Hi @gterdem
Thankyou for looking into this one and confirming the reproducability. Do you have any additional updates on the status / progress of your investigation and a potential way forward (bug fix / workaround / configuration) for resolving this one in the short term?
We have a release planned in the next 1-2 weeks that was expected to include Azure AD integration for our clients. Depending on the complexity of the issue here and an ETA on a fix, my team may need the time period leading up to the release to figure something else out if Azure AD integration is not possible before the end of the month.
Thankyou again for your help.
<br> Hello
I'm trying to integrate Azure Active Directory as an external login provider for our application which is using the Angular UI. I have followed the instructions in this article (https://community.abp.io/articles/how-to-setup-azure-active-directory-and-integrate-abp-angular-application-lyk87w5l) but I have encountered a number of issues during the setup that I hope you can assist me in resolving.
I have created a fresh copy of the ABP solution to rule out anything specific with our product and I am still able to reproduce the issues in the fresh solution. Either there is a bug or I am misconfiguring something in the app or in Azure AD.
CORS request made for path: /api/abp/application-configuration from origin: http://localhost:4200 but was ignored because path was not for an allowed IdentityServer CORS endpoint error in the provided logs. I have added this origin to the CORS configuration in the database, and it appears to be accessing that origin just fine based on the network logs (see screenshots). I'm not sure whether this is an issue.
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear(); JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Add("sub", ClaimTypes.NameIdentifier);
I am able to log in with a local user if those code blocks are removed, but if I try and log in with the AzureAD user I just get returned to the login page. I've attached logs of whats going on under the REMOVED JwtSecurityTokenHandler CODE BLOCKS log below.I've provided as much information as possible to help with diagnosing this issue. It would be good if you are able to confirm the problems I've described on your end with a fresh solution following the reproducability steps I've detailed above. That would help narrow down whether these issues are related to bugs in the solution or if I am misconfiguring something / the article I've followed is no longer accurate for version 4.3.0 and I need to perform additional configuration.
Thank you
REMOVED JwtSecurityTokenHandler CODE BLOCKS LOG:https://perceptualcomputing-my.sharepoint.com/:t:/g/personal/riley_trevillion_perceptualcomputing_com_au/EUYhYWRsvl1LjrARezYmZW4BN9rBajLXdP5-LPsfRTHLZw?e=Fagkr1
Hi @maliming
I've upgraded our solution to 4.3 and this issue appears to be fixed now. Thankyou for resolving this.
Hi @maliming
I have created a brand new 4.3.0-rc.2 application but, unfortunately, the problem has not been resolved. I am still immediately logged in to the application upon registration without having to verify my email address first.
Have you been able to reproduce the issue on your end using the reproducability steps I have provided?
Many thanks
<br> <br>
Id,ClientId,ClientName,Description,ClientUri,LogoUri,Enabled,ProtocolType,RequireClientSecret,RequireConsent,AllowRememberConsent,AlwaysIncludeUserClaimsInIdToken,RequirePkce,AllowPlainTextPkce,RequireRequestObject,AllowAccessTokensViaBrowser,FrontChannelLogoutUri,FrontChannelLogoutSessionRequired,BackChannelLogoutUri,BackChannelLogoutSessionRequired,AllowOfflineAccess,IdentityTokenLifetime,AllowedIdentityTokenSigningAlgorithms,AccessTokenLifetime,AuthorizationCodeLifetime,ConsentLifetime,AbsoluteRefreshTokenLifetime,SlidingRefreshTokenLifetime,RefreshTokenUsage,UpdateAccessTokenClaimsOnRefresh,RefreshTokenExpiration,AccessTokenType,EnableLocalLogin,IncludeJwtId,AlwaysSendClientClaims,ClientClaimsPrefix,PairWiseSubjectSalt,UserSsoLifetime,UserCodeType,DeviceCodeLifetime,ExtraProperties,ConcurrencyStamp,CreationTime,CreatorId,LastModificationTime,LastModifierId,IsDeleted,DeleterId,DeletionTime
39fb0cd8-5ebd-d891-7227-41d8bdb599c4,Client_Swagger,Client_Swagger,Client_Swagger,,,t,oidc,f,f,t,t,f,f,f,f,,t,,t,t,300,,31536000,300,,31536000,1296000,1,f,1,0,t,f,f,client_,,,,300,{},d17f0620c203454b9a9aec1fffacd6e2,38:01.2,,38:01.2,,f,,
39fb0cd8-5e77-c65d-6d9b-b4a467324d69,Client_App,Client_App,Client_App,,,t,oidc,f,f,t,t,f,f,f,f,,t,,t,t,300,,400,300,,1800,900,1,f,1,0,t,f,f,client_,,,,300,{},2577c8202df3412db530849fa91dc765,38:01.1,,15:01.1,39fb0cd8-5993-8e42-b1a5-e791f73d1e9f,f,,
I've removed some of the repeating successful token refresh lines to fit within forum text limit
[23:27:53 INF] Request starting HTTP/2 OPTIONS [https://localhost:44362/connect/token](https://localhost:44362/connect/token) - -
[23:27:53 INF] CORS policy execution successful.
[23:27:53 INF] Request finished HTTP/2 OPTIONS [https://localhost:44362/connect/token](https://localhost:44362/connect/token) - - - 204 - - 0.2743ms
[23:27:53 INF] Request starting HTTP/2 POST [https://localhost:44362/connect/token](https://localhost:44362/connect/token) application/x-www-form-urlencoded 160
[23:27:53 INF] CORS policy execution successful.
[23:27:53 INF] Successfully validated the token.
[23:27:53 DBG] CORS request made for path: /connect/token from origin: [http://localhost:4200](http://localhost:4200)
[23:27:53 DBG] CorsPolicyService allowed origin: [http://localhost:4200](http://localhost:4200)
[23:27:53 INF] CORS policy execution successful.
[23:27:53 DBG] Request path /connect/token matched to endpoint type Token
[23:27:53 DBG] Endpoint enabled: Token, successfully created handler: IdentityServer4.Endpoints.TokenEndpoint
[23:27:53 INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.TokenEndpoint for /connect/token
[23:27:53 DBG] Start token request.
[23:27:53 DBG] Start client validation
[23:27:53 DBG] Start parsing Basic Authentication secret
[23:27:53 DBG] Start parsing for secret in post body
[23:27:53 DBG] client id without secret found
[23:27:53 DBG] Parser found secret: PostBodySecretParser
[23:27:53 DBG] Secret id found: Client_App
[23:27:53 DBG] client configuration validation for client Client_App succeeded.
[23:27:53 DBG] Public Client - skipping secret validation success
[23:27:53 DBG] Client validation success
[23:27:53 INF] {"ClientId": "Client_App", "AuthenticationMethod": "NoSecret", "Category": "Authentication", "Name": "Client Authentication Success", "EventType": "Success", "Id": 1010, "Message": null, "ActivityId": "80000182-0003-f700-b63f-84710c7967bb", "TimeStamp": "2021-03-31T12:27:53.0000000Z", "ProcessId": 10416, "LocalIpAddress": "127.0.0.1:44362", "RemoteIpAddress": "127.0.0.1", "$type": "ClientAuthenticationSuccessEvent"}
[23:27:53 DBG] Start token request validation
[23:27:53 DBG] Start validation of refresh token request
[23:27:53 DBG] Validation of refresh token request success
[23:27:53 INF] Token request validation success, {"ClientId": "Client_App", "ClientName": "Client_App", "GrantType": "refresh_token", "Scopes": null, "AuthorizationCode": "********", "RefreshToken": "****ED42", "UserName": null, "AuthenticationContextReferenceClasses": null, "Tenant": null, "IdP": null, "Raw": {"grant_type": "refresh_token", "scope": "offline_access Client", "refresh_token": "***REDACTED***", "client_id": "Client_App"}, "$type": "TokenRequestValidationLog"}
[23:27:53 DBG] Updating refresh token
[23:27:53 DBG] Token usage is one-time only. Setting current handle as consumed, and generating new handle
[23:27:53 DBG] Created refresh token in store
[23:27:53 DBG] Getting claims for identity token for subject: 39fb0cd8-5993-8e42-b1a5-e791f73d1e9f and client: Client_App
[23:27:53 INF] {"ClientId": "Client_App", "ClientName": "Client_App", "RedirectUri": null, "Endpoint": "Token", "SubjectId": "39fb0cd8-5993-8e42-b1a5-e791f73d1e9f", "Scopes": "openid Client offline_access", "GrantType": "refresh_token", "Tokens": [{"TokenType": "id_token", "TokenValue": "****4Wmw", "$type": "Token"}, {"TokenType": "refresh_token", "TokenValue": "****62BC", "$type": "Token"}, {"TokenType": "access_token", "TokenValue": "****l3yQ", "$type": "Token"}], "Category": "Token", "Name": "Token Issued Success", "EventType": "Success", "Id": 2000, "Message": null, "ActivityId": "80000182-0003-f700-b63f-84710c7967bb", "TimeStamp": "2021-03-31T12:27:53.0000000Z", "ProcessId": 10416, "LocalIpAddress": "127.0.0.1:44362", "RemoteIpAddress": "127.0.0.1", "$type": "TokenIssuedSuccessEvent"}
[23:27:53 DBG] Token request success.
[23:27:53 INF] Request finished HTTP/2 POST [https://localhost:44362/connect/token](https://localhost:44362/connect/token) application/x-www-form-urlencoded 160 - 200 - application/json;+charset=UTF-8 123.8776ms
[REMOVED MULTIPLE REPEATING TOEKN REFRESH SUCCESS BLOCKS]
[23:53:08 INF] Request starting HTTP/2 OPTIONS [https://localhost:44362/connect/token](https://localhost:44362/connect/token) - -
[23:53:08 INF] CORS policy execution successful.
[23:53:08 INF] Request finished HTTP/2 OPTIONS [https://localhost:44362/connect/token](https://localhost:44362/connect/token) - - - 204 - - 0.3562ms
[23:53:08 INF] Request starting HTTP/2 POST [https://localhost:44362/connect/token](https://localhost:44362/connect/token) application/x-www-form-urlencoded 160
[23:53:08 INF] CORS policy execution successful.
[23:53:08 INF] Successfully validated the token.
[23:53:08 DBG] CORS request made for path: /connect/token from origin: [http://localhost:4200](http://localhost:4200)
[23:53:08 DBG] CorsPolicyService allowed origin: [http://localhost:4200](http://localhost:4200)
[23:53:08 INF] CORS policy execution successful.
[23:53:08 DBG] Request path /connect/token matched to endpoint type Token
[23:53:08 DBG] Endpoint enabled: Token, successfully created handler: IdentityServer4.Endpoints.TokenEndpoint
[23:53:08 INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.TokenEndpoint for /connect/token
[23:53:08 DBG] Start token request.
[23:53:08 DBG] Start client validation
[23:53:08 DBG] Start parsing Basic Authentication secret
[23:53:08 DBG] Start parsing for secret in post body
[23:53:08 DBG] client id without secret found
[23:53:08 DBG] Parser found secret: PostBodySecretParser
[23:53:08 DBG] Secret id found: Client_App
[23:53:08 DBG] client configuration validation for client Client_App succeeded.
[23:53:08 DBG] Public Client - skipping secret validation success
[23:53:08 DBG] Client validation success
[23:53:08 INF] {"ClientId": "Client_App", "AuthenticationMethod": "NoSecret", "Category": "Authentication", "Name": "Client Authentication Success", "EventType": "Success", "Id": 1010, "Message": null, "ActivityId": "800001f6-0004-ea00-b63f-84710c7967bb", "TimeStamp": "2021-03-31T12:53:08.0000000Z", "ProcessId": 10416, "LocalIpAddress": "127.0.0.1:44362", "RemoteIpAddress": "127.0.0.1", "$type": "ClientAuthenticationSuccessEvent"}
[23:53:08 DBG] Start token request validation
[23:53:08 DBG] Start validation of refresh token request
[23:53:08 WRN] Refresh token has expired.
[23:53:08 WRN] Refresh token validation failed. aborting, {"ClientId": "Client_App", "ClientName": "Client_App", "GrantType": "refresh_token", "Scopes": null, "AuthorizationCode": "********", "RefreshToken": "********", "UserName": null, "AuthenticationContextReferenceClasses": null, "Tenant": null, "IdP": null, "Raw": {"grant_type": "refresh_token", "scope": "offline_access Client", "refresh_token": "***REDACTED***", "client_id": "Client_App"}, "$type": "TokenRequestValidationLog"}
[23:53:08 INF] {"ClientId": "Client_App", "ClientName": "Client_App", "RedirectUri": null, "Endpoint": "Token", "SubjectId": null, "Scopes": null, "GrantType": "refresh_token", "Error": "invalid_grant", "ErrorDescription": null, "Category": "Token", "Name": "Token Issued Failure", "EventType": "Failure", "Id": 2001, "Message": null, "ActivityId": "800001f6-0004-ea00-b63f-84710c7967bb", "TimeStamp": "2021-03-31T12:53:08.0000000Z", "ProcessId": 10416, "LocalIpAddress": "127.0.0.1:44362", "RemoteIpAddress": "127.0.0.1", "$type": "TokenIssuedFailureEvent"}
[23:53:08 INF] Request finished HTTP/2 POST [https://localhost:44362/connect/token](https://localhost:44362/connect/token) application/x-www-form-urlencoded 160 - 400 - application/json;+charset=UTF-8 41.7969ms
[23:56:04 INF] Request starting HTTP/2 OPTIONS [https://localhost:44362/.well-known/openid-configuration](https://localhost:44362/.well-known/openid-configuration) - -
[23:56:04 INF] CORS policy execution successful.
[23:56:04 INF] Request finished HTTP/2 OPTIONS [https://localhost:44362/.well-known/openid-configuration](https://localhost:44362/.well-known/openid-configuration) - - - 204 - - 0.9833ms
[23:56:04 INF] Request starting HTTP/2 GET [https://localhost:44362/.well-known/openid-configuration](https://localhost:44362/.well-known/openid-configuration) - -
[23:56:04 INF] CORS policy execution successful.
[23:56:04 INF] Successfully validated the token.
[23:56:04 DBG] CORS request made for path: /.well-known/openid-configuration from origin: [http://localhost:4200](http://localhost:4200)
[23:56:04 DBG] CorsPolicyService allowed origin: [http://localhost:4200](http://localhost:4200)
[23:56:04 INF] CORS policy execution successful.
[23:56:04 DBG] Request path /.well-known/openid-configuration matched to endpoint type Discovery
[23:56:04 DBG] Endpoint enabled: Discovery, successfully created handler: IdentityServer4.Endpoints.DiscoveryEndpoint
[23:56:04 INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.DiscoveryEndpoint for /.well-known/openid-configuration
[23:56:04 DBG] Start discovery request
[23:56:04 INF] Request finished HTTP/2 GET [https://localhost:44362/.well-known/openid-configuration](https://localhost:44362/.well-known/openid-configuration) - - - 200 - application/json;+charset=UTF-8 29.5408ms
[23:56:04 INF] Request starting HTTP/2 OPTIONS [https://localhost:44362/.well-known/openid-configuration/jwks](https://localhost:44362/.well-known/openid-configuration/jwks) - -
[23:56:04 INF] CORS policy execution successful.
[23:56:04 INF] Request finished HTTP/2 OPTIONS [https://localhost:44362/.well-known/openid-configuration/jwks](https://localhost:44362/.well-known/openid-configuration/jwks) - - - 204 - - 0.2289ms
[23:56:04 INF] Request starting HTTP/2 GET [https://localhost:44362/.well-known/openid-configuration/jwks](https://localhost:44362/.well-known/openid-configuration/jwks) - -
[23:56:04 INF] CORS policy execution successful.
[23:56:04 INF] Successfully validated the token.
[23:56:04 DBG] CORS request made for path: /.well-known/openid-configuration/jwks from origin: [http://localhost:4200](http://localhost:4200)
[23:56:04 DBG] CorsPolicyService allowed origin: [http://localhost:4200](http://localhost:4200)
[23:56:04 INF] CORS policy execution successful.
[23:56:04 DBG] Request path /.well-known/openid-configuration/jwks matched to endpoint type Discovery
[23:56:04 DBG] Endpoint enabled: Discovery, successfully created handler: IdentityServer4.Endpoints.DiscoveryKeyEndpoint
[23:56:04 INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.DiscoveryKeyEndpoint for /.well-known/openid-configuration/jwks
[23:56:04 DBG] Start key discovery request
[23:56:04 INF] Request finished HTTP/2 GET [https://localhost:44362/.well-known/openid-configuration/jwks](https://localhost:44362/.well-known/openid-configuration/jwks) - - - 200 - application/json;+charset=UTF-8 10.8135ms
[23:56:04 INF] Request starting HTTP/2 OPTIONS [https://localhost:44362/connect/token](https://localhost:44362/connect/token) - -
[23:56:04 INF] CORS policy execution successful.
[23:56:04 INF] Request finished HTTP/2 OPTIONS [https://localhost:44362/connect/token](https://localhost:44362/connect/token) - - - 204 - - 0.2310ms
[23:56:04 INF] Request starting HTTP/2 POST [https://localhost:44362/connect/token](https://localhost:44362/connect/token) application/x-www-form-urlencoded 160
[23:56:04 INF] CORS policy execution successful.
[23:56:04 INF] Successfully validated the token.
[23:56:04 DBG] CORS request made for path: /connect/token from origin: [http://localhost:4200](http://localhost:4200)
[23:56:04 DBG] CorsPolicyService allowed origin: [http://localhost:4200](http://localhost:4200)
[23:56:04 INF] CORS policy execution successful.
[23:56:04 DBG] Request path /connect/token matched to endpoint type Token
[23:56:04 DBG] Endpoint enabled: Token, successfully created handler: IdentityServer4.Endpoints.TokenEndpoint
[23:56:04 INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.TokenEndpoint for /connect/token
[23:56:04 DBG] Start token request.
[23:56:04 DBG] Start client validation
[23:56:04 DBG] Start parsing Basic Authentication secret
[23:56:04 DBG] Start parsing for secret in post body
[23:56:04 DBG] client id without secret found
[23:56:04 DBG] Parser found secret: PostBodySecretParser
[23:56:04 DBG] Secret id found: Client_App
[23:56:04 DBG] client configuration validation for client Client_App succeeded.
[23:56:04 DBG] Public Client - skipping secret validation success
[23:56:04 DBG] Client validation success
[23:56:04 INF] {"ClientId": "Client_App", "AuthenticationMethod": "NoSecret", "Category": "Authentication", "Name": "Client Authentication Success", "EventType": "Success", "Id": 1010, "Message": null, "ActivityId": "8000053f-0005-e500-b63f-84710c7967bb", "TimeStamp": "2021-03-31T12:56:04.0000000Z", "ProcessId": 10416, "LocalIpAddress": "127.0.0.1:44362", "RemoteIpAddress": "127.0.0.1", "$type": "ClientAuthenticationSuccessEvent"}
[23:56:04 DBG] Start token request validation
[23:56:04 DBG] Start validation of refresh token request
[23:56:04 WRN] Refresh token has expired.
[23:56:04 WRN] Refresh token validation failed. aborting, {"ClientId": "Client_App", "ClientName": "Client_App", "GrantType": "refresh_token", "Scopes": null, "AuthorizationCode": "********", "RefreshToken": "********", "UserName": null, "AuthenticationContextReferenceClasses": null, "Tenant": null, "IdP": null, "Raw": {"grant_type": "refresh_token", "scope": "offline_access Client", "refresh_token": "***REDACTED***", "client_id": "Client_App"}, "$type": "TokenRequestValidationLog"}
[23:56:04 INF] {"ClientId": "Client_App", "ClientName": "Client_App", "RedirectUri": null, "Endpoint": "Token", "SubjectId": null, "Scopes": null, "GrantType": "refresh_token", "Error": "invalid_grant", "ErrorDescription": null, "Category": "Token", "Name": "Token Issued Failure", "EventType": "Failure", "Id": 2001, "Message": null, "ActivityId": "8000053f-0005-e500-b63f-84710c7967bb", "TimeStamp": "2021-03-31T12:56:04.0000000Z", "ProcessId": 10416, "LocalIpAddress": "127.0.0.1:44362", "RemoteIpAddress": "127.0.0.1", "$type": "TokenIssuedFailureEvent"}
[23:56:04 INF] Request finished HTTP/2 POST [https://localhost:44362/connect/token](https://localhost:44362/connect/token) application/x-www-form-urlencoded 160 - 400 - application/json;+charset=UTF-8 31.2436ms
Hello
I've been looking for a way to expire a users login session after X period of time has passed which automatically redirects them to the Identity Server login page.
As a starting point for this task, I have followed the advice provided on https://support.abp.io/QA/Questions/957/Force-users-to-re-login-if-they-are-inactive-in-30-minutes and set, in the IdentityServerClients DB table, the
As expected, the access_tokenis renewed using the refresh_token at the correct time and continues to do so up until the 30 min mark when the refresh_token expires. This is all fine and works as expected.
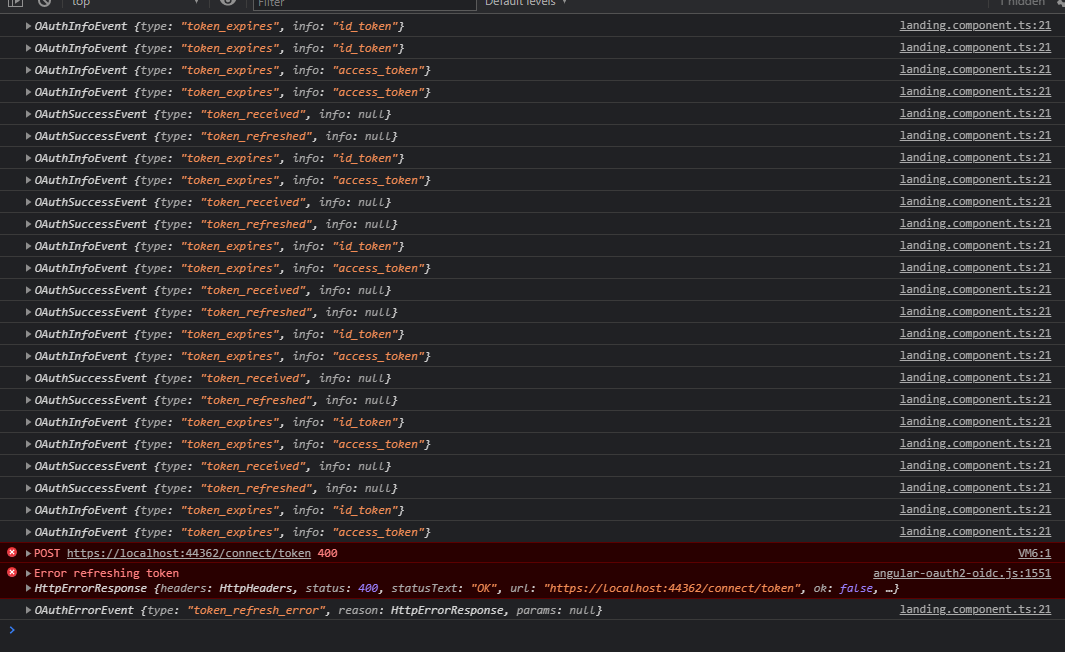
Where I'm having trouble is when the refresh_token expires, instead of the ABP / Angular client redirecting to the Identity Server login screen for re-authentication, the application becomes stuck when refreshing the browser page and is unusable until the user clears all their cookies / cache. A 400 error is given which makes me think the application is trying to use the expired refresh_token to get more access_tokens after the 30 minute mark.
<br>
log.js:24 [HMR] Waiting for update signal from WDS...
ngxs-store.js:1965 RECOMMENDATION: Set developmentMode to true on the NgxsModule when Angular is running in development mode.
angular-oauth2-oidc.js:1551 Error refreshing token HttpErrorResponse {headers: HttpHeaders, status: 400, statusText: "OK", url: "https://localhost:44362/connect/token", ok: false, …}
core.js:5980 ERROR HttpErrorResponse {headers: HttpHeaders, status: 400, statusText: "OK", url: "https://localhost:44362/connect/token", ok: false, …}
main.ts:14 HttpErrorResponse {headers: HttpHeaders, status: 400, statusText: "OK", url: "https://localhost:44362/connect/token", ok: false, …}
(anonymous) @ main.ts:14
invoke @ zone-evergreen.js:364
run @ zone-evergreen.js:123
(anonymous) @ zone-evergreen.js:857
invokeTask @ zone-evergreen.js:399
runTask @ zone-evergreen.js:167
drainMicroTaskQueue @ zone-evergreen.js:569
invokeTask @ zone-evergreen.js:484
invokeTask @ zone-evergreen.js:1621
globalZoneAwareCallback @ zone-evergreen.js:1658
load (async)
customScheduleGlobal @ zone-evergreen.js:1773
scheduleTask @ zone-evergreen.js:385
onScheduleTask @ zone-evergreen.js:272
scheduleTask @ zone-evergreen.js:378
scheduleTask @ zone-evergreen.js:210
scheduleEventTask @ zone-evergreen.js:236
(anonymous) @ zone-evergreen.js:1928
(anonymous) @ http.js:1773
_trySubscribe @ Observable.js:42
subscribe @ Observable.js:28
call @ finalize.js:11
subscribe @ Observable.js:23
innerSubscribe @ innerSubscribe.js:67
_innerSub @ mergeMap.js:57
_tryNext @ mergeMap.js:51
_next @ mergeMap.js:34
next @ Subscriber.js:49
(anonymous) @ subscribeToArray.js:3
_trySubscribe @ Observable.js:42
subscribe @ Observable.js:28
call @ mergeMap.js:19
subscribe @ Observable.js:23
call @ filter.js:13
subscribe @ Observable.js:23
call @ map.js:16
subscribe @ Observable.js:23
call @ switchMap.js:15
subscribe @ Observable.js:23
(anonymous) @ angular-oauth2-oidc.js:1543
ZoneAwarePromise @ zone-evergreen.js:960
refreshToken @ angular-oauth2-oidc.js:1512
(anonymous) @ abp-ng.core.js:2411
invoke @ zone-evergreen.js:364
onInvoke @ core.js:28301
invoke @ zone-evergreen.js:363
run @ zone-evergreen.js:123
(anonymous) @ zone-evergreen.js:857
invokeTask @ zone-evergreen.js:399
onInvokeTask @ core.js:28289
invokeTask @ zone-evergreen.js:398
runTask @ zone-evergreen.js:167
drainMicroTaskQueue @ zone-evergreen.js:569
invokeTask @ zone-evergreen.js:484
invokeTask @ zone-evergreen.js:1621
globalZoneAwareCallback @ zone-evergreen.js:1658
load (async)
customScheduleGlobal @ zone-evergreen.js:1773
scheduleTask @ zone-evergreen.js:385
onScheduleTask @ zone-evergreen.js:272
scheduleTask @ zone-evergreen.js:378
scheduleTask @ zone-evergreen.js:210
scheduleEventTask @ zone-evergreen.js:236
(anonymous) @ zone-evergreen.js:1928
(anonymous) @ http.js:1773
_trySubscribe @ Observable.js:42
subscribe @ Observable.js:28
call @ finalize.js:11
subscribe @ Observable.js:23
innerSubscribe @ innerSubscribe.js:67
_innerSub @ mergeMap.js:57
_tryNext @ mergeMap.js:51
_next @ mergeMap.js:34
next @ Subscriber.js:49
(anonymous) @ subscribeToArray.js:3
_trySubscribe @ Observable.js:42
subscribe @ Observable.js:28
call @ mergeMap.js:19
subscribe @ Observable.js:23
call @ filter.js:13
subscribe @ Observable.js:23
call @ map.js:16
subscribe @ Observable.js:23
(anonymous) @ angular-oauth2-oidc.js:1339
ZoneAwarePromise @ zone-evergreen.js:960
loadJwks @ angular-oauth2-oidc.js:1337
(anonymous) @ angular-oauth2-oidc.js:1313
__tryOrUnsub @ Subscriber.js:183
next @ Subscriber.js:122
_next @ Subscriber.js:72
next @ Subscriber.js:49
_next @ map.js:35
next @ Subscriber.js:49
_next @ filter.js:33
next @ Subscriber.js:49
notifyNext @ mergeMap.js:70
_next @ innerSubscribe.js:10
next @ Subscriber.js:49
_next @ Subscriber.js:72
next @ Subscriber.js:49
onLoad @ http.js:1687
invokeTask @ zone-evergreen.js:399
onInvokeTask @ core.js:28289
invokeTask @ zone-evergreen.js:398
runTask @ zone-evergreen.js:167
invokeTask @ zone-evergreen.js:480
invokeTask @ zone-evergreen.js:1621
globalZoneAwareCallback @ zone-evergreen.js:1658
load (async)
customScheduleGlobal @ zone-evergreen.js:1773
scheduleTask @ zone-evergreen.js:385
onScheduleTask @ zone-evergreen.js:272
scheduleTask @ zone-evergreen.js:378
scheduleTask @ zone-evergreen.js:210
scheduleEventTask @ zone-evergreen.js:236
(anonymous) @ zone-evergreen.js:1928
(anonymous) @ http.js:1773
_trySubscribe @ Observable.js:42
subscribe @ Observable.js:28
call @ finalize.js:11
subscribe @ Observable.js:23
innerSubscribe @ innerSubscribe.js:67
_innerSub @ mergeMap.js:57
_tryNext @ mergeMap.js:51
_next @ mergeMap.js:34
next @ Subscriber.js:49
(anonymous) @ subscribeToArray.js:3
_trySubscribe @ Observable.js:42
subscribe @ Observable.js:28
call @ mergeMap.js:19
subscribe @ Observable.js:23
call @ filter.js:13
subscribe @ Observable.js:23
call @ map.js:16
subscribe @ Observable.js:23
(anonymous) @ angular-oauth2-oidc.js:1291
ZoneAwarePromise @ zone-evergreen.js:960
loadDiscoveryDocument @ angular-oauth2-oidc.js:1279
(anonymous) @ abp-ng.core.js:2391
(anonymous) @ tslib.es6.js:76
ZoneAwarePromise @ zone-evergreen.js:960
__awaiter @ tslib.es6.js:72
init @ abp-ng.core.js:2386
(anonymous) @ abp-ng.core.js:2405
(anonymous) @ tslib.es6.js:76
ZoneAwarePromise @ zone-evergreen.js:960
__awaiter @ tslib.es6.js:72
init @ abp-ng.core.js:2404
(anonymous) @ abp-ng.core.js:2492
(anonymous) @ tslib.es6.js:76
ZoneAwarePromise @ zone-evergreen.js:960
__awaiter @ tslib.es6.js:72
init @ abp-ng.core.js:2491
(anonymous) @ abp-ng.core.js:2654
fulfilled @ tslib.es6.js:73
invoke @ zone-evergreen.js:364
onInvoke @ core.js:28301
invoke @ zone-evergreen.js:363
run @ zone-evergreen.js:123
(anonymous) @ zone-evergreen.js:857
invokeTask @ zone-evergreen.js:399
onInvokeTask @ core.js:28289
invokeTask @ zone-evergreen.js:398
runTask @ zone-evergreen.js:167
drainMicroTaskQueue @ zone-evergreen.js:569
invokeTask @ zone-evergreen.js:484
invokeTask @ zone-evergreen.js:1621
globalZoneAwareCallback @ zone-evergreen.js:1658
load (async)
customScheduleGlobal @ zone-evergreen.js:1773
scheduleTask @ zone-evergreen.js:385
onScheduleTask @ zone-evergreen.js:272
scheduleTask @ zone-evergreen.js:378
scheduleTask @ zone-evergreen.js:210
scheduleEventTask @ zone-evergreen.js:236
(anonymous) @ zone-evergreen.js:1928
(anonymous) @ http.js:1773
_trySubscribe @ Observable.js:42
subscribe @ Observable.js:28
call @ finalize.js:11
subscribe @ Observable.js:23
innerSubscribe @ innerSubscribe.js:67
_innerSub @ mergeMap.js:57
_tryNext @ mergeMap.js:51
_next @ mergeMap.js:34
next @ Subscriber.js:49
(anonymous) @ subscribeToArray.js:3
_trySubscribe @ Observable.js:42
subscribe @ Observable.js:28
call @ mergeMap.js:19
subscribe @ Observable.js:23
call @ filter.js:13
subscribe @ Observable.js:23
call @ map.js:16
subscribe @ Observable.js:23
call @ catchError.js:14
subscribe @ Observable.js:23
call @ tap.js:16
subscribe @ Observable.js:23
(anonymous) @ Observable.js:91
ZoneAwarePromise @ zone-evergreen.js:960
toPromise @ Observable.js:89
getRemoteEnv @ abp-ng.core.js:2521
(anonymous) @ abp-ng.core.js:2652
(anonymous) @ tslib.es6.js:76
ZoneAwarePromise @ zone-evergreen.js:960
__awaiter @ tslib.es6.js:72
fn @ abp-ng.core.js:2646
runInitializers @ core.js:27596
(anonymous) @ core.js:28911
_callAndReportToErrorHandler @ core.js:29012
(anonymous) @ core.js:28909
invoke @ zone-evergreen.js:364
onInvoke @ core.js:28301
invoke @ zone-evergreen.js:363
run @ zone-evergreen.js:123
run @ core.js:28184
bootstrapModuleFactory @ core.js:28891
(anonymous) @ core.js:28943
invoke @ zone-evergreen.js:364
run @ zone-evergreen.js:123
(anonymous) @ zone-evergreen.js:857
invokeTask @ zone-evergreen.js:399
runTask @ zone-evergreen.js:167
drainMicroTaskQueue @ zone-evergreen.js:569
Promise.then (async)
scheduleMicroTask @ zone-evergreen.js:552
scheduleTask @ zone-evergreen.js:388
scheduleTask @ zone-evergreen.js:210
scheduleMicroTask @ zone-evergreen.js:230
scheduleResolveOrReject @ zone-evergreen.js:847
then @ zone-evergreen.js:979
bootstrapModule @ core.js:28943
(anonymous) @ main.ts:13
zUnb @ main.ts:14
__webpack_require__ @ bootstrap:853
fn @ bootstrap:150
9 @ main.js:2507
__webpack_require__ @ bootstrap:853
checkDeferredModules @ bootstrap:45
webpackJsonpCallback @ bootstrap:32
(anonymous) @ main.js:1
Show 191 more frames
<br>
I have tried to handle this error in my top level component and redirect the user to the login page manually by subscribing to the OAuthService events Observable, but the 400 error seems to be happening much earlier in the application startup process so it never reaches my handling code. It seems to be happening in the @abp/ng.core module (in this file I think - https://github.com/abpframework/abp/blob/b183a24cfe56ad8263aaefcf4939b9cd0c18b1c7/npm/ng-packs/packages/core/src/lib/strategies/auth-flow.strategy.ts#L23).
Are you able to confirm if this is a bug? If it is not a bug or is intended behaviour, do you know how I can correctly handle this 400 error before the @abp/ng.core module attempts to get a new access_token with an expired refresh_token (if that is indeed the issue)?
Thankyou
Hi @maliming
I have switched over to the 4.3-preview branch using ABP Suite and the issue I have described above is still happening. Are you able to confirm the issue on your end using the reproducability steps I've provided above?
Thankyou
Hi maliming
Thankyou for your reply.
The upcoming enhancements sound great. I will wait for 4.3 to be released to verify whether the issue I've described above has been resolved or not. I think the 4.3-preview is coming out in the next couple of days according to the milestones you have defined in Github.
Thanks again
Log extract part 2 <br>
[17:57:05 INF] {"ClientId": "EmailConfirmationVerify_App", "AuthenticationMethod": "NoSecret", "Category": "Authentication", "Name": "Client Authentication Success", "EventType": "Success", "Id": 1010, "Message": null, "ActivityId": "80000038-0005-eb00-b63f-84710c7967bb", "TimeStamp": "2021-03-30T06:57:05.0000000Z", "ProcessId": 15492, "LocalIpAddress": "127.0.0.1:44362", "RemoteIpAddress": "127.0.0.1", "$type": "ClientAuthenticationSuccessEvent"}
[17:57:05 DBG] Start token request validation
[17:57:05 DBG] Start validation of authorization code token request
[17:57:05 DBG] Client required a proof key for code exchange. Starting PKCE validation
[17:57:05 DBG] Validation of authorization code token request success
[17:57:05 INF] Token request validation success, {"ClientId": "EmailConfirmationVerify_App", "ClientName": "EmailConfirmationVerify_App", "GrantType": "authorization_code", "Scopes": null, "AuthorizationCode": "****787D", "RefreshToken": "********", "UserName": null, "AuthenticationContextReferenceClasses": null, "Tenant": null, "IdP": null, "Raw": {"grant_type": "authorization_code", "code": "E6FEB6A7F36746AE123310B92BD9E63D398A406E3BAC7F69B80715B28CC5787D", "redirect_uri": "http://localhost:4200", "code_verifier": "MUswUERQazhBUS5hUDB2VWhtVTJDYVUtdTBTMUhYZWJEYzVycmhmWmk2a0hG", "client_id": "EmailConfirmationVerify_App"}, "$type": "TokenRequestValidationLog"}
[17:57:05 DBG] client configuration validation for client EmailConfirmationVerify_App succeeded.
[17:57:05 DBG] Getting claims for access token for client: EmailConfirmationVerify_App
[17:57:05 DBG] Getting claims for access token for subject: 39fb9418-c0c9-105d-2469-f451a67e059c
[17:57:05 DBG] Creating refresh token
[17:57:05 DBG] Setting an absolute lifetime: 31536000
[17:57:05 DBG] client configuration validation for client EmailConfirmationVerify_App succeeded.
[17:57:05 DBG] Getting claims for identity token for subject: 39fb9418-c0c9-105d-2469-f451a67e059c and client: EmailConfirmationVerify_App
[17:57:05 INF] {"ClientId": "EmailConfirmationVerify_App", "ClientName": "EmailConfirmationVerify_App", "RedirectUri": null, "Endpoint": "Token", "SubjectId": "39fb9418-c0c9-105d-2469-f451a67e059c", "Scopes": "offline_access openid profile role email phone EmailConfirmationVerify", "GrantType": "authorization_code", "Tokens": [{"TokenType": "id_token", "TokenValue": "****37Jw", "$type": "Token"}, {"TokenType": "refresh_token", "TokenValue": "****F8C5", "$type": "Token"}, {"TokenType": "access_token", "TokenValue": "****FQsg", "$type": "Token"}], "Category": "Token", "Name": "Token Issued Success", "EventType": "Success", "Id": 2000, "Message": null, "ActivityId": "80000038-0005-eb00-b63f-84710c7967bb", "TimeStamp": "2021-03-30T06:57:05.0000000Z", "ProcessId": 15492, "LocalIpAddress": "127.0.0.1:44362", "RemoteIpAddress": "127.0.0.1", "$type": "TokenIssuedSuccessEvent"}
[17:57:05 DBG] Token request success.
[17:57:05 INF] Request finished HTTP/2 POST https://localhost:44362/connect/token application/x-www-form-urlencoded 247 - 200 - application/json;+charset=UTF-8 108.0022ms
[17:57:05 INF] Request starting HTTP/2 OPTIONS https://localhost:44362/api/abp/application-configuration - -
[17:57:05 INF] CORS policy execution successful.
[17:57:05 INF] Request finished HTTP/2 OPTIONS https://localhost:44362/api/abp/application-configuration - - - 204 - - 0.1693ms
[17:57:05 INF] Request starting HTTP/2 GET https://localhost:44362/api/abp/application-configuration - -
[17:57:05 INF] CORS policy execution successful.
[17:57:05 INF] Successfully validated the token.
[17:57:05 DBG] CORS request made for path: /api/abp/application-configuration from origin: http://localhost:4200 but was ignored because path was not for an allowed IdentityServer CORS endpoint
[17:57:05 INF] No CORS policy found for the specified request.
[17:57:05 INF] Executing endpoint 'Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController.GetAsync (Volo.Abp.AspNetCore.Mvc)'
[17:57:05 INF] Route matched with {area = "abp", action = "Get", controller = "AbpApplicationConfiguration", page = ""}. Executing controller action with signature System.Threading.Tasks.Task`1[Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ApplicationConfigurationDto] GetAsync() on controller Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController (Volo.Abp.AspNetCore.Mvc).
[17:57:05 DBG] Executing AbpApplicationConfigurationAppService.GetAsync()...
[17:57:05 DBG] Getting not cache granted permissions from the repository for this provider name,key: U,39fb9418-c0c9-105d-2469-f451a67e059c
[17:57:05 DBG] Setting the cache items. Count: 63
[17:57:05 DBG] Finished setting the cache items. Count: 63
[17:57:05 DBG] Getting not cache granted permissions from the repository for this provider name,key: R,user
[17:57:05 DBG] Setting the cache items. Count: 63
[17:57:05 DBG] Finished setting the cache items. Count: 63
[17:57:05 DBG] Executed AbpApplicationConfigurationAppService.GetAsync().
[17:57:05 INF] Executing ObjectResult, writing value of type 'Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ApplicationConfigurationDto'.
[17:57:05 INF] Executed action Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController.GetAsync (Volo.Abp.AspNetCore.Mvc) in 98.628ms
[17:57:05 INF] Executed endpoint 'Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController.GetAsync (Volo.Abp.AspNetCore.Mvc)'
[17:57:05 INF] Request finished HTTP/2 GET https://localhost:44362/api/abp/application-configuration - - - 200 - application/json;+charset=utf-8 112.3838ms
[17:57:05 INF] Request starting HTTP/2 OPTIONS https://localhost:44362/api/account/profile-picture/39fb9418-c0c9-105d-2469-f451a67e059c - -
[17:57:05 INF] CORS policy execution successful.
[17:57:05 INF] Request finished HTTP/2 OPTIONS https://localhost:44362/api/account/profile-picture/39fb9418-c0c9-105d-2469-f451a67e059c - - - 204 - - 0.5028ms
[17:57:05 INF] Request starting HTTP/2 GET https://localhost:44362/api/account/profile-picture/39fb9418-c0c9-105d-2469-f451a67e059c - -
[17:57:05 INF] CORS policy execution successful.
[17:57:05 INF] Successfully validated the token.
[17:57:05 DBG] CORS request made for path: /api/account/profile-picture/39fb9418-c0c9-105d-2469-f451a67e059c from origin: http://localhost:4200 but was ignored because path was not for an allowed IdentityServer CORS endpoint
[17:57:05 INF] No CORS policy found for the specified request.
[17:57:05 INF] Executing endpoint 'Volo.Abp.Account.AccountController.GetProfilePictureAsync (Volo.Abp.Account.Pro.Public.HttpApi)'
[17:57:05 INF] Route matched with {area = "account", action = "GetProfilePicture", controller = "Account", page = ""}. Executing controller action with signature System.Threading.Tasks.Task`1[Volo.Abp.Account.ProfilePictureSourceDto] GetProfilePictureAsync(System.Guid) on controller Volo.Abp.Account.AccountController (Volo.Abp.Account.Pro.Public.HttpApi).
[17:57:05 INF] Executing ObjectResult, writing value of type 'Volo.Abp.Account.ProfilePictureSourceDto'.
[17:57:05 INF] Executed action Volo.Abp.Account.AccountController.GetProfilePictureAsync (Volo.Abp.Account.Pro.Public.HttpApi) in 14.7263ms
[17:57:05 INF] Executed endpoint 'Volo.Abp.Account.AccountController.GetProfilePictureAsync (Volo.Abp.Account.Pro.Public.HttpApi)'
[17:57:05 INF] Request finished HTTP/2 GET https://localhost:44362/api/account/profile-picture/39fb9418-c0c9-105d-2469-f451a67e059c - - - 200 - application/json;+charset=utf-8 25.2785ms

