this error 9.1.0 has been fixed. But 9.2.1 version reopen
- ABP Framework version: v8.3.1
- UI Type:Blazor Server
- Database System: EF Core (SQL Server,
- Tiered (for MVC) or Auth Server Separated (for Angular): yes
- Exception message and full stack trace:
- Steps to reproduce the issue:
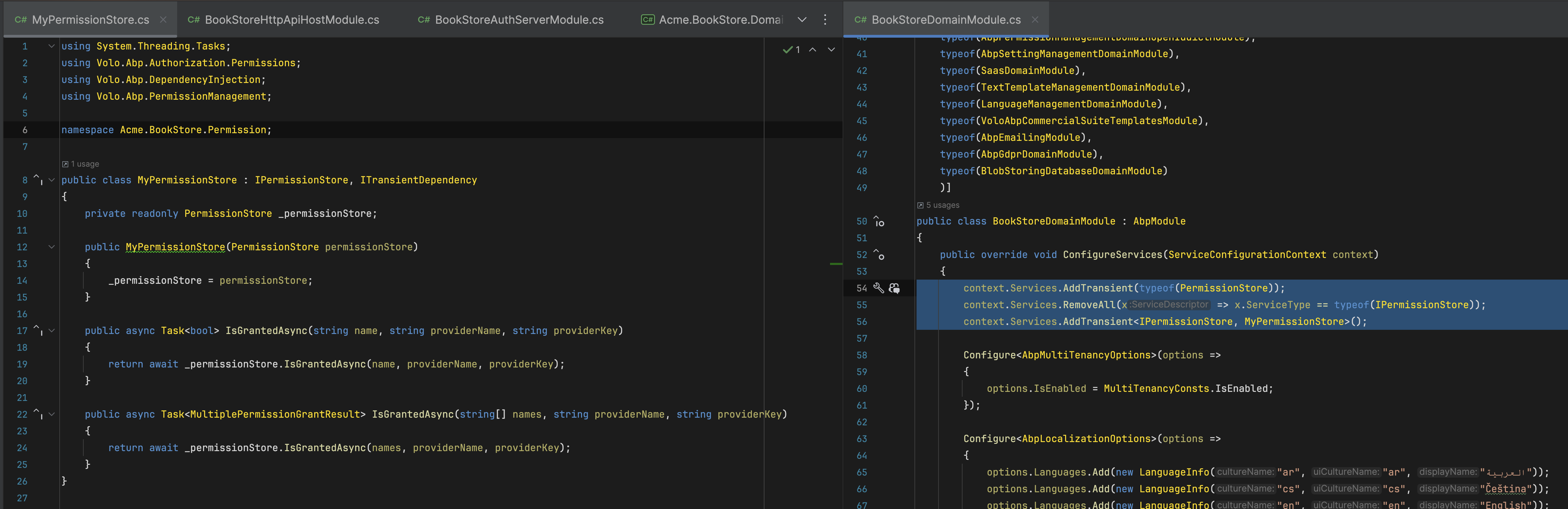
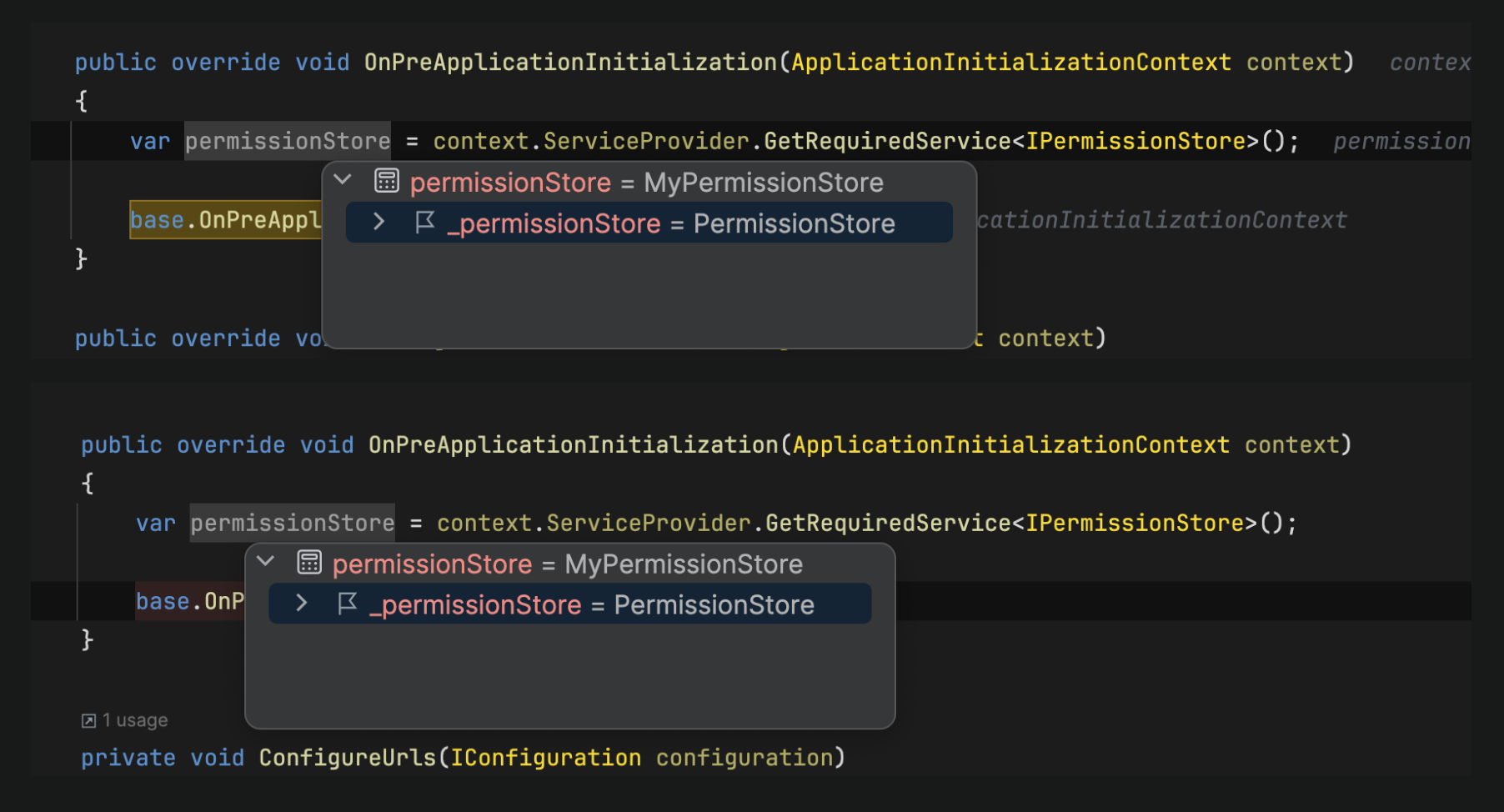
we overrided IPermissionStore in Application project . but after login IPermissionStore dont working Our code:
using Microsoft.Extensions.Logging.Abstractions; using Microsoft.Extensions.Logging; using System.Collections.Generic; using System.Linq; using System.Threading.Tasks; using Volo.Abp; using Volo.Abp.Authorization.Permissions; using Volo.Abp.Caching; using Volo.Abp.DependencyInjection; using Volo.Abp.PermissionManagement; using EnzimWeb.Helpers; using Volo.Abp.Identity; using Volo.Abp.Users; using Volo.Abp.Data; using System.Reflection; using IdentityModel; using System.Security.Claims; using Veri.Temel; using System; using Veri.Temel.Sabitler; using EnzimWeb.Permissions; using EnzimWeb.CrmKurums; using EnzimWeb.Rols; using Microsoft.Extensions.Configuration;
namespace EnzimWeb.Overrides { [Dependency(ReplaceServices = true)] [ExposeServices(typeof(IPermissionStore))] public class MyPermissionStore : IPermissionStore, ITransientDependency { public ILogger<PermissionStore> Logger { get; set; }
protected IPermissionGrantRepository PermissionGrantRepository { get; }
protected IPermissionDefinitionManager PermissionDefinitionManager { get; }
protected IDistributedCache<PermissionGrantCacheItem> Cache { get; }
protected IRoleHelperRepository _roleHelperRepository { get; }
protected IdentityUserManager _identityUserManager { get; }
protected ICurrentUser _currentUser { get; }
protected IIdentityRoleRepository _roleRepository;
private readonly IConfiguration _configuration;
public MyPermissionStore(
IPermissionGrantRepository permissionGrantRepository,
IDistributedCache<PermissionGrantCacheItem> cache,
IPermissionDefinitionManager permissionDefinitionManager,
IRoleHelperRepository roleHelperRepository,
IdentityUserManager userManager,
ICurrentUser currentUser,
IIdentityRoleRepository roleRepository,
IConfiguration configuration)
{
PermissionGrantRepository = permissionGrantRepository;
Cache = cache;
PermissionDefinitionManager = permissionDefinitionManager;
Logger = NullLogger<PermissionStore>.Instance;
_roleHelperRepository = roleHelperRepository;
_identityUserManager = userManager;
_currentUser = currentUser;
_roleRepository = roleRepository;
_configuration = configuration;
}
public virtual async Task<bool> IsGrantedAsync(string name, string providerName, string providerKey)
{
return (await GetCacheItemAsync(name, providerName, providerKey)).IsGranted;
}
protected virtual async Task<PermissionGrantCacheItem> GetCacheItemAsync(
string name,
string providerName,
string providerKey)
{
var cacheKey = CalculateCacheKey(name, providerName, providerKey);
Logger.LogInformation($"PermissionStore.GetCacheItemAsync: {cacheKey}");
var cacheItem = await Cache.GetAsync(cacheKey);
if (cacheItem != null)
{
Logger.LogInformation($"Found in the cache: {cacheKey}");
return cacheItem;
}
Logger.LogInformation($"Not found in the cache: {cacheKey}");
cacheItem = new PermissionGrantCacheItem(false);
await SetCacheItemsAsync(providerName, providerKey, name, cacheItem);
return cacheItem;
}
protected virtual async Task SetCacheItemsAsync(
string providerName,
string providerKey,
string currentName,
PermissionGrantCacheItem currentCacheItem)
{
var permissions = await PermissionDefinitionManager.GetPermissionsAsync();
Logger.LogInformation($"Getting all granted permissions from the repository for this provider name,key: {providerName},{providerKey}");
var grantedPermissionsHashSet = new HashSet<string>(
(await PermissionGrantRepository.GetListAsync(providerName, providerKey)).Select(p => p.Name)
);
foreach (var item in await GetEnzimPermissions(providerName, providerKey))
{
grantedPermissionsHashSet.AddIfNotContains(item);
}
Logger.LogInformation($"Setting the cache items. Count: {permissions.Count}");
var cacheItems = new List<KeyValuePair<string, PermissionGrantCacheItem>>();
foreach (var permission in permissions)
{
var isGranted = grantedPermissionsHashSet.Contains(permission.Name);
cacheItems.Add(new KeyValuePair<string, PermissionGrantCacheItem>(
CalculateCacheKey(permission.Name, providerName, providerKey),
new PermissionGrantCacheItem(isGranted))
);
if (permission.Name == currentName)
{
currentCacheItem.IsGranted = isGranted;
}
}
await Cache.SetManyAsync(cacheItems);
Logger.LogInformation($"Finished setting the cache items. Count: {permissions.Count}");
}
public virtual async Task<MultiplePermissionGrantResult> IsGrantedAsync(string[] names, string providerName, string providerKey)
{
Check.NotNullOrEmpty(names, nameof(names));
var result = new MultiplePermissionGrantResult();
if (names.Length == 1)
{
var name = names.First();
result.Result.Add(name,
await IsGrantedAsync(names.First(), providerName, providerKey)
? PermissionGrantResult.Granted
: PermissionGrantResult.Undefined);
return result;
}
var cacheItems = await GetCacheItemsAsync(names, providerName, providerKey);
foreach (var item in cacheItems)
{
result.Result.Add(GetPermissionNameFormCacheKeyOrNull(item.Key),
item.Value != null && item.Value.IsGranted
? PermissionGrantResult.Granted
: PermissionGrantResult.Undefined);
}
return result;
}
protected virtual async Task<List<KeyValuePair<string, PermissionGrantCacheItem>>> GetCacheItemsAsync(
string[] names,
string providerName,
string providerKey)
{
var cacheKeys = names.Select(x => CalculateCacheKey(x, providerName, providerKey)).ToList();
Logger.LogInformation($"PermissionStore.GetCacheItemAsync: {string.Join(",", cacheKeys)}");
var cacheItems = (await Cache.GetManyAsync(cacheKeys)).ToList();
if (cacheItems.All(x => x.Value != null))
{
Logger.LogInformation($"Found in the cache: {string.Join(",", cacheKeys)}");
return cacheItems;
}
var notCacheKeys = cacheItems.Where(x => x.Value == null).Select(x => x.Key).ToList();
Logger.LogInformation($"Not found in the cache: {string.Join(",", notCacheKeys)}");
var newCacheItems = await SetCacheItemsAsync(providerName, providerKey, notCacheKeys);
var result = new List<KeyValuePair<string, PermissionGrantCacheItem>>();
foreach (var key in cacheKeys)
{
var item = newCacheItems.FirstOrDefault(x => x.Key == key);
if (item.Value == null)
{
item = cacheItems.FirstOrDefault(x => x.Key == key);
}
result.Add(new KeyValuePair<string, PermissionGrantCacheItem>(key, item.Value));
}
return result;
}
protected virtual async Task<List<KeyValuePair<string, PermissionGrantCacheItem>>> SetCacheItemsAsync(
string providerName,
string providerKey,
List<string> notCacheKeys)
{
var permissions = (await PermissionDefinitionManager.GetPermissionsAsync())
.Where(x => notCacheKeys.Any(k => GetPermissionNameFormCacheKeyOrNull(k) == x.Name)).ToList();
Logger.LogInformation($"Getting not cache granted permissions from the repository for this provider name,key: {providerName},{providerKey}");
var grantedPermissionsHashSet = new HashSet<string>(
(await PermissionGrantRepository.GetListAsync(notCacheKeys.Select(GetPermissionNameFormCacheKeyOrNull).ToArray(), providerName, providerKey)).Select(p => p.Name)
);
var nCacheKeys = notCacheKeys.Select(GetPermissionNameFormCacheKeyOrNull).ToArray();
foreach (var item in await GetEnzimPermissions(providerName, providerKey))
{
grantedPermissionsHashSet.AddIfNotContains(item);
}
Logger.LogInformation($"Setting the cache items. Count: {permissions.Count}");
var cacheItems = new List<KeyValuePair<string, PermissionGrantCacheItem>>();
foreach (var permission in permissions)
{
var isGranted = grantedPermissionsHashSet.Contains(permission.Name);
cacheItems.Add(new KeyValuePair<string, PermissionGrantCacheItem>(
CalculateCacheKey(permission.Name, providerName, providerKey),
new PermissionGrantCacheItem(isGranted))
);
}
await Cache.SetManyAsync(cacheItems);
Logger.LogInformation($"Finished setting the cache items. Count: {permissions.Count}");
return cacheItems;
}
protected virtual string CalculateCacheKey(string name, string providerName, string providerKey)
{
return PermissionGrantCacheItem.CalculateCacheKey(name, providerName, providerKey);
}
protected virtual string GetPermissionNameFormCacheKeyOrNull(string key)
{
//TODO: throw ex when name is null?
return PermissionGrantCacheItem.GetPermissionNameFormCacheKeyOrNull(key);
}
private async Task<List<string>> GetEnzimPermissions(string providerName, string providerKey)
{
List<string> permissions = new List<string>();
return permissions;
}
}
}
and we added Application project's ConfigureServices
context.Services.Replace(
ServiceDescriptor.Transient<IPermissionStore, MyPermissionStore>()
);
27 Answer(s)
-
0
hi
What is the instance of
IPermissionStoreif you get it from DI? -
0
I don't understand your question. we shared code . we want to override IPermissionStore ? how can I implement abp version 8.3.1 this code worked on abp version 8.1.4
-
0
hi
You can inject the
IPermissionStoreand set a breakpoint to see its instance. Or you can share a test project with your PermissionStore. I will download and check it. liming.ma@volosoft.comThanks
-
0
can you share default tiered blazor server project with override IPermissionStore
cetin.sahin@iberteknoloji.com.
-
0
No problem. Please create a template project and share it via https://wetransfer.com/
I will download and change code.
liming.ma@volosoft.com
Thanks.
-
0
I think I wasn't able to explain our issue clearly.
What we want is to override the IPermissionStore in the most up-to-date abp.io Blazor Server tiered project. We want to make additional custom developments on the IPermissionStore side.
We want to replace the service with the following annotations.
I don't understand why we need to create the template project ourselves for this.
[Dependency(ReplaceServices = true)] [ExposeServices(typeof(IPermissionStore ))] -
0
ok, I see your point.
I don't understand why we need to create the template project ourselves for this.
Because the template project contains the license info, that's why you need to create it and share it. Then, I will add the code for you.
Thanks.
-
0
I sent we transfer code in e-mail can you check IPermissionStore run after log in
-
0
-
0
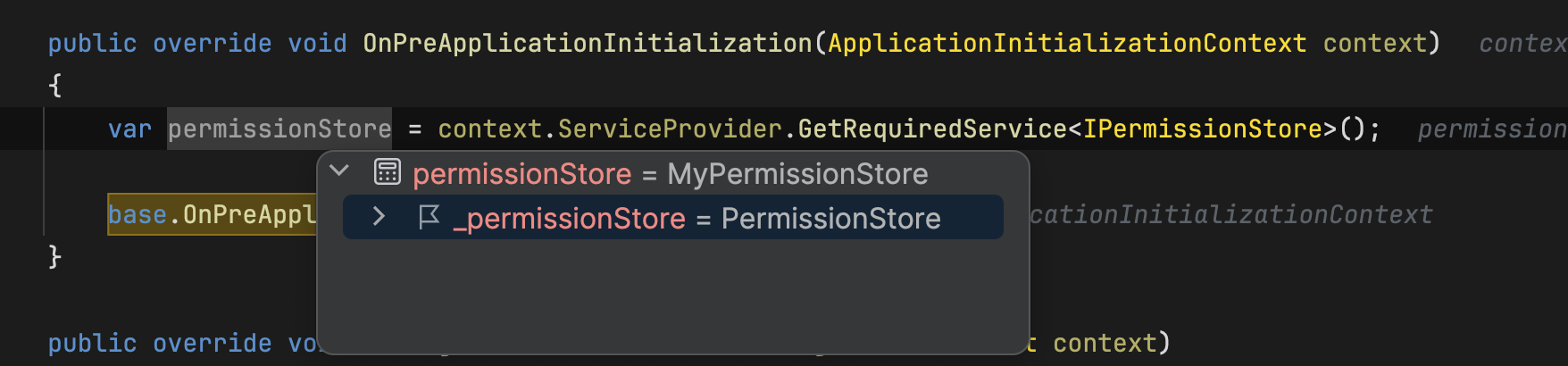
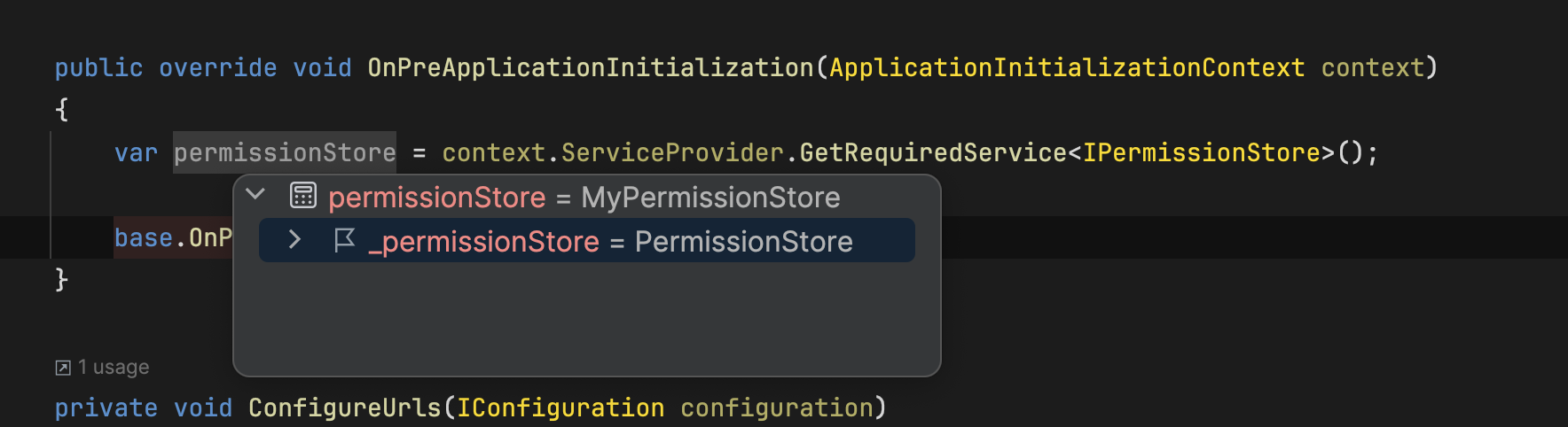
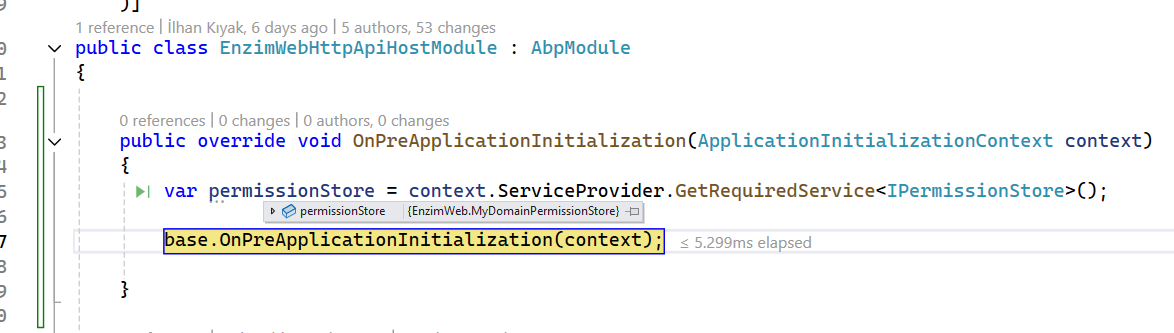
we want to override IPermissionStore with this code [Dependency(ReplaceServices = true)] [ExposeServices(typeof(IPermissionStore))] I set break point on IsGrantedAsyncmethod in MyPermissionStore class but the break point doesn't trigger.
-
0
hi
Can you try the code I provided?
then inject the
IPermissionStoreand see it type. should beMyPermissionStore -
0
-
0
hi
but api host doesn't call IPermissionStore .
IPermissionStoreis only called when checking permissions.Can you reproduce this in a template project? That way I can check.
Thanks
-
0
Hi; we cant triggered IPermissionStore IsGrantedAsync method. can you recommend another procedure for override Permission save and get method
-
0
Your
MyPermissionStorehas already replaced the built-inPermissionStore.I don't understand what your problem is with it.
Can you reproduce your problem in a template project? That way I can check.
Thanks
-
0
Our project cant trigger PermissionStore.
-
0
hi
Can you reproduce your problem in a template project? That way I can check.
-
0
our code run 8.1.4 version succesfully But 8.3.1 version cant trigger PermissionStore. Did you change the Permission Stored structure in version 8.3.1?
-
0
hi
There is no such change in the new version.
-
0
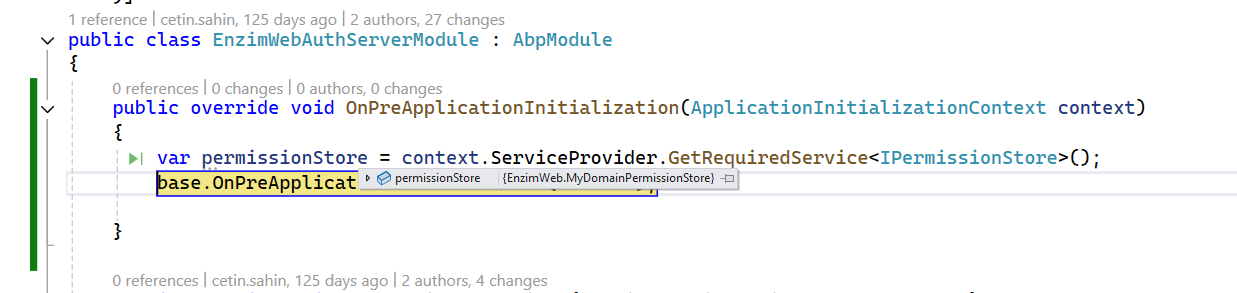
we overrided IPermissionStore in Application project. is it wrong
-
0
hi
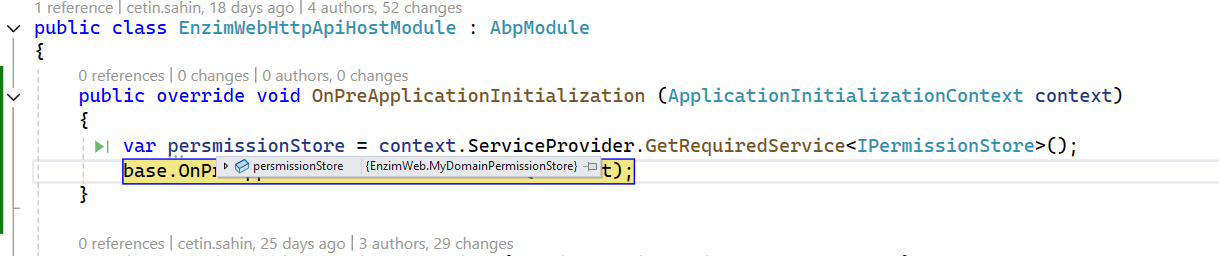
You can try to override
IPermissionStorein Domain project. -
0
can we get online meeting ?
-
0
-
0
I made the changes as you requested, but unfortunately the permission store is not triggered.
Also, even if we do not override IPermissionStore, abp.io permission store does not work. Menus are not loaded. Authorizations are not received. The values of permissions pulled from the redis appear to be null.

-
0
Override
IPermissionStoremay not be the solution to your problem.Also, even if we do not override IPermissionStore, abp.io permission store does not work. Menus are not loaded. Authorizations are not received. The values of permissions pulled from the redis appear to be null.
In this case, it would be better if you could share a project that reproduces the problem, and I will check it locally, it will be difficult to check your code in a remote meeting.
liming.ma@volosoft.com
Thanks