthServer.Pages.IndexModel.OnGet - ModelState is "Valid" 2024-09-17 11:35:48.223 +05:30 [INF] Executed handler method OnGet, returned result Microsoft.AspNetCore.Mvc.RedirectResult. 2024-09-17 11:35:48.223 +05:30 [INF] Executing RedirectResult, redirecting to http://test2dev.localhost:4200?redirect=true. 2024-09-17 11:35:48.223 +05:30 [INF] Executed page /Index in 2.6087ms 2024-09-17 11:35:48.223 +05:30 [INF] Executed endpoint '/Index' 2024-09-17 11:35:48.226 +05:30 [INF] Request finished HTTP/2 GET https://test2dev.localhost:44322/ - 302 null null 34.9218ms 2024-09-17 11:35:49.884 +05:30 [INF] Request starting HTTP/2 OPTIONS https://test2dev.localhost:44322/.well-known/openid-configuration - null null 2024-09-17 11:35:49.885 +05:30 [INF] CORS policy execution successful. 2024-09-17 11:35:49.885 +05:30 [INF] Request finished HTTP/2 OPTIONS https://test2dev.localhost:44322/.well-known/openid-configuration - 204 null null 0.9444ms 2024-09-17 11:35:49.892 +05:30 [INF] Request starting HTTP/2 GET https://test2dev.localhost:44322/.well-known/openid-configuration - null null 2024-09-17 11:35:49.893 +05:30 [INF] CORS policy execution successful. 2024-09-17 11:35:49.893 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri. 2024-09-17 11:35:49.893 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri. 2024-09-17 11:35:49.893 +05:30 [INF] The request URI matched a server endpoint: "Configuration". 2024-09-17 11:35:49.893 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType. 2024-09-17 11:35:49.893 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType. 2024-09-17 11:35:49.893 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement. 2024-09-17 11:35:49.893 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader. 2024-09-17 11:35:49.894 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ExtractConfigurationRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ExtractGetRequest
1[[OpenIddict.Server.OpenIddictServerEvents+ExtractConfigurationRequestContext, OpenIddict.Server, Version=5.5.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-09-17 11:35:49.894 +05:30 [INF] The configuration request was successfully extracted: {}. 2024-09-17 11:35:49.894 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+ExtractConfigurationRequest. 2024-09-17 11:35:49.895 +05:30 [INF] The configuration request was successfully validated. 2024-09-17 11:35:49.895 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+ValidateConfigurationRequest. 2024-09-17 11:35:49.895 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachIssuer. 2024-09-17 11:35:49.896 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachEndpoints. 2024-09-17 11:35:49.896 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachGrantTypes. 2024-09-17 11:35:49.896 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachResponseModes. 2024-09-17 11:35:49.897 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachResponseTypes. 2024-09-17 11:35:49.897 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachClientAuthenticationMethods. 2024-09-17 11:35:49.897 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachCodeChallengeMethods. 2024-09-17 11:35:49.898 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachScopes. 2024-09-17 11:35:50.201 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by Volo.Abp.OpenIddict.Scopes.AttachScopes. 2024-09-17 11:35:50.201 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachClaims. 2024-09-17 11:35:50.202 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachSubjectTypes. 2024-09-17 11:35:50.202 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachSigningAlgorithms. 2024-09-17 11:35:50.202 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleConfigurationRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachAdditionalMetadata. 2024-09-17 11:35:50.202 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+HandleConfigurationRequest. 2024-09-17 11:35:50.203 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyConfigurationResponseContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+AttachHttpResponseCode1[[OpenIddict.Server.OpenIddictServerEvents+ApplyConfigurationResponseContext, OpenIddict.Server, Version=5.5.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-09-17 11:35:50.204 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyConfigurationResponseContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+AttachWwwAuthenticateHeader`1[[OpenIddict.Server.OpenIddictServerEvents+ApplyConfigurationResponseContext, OpenIddict.Server, Version=5.5.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. -
0
2024-09-17 11:35:50.204 +05:30 [INF] The response was successfully returned as a JSON document: { "issuer": "https://test2dev.localhost:44322/", "authorization_endpoint": "https://test2dev.localhost:44322/connect/authorize", "token_endpoint": "https://test2dev.localhost:44322/connect/token", "introspection_endpoint": "https://test2dev.localhost:44322/connect/introspect", "end_session_endpoint": "https://test2dev.localhost:44322/connect/logout", "revocation_endpoint": "https://test2dev.localhost:44322/connect/revocat", "userinfo_endpoint": "https://test2dev.localhost:44322/connect/userinfo", "device_authorization_endpoint": "https://test2dev.localhost:44322/device", "jwks_uri": "https://test2dev.localhost:44322/.well-known/jwks", "grant_types_supported": [ "authorization_code", "implicit", "password", "client_credentials", "refresh_token", "urn:ietf:params:oauth:grant-type:device_code", "LinkLogin", "Impersonation" ], "response_types_supported": [ "code", "code id_token", "code id_token token", "code token", "id_token", "id_token token", "token", "none" ], "response_modes_supported": [ "form_post", "fragment", "query" ], "scopes_supported": [ "openid", "offline_access", "email", "profile", "phone", "roles", "address", "AccountService", "IdentityService", "AdministrationService", "SaasService", "ProductService", "ClinicService", "AppointmentService", "FormsService" ], "claims_supported": [ "aud", "exp", "iat", "iss", "sub" ], "id_token_signing_alg_values_supported": [ "RS256" ], "code_challenge_methods_supported": [ "plain", "S256" ], "subject_types_supported": [ "public" ], "token_endpoint_auth_methods_supported": [ "client_secret_post", "private_key_jwt", "client_secret_basic" ], "introspection_endpoint_auth_methods_supported": [ "client_secret_post", "private_key_jwt", "client_secret_basic" ], "revocation_endpoint_auth_methods_supported": [ "client_secret_post", "private_key_jwt", "client_secret_basic" ], "device_authorization_endpoint_auth_methods_supported": [ "client_secret_post", "private_key_jwt", "client_secret_basic" ], "claims_parameter_supported": false, "request_parameter_supported": false, "request_uri_parameter_supported": false, "authorization_response_iss_parameter_supported": true }.
2024-09-17 11:35:50.204 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyConfigurationResponseContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ProcessJsonResponse
1[[OpenIddict.Server.OpenIddictServerEvents+ApplyConfigurationResponseContext, OpenIddict.Server, Version=5.5.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-09-17 11:35:50.204 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyConfigurationResponseContext was marked as handled by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ProcessJsonResponse1[[OpenIddict.Server.OpenIddictServerEvents+ApplyConfigurationResponseContext, OpenIddict.Server, Version=5.5.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-09-17 11:35:50.205 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+ApplyConfigurationResponse1[[OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext, OpenIddict.Server, Version=5.5.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-09-17 11:35:50.205 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was marked as handled by OpenIddict.Server.OpenIddictServerHandlers+Discovery+ApplyConfigurationResponse1[[OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext, OpenIddict.Server, Version=5.5.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-09-17 11:35:50.205 +05:30 [INF] Request finished HTTP/2 GET https://test2dev.localhost:44322/.well-known/openid-configuration - 200 2528 application/json;charset=UTF-8 312.6074ms 2024-09-17 11:35:50.232 +05:30 [INF] Request starting HTTP/2 OPTIONS https://test2dev.localhost:44322/.well-known/jwks - null null 2024-09-17 11:35:50.232 +05:30 [INF] CORS policy execution successful. 2024-09-17 11:35:50.232 +05:30 [INF] Request finished HTTP/2 OPTIONS https://test2dev.localhost:44322/.well-known/jwks - 204 null null 0.4934ms 2024-09-17 11:35:50.237 +05:30 [INF] Request starting HTTP/2 GET https://test2dev.localhost:44322/.well-known/jwks - null null 2024-09-17 11:35:50.237 +05:30 [INF] CORS policy execution successful. 2024-09-17 11:35:50.239 +05:30 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri. 2024-09-17 11:35:50.239 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri. 2024-09-17 11:35:50.239 +05:30 [INF] The request URI matched a server endpoint: "Cryptography". 2024-09-17 11:35:50.239 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType. 2024-09-17 11:35:50.240 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType. 2024-09-17 11:35:50.240 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement. 2024-09-17 11:35:50.240 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader. 2024-09-17 11:35:50.240 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ExtractCryptographyRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ExtractGetRequest1[[OpenIddict.Server.OpenIddictServerEvents+ExtractCryptographyRequestContext, OpenIddict.Server, Version=5.5.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-09-17 11:35:50.240 +05:30 [INF] The cryptography request was successfully extracted: {}. 2024-09-17 11:35:50.240 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+ExtractCryptographyRequest. 2024-09-17 11:35:50.240 +05:30 [INF] The cryptography request was successfully validated. 2024-09-17 11:35:50.240 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+ValidateCryptographyRequest. 2024-09-17 11:35:50.241 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+HandleCryptographyRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+AttachSigningKeys. 2024-09-17 11:35:50.241 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Discovery+HandleCryptographyRequest. 2024-09-17 11:35:50.242 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyCryptographyResponseContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+AttachHttpResponseCode1[[OpenIddict.Server.OpenIddictServerEvents+ApplyCryptographyResponseContext, OpenIddict.Server, Version=5.5.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-09-17 11:35:50.242 +05:30 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyCryptographyResponseContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+AttachWwwAuthenticateHeader`1[[OpenIddict.Server.OpenIddictServerEvents+ApplyCryptographyResponseContext, OpenIddict.Server, Version=5.5.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-09-17 11:35:50.242 +05:30 [INF] The response was successfully returned as a JSON document: { "keys": [ { "kid": "13BD91B9E1CFB6B2FE468D5DA555027467241BF3", "use": "sig", "kty": "RSA", "alg": "RS256", "e": "AQAB", "n": "xyWrMvmdWh9ZTAw1wg7HxCAJwaqGkey_y0ipnlk6UUpVqD4BtmXJI6tBdsUKHHw1tQM128REluVzA1dKAdK2fsW3sORPcBnn88s_GWa3L9l0HQbWUHx0wvZbt0pitR_rYSNrjU6Imrbk-7Q9_F0zShSZC35Skov2bKA32hFCSTQ_Cy70lj3AxquJxSWDeavtRRwzTt-BeKzEjeXc_uToWe7qxZcoi_UQ6onqGLsDYquJzsBCnpKqBE4XdXTu4uy4Lg_aqzSQ0MwwrU6dzHd2fzJ9BGpSoTbuFPJ40xW73IgTyhhDvnb3yzW3ZpZ1NdYKwx0jEJncnBK9PrXS7Jx0PQ", "x5t": "E72RueHPtrL-Ro1dpVUCdGckG_M", "x5c": [ "MIIC9DCCAdygAwIBAgIIH/kzt+xSBmYwDQYJKoZIhvcNAQELBQAwMDEuMCwGA1UEAxMlT3BlbklkZGljdCBTZXJ2ZXIgU2lnbmluZyBDZXJ0aWZpY2F0ZTAeFw0yMzA2MTMwOTUxMThaFw0yNTA2MTMwOTUxMThaMDAxLjAsBgNVBAMTJU9wZW5JZGRpY3QgU2VydmVyIFNpZ25pbmcgQ2VydGlmaWNhdGUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDHJasy+Z1aH1lMDDXCDsfEIAnBqoaR7L/LSKmeWTpRSlWoPgG2Zckjq0F2xQocfDW1AzXbxESW5XMDV0oB0rZ+xbew5E9wGefzyz8ZZrcv2XQdBtZQfHTC9lu3SmK1H+thI2uNToiatuT7tD38XTNKFJkLflKSi/ZsoDfaEUJJND8LLvSWPcDGq4nFJYN5q+1FHDNO34F4rMSN5dz+5OhZ7urFlyiL9RDqieoYuwNiq4nOwEKekqoEThd1dO7i7LguD9qrNJDQzDCtTp3Md3Z/Mn0EalKhNu4U8njTFbvciBPKGEO+dvfLNbdmlnU11grDHSMQmdycEr0+tdLsnHQ9AgMBAAGjEjAQMA4GA1UdDwEB/wQEAwIHgDANBgkqhkiG9w0BAQsFAAOCAQEAYGyPok4xUhA2LMv1Eyu92IlMqRwC7DNvCvSgSA+FVagzAjq6WAKrCE/wpCuQmVSoJPPHpj0gO5sj3+mTSGLDtwqychKxYwFWw8iISFGdR+/q5x64HSAugJdhAl7uJ+A6XbWNUrDWUOh82PfegmgUqcKoFsLD41U40xmwAJd+pdsvjDL0yOwByQiGlYj1umU1UaLyBvv1glZ7R1d1udQzEeva7UnacstnfIlsLTSioQdR68YDsfOHoJY9Kn2MTWT2zPd7Erig6N4UWU1lXCyN60kEooxmxzDo7+Pf+xeA8KSrHCSvkWLPSkuoVw9i192bS4wldxwuc9udlTMclnmvhw==" ] } ] }. -
0
hi
Please send the
logs.txtto liming.ma@volosoft.com
Thanks -
0
Okay
-
0
hi
- Please update
https://{0}.localhosttohttp://{0}.localhost:4200
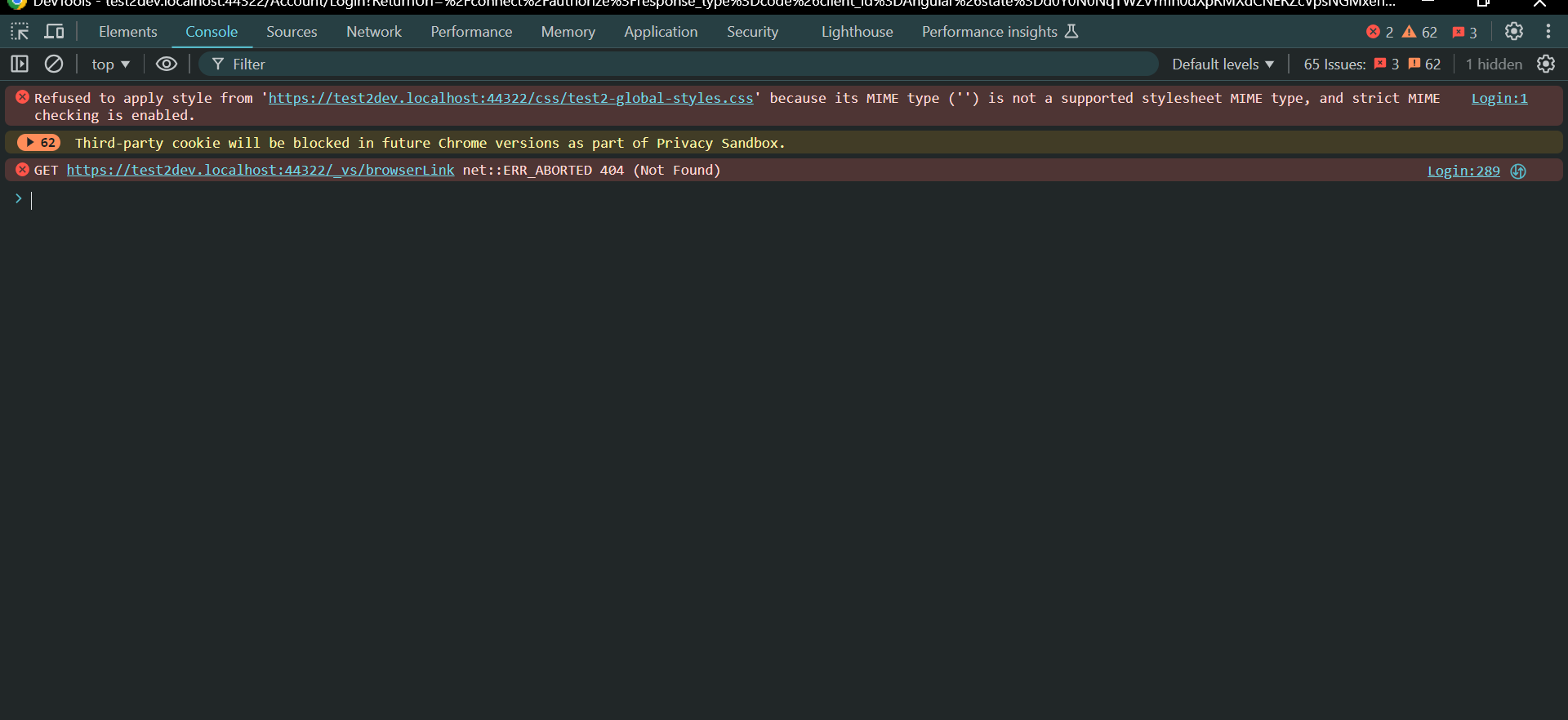
2024-09-17 11:35:50.876 +05:30 [DBG] Checking wildcard domain for url: http://test2dev.localhost:4200 2024-09-17 11:35:50.876 +05:30 [DBG] Checking wildcard domain format: https://{0}.localhost 2024-09-17 11:35:50.876 +05:30 [DBG] Checking wildcard domain format: https://{0}.localhost 2024-09-17 11:35:50.876 +05:30 [DBG] Wildcard domain not found for url: http://test2dev.localhost:4200- It seems the Login not the POST request. Are there any errors in the browser console?
- Please update
-
0
-
0
hi
Can I check it remotely?
https://us05web.zoom.us/j/84296078428?pwd=QPh9vbJQmZdQv47RAaNrqv7WNvMU6d.1
Join and share your screen.
Thanks
-
0
hi
The user is null here: https://github.com/abpframework/abp/blob/net9/modules/openiddict/src/Volo.Abp.OpenIddict.AspNetCore/Volo/Abp/OpenIddict/Controllers/AuthorizeController.cs#L84
Is the user id
3a0daa97-5fba-2079-563c-3e26309bdc81valid?