- ABP Framework version: v7.4.5
- UI Type: Angular
- Database System: EF Core (SQL Serve)
- Tiered (for MVC) or Auth Server Separated (for Angular): yes/
- Implemting SSO I have implemented Okta SSO and obtained the ID Token from Okta. I have also installed the following packages:
@okta/okta-angular (v6.4.0) @okta/okta-auth-js (v7.10.1)
Authentication is working as expected, as confirmed by the following check:
this.oktaAuth.isAuthenticated().then(async (authStatus) => {
if (authStatus) {
// Authenticated successfully
}
});
Additionally, I can successfully invoke APIs using this authentication setup but not check authorization with different role:
context.Services.AddAuthentication(options =>
{
options.DefaultAuthenticateScheme = "MultipleAuthSchemes";
options.DefaultChallengeScheme = "MultipleAuthSchemes";
})
.AddPolicyScheme("MultipleAuthSchemes", JwtBearerDefaults.AuthenticationScheme, options =>
{
options.ForwardDefaultSelector = context =>
{
string? authorization = context.Request.Headers["Authorization"];
if (!string.IsNullOrEmpty(authorization) && authorization.StartsWith("Bearer "))
{
var token = authorization.Substring("Bearer ".Length).Trim();
return token.Contains("okta") ? "okta_jwt_schema" : JwtBearerDefaults.AuthenticationScheme;
}
return JwtBearerDefaults.AuthenticationScheme;
};
})
.AddJwtBearer(JwtBearerDefaults.AuthenticationScheme, options =>
{
options.Authority = configuration["AuthServer:Authority"];
options.RequireHttpsMetadata = Convert.ToBoolean(configuration["AuthServer:RequireHttpsMetadata"]);
options.Audience = "Project42";
})
.AddJwtBearer("okta_jwt_schema", options =>
{
options.Authority = configuration["Okta:Authority"];
options.RequireHttpsMetadata = Convert.ToBoolean(configuration["Okta:RequireHttpsMetadata"]);
options.Audience = "api://default";
options.TokenValidationParameters = new TokenValidationParameters
{
ValidateIssuerSigningKey = true,
ValidIssuer = "https://dev-96317405.okta.com/oauth2/default",
ValidAudience = "api://default",
ValidateLifetime = true
};
});
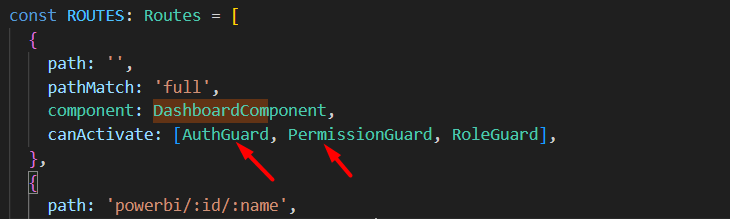
Now, I have route guards set up as follows:
{
path: '',
pathMatch: 'full',
component: DashboardComponent,
canActivate: [AuthGuard, PermissionGuard, RoleGuard],
}
I believe these guards require the ABP token instead of the Okta token. How can I properly pass authentication to AuthGuard and PermissionGuard while ensuring authorization in the system using Okta?
Can I do something like if authenticated then logged in with the user by matching the email but I don't know the password I have this method this.authService .login({ username, password, rememberMe })
if I can login into the system without password or similar method in backend then I believe i can login the user with proper abp login and can just authenticate with okta.
44 Answer(s)
-
0
-
0
Hello, our relevant team member will respond to you as soon as possible.
-
0
sure, please respond at earliest. I need to windup, thanks.
-
0
Unfortunately, our team member is out of working time at the moment. He will probably respond tomorrow during the day. Thank you for your patience.
-
0
Sure.
-
0
hi
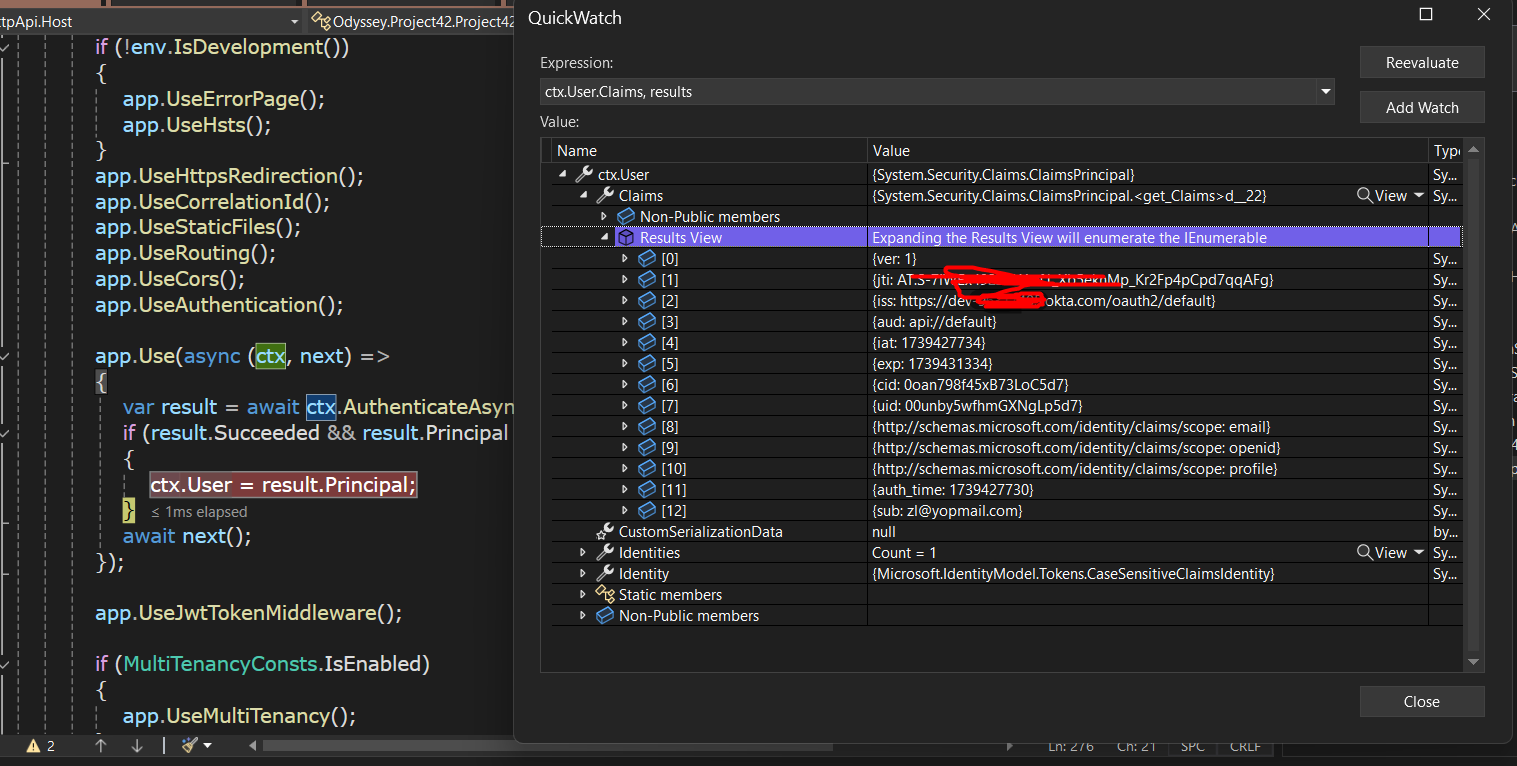
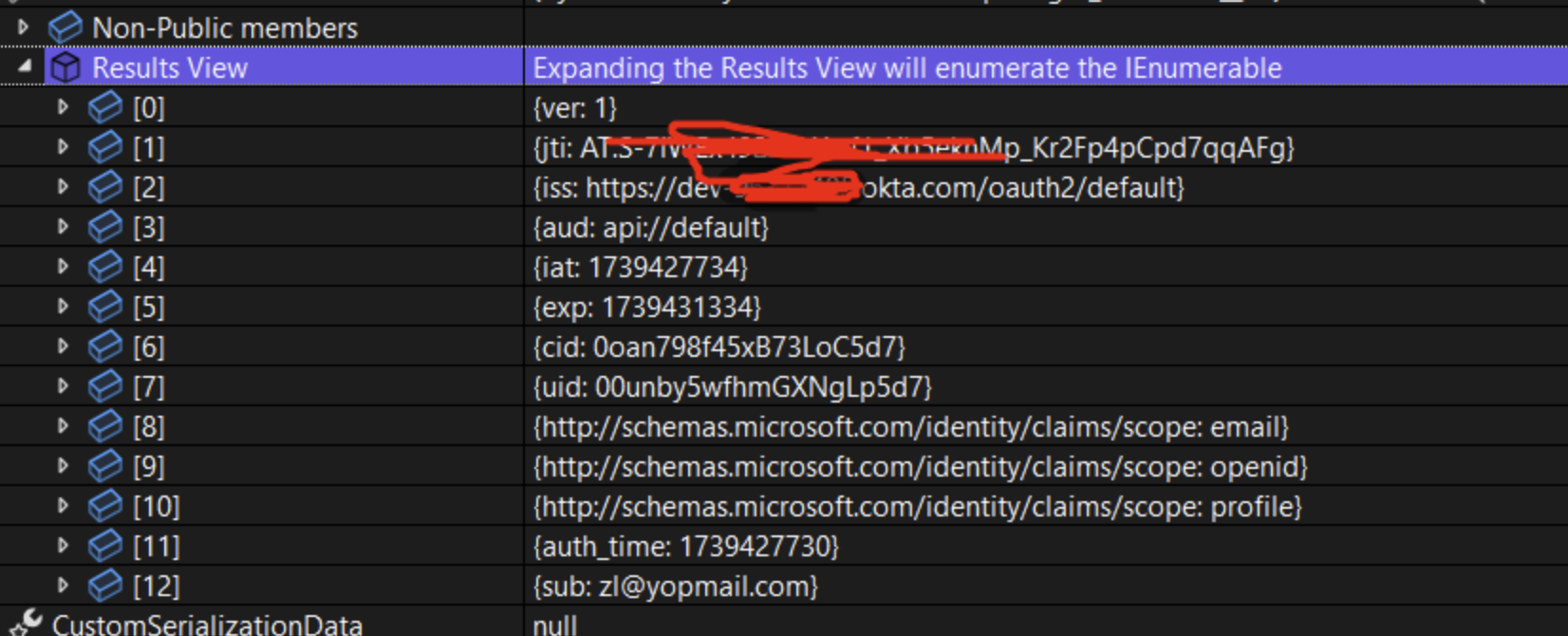
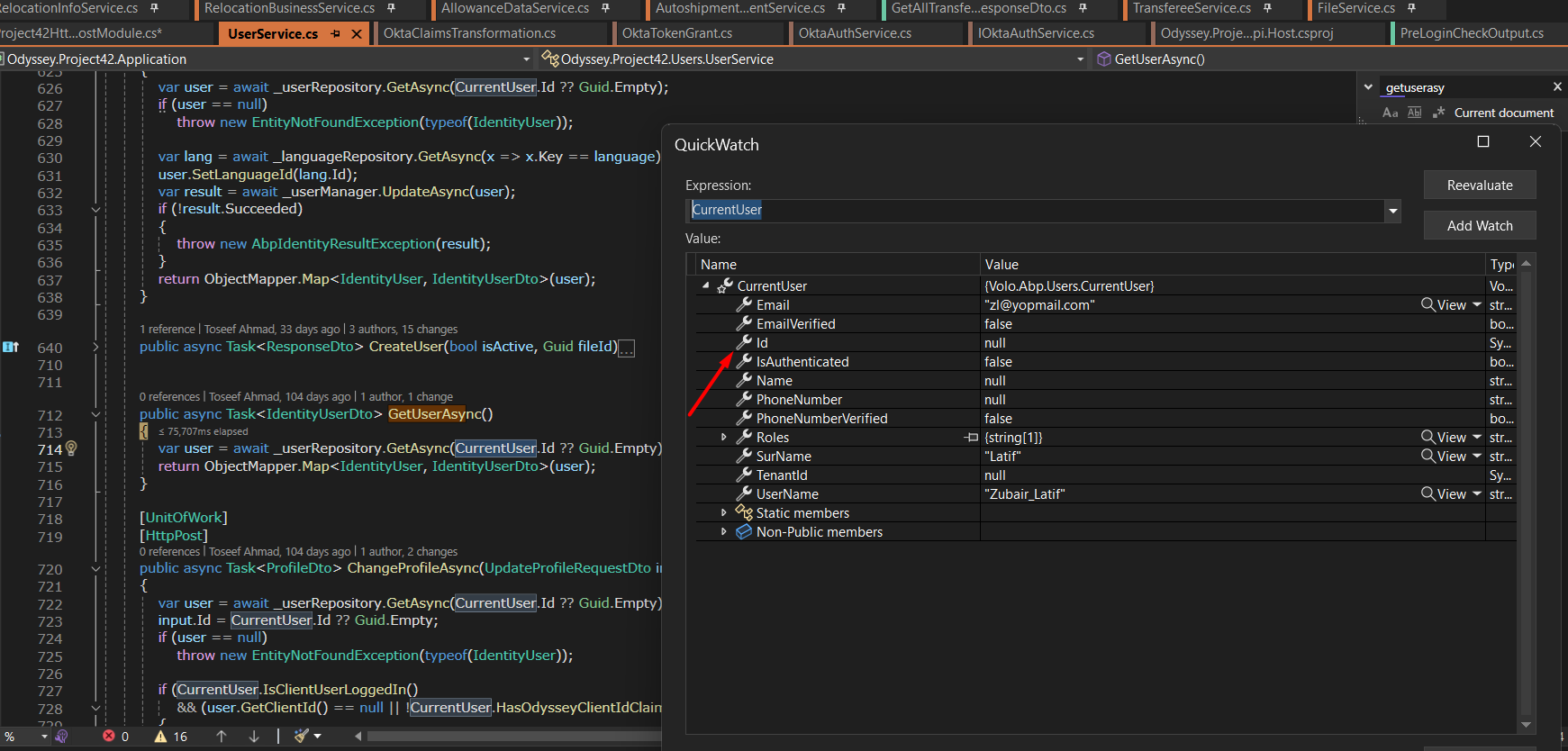
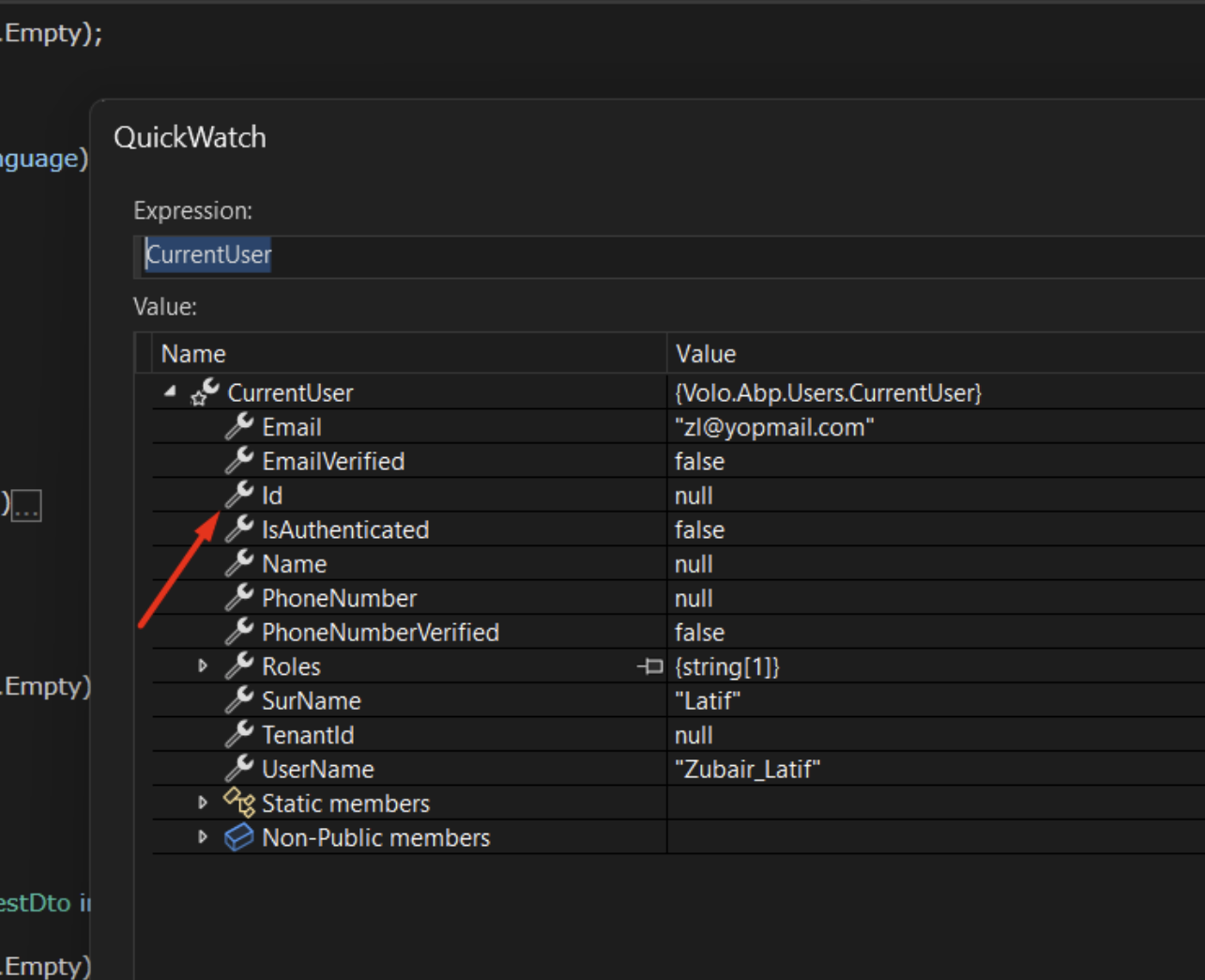
Can you check the current principal(HttpContext.User) after authentication using
okta_jwt_schema?What are the claims(type:value)?
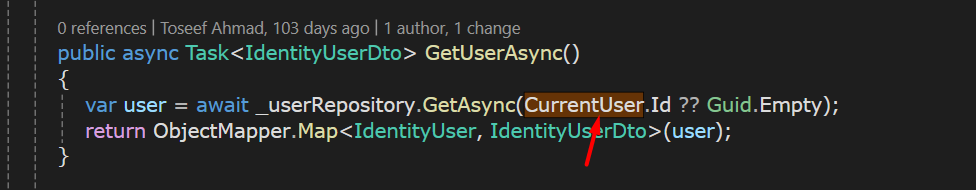
The
CurrentUser's values come from claims.AddJwtBearer("okta_jwt_schema", options => { options.Authority = configuration["Okta:Authority"]; options.RequireHttpsMetadata = Convert.ToBoolean(configuration["Okta:RequireHttpsMetadata"]); options.Audience = "api://default"; options.TokenValidationParameters = new TokenValidationParameters { ValidateIssuerSigningKey = true, ValidIssuer = "https://dev-96317405.okta.com/oauth2/default", ValidAudience = "api://default", ValidateLifetime = true }; }); -
0
-
0
also needs to address this issue, I have route guards set up as follows:
{ path: '', pathMatch: 'full', component: DashboardComponent, canActivate: [AuthGuard, PermissionGuard, RoleGuard], }
I believe these guards require the ABP token instead of the Okta token. How can I properly pass authentication to AuthGuard and PermissionGuard while ensuring authorization in the system using Okta?
-
0
-
0
hi
Can I do something like if authenticated then logged in with the user by matching the email but I don't know the password I have this method this.authService .login({ username, password, rememberMe })
if I can login into the system without password or similar method in backend then I believe i can login the user with proper abp login and can just authenticate with okta.
IF NOT then what changes I need to make to compatible claim with ABP?
-
0
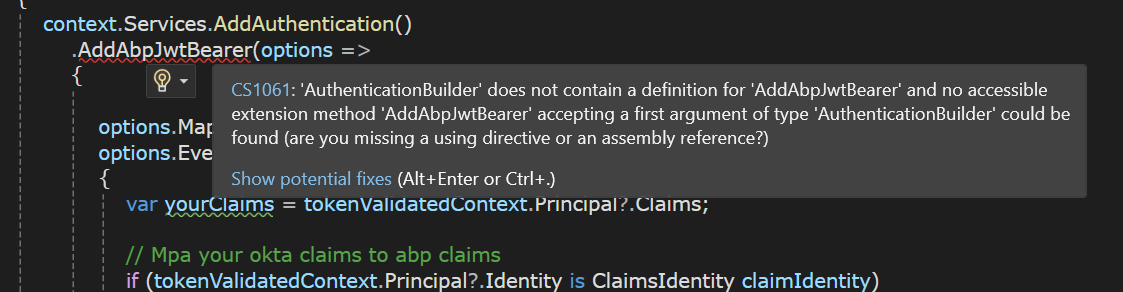
hi
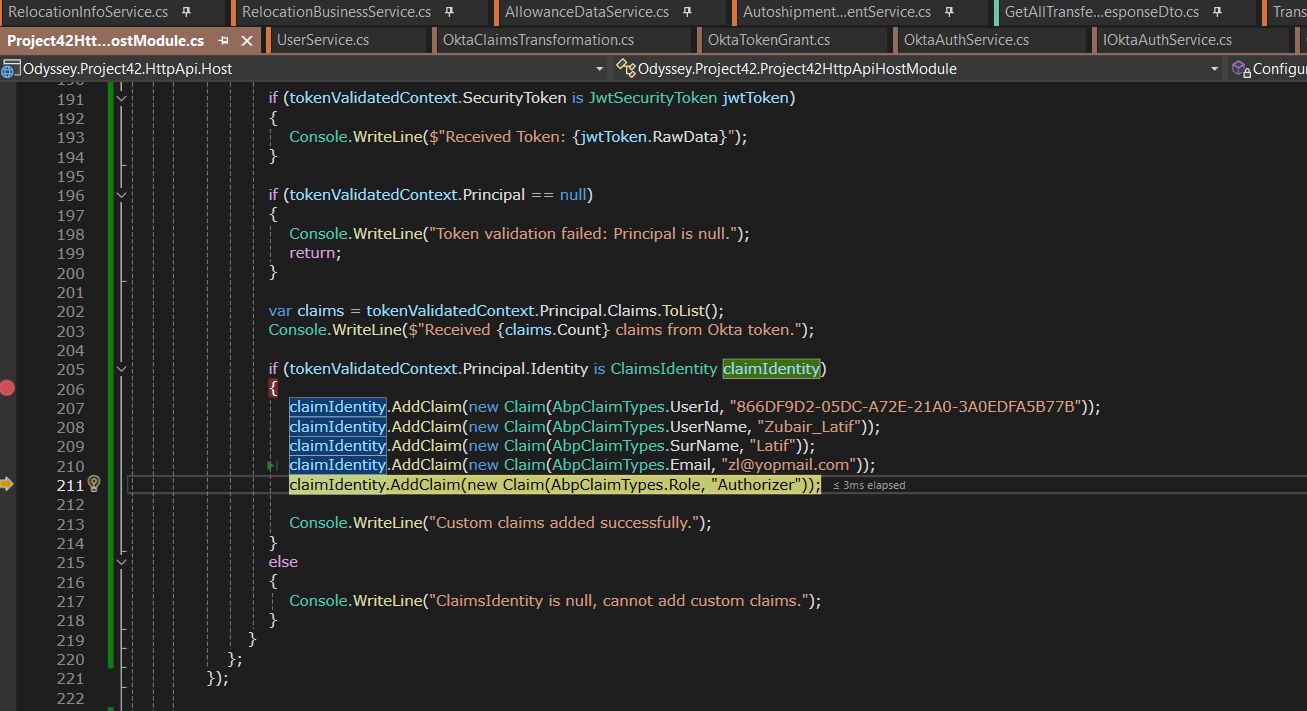
AddJwtBearermethod can map yourokta_jwt_schemato compatible with abp..AddAbpJwtBearer(options => { options.MapInboundClaims = false; options.Events.OnTokenValidated = async tokenValidatedContext => { var yourClaims = tokenValidatedContext.Principal?.Claims; // Mpa your okta claims to abp claims if (tokenValidatedContext.Principal?.Identity is ClaimsIdentity claimIdentity) { claimIdentity.AddClaim(AbpClaimTypes.UserId, ""); claimIdentity.AddClaim(AbpClaimTypes.UserName, ""); claimIdentity.AddClaim(AbpClaimTypes.SurName, ""); claimIdentity.AddClaim(AbpClaimTypes.Email, ""); claimIdentity.AddClaim(AbpClaimTypes.Role, ""); } }; }); -
0
-
0
Hi
You can replace it to
AddJwtBearer -
0
-
0
-
0
-
0
-
0
Can you try to debug the
FindUserIdmethod?https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.Security/System/Security/Principal/AbpClaimsIdentityExtensions.cs#L11-L47 https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.Security/Volo/Abp/Users/CurrentUser.cs#L16
-
0
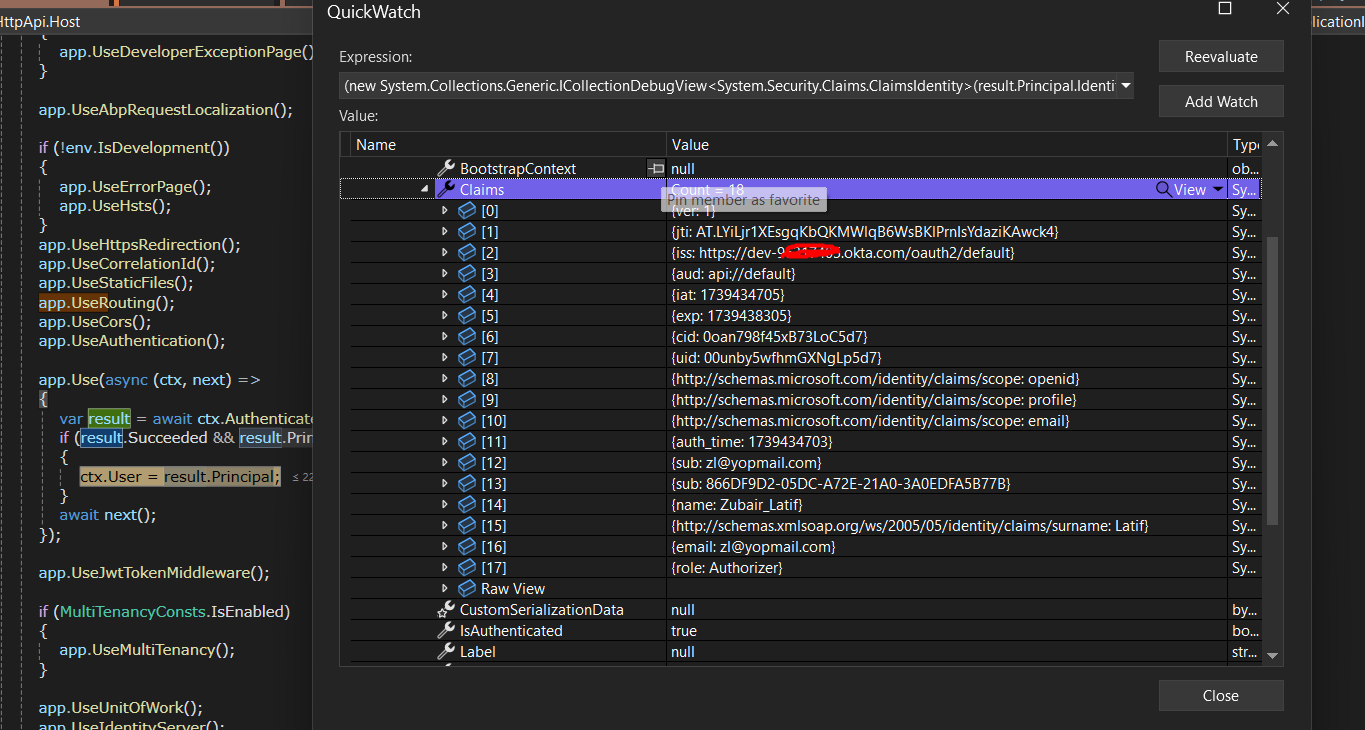
Hi I'm able to fetch the UserId, there are two sub in my claims, I just make it one sub claim.
Now still my frontend application is not loading as expected many components are not loading.
I believe this is the issue
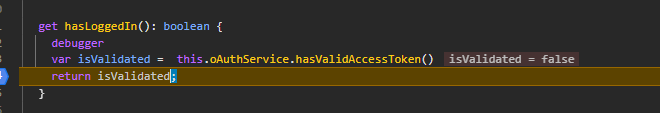
I have seen AuthGuard and PermissionGuard are not allowing me access dashboard with my Okta Authentication
-
0
What are JSON results of
https://yourwebsite/api/abp/application-configuration?includeLocalizationResources=falsein your angular app? -
0
-
0
hi
liming.ma@volosoft.com
-
0
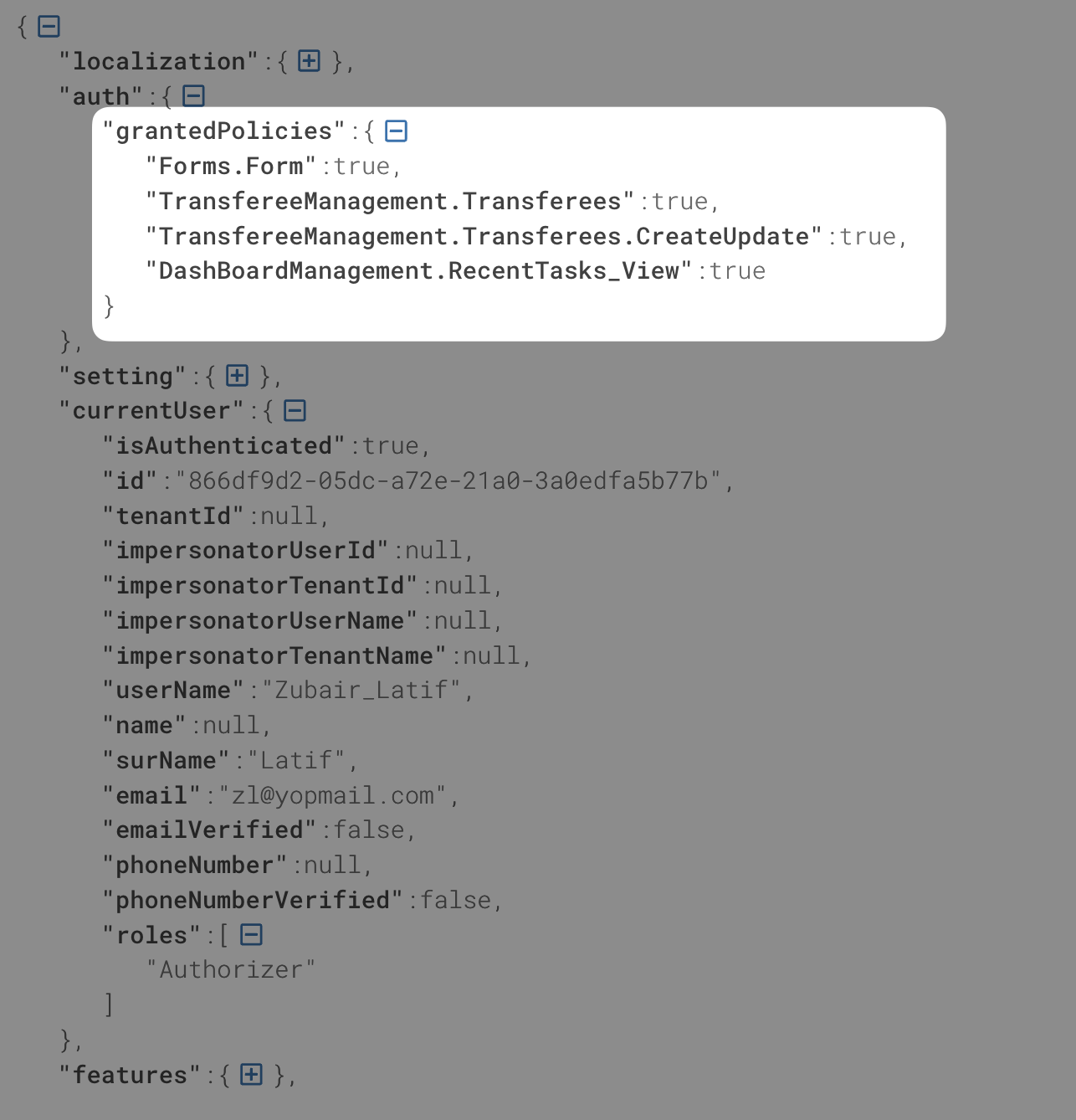
Hi I have shared the response with you.
-
0
-
0