There are 2 kinds of SPA authentication; Authorization Code Flow (Recommended) and Resource Owner Password Flow. We support both of them that you can check at Authorization in Angular UI docs.
This question seems a broad 10 hour lecture about authorization and authentication :)
Can you check docs and google about authorization flows in SPA and ask specific question about your problem?
Navigate to Administration ->Identity Server -> Clients
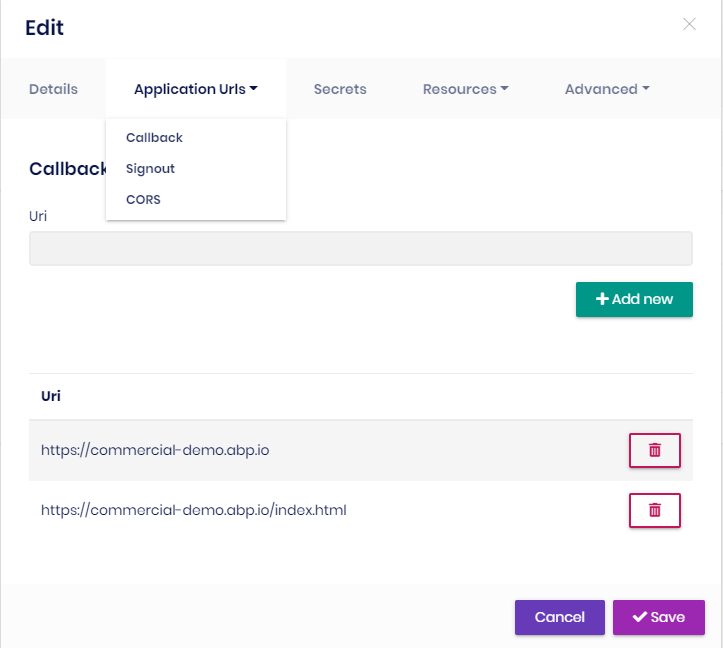
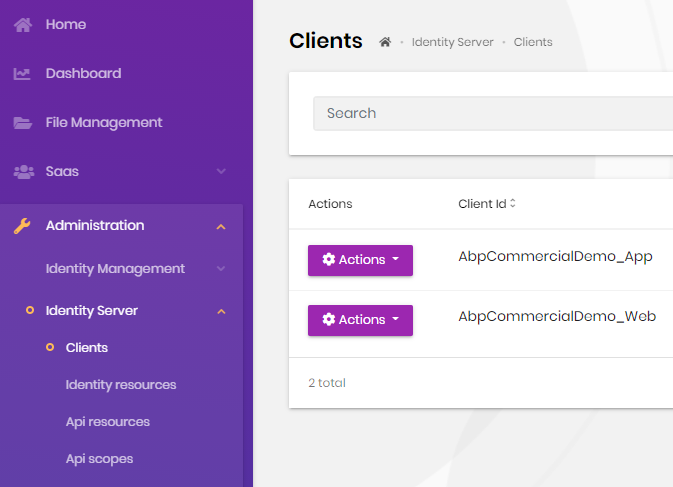 Under Actions button, Edit -> Application Urls -> Callback
Under Actions button, Edit -> Application Urls -> Callback
Create an other environment like appsettings.staging.json that has staging client root url (Swagger:RootUrl or App:RootUrl) in the appsettings. When you set the environment and run the DbMigrator, it will add the staging data from the appsettings.
Hi, thank you for the clarification, however after resolving the errors and getting all the applications running we are still running into the Prometheus error as shown above. All the other infrastructure services are working except for Prometheus. Any solution you could provide would be much appreciated. Thanks
You need to add prometheus data in Grafana UI as far as I remember. Sorry, I don't have much knowledge about Grafana and Prometheus.
You can also remove them from your docker-compose.infrastructure.yml (also from .override) file if you are not using.
- What about logout from B2C?
You can check microsoft docs about single signout behaviour.
2021-09-24 14:29:24.431 +00:00 [ERR] Invalid redirect_uri: https://fwateer.azurewebsites.net/swagger/oauth2-redirect.html
{"ClientId":"eInvoicing_Swagger","ClientName":"eInvoicing_Swagger","RedirectUri":null,"AllowedRedirectUris": ["https://localhost:44318/swagger/oauth2-redirect.html"]
Apparently you have the dev environment redirect uri (https://localhost:44318/swagger/oauth2-redirect.html) and missing production redirect uri (https://fwateer.azurewebsites.net/swagger/oauth2-redirect.html) for the swagger client.
Check your database (or from identity server UI) that your client with eInvoicing_Swagger ID has https://fwateer.azurewebsites.net/swagger/oauth2-redirect.html redirect Uri.
Yes it is discouraged unless you trust the js client and you know what you are doing.
Default flow is Authorization Code with PKCE and you can change the flow from envrionment.ts file. You can check the Authorization in Angular UI docs for more and how to do it.
Microservice template is more complex than monolith solutions because of the nature of microservice development itself. Main solution doesn't consist all the projects but just the runnable projects. So that you need to manually build all the referenced projects by yourself if you are not using tye.
AdministrationService.EntityFrameworkCore version mismatch is related with local nuget cache referance and we are investigating if there is a configuration error on our side or if there is a bug on Microsoft side.
Currently, removing PrivateAssets and IncludeAssets to set default in AdministrationService.EntityFrameworkCore.csproj file seems to fix the version mismatch as shown above.
It is hard to say anything before checking the application logs. It may be related with ssl certificate or http/https mismatch.. Or it can simply be a redirect uri typo.
Can you share the applications logs of authserver and web (backoffice) application?
I am guessing you want to login to your application through react application and not redirect to Authorization Server (backend).
Default suggested authentication flow for SPA applications is Authorization Code with PKCE because of security reasons.
You can check our documentations about it: https://docs.abp.io/en/abp/latest/UI/Angular/Authorization#resource-owner-password-flow
If you don't set responseType it will be password flow automatically.
For more detailed information about the flow:
You need to add your client to identity server with grant type and a secret. Sample can be found here: https://docs.identityserver.io/en/release/quickstarts/2_resource_owner_passwords.html
Eventually create a url to make the request to authorize endpoint. Here is some documentation from auth0 about what the url should look like: https://auth0.com/docs/authorization/flows/call-your-api-using-resource-owner-password-flow. There should be react libraries easing client request process.
Getting access-token from azure-ad is related with Microsoft and completely out of our scope.
However i will try to help you;
I willl use client credential flow using ConfidentialClientApplicationBuilder of Microsoft.Identity.Client package.
Create a Page something like: <br>
public class AzurePage : PageModel
{
IConfidentialClientApplication app;
private const string clientId = "my-client-id-in-appsettings";
private const string tenantId = "my-tenant-id-in-appsettings";
private const string clientSecret = "my-client-secret-in-appsettings";
public string azureAccessToken = string.Empty;
public AzurePage()
{
string authority = $"https://login.microsoftonline.com/{tenantId}/v2.0/";
app = ConfidentialClientApplicationBuilder.Create(clientId)
.WithClientSecret(clientSecret)
.WithAuthority(new Uri(authority))
.Build();
}
public async Task<IActionResult> OnGet()
{
string[] scopes = new string[] { "https://graph.microsoft.com/.default" };
AuthenticationResult result = null;
try
{
result = await app.AcquireTokenForClient(scopes)
.ExecuteAsync();
azureAccessToken = result.AccessToken;
}
catch(MsalServiceException ex)
{
// AADSTS70011
// Invalid scope. The scope has to be of the form "https://resourceurl/.default"
// Mitigation: this is a dev issue. Change the scope to be as expected
}
return Page();
}
Result:
and Jwt.io:
Use IConfidentialClientApplication wherever you need.

