I have a second MAUI app that was created with abp.io commercial 8.0.4 and it does the exact same thing when I attempt to login with the iOS app. There is no error in the log file, and it actually indicates that the call succeeds and returns a 200 status, but if fails in both the app and pasting the URL into a browser.
Both of these apps are fresh builds without any modifications to the MAUI project other than pointing them to the Azure web app service that hosts the web / api portion of the solution.
There is no error in the log file. The error happens when the result is sent back. It is a System.UriException: the Uri scheme is invalid. The rest of the message merely points to the call to this call:
var webAuthenticatorOptions = new WebAuthenticatorOptions
{
Url = new Uri(options.StartUrl),
CallbackUrl = new Uri(options.EndUrl),
PrefersEphemeralWebBrowserSession = true
};
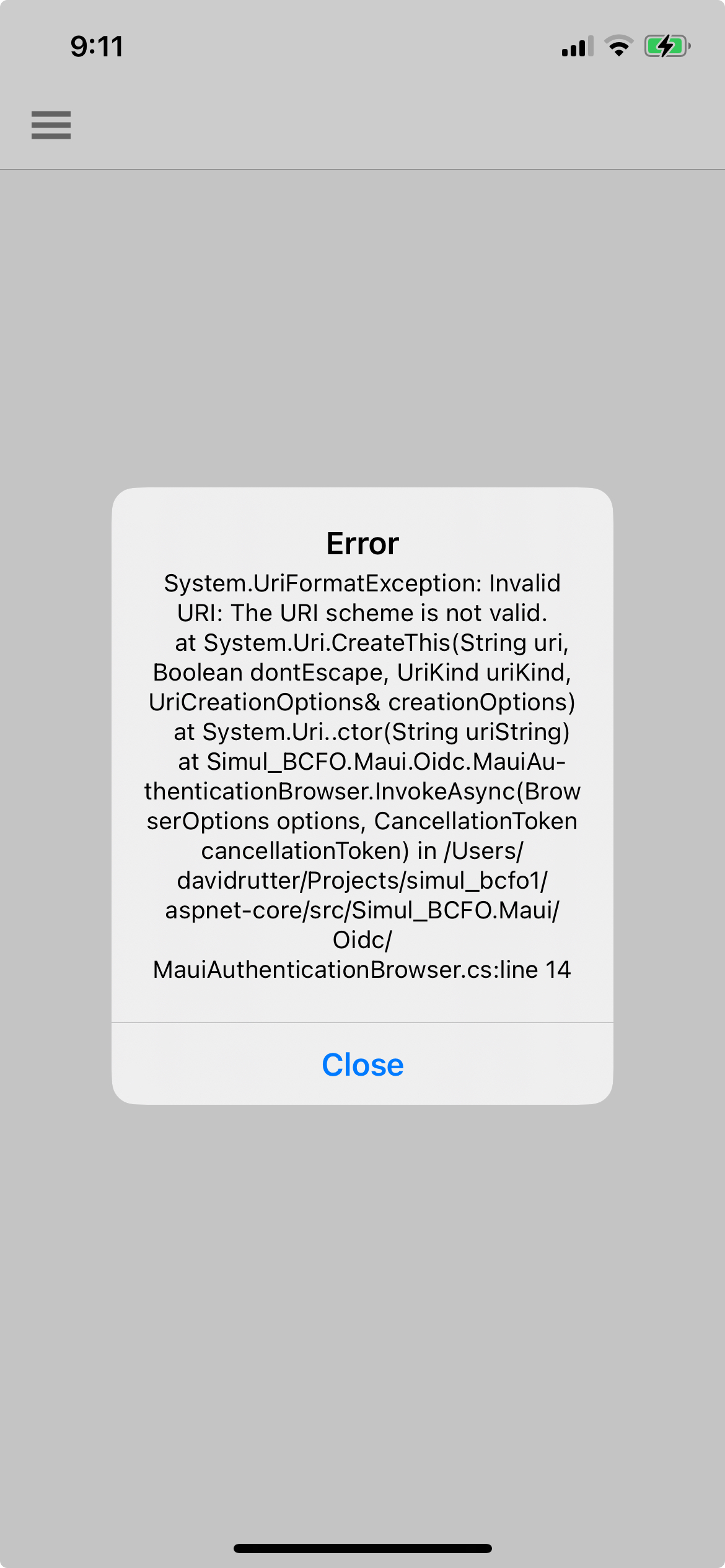
As I mentioned, If i copy the URL from the call into a browser I get a 400 error with no real information.
When I copy the Url from the call in the MauiAuthenticationBrowser.cs file into the browser, I get a 400 error. Can you provide any insight to what is happening and how to fix it?
The only way I could get this to work was to put the code that is embedded in the call to AddProductionEncryptionAndSigningCertificate("openiddict.pfx", <passcode>) with the code that used to be in the WebModule.cs file and add the following additional parameters to the create certificate (X509KeyStorageFlags.PersistKeySet | X509KeyStorageFlags.MachineKeySet).
Because Azure seems to require those two flags on the new X509Certificate2() call, it would be nice if abp.io would go back to the previous way and let us add those parameters.
I attempted to ask another question but got a message that my limit of 30 questions had been met. The 30 questions spans over 2 years and 2 subscriptions. When I repurchased my license in April of 2023 I would have expected that count to have been reset. It is ridiculous that the question count spans all years of my continued subscription. With each new release there are new issues and challenges that arise and not being able to ask questions as those arise makes using your framework much less reasonable. I need to have my question count to be reset with each extension of my license.
I got past the cryptographic issue and tried to run the iOS app (MAUI app) and am getting an AutoFac.Core.DependencyResolutionException. Autofac.Core.DependencyResolutionException: An exception was thrown while activating BCFOTest.Maui.App. ---> Autofac.Core.DependencyResolutionException: An exception was thrown while invoking the constructor 'Void .ctor(System.IServiceProvider)' on type 'App'. ---> Autofac.Core.DependencyResolutionException: An exception was thrown while activating BCFOTest.Maui.AppShell. ---> Autofac.Core.DependencyResolutionException: An exception was thrown while invoking the constructor 'Void .ctor(BCFOTest.Maui.ViewModels.ShellViewModel)' on type 'AppShell'. ---> Volo.Abp.Http.Client.AbpRemoteCallException: An error occurred during the ABP remote HTTP request. (An error occurred while sending the request.) See the inner exception for details. ---> System.Net.Http.HttpRequestException: An error occurred while sending the request. ---> System.Net.WebException: Error: TrustFailure --- End of inner exception stack trace ---
How do I get past this?
ABP Framework version: v8.0.2
UI Type: MVC
Database System: EF Core (SQL Server)
Tiered (for MVC) or Auth Server Separated (for Angular): no
Exception message and full stack trace:
Volo.Abp.AbpInitializationException: An error occurred during ConfigureServicesAsync phase of the module Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule, Volo.Abp.OpenIddict.AspNetCore, Version=8.0.1.0, Culture=neutral, PublicKeyToken=null. See the inner exception for details. ---> System.Security.Cryptography.CryptographicException: The system cannot find the file specified. at System.Security.Cryptography.X509Certificates.CertificatePal.FilterPFXStore(ReadOnlySpan`1 rawData, SafePasswordHandle password, PfxCertStoreFlags pfxCertStoreFlags)
Steps to reproduce the issue:
Create new abp.io commercial app using suite v8.0.2
Create both OpenIddict.pfx and authserver.pfx using appropriate pass phrase as defined in call to serverBuilder.AddProductionEncryptionAndSigningCertificate("openiddict.pfx", "
Deploy to Azure app service
set WEB_LOAD_CERTIFICATES=1and WEB_LOAD_USER_PROFILE=1 in app service configuration
verify that both openiddict.pfx and authserver.pfx files exist in /home/site/wwwroot
attempt to start website
receive exception
The process for configuring the certificate (AddProductionEncryptionAndSigningCertificate) hides the implementation and does not include the parameter X509KeyStorageFlags.MachineKeySet when creating the X509Certificate. On Azure it appears this parameter is required to enable proper loading of the cert.
This is being deployed to Azure.
public override void PreConfigureServices(ServiceConfigurationContext context)
{
var hostingEnvironment = context.Services.GetHostingEnvironment();
var configuration = context.Services.GetConfiguration();
context.Services.PreConfigure<AbpMvcDataAnnotationsLocalizationOptions>(options =>
{
options.AddAssemblyResource(
typeof(StatAlertResource),
typeof(StatAlertDomainModule).Assembly,
typeof(StatAlertDomainSharedModule).Assembly,
typeof(StatAlertApplicationModule).Assembly,
typeof(StatAlertApplicationContractsModule).Assembly,
typeof(StatAlertWebModule).Assembly
);
});
PreConfigure<OpenIddictBuilder>(builder =>
{
builder.AddValidation(options =>
{
options.AddAudiences("StatAlert");
options.UseLocalServer();
options.UseAspNetCore();
});
});
if (!hostingEnvironment.IsDevelopment())
{
PreConfigure<AbpOpenIddictAspNetCoreOptions>(options =>
{
options.AddDevelopmentEncryptionAndSigningCertificate = false;
});
PreConfigure<OpenIddictServerBuilder>(builder =>
{
builder.AddSigningCertificate(GetSigningCertificate(hostingEnvironment, configuration));
builder.AddEncryptionCertificate(GetSigningCertificate(hostingEnvironment, configuration));
builder.SetIssuer(new Uri(configuration["AuthServer:Authority"]));
});
}
}
This is the code in the GetSigningCertificate (minus the line that defines the actual key) var file = Path.Combine(hostingEnv.ContentRootPath, fileName);
if (!File.Exists(file))
{
throw new FileNotFoundException($"Signing Certificate couldn't found: {file}");
}
return new X509Certificate2(file, passPhrase);
NOTICE that the message if the file doesn't exist is not the message received in the error.
The file does exist and it the one I created with the correct key.

