We have an old 3.1v Microservice Template, But version is upgraded 8.0. And we need to upgrade the 3.1v Microservice Template to the latest version. What is the best approach to upgrade: should we create a new template with the latest version and manually migrate the code?
Could you please provide your guidance on this?
For your reference pls find attached screen shot.

After adding the redirectUri and responseType parameters in my environment.ts file as part of the SSO OIDC integration, the SSO OIDC integration is working as expected. However, it is breaking the existing functionality.
If I comment out the redirectUri parameter, my Angular login page loads successfully. However, without commenting out the redirectUri parameter, how can I handle both scenarios: the normal user login page and the SSO OIDC login functionality?
const baseUrl = 'http://localhost:4200';
const oAuthConfig = {
issuer: 'https://localhost:44350/',
redirectUri: baseUrl,
clientId: '',
responseType: 'code',
scope: 'offline_access ',
requireHttps: true,
showDebugInformation: true,
requireHttps: true,
};
The "ClientType" column in the "OpenIddictApplications" table was initially set to "confidential" and after that you update value as "public", Then Angular application was able to successfully redirect.
However, I have notice after some time, this value automatically changed to "confidential". I have cross-checked the application but was unable to find where the value is being set.
Can you please suggest how I can fix this issue?
Tenant-Id and Tenant-Name Not Set in Header After Dashboard Redirect (SSO OIDC) #8132
https://abp.io/support/questions/8132/Tenant-Id-and-Tenant-Name-Not-Set-in-Header-After-Dashboard-Redirect-SSO-OIDC?CurrentPage=5
We have a requirement where, when a client clicks on our application logo (which is already configured within their application), they should be redirected directly to the IdP's login page instead of the ABP.IO login page. After authentication with the IdP, the user should be redirected to our dashboard.
Using below ABP.IO support ticket i am successfully able to run POC project. Note :- Tenant not set in POC project.
Error :- After integrating the same code into our existing project, we successfully authenticated with the IDP, added the user to the database, and were redirected to the dashboard. However, after a few seconds, the application automatically redirects to the logout page I have cross check log it's look like tenant not set that's why user not able to login.
For your refence please find below log
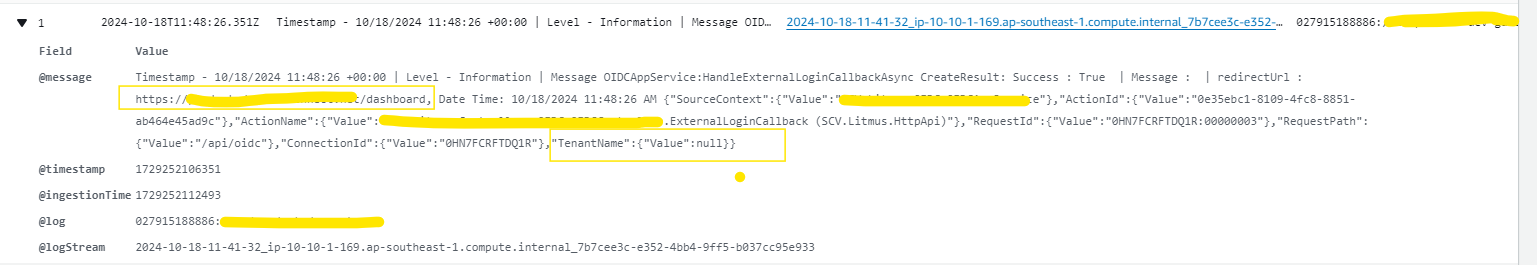
We need to set the tenant name and tenant ID headers for the dashboard redirect URL. How can we do this ?
Subject :- SSO OIDC integration issue
Exception details :- In our microservices architecture, we handle internal API calls using HTTP, while external applications access our APIs over HTTPS. However, when setting up the callback URL, it automatically picks up the internal domain with HTTP, leading to issues when using HTTPS.
To address this, I added the following code to modify the redirect URI:
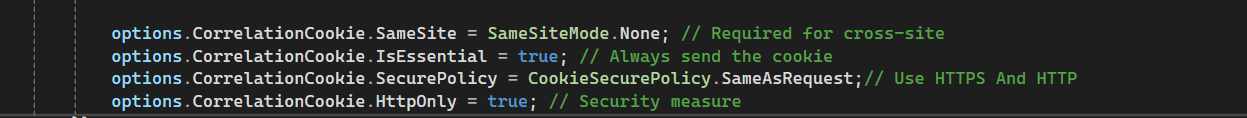
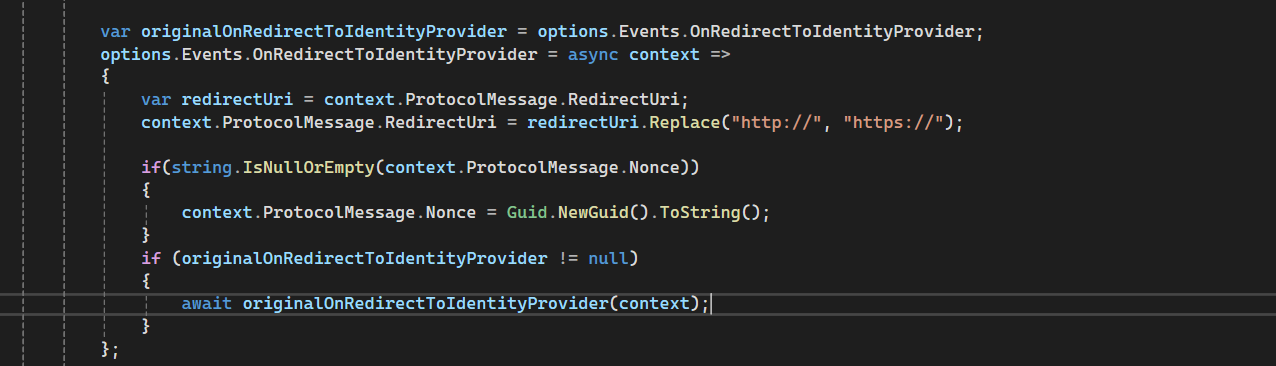 After implementing this change, I started facing the "Correlation failed" error in the remote authentication process. I’ve applied some additional fixes to resolve this issue.
After implementing this change, I started facing the "Correlation failed" error in the remote authentication process. I’ve applied some additional fixes to resolve this issue.
I am currently facing an issue in my application, and I would greatly appreciate your assistance in resolving it.
public async Task<bool> CreateAsync(IdentityUserCreateDto input, Guid tenantId)
{
try
{
var newUserName = await GetUniqueUserNameAsync(input.Name.Trim(), input.Surname.Trim());
var user = new IdentityUser(\_guidGenerator.Create(), newUserName.Trim(), input.Email, tenantId);
var creationResult = await \_identityUserManager.CreateAsync(user, input.Password.Trim());
creationResult.CheckErrors();
await \_identityUserManager.SetEmailAsync(user, input.Email.Trim());
await \_identityUserManager.SetPhoneNumberAsync(user, input.PhoneNumber.Trim());
user.Name = input.Name.Trim();
user.Surname = input.Surname.Trim();
var claimsToAdd = new List\<Claim>
{
new Claim(ClaimTypes.Email, input.Email.Trim()),
};
await \_identityUserManager.AddClaimsAsync(user, claimsToAdd);
await \_unitOfWorkManager.Current.SaveChangesAsync();
await assignRoles(input, user);
var userDetails = await \_identityUserManager.GetByIdAsync(user.Id);
if (userDetails != null)
{
userDetails.SetProperty("Status", 1);
userDetails.SetProperty("Language", "en");
}
await \_unitOfWorkManager.Current.SaveChangesAsync();
}
catch (Exception ex)
{
}
}
<br>
After successfully adding the user to the database, I encountered an error when executing the line var userDetails = await _identityUserManager.GetByIdAsync(user.Id);.
I have verified that the user was added to the database and that the user ID is present and correct.
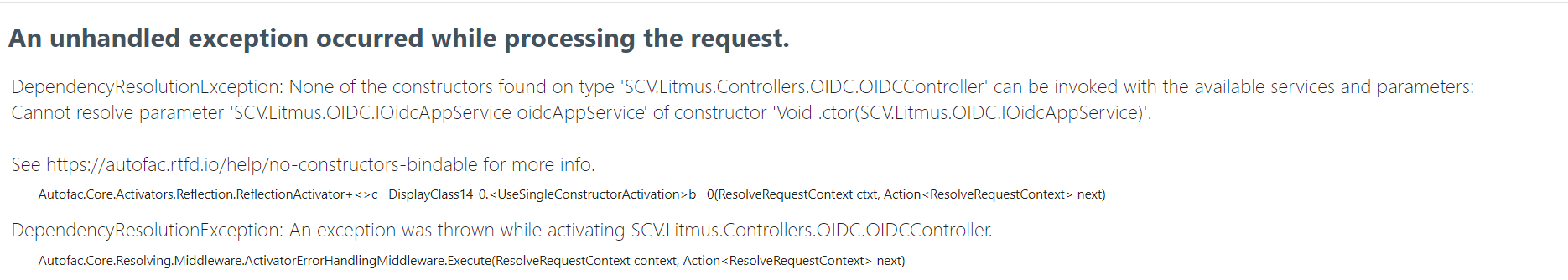
I need your assistance.
Objective: To bypass the ABP.IO login page and redirect users directly to the IdP’s login page, and after successful authentication, redirect them to application’s dashboard.
Description :- I have integrated OpenIdConnect with a third-party Identity Provider (IdP) in a new ABP.IO template project, and it is working as expected. However, we have a requirement where, when a client clicks on our application logo (which is already configured within their application), they should be redirected directly to the IdP's login page instead of the ABP.IO login page. After authentication with the IdP, the user should be redirected to our dashboard.
I need assistance how to handle routing and above scenario in abp.io template.
<br> I don't want to show below screen for OpenIdConnect login user.
However, I have added very high level analysis code please go thought it and let me know correct or not ?
Step 1: Add NuGet Packages
Ensure you have the following packages installed in our Gateway web project :
<PackageReference Include="Microsoft.AspNetCore.Authentication.OpenIdConnect" Version="5.0.0" />
<PackageReference Include="Microsoft.IdentityModel.Protocols.OpenIdConnect" Version="6.8.0" />
Step 2: Configure appsettings.json
Add the OpenIdConnect settings to gateway appsettings.json:
{
"Authentication": {
"OpenId": {
"Authority": "https://{yourOktaDomain}/oauth2/default",
"ClientId": "{yourClientId}",
"ClientSecret": "{yourClientSecret}",
"ResponseType": "code",
"SaveTokens": true,
"GetClaimsFromUserInfoEndpoint": true,
"Scope": "openid profile email"
}
}
}
3. Update the `ConfigureServices` and `Configure` methods to set up authentication:
//The code you provided configures authorization policies in your application,
specifically setting a default authorization policy that requires users to be authenticated
using either the primary JWT Bearer scheme or the OIDC JWT Bearer scheme.
private static void ConfigureAuthentication(ServiceConfigurationContext context, IConfiguration configuration)
{
context.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme)
.AddJwtBearer(JwtBearerDefaults.AuthenticationScheme, options =>
{
options.Authority = configuration["AuthServer:Authority"];
options.RequireHttpsMetadata = false;
options.Audience = configuration["AuthServer:ApiResource"];
})
.AddJwtBearer("OIDC", options =>
{
options.Audience = configuration["AuthServer:ApiResource"];
options.RequireHttpsMetadata = false;
options.Authority = configuration["AuthServer:Authority"];
});
Log.Information($"ApiResource: {configuration["AuthServer:ApiResource"]}");
// Authorization
context.Services.AddAuthorization(options =>
{
var defaultAuthorizationPolicyBuilder = new AuthorizationPolicyBuilder(
JwtBearerDefaults.AuthenticationScheme,
"OIDC");
defaultAuthorizationPolicyBuilder =
defaultAuthorizationPolicyBuilder.RequireAuthenticatedUser();
options.DefaultPolicy = defaultAuthorizationPolicyBuilder.Build();
});
}
public void ConfigureServices(IServiceCollection services)
{
need to discuss commented code
//services.AddAuthentication(options =>
// {
// options.DefaultScheme = CookieAuthenticationDefaults.AuthenticationScheme;
// options.DefaultChallengeScheme = OpenIdConnectDefaults.AuthenticationScheme;
//})
// .AddCookie()
.AddOpenIdConnect(OpenIdConnectDefaults.AuthenticationScheme, options =>
{
options.Authority = Configuration["Authentication:OpenId:Authority"];
options.ClientId = Configuration["Authentication:OpenId:ClientId"];
options.ClientSecret = Configuration["Authentication:OpenId:ClientSecret"];
options.ResponseType = Configuration["Authentication:OpenId:ResponseType"];
options.SaveTokens = Configuration["Authentication:OpenId:SaveTokens"];
options.GetClaimsFromUserInfoEndpoint = Configuration["Authentication:OpenId:GetClaimsFromUserInfoEndpoint"];
options.Scope.Add("openid");
options.Scope.Add("profile");
options.Scope.Add("email");
});
}
public override void OnApplicationInitialization(ApplicationInitializationContext context)
{
app.UseAuthentication();
app.UseAuthorization();
}
modules\Identity-core\src\Identity.HttpApi\Controllers\OIDC\OIDCController.cs
Note :- AuthenticationSchemes we can use Controllers or Method level as well
namespace Identity.Controllers.OIDC
{
[Route("api/OIDC")]
[Authorize(AuthenticationSchemes = "OIDC")]
public class OIDCController : AbpController, OIDCAppService
{
}
[Authorize("OIDC")]
public Task CreateAsync(CreateAuthorDto input)
{
}
all IDP end points.
}

