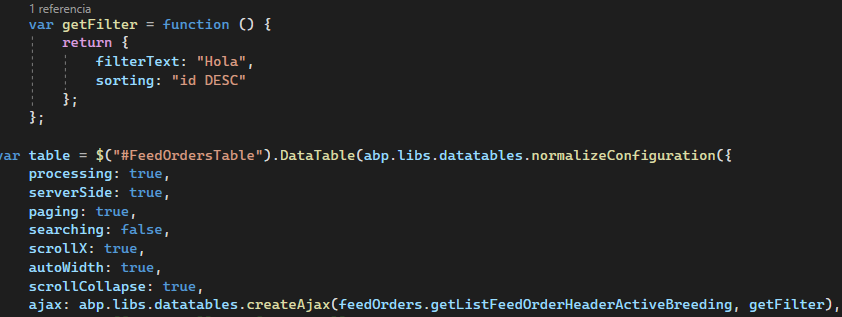
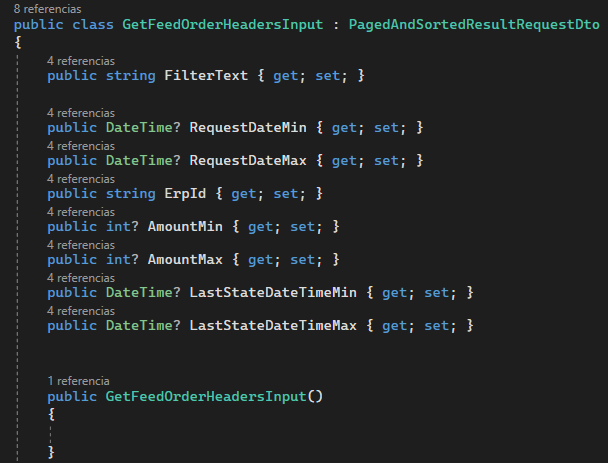
Activities of "inavarro.cp"
I would like to know how to capture the exceptions I receive from the backend and display them on the frontend. I have a modal where in the OnGet() method I receive the data, in the case that there is a problem with the data from the backend I will have received a UserFriendlyException() exception.
For example:
This is my OnGet() method inside the modal
public async Task OnGet()
{
var data = await _feedOrderLinesAppService.GetListFeedOrderLinesFromDeliveryAsync(Id);
if (data != null)
{
FeedOrderLineBasicInfoDtoViewModel = ObjectMapper.Map<List<FeedOrderLineBasicInfoDto>, List<FeedOrderLineBasicInfoDtoViewModel>>(data);
}
}
Let's review the method GetListFeedOrderLinesFromDeliveryAsync(Id)
public async Task<List<FeedOrderLineBasicInfoDto>> GetListFeedOrderLinesFromDeliveryAsync(string feedDeliveryId)
{
var feedOrderLines = await _feedOrderManager.GetListFeedOrderLinesFromDeliveryAsync(feedDeliveryId);
return ObjectMapper.Map<List<FeedOrderLineWithNavigationProperties>, List<FeedOrderLineBasicInfoDto>>(feedOrderLines);
}
Let's review the method GetListFeedOrderLinesFromDeliveryAsync(feedDeliveryId), This method must first obtain the header ID, and then obtain the lines, but in the case that the header does not exist, it throws an exception.
public async Task<List<FeedOrderLineWithNavigationProperties>> GetListFeedOrderLinesFromDeliveryAsync(string feedOrderHeaderErpId)
{
var feedOrderHeader = await _feedOrderHeaderRepository.FirstOrDefaultAsync(x => x.ErpId == feedOrderHeaderErpId);
if (feedOrderHeader == null)
{
throw new UserFriendlyException("Feed order header not found");
}
return await _feedOrderLineRepository.GetListWithNavigationPropertiesAsync(feedOrderHeaderId: feedOrderHeader.Id);
}
- ABP Framework version: v6.0.1
- UI Type: MVC
- Database System: EF Core ( PostgreSQL)
- Tiered (for MVC) or Auth Server Separated (for Angular): Tiered
- Exception message and full stack trace:
- Steps to reproduce the issue:
These are the logs generated by the Identity:
Volo.Abp.AbpInitializationException: An error occurred during ConfigureServicesAsync phase of the module Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule, Volo.Abp.OpenIddict.AspNetCore, Version=6.0.1.0, Culture=neutral, PublicKeyToken=null. See the inner exception for details.
---> System.IO.FileNotFoundException: Signing Certificate couldn't found: openiddict.pfx
at Microsoft.Extensions.DependencyInjection.OpenIddictServerBuilderExtensions.AddProductionEncryptionAndSigningCertificate(OpenIddictServerBuilder builder, String fileName, String passPhrase) in /home/runner/work/Cincaporc.WebApp/Cincaporc.WebApp/src/Cincaporc.WebApp.AuthServer/OpenIddictServerBuilderExtensions.cs:line 13
at Cincaporc.WebApp.WebAppAuthServerModule.<>c__DisplayClass0_0.<PreConfigureServices>b__2(OpenIddictServerBuilder serverBuilder) in /home/runner/work/Cincaporc.WebApp/Cincaporc.WebApp/src/Cincaporc.WebApp.AuthServer/WebAppAuthServerModule.cs:line 96
at Volo.Abp.Options.PreConfigureActionList`1.Configure(TOptions options)
at Microsoft.Extensions.DependencyInjection.ServiceCollectionPreConfigureExtensions.ExecutePreConfiguredActions[TOptions](IServiceCollection services, TOptions options)
at Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule.<>c__DisplayClass1_0.<AddOpenIddictServer>b__0(OpenIddictServerBuilder builder)
at Microsoft.Extensions.DependencyInjection.OpenIddictServerExtensions.AddServer(OpenIddictBuilder builder, Action`1 configuration)
at Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule.AddOpenIddictServer(IServiceCollection services)
at Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule.ConfigureServices(ServiceConfigurationContext context)
at Volo.Abp.Modularity.AbpModule.ConfigureServicesAsync(ServiceConfigurationContext context)
at Volo.Abp.AbpApplicationBase.ConfigureServicesAsync()
These are the logs generated by the GitHubActions:
Run dotnet dev-certs https -v -ep /home/runner/.dotnet/Cincaporc.WebApp.AuthServer/openiddict.pfx -p 00000000-0000-0000-0000-000000000000
[1] Listing certificates from CurrentUser\My
[2] Found certificates: 1 certificate
1) 85401136598E5431084B7F11E2486FA96A65D658 - CN=localhost - Valid from 2024-08-09 10:24:49Z to 2025-08-09 10:24:49Z - IsHttpsDevelopmentCertificate: true - IsExportable: true
[3] Checking certificates validity
[4] Valid certificates: 1 certificate
1) 85401136598E5431084B7F11E2486FA96A65D658 - CN=localhost - Valid from 2024-08-09 10:24:49Z to 2025-08-09 10:24:49Z - IsHttpsDevelopmentCertificate: true - IsExportable: true
[5] Invalid certificates: no certificates
[6] Finished listing certificates.
[1] Listing certificates from LocalMachine\My
[7] An error occurred while listing the certificates: System.Security.Cryptography.CryptographicException: Unix LocalMachine X509Store is limited to the Root and CertificateAuthority stores.
---> System.PlatformNotSupportedException: Unix LocalMachine X509Store is limited to the Root and CertificateAuthority stores.
--- End of inner exception stack trace ---
at Internal.Cryptography.Pal.StorePal.FromSystemStore(String storeName, StoreLocation storeLocation, OpenFlags openFlags)
at System.Security.Cryptography.X509Certificates.X509Store.Open(OpenFlags flags)
at Microsoft.AspNetCore.Certificates.Generation.CertificateManager.ListCertificates(StoreName storeName, StoreLocation location, Boolean isValid, Boolean requireExportable)
[8] Filtered certificates: 1 certificate
1) 85401136598E5431084B7F11E2486FA96A65D658 - CN=localhost - Valid from 2024-08-09 10:24:49Z to 2025-08-09 10:24:49Z - IsHttpsDevelopmentCertificate: true - IsExportable: true
[9] Excluded certificates: no certificates
[14] Valid certificates: 1 certificate
1) 85401136598E5431084B7F11E2486FA96A65D658 - CN=localhost - Valid from 2024-08-09 10:24:49Z to 2025-08-09 10:24:49Z - IsHttpsDevelopmentCertificate: true - IsExportable: true
[15] Selected certificate: 85401136598E5431084B7F11E2486FA96A65D658 - CN=localhost - Valid from 2024-08-09 10:24:49Z to 2025-08-09 10:24:49Z - IsHttpsDevelopmentCertificate: true - IsExportable: true
[23] Saving certificate '85401136598E5431084B7F11E2486FA96A65D658 - CN=localhost - Valid from 2024-08-09 10:24:49Z to 2025-08-09 10:24:49Z - IsHttpsDevelopmentCertificate: true - IsExportable: true' to /home/runner/.dotnet/Cincaporc.WebApp.AuthServer/openiddict.pfx with private key.
[25] Creating directory /home/runner/.dotnet/Cincaporc.WebApp.AuthServer.
[27] Writing the certificate to: /home/runner/.dotnet/Cincaporc.WebApp.AuthServer/openiddict.pfx.
A valid HTTPS certificate is already present.
The certificate was exported to /home/runner/.dotnet/Cincaporc.WebApp.AuthServer/openiddict.pfx
In the github Actions logs, the certificate is generated correctly, the problem is a routing issue that the ABP code cannot locate the generated certificate.
This is the GitHubActions code:
name: Deploy all webapps in pre environment.
on:
push:
branches:
- development
workflow_dispatch:
env:
ASPNETCORE_ENVIRONMENT: Staging
AbpLicenseCode: ${{ secrets.ABP_COMMERCIAL_LICENSE }}
jobs:
Deploy_Apps:
runs-on: ubuntu-latest
env:
DOTNET_ROOT: /home/runner/.dotnet
steps:
- uses: actions/checkout@v2
# notify on each build event like starting and finishing a build
- uses: toko-bifrost/ms-teams-deploy-card@master
if: always()
with:
github-token: ${{ github.token }}
webhook-uri: ${{ secrets.MICROSOFT_TEAMS_WEBHOOK_URI }}
- name: Setup .NET Core SDK
uses: actions/setup-dotnet@v1
with:
dotnet-version: '6.0.x'
- name: Install ABP CLI
run: dotnet tool install -g Volo.Abp.Cli --version 6.0.1
- name: Install ABP libs
run: abp install-libs
- name: Az CLI login
id: az_login
uses: azure/login@v1
with:
creds: ${{ secrets.AZURE_CREDENTIALS }}
- name: Prepare Migrations
run: cd src/Cincaporc.WebApp.DbMigrator && dotnet publish -c Release && cd
- name: Run Migrations
run: cd src/Cincaporc.WebApp.DbMigrator && dotnet bin/Release/net6.0/publish/Cincaporc.WebApp.DbMigrator.dll --Environment Staging --configuration Release && cd
- name: Publish CincaPorc WebApp.Auth.Server.
run: dotnet publish --configuration Release --output WebApp.Auth.Server src/Cincaporc.WebApp.AuthServer/Cincaporc.WebApp.AuthServer.csproj
- name: Generate openiddict.pfx
run: dotnet dev-certs https -v -ep ${{env.DOTNET_ROOT}}/Cincaporc.WebApp.AuthServer/openiddict.pfx -p 00000000-0000-0000-0000-000000000000
- name: Deploy APP WebApp.Auth.Server
uses: azure/webapps-deploy@v2.2.3
with:
app-name: extranetIdentity-dev
package: WebApp.Auth.Server
- name: Publish CincaPorc WebApp.HttpApi.Host.
run: dotnet publish --configuration Release --output WebApp.HttpApi.Host src/Cincaporc.WebApp.HttpApi.Host/Cincaporc.WebApp.HttpApi.Host.csproj
- name: Deploy APP WebApp.HttpApi.Host
uses: azure/webapps-deploy@v2.2.3
with:
app-name: extranetappapi-dev
package: WebApp.HttpApi.Host
- name: Publish CincaPorc WebApp.Web.
run: dotnet publish --configuration Release --output WebApp.Web src/Cincaporc.WebApp.Web/Cincaporc.WebApp.Web.csproj
- name: Deploy APP WebApp
uses: azure/webapps-deploy@v2.2.3
with:
app-name: extranetapp-dev
package: WebApp.Web
- name: Publish CincaPorc WebApp.Web.Public.
run: dotnet publish --configuration Release --output WebApp.Web.Public src/Cincaporc.WebApp.Web.Public/Cincaporc.WebApp.Web.Public.csproj
- name: Deploy APP WebApp.Web.Public
uses: azure/webapps-deploy@v2.2.3
with:
app-name: IntegradosApp-dev
package: WebApp.Web.Public
- name: Az Logout.
if: ${{ always() && steps.az_login.conclusion == 'success' }}
run: |
az logout
az cache purge
az account clear
We have followed the example of the official documentation: https://abp.io/docs/latest/deployment/configuring-openiddict
This is the code that we have added to the ABP project:
using System;
using System.IO;
using System.Security.Cryptography.X509Certificates;
namespace Microsoft.Extensions.DependencyInjection;
public static class OpenIddictServerBuilderExtensions
{
public static OpenIddictServerBuilder AddProductionEncryptionAndSigningCertificate(this OpenIddictServerBuilder builder, string fileName, string passPhrase)
{
if (!File.Exists(fileName))
{
throw new FileNotFoundException($"Signing Certificate couldn't found: {fileName}");
}
var certificate = new X509Certificate2(fileName, passPhrase);
builder.AddSigningCertificate(certificate);
builder.AddEncryptionCertificate(certificate);
return builder;
}
}
Perfect, this is already working for us. Thank you so much
We already solved the previous error, but now we get this new error, this happens when launching Application.Tests.
Cincaporc.WebApp.Adss.AdssAppServiceTests.CreateAsync Origen: AdsApplicationTests.cs línea 46 Duración: 1 ms
Mensaje: Volo.Abp.AbpInitializationException : An error occurred during the initialize Volo.Abp.Modularity.OnPreApplicationInitializationModuleLifecycleContributor phase of the module Volo.Abp.BackgroundWorkers.Hangfire.AbpBackgroundWorkersHangfireModule, Volo.Abp.BackgroundWorkers.Hangfire, Version=6.0.1.0, Culture=neutral, PublicKeyToken=null: An exception was thrown while activating λ:Volo.Abp.Hangfire.AbpHangfireBackgroundJobServer -> λ:Hangfire.JobStorage.. See the inner exception for details. ---- Autofac.Core.DependencyResolutionException : An exception was thrown while activating λ:Volo.Abp.Hangfire.AbpHangfireBackgroundJobServer -> λ:Hangfire.JobStorage. -------- System.InvalidOperationException : JobStorage.Current property value has not been initialized. You must set it before using Hangfire Client or Server API.
Seguimiento de la pila:
ModuleManager.InitializeModules(ApplicationInitializationContext context)
AbpApplicationBase.InitializeModules()
AbpApplicationWithExternalServiceProvider.Initialize(IServiceProvider serviceProvider)
AbpIntegratedTest1.ctor() WebAppTestBase1.ctor()
WebAppApplicationTestBase.ctor()
AdssAppServiceTests.ctor() línea 15
RuntimeType.CreateInstanceDefaultCtor(Boolean publicOnly, Boolean wrapExceptions)
----- Inner Stack Trace -----
ActivatorErrorHandlingMiddleware.Execute(ResolveRequestContext context, Action1 next) <>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt) ResolvePipeline.Invoke(ResolveRequestContext ctxt) RegistrationPipelineInvokeMiddleware.Execute(ResolveRequestContext context, Action1 next)
<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
<>c__DisplayClass5_0.<Execute>b__0()
LifetimeScope.CreateSharedInstance(Guid id, Func1 creator) LifetimeScope.CreateSharedInstance(Guid primaryId, Nullable1 qualifyingId, Func1 creator) SharingMiddleware.Execute(ResolveRequestContext context, Action1 next)
<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
CircularDependencyDetectorMiddleware.Execute(ResolveRequestContext context, Action1 next) <>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt) ResolvePipeline.Invoke(ResolveRequestContext ctxt) ResolveOperation.GetOrCreateInstance(ISharingLifetimeScope currentOperationScope, ResolveRequest request) ResolveOperation.ExecuteOperation(ResolveRequest request) ResolveOperation.Execute(ResolveRequest request) LifetimeScope.ResolveComponent(ResolveRequest request) ResolutionExtensions.TryResolveService(IComponentContext context, Service service, IEnumerable1 parameters, Object& instance)
ResolutionExtensions.ResolveService(IComponentContext context, Service service, IEnumerable1 parameters) ResolutionExtensions.Resolve(IComponentContext context, Type serviceType, IEnumerable1 parameters)
ResolutionExtensions.Resolve(IComponentContext context, Type serviceType)
AutofacServiceProvider.GetRequiredService(Type serviceType)
ServiceProviderServiceExtensions.GetRequiredService(IServiceProvider provider, Type serviceType)
ServiceProviderServiceExtensions.GetRequiredService[T](IServiceProvider provider)
HangfireBackgroundWorkerManager.StartAsync(CancellationToken cancellationToken)
AbpBackgroundWorkersHangfireModule.OnPreApplicationInitializationAsync(ApplicationInitializationContext context)
TaskExtensions.WaitAndUnwrapException(Task task)
<>c__DisplayClass15_0.<Run>b__0(Task t)
ContinuationTaskFromTask.InnerInvoke()
<.cctor>b__272_0(Object obj)
ExecutionContext.RunInternal(ExecutionContext executionContext, ContextCallback callback, Object state)
--- End of stack trace from previous location ---
ExecutionContext.RunInternal(ExecutionContext executionContext, ContextCallback callback, Object state)
Task.ExecuteWithThreadLocal(Task& currentTaskSlot, Thread threadPoolThread)
--- End of stack trace from previous location ---
TaskExtensions.WaitAndUnwrapException(Task task)
AsyncContext.Run(Func1 action) AsyncHelper.RunSync(Func1 action)
AbpBackgroundWorkersHangfireModule.OnPreApplicationInitialization(ApplicationInitializationContext context)
OnPreApplicationInitializationModuleLifecycleContributor.Initialize(ApplicationInitializationContext context, IAbpModule module)
ModuleManager.InitializeModules(ApplicationInitializationContext context)
----- Inner Stack Trace -----
JobStorage.get_Current()
<>c.<AddHangfire>b__1_0(IServiceProvider _)
<>c__DisplayClass13_01.<TryAddSingletonChecked>b__0(IServiceProvider serviceProvider) <>c__DisplayClass3_0.<Register>b__0(IComponentContext context, IEnumerable1 parameters)
DelegateActivator.ActivateInstance(IComponentContext context, IEnumerable1 parameters) DelegateActivator.<ConfigurePipeline>b__2_0(ResolveRequestContext ctxt, Action1 next)
DelegateMiddleware.Execute(ResolveRequestContext context, Action1 next) <>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt) DisposalTrackingMiddleware.Execute(ResolveRequestContext context, Action1 next)
<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
ActivatorErrorHandlingMiddleware.Execute(ResolveRequestContext context, Action`1 next)
- ABP Framework version: v6.0.1
- UI type: MVC
- DB provider: EF Core
- Tiered (MVC) or Auth Server Separated (Angular): Tired
- Exception message and stack trace:
- Steps to reproduce the issue:"
Hi, Anyone can help us with test modules? Right now when we run every test projecte, we get this error:
Mensaje:
Volo.Abp.AbpInitializationException : An error occurred during the initialize Volo.Abp.Modularity.OnApplicationInitializationModuleLifecycleContributor phase of the module Cincaporc.WebApp.WebAppTestBaseModule, Cincaporc.WebApp.TestBase, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null: An exception was thrown while activating λ:Volo.Abp.Identity.EntityFrameworkCore.IIdentityDbContext -> λ:Volo.Abp.Identity.EntityFrameworkCore.IIdentityProDbContext -> Cincaporc.WebApp.EntityFrameworkCore.WebAppDbContext -> λ:Microsoft.EntityFrameworkCore.DbContextOptions`1[[Cincaporc.WebApp.EntityFrameworkCore.WebAppDbContext, Cincaporc.WebApp.EntityFrameworkCore, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null]].. See the inner exception for details.
---- Autofac.Core.DependencyResolutionException : An exception was thrown while activating λ:Volo.Abp.Identity.EntityFrameworkCore.IIdentityDbContext -> λ:Volo.Abp.Identity.EntityFrameworkCore.IIdentityProDbContext -> Cincaporc.WebApp.EntityFrameworkCore.WebAppDbContext -> λ:Microsoft.EntityFrameworkCore.DbContextOptions`1[[Cincaporc.WebApp.EntityFrameworkCore.WebAppDbContext, Cincaporc.WebApp.EntityFrameworkCore, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null]].
-------- System.ArgumentNullException : Value cannot be null. (Parameter 'connectionString')
Seguimiento de la pila:
ModuleManager.InitializeModules(ApplicationInitializationContext context)
AbpApplicationBase.InitializeModules()
AbpApplicationWithExternalServiceProvider.Initialize(IServiceProvider serviceProvider)
AbpIntegratedTest`1.ctor()
WebAppTestBase`1.ctor()
WebAppEntityFrameworkCoreTestBase.ctor()
AdsRepositoryTests.ctor() línea 15
RuntimeType.CreateInstanceDefaultCtor(Boolean publicOnly, Boolean wrapExceptions)
----- Inner Stack Trace -----
ActivatorErrorHandlingMiddleware.Execute(ResolveRequestContext context, Action`1 next)
<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
ResolvePipeline.Invoke(ResolveRequestContext ctxt)
RegistrationPipelineInvokeMiddleware.Execute(ResolveRequestContext context, Action`1 next)
<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
SharingMiddleware.Execute(ResolveRequestContext context, Action`1 next)
<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
CircularDependencyDetectorMiddleware.Execute(ResolveRequestContext context, Action`1 next)
<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
ResolvePipeline.Invoke(ResolveRequestContext ctxt)
ResolveOperation.GetOrCreateInstance(ISharingLifetimeScope currentOperationScope, ResolveRequest request)
ResolveOperation.ExecuteOperation(ResolveRequest request)
ResolveOperation.Execute(ResolveRequest request)
LifetimeScope.ResolveComponent(ResolveRequest request)
ResolutionExtensions.TryResolveService(IComponentContext context, Service service, IEnumerable`1 parameters, Object& instance)
ResolutionExtensions.ResolveService(IComponentContext context, Service service, IEnumerable`1 parameters)
ResolutionExtensions.Resolve(IComponentContext context, Type serviceType, IEnumerable`1 parameters)
ResolutionExtensions.Resolve(IComponentContext context, Type serviceType)
AutofacServiceProvider.GetRequiredService(Type serviceType)
ServiceProviderServiceExtensions.GetRequiredService(IServiceProvider provider, Type serviceType)
ServiceProviderServiceExtensions.GetRequiredService[T](IServiceProvider provider)
UnitOfWorkDbContextProvider`1.CreateDbContextWithTransactionAsync(IUnitOfWork unitOfWork)
UnitOfWorkDbContextProvider`1.CreateDbContextAsync(IUnitOfWork unitOfWork)
UnitOfWorkDbContextProvider`1.CreateDbContextAsync(IUnitOfWork unitOfWork, String connectionStringName, String connectionString)
UnitOfWorkDbContextProvider`1.GetDbContextAsync()
EfCoreRepository`2.GetDbSetAsync()
EfCoreIdentityUserRepository.FindByNormalizedUserNameAsync(String normalizedUserName, Boolean includeDetails, CancellationToken cancellationToken)
AsyncInterceptorBase.ProceedAsynchronous[TResult](IInvocation invocation, IInvocationProceedInfo proceedInfo)
CastleAbpMethodInvocationAdapterWithReturnValue`1.ProceedAsync()
UnitOfWorkInterceptor.InterceptAsync(IAbpMethodInvocation invocation)
CastleAsyncAbpInterceptorAdapter`1.InterceptAsync[TResult](IInvocation invocation, IInvocationProceedInfo proceedInfo, Func`3 proceed)
IdentityDataSeeder.SeedAsync(String adminEmail, String adminPassword, Nullable`1 tenantId)
AsyncInterceptorBase.ProceedAsynchronous[TResult](IInvocation invocation, IInvocationProceedInfo proceedInfo)
CastleAbpMethodInvocationAdapterWithReturnValue`1.ProceedAsync()
UnitOfWorkInterceptor.InterceptAsync(IAbpMethodInvocation invocation)
CastleAsyncAbpInterceptorAdapter`1.InterceptAsync[TResult](IInvocation invocation, IInvocationProceedInfo proceedInfo, Func`3 proceed)
DataSeeder.SeedAsync(DataSeedContext context)
AsyncInterceptorBase.ProceedAsynchronous(IInvocation invocation, IInvocationProceedInfo proceedInfo)
CastleAbpMethodInvocationAdapter.ProceedAsync()
UnitOfWorkInterceptor.InterceptAsync(IAbpMethodInvocation invocation)
CastleAsyncAbpInterceptorAdapter`1.InterceptAsync(IInvocation invocation, IInvocationProceedInfo proceedInfo, Func`3 proceed)
<<SeedTestData>b__0>d.MoveNext() línea 48
--- End of stack trace from previous location ---
TaskExtensions.WaitAndUnwrapException(Task task)
<>c__DisplayClass15_0.<Run>b__0(Task t)
ContinuationTaskFromTask.InnerInvoke()
<.cctor>b__272_0(Object obj)
ExecutionContext.RunInternal(ExecutionContext executionContext, ContextCallback callback, Object state)
--- End of stack trace from previous location ---
ExecutionContext.RunInternal(ExecutionContext executionContext, ContextCallback callback, Object state)
Task.ExecuteWithThreadLocal(Task& currentTaskSlot, Thread threadPoolThread)
--- End of stack trace from previous location ---
TaskExtensions.WaitAndUnwrapException(Task task)
AsyncContext.Run(Func`1 action)
AsyncHelper.RunSync(Func`1 action)
WebAppTestBaseModule.SeedTestData(ApplicationInitializationContext context) línea 44
WebAppTestBaseModule.OnApplicationInitialization(ApplicationInitializationContext context) línea 39
OnApplicationInitializationModuleLifecycleContributor.Initialize(ApplicationInitializationContext context, IAbpModule module)
ModuleManager.InitializeModules(ApplicationInitializationContext context)
----- Inner Stack Trace -----
Check.NotEmpty(String value, String parameterName)
NpgsqlDbContextOptionsBuilderExtensions.UseNpgsql(DbContextOptionsBuilder optionsBuilder, String connectionString, Action`1 npgsqlOptionsAction)
NpgsqlDbContextOptionsBuilderExtensions.UseNpgsql[TContext](DbContextOptionsBuilder`1 optionsBuilder, String connectionString, Action`1 npgsqlOptionsAction)
<>c__DisplayClass1_0.<ConfigureServices>b__3(AbpDbContextConfigurationContext`1 dbContextOptions) línea 158
DbContextOptionsFactory.Configure[TDbContext](AbpDbContextOptions options, AbpDbContextConfigurationContext`1 context)
DbContextOptionsFactory.Create[TDbContext](IServiceProvider serviceProvider)
<>c__DisplayClass3_0.<Register>b__0(IComponentContext context, IEnumerable`1 parameters)
DelegateActivator.ActivateInstance(IComponentContext context, IEnumerable`1 parameters)
DelegateActivator.<ConfigurePipeline>b__2_0(ResolveRequestContext ctxt, Action`1 next)
DelegateMiddleware.Execute(ResolveRequestContext context, Action`1 next)
<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
DisposalTrackingMiddleware.Execute(ResolveRequestContext context, Action`1 next)
<>c__DisplayClass14_0.<BuildPipeline>b__1(ResolveRequestContext ctxt)
ActivatorErrorHandlingMiddleware.Execute(ResolveRequestContext context, Action`1 next)
Hi, We have already removed the login part from ABP in the Github Actions. Our license is on file appsettings.secrets.json. Now when we run the Github Actions in the migration part it shows us the following error: Error: Process completed with exit code 214.