Log extract part 1 (split due to forum text limit) <br>
[17:57:04 INF] Request starting HTTP/2 POST https://localhost:44362/Account/Register?returnUrl=%2Fconnect%2Fauthorize%2Fcallback%3Fresponse_type%3Dcode%26client_id%3DEmailConfirmationVerify_App%26state%3DLWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs%26redirect_uri%3Dhttp%253A%252F%252Flocalhost%253A4200%26scope%3Doffline_access%2520openid%2520profile%2520role%2520email%2520phone%2520EmailConfirmationVerify%26code_challenge%3DcQ4FhogKNMUbr6EIkVpCDsG-db_LISzwN8TPrhdWWp8%26code_challenge_method%3DS256%26nonce%3DLWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs application/x-www-form-urlencoded 278
[17:57:04 INF] CORS policy execution failed.
[17:57:04 INF] Request origin https://localhost:44362 does not have permission to access the resource.
[17:57:04 INF] No CORS policy found for the specified request.
[17:57:04 INF] Executing endpoint '/Account/Register'
[17:57:04 INF] Route matched with {page = "/Account/Register", action = "", controller = "", area = ""}. Executing page /Account/Register
[17:57:04 INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy
[17:57:04 INF] Executing handler method Volo.Abp.Account.Public.Web.Pages.Account.RegisterModel.OnPostAsync - ModelState is Valid
[17:57:04 DBG] Added 0 entity changes to the current audit log
[17:57:04 DBG] Added 0 entity changes to the current audit log
[17:57:04 DBG] Added 0 entity changes to the current audit log
[17:57:04 DBG] Added 0 entity changes to the current audit log
[17:57:04 WRN] USING NullEmailSender!
[17:57:04 DBG] SendEmailAsync:
[17:57:04 DBG] test.user@fakedomain.com
[17:57:04 DBG]
[17:57:04 DBG] Email confirmation
[17:57:04 DBG] <!DOCTYPE html>
<html lang="en" xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta charset="utf-8" />
</head>
<body>
<h3>Email confirmation</h3>
<p>Please confirm your email address by clicking the following link.</p>
<div>
<a href="https://localhost:44362/Account/EmailConfirmation?userId=39fb9418-c0c9-105d-2469-f451a67e059c&tenantId=&confirmationToken=CfDJ8EsHVoI09O9NqclZwYBgchfwhFgPHiKsv2nj17jXpv7vh3DthB5QHOvX5iim0tJ2q%2BXiHpfS9DAj%2BPNn4KYkIyQqe6Ky1gvPndCYob7rFZ9WS%2BuLOKgSLCUSIf3MOBORWNAI5X%2Bo1cv6nLCN4Oo3seFtoYEAAZUd8mAVfAv0oIzTeHAjTkT%2BWORmsSy2HuclR70ALN8Bs8rvENhedD3sth8lgfDya4OIzH6v1y1J563ia665fkOX0uqh%2BHqdnH25%2FQ%3D%3D&returnUrl=http://localhost:4200">Confirm my email address</a>
</div>
</body>
</html>
[17:57:04 DBG] Augmenting SignInContext
[17:57:04 DBG] Adding idp claim with value: local
[17:57:04 DBG] Adding amr claim with value: pwd
[17:57:04 DBG] Adding auth_time claim with value: 1617087424
[17:57:04 INF] AuthenticationScheme: Identity.Application signed in.
[17:57:04 INF] Executed handler method OnPostAsync, returned result Microsoft.AspNetCore.Mvc.RedirectResult.
[17:57:04 INF] Executing RedirectResult, redirecting to /connect/authorize/callback?response_type=code&client_id=EmailConfirmationVerify_App&state=LWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs&redirect_uri=http%3A%2F%2Flocalhost%3A4200&scope=offline_access%20openid%20profile%20role%20email%20phone%20EmailConfirmationVerify&code_challenge=cQ4FhogKNMUbr6EIkVpCDsG-db_LISzwN8TPrhdWWp8&code_challenge_method=S256&nonce=LWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs.
[17:57:04 INF] Executed page /Account/Register in 79.2189ms
[17:57:04 INF] Executed endpoint '/Account/Register'
[17:57:04 DBG] Added 0 entity changes to the current audit log
[17:57:04 DBG] Added 0 entity changes to the current audit log
[17:57:04 INF] Request finished HTTP/2 POST https://localhost:44362/Account/Register?returnUrl=%2Fconnect%2Fauthorize%2Fcallback%3Fresponse_type%3Dcode%26client_id%3DEmailConfirmationVerify_App%26state%3DLWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs%26redirect_uri%3Dhttp%253A%252F%252Flocalhost%253A4200%26scope%3Doffline_access%2520openid%2520profile%2520role%2520email%2520phone%2520EmailConfirmationVerify%26code_challenge%3DcQ4FhogKNMUbr6EIkVpCDsG-db_LISzwN8TPrhdWWp8%26code_challenge_method%3DS256%26nonce%3DLWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs application/x-www-form-urlencoded 278 - 302 - - 95.2128ms
[17:57:04 INF] Request starting HTTP/2 GET https://localhost:44362/connect/authorize/callback?response_type=code&client_id=EmailConfirmationVerify_App&state=LWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs&redirect_uri=http%3A%2F%2Flocalhost%3A4200&scope=offline_access%20openid%20profile%20role%20email%20phone%20EmailConfirmationVerify&code_challenge=cQ4FhogKNMUbr6EIkVpCDsG-db_LISzwN8TPrhdWWp8&code_challenge_method=S256&nonce=LWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs - -
[17:57:04 DBG] Request path /connect/authorize/callback matched to endpoint type Authorize
[17:57:04 DBG] Endpoint enabled: Authorize, successfully created handler: IdentityServer4.Endpoints.AuthorizeCallbackEndpoint
[17:57:04 INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.AuthorizeCallbackEndpoint for /connect/authorize/callback
[17:57:04 DBG] Start authorize callback request
[17:57:04 DBG] User in authorize request: 39fb9418-c0c9-105d-2469-f451a67e059c
[17:57:04 DBG] Start authorize request protocol validation
[17:57:04 DBG] client configuration validation for client EmailConfirmationVerify_App succeeded.
[17:57:04 DBG] Checking for PKCE parameters
[17:57:04 DBG] Calling into custom validator: IdentityServer4.Validation.DefaultCustomAuthorizeRequestValidator
[17:57:04 DBG] ValidatedAuthorizeRequest
{"ClientId": "EmailConfirmationVerify_App", "ClientName": "EmailConfirmationVerify_App", "RedirectUri": "http://localhost:4200", "AllowedRedirectUris": ["http://localhost:4200"], "SubjectId": "39fb9418-c0c9-105d-2469-f451a67e059c", "ResponseType": "code", "ResponseMode": "query", "GrantType": "authorization_code", "RequestedScopes": "offline_access openid profile role email phone EmailConfirmationVerify", "State": "LWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs", "UiLocales": null, "Nonce": "LWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs", "AuthenticationContextReferenceClasses": null, "DisplayMode": null, "PromptMode": "", "MaxAge": null, "LoginHint": null, "SessionId": "60EB95D1AF5D4756950AB452A81480BF", "Raw": {"response_type": "code", "client_id": "EmailConfirmationVerify_App", "state": "LWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs", "redirect_uri": "http://localhost:4200", "scope": "offline_access openid profile role email phone EmailConfirmationVerify", "code_challenge": "cQ4FhogKNMUbr6EIkVpCDsG-db_LISzwN8TPrhdWWp8", "code_challenge_method": "S256", "nonce": "LWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs"}, "$type": "AuthorizeRequestValidationLog"}
[17:57:04 DBG] Client is configured to not require consent, no consent is required
[17:57:04 DBG] Creating Authorization Code Flow response.
[17:57:04 INF] {"ClientId": "EmailConfirmationVerify_App", "ClientName": "EmailConfirmationVerify_App", "RedirectUri": "http://localhost:4200", "Endpoint": "Authorize", "SubjectId": "39fb9418-c0c9-105d-2469-f451a67e059c", "Scopes": "offline_access openid profile role email phone EmailConfirmationVerify", "GrantType": "authorization_code", "Tokens": [{"TokenType": "code", "TokenValue": "****787D", "$type": "Token"}], "Category": "Token", "Name": "Token Issued Success", "EventType": "Success", "Id": 2000, "Message": null, "ActivityId": "80000089-0001-d900-b63f-84710c7967bb", "TimeStamp": "2021-03-30T06:57:04.0000000Z", "ProcessId": 15492, "LocalIpAddress": "127.0.0.1:44362", "RemoteIpAddress": "127.0.0.1", "$type": "TokenIssuedSuccessEvent"}
[17:57:04 DBG] Authorize endpoint response
{"SubjectId": "39fb9418-c0c9-105d-2469-f451a67e059c", "ClientId": "EmailConfirmationVerify_App", "RedirectUri": "http://localhost:4200", "State": "LWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs", "Scope": "offline_access openid profile role email phone EmailConfirmationVerify", "Error": null, "ErrorDescription": null, "$type": "AuthorizeResponseLog"}
[17:57:04 DBG] Augmenting SignInContext
[17:57:04 INF] AuthenticationScheme: Identity.Application signed in.
[17:57:04 INF] Request finished HTTP/2 GET https://localhost:44362/connect/authorize/callback?response_type=code&client_id=EmailConfirmationVerify_App&state=LWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs&redirect_uri=http%3A%2F%2Flocalhost%3A4200&scope=offline_access%20openid%20profile%20role%20email%20phone%20EmailConfirmationVerify&code_challenge=cQ4FhogKNMUbr6EIkVpCDsG-db_LISzwN8TPrhdWWp8&code_challenge_method=S256&nonce=LWlUVlBrY3BFMU9PZ3BGbnNaVEY3bGJwcGRIVy5qcmVPcEdIWHB4REozUVRs - - - 302 - - 41.7471ms
[17:57:05 INF] Request starting HTTP/2 GET https://localhost:44362/.well-known/openid-configuration - -
[17:57:05 INF] CORS policy execution successful.
[17:57:05 DBG] CORS request made for path: /.well-known/openid-configuration from origin: http://localhost:4200
[17:57:05 DBG] CorsPolicyService allowed origin: http://localhost:4200
[17:57:05 INF] CORS policy execution successful.
[17:57:05 DBG] Request path /.well-known/openid-configuration matched to endpoint type Discovery
[17:57:05 DBG] Endpoint enabled: Discovery, successfully created handler: IdentityServer4.Endpoints.DiscoveryEndpoint
[17:57:05 INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.DiscoveryEndpoint for /.well-known/openid-configuration
[17:57:05 DBG] Start discovery request
[17:57:05 INF] Request finished HTTP/2 GET https://localhost:44362/.well-known/openid-configuration - - - 200 - application/json;+charset=UTF-8 25.6047ms
[17:57:05 INF] Request starting HTTP/2 GET https://localhost:44362/.well-known/openid-configuration/jwks - -
[17:57:05 INF] CORS policy execution successful.
[17:57:05 DBG] CORS request made for path: /.well-known/openid-configuration/jwks from origin: http://localhost:4200
[17:57:05 DBG] CorsPolicyService allowed origin: http://localhost:4200
[17:57:05 INF] CORS policy execution successful.
[17:57:05 DBG] Request path /.well-known/openid-configuration/jwks matched to endpoint type Discovery
[17:57:05 DBG] Endpoint enabled: Discovery, successfully created handler: IdentityServer4.Endpoints.DiscoveryKeyEndpoint
[17:57:05 INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.DiscoveryKeyEndpoint for /.well-known/openid-configuration/jwks
[17:57:05 DBG] Start key discovery request
[17:57:05 INF] Request finished HTTP/2 GET https://localhost:44362/.well-known/openid-configuration/jwks - - - 200 - application/json;+charset=UTF-8 17.5562ms
[17:57:05 INF] Request starting HTTP/2 POST https://localhost:44362/connect/token application/x-www-form-urlencoded 247
[17:57:05 INF] CORS policy execution successful.
[17:57:05 DBG] CORS request made for path: /connect/token from origin: http://localhost:4200
[17:57:05 DBG] CorsPolicyService allowed origin: http://localhost:4200
[17:57:05 INF] CORS policy execution successful.
[17:57:05 DBG] Request path /connect/token matched to endpoint type Token
[17:57:05 DBG] Endpoint enabled: Token, successfully created handler: IdentityServer4.Endpoints.TokenEndpoint
[17:57:05 INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.TokenEndpoint for /connect/token
[17:57:05 DBG] Start token request.
[17:57:05 DBG] Start client validation
[17:57:05 DBG] Start parsing Basic Authentication secret
[17:57:05 DBG] Start parsing for secret in post body
[17:57:05 DBG] client id without secret found
[17:57:05 DBG] Parser found secret: PostBodySecretParser
[17:57:05 DBG] Secret id found: EmailConfirmationVerify_App
[17:57:05 DBG] client configuration validation for client EmailConfirmationVerify_App succeeded.
[17:57:05 DBG] Public Client - skipping secret validation success
[17:57:05 DBG] Client validation success
Hello
I'm having trouble with users self registering where they are being directly logged into the application before they've confirmed their email address. This only occurs when they register initially. If they log out and attempt to log in again they are prevented from doing so until they confirm their email address. Ideally, they should not be immediately logged in upon registration until they have confirmed their email.
I have seen other people bring this issue up in another ticket (https://github.com/abpframework/abp/issues/3541), but I don't think concrete steps have been given to you for confirming the issue which is why it was closed off. Hopefully these steps will help
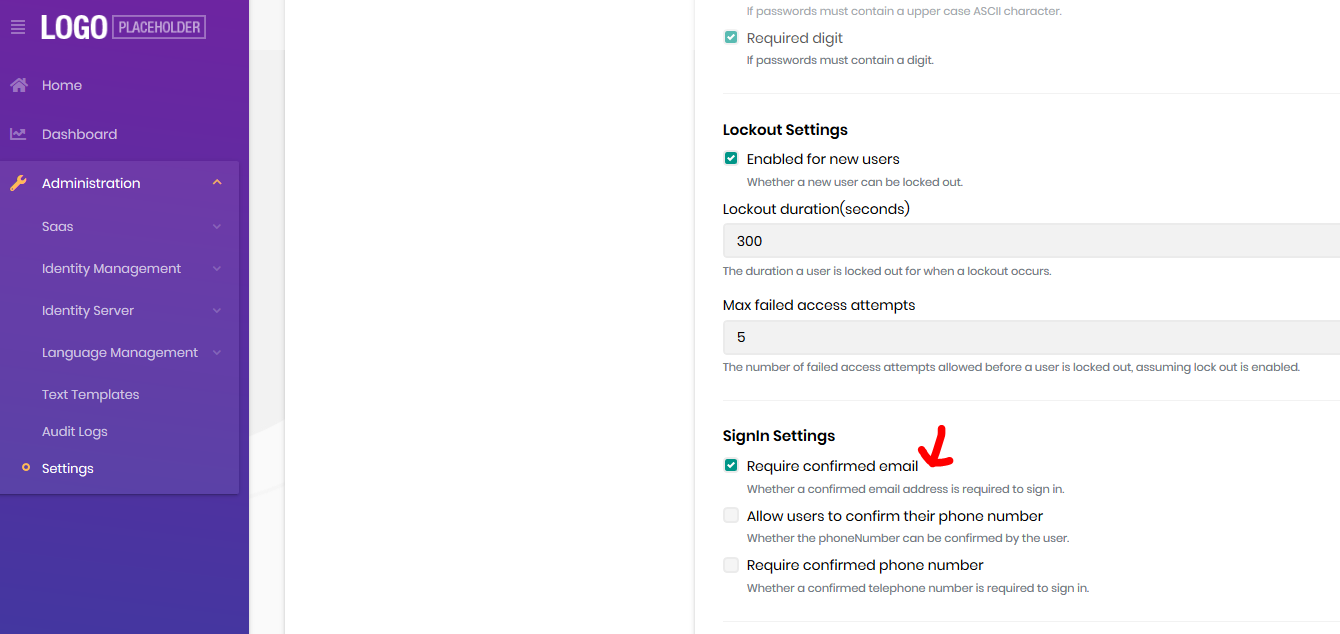
<br> Any assistance on whether I need to perform additional configuration would be appreciated, or whether this is a bug that needs fixing. If it's a bug, any workaround code as a temporary solution until a real fix is integrated into the main ABP codebase would also be appreciated.
Thankyou
Hi Alper and Mehmet
I'm very sorry for not responding back to this issue - I've been very busy implementing client functionality within the ABP framework(!) and it slipped my mind.
Thankyou for the instructions you provided. I have used bits and pieces from them with varying levels of success (like using the global styles to override component level styles and adding a new theme). I did, however, have to download the Lepton Theme sourcecode and integrate it within our main project to make the changes needed for the login screen layout we wanted.
I understand the styling customization features slated for 4.2 got pushed to 4.3, so I might revisit our approach once 4.3 comes out.
Thankyou again for your help. Keep up the good work!
Hello, thankyou for the information you have provided!
For customizing the MVC login screen, I have followed the instructions you have at this link - https://gist.github.com/ebicoglu/ce0f0425bab806d0ee1a87d0073af96b but this seems to only allow us to change the login form itself, but none of the structure / layouts around it. For example, what if I want to set the background to an image and move the login form over to the right of the screen? I've attached a picture showing a potential arrangement of the login screen. To be clear, I'm not asking how to implement this specific layout, rather I'm asking how can we implement layouts like it. The picture is just an example. It would also be important to know if layouts like the one in the picture be easily achieved without access to the commercial modules sourcecode, or do we require access to the commercial modules sourcecode to do this?
With regards to the Angular specific styling, you mention that there is something coming in v4.2-preview that will make it easier to add our own custom styling to the Lepton themed Angular components. Are you able to provide further details on the feature and how it will work?
In the meantime, before the new feature is available, if we had full access to the commercial module sourcecode (i.e business plan), would we be able to make our own styles for the Lepton themed Angular UI and put them into the application without too much trouble? It doesn't have to be a dynamically loaded style. It could be one premade at build time. Is there a guide somewhere on how this can be done with the Angular UI? I noticed the link you provided (https://community.abp.io/articles/creating-a-new-ui-theme-by-copying-the-basic-theme-for-blazor-ui-qaf5ho1b) was for the Blazor UI and not the Angular UI. The main thing we want to determine here is whether full access to the sourcecode is needed to change the styling, colours etc. of all the existing Lepton UI elements easily without requiring us to have to rip apart the entire framework to get it done.
Thankyou in advanced

