Activities of "william@iwell.nl"
- ABP Framework version: v8.2.2
- UI Type: Angular
- Database System: EF Core (SQL Server)
- Tiered (for MVC) or Auth Server Separated (for Angular): no
- Exception message and full stack trace:
- Steps to reproduce the issue:
We have enabled the impersonation, however the impersonation grant type is not seeded to the database. We added "Impersonation" to the grantTypes, as described in the documentation (https://abp.io/docs/latest/modules/account/impersonation#angular). When creating a new database, the Console Test / Angular Application is added to the table OpenIddictApplications.
However, the OpenIddictApplications row Portal_App and column Permissions is missing the 'gt:Impersonation' field. This results in the error message This client application is not allowed to use the specified grant type.. We can fix this by manually adding the gt:Impersonation, as described in this issue.
We would like this to be seeded, so new databases don't require this manual step.
What are we missing?
Content of OpenIddictApplications row Portal_App and column Permissions after seeding. [ "ept:logout", "gt:authorization_code", "rst:code", "ept:authorization", "ept:token", "ept:revocation", "ept:introspection", "gt:password", "gt:client_credentials", "gt:refresh_token", "scp:address", "scp:email", "scp:phone", "scp:profile", "scp:roles", "scp:Portal" ]
Our implementation of the seeder: We are sure this one is being used, as changing the display name does work.
OpenIddictDataSeedContributor
//Console Test / Angular Client
var consoleAndAngularClientId = configurationSection["Portal_App:ClientId"];
if (!consoleAndAngularClientId.IsNullOrWhiteSpace())
{
var consoleAndAngularClientRootUrl = configurationSection["Portal_App:RootUrl"]?.TrimEnd('/');
await CreateApplicationAsync(
name: consoleAndAngularClientId,
type: OpenIddictConstants.ClientTypes.Public,
consentType: OpenIddictConstants.ConsentTypes.Implicit,
displayName: "Console Test / Angular Application",
secret: null,
grantTypes:
[
OpenIddictConstants.GrantTypes.AuthorizationCode,
OpenIddictConstants.GrantTypes.Password,
OpenIddictConstants.GrantTypes.ClientCredentials,
OpenIddictConstants.GrantTypes.RefreshToken,
"LinkLogin", // somehow this is not being seeded to the database
"Impersonation" // somehow this is not being seeded to the database
],
scopes: commonScopes,
redirectUri: consoleAndAngularClientRootUrl,
clientUri: consoleAndAngularClientRootUrl,
postLogoutRedirectUri: consoleAndAngularClientRootUrl
);
}
- ABP Framework version: v7
- UI Type: Angular
- Database System: EF Core (SQL Server)
- Tiered (for MVC) or Auth Server Separated (for Angular): Auth server angular
When a request is cancelled by the browser, the logs show an error (see below). However this is expected behaviour and should not be logged as error as it clutters our logs. Can you guide us in how to filter this error message from the logs?
I have read the documentation about exception handling, but did not find a way https://docs.abp.io/en/abp/latest/Exception-Handling
- I've created a SuppressTaskCanceledExceptionFilter. Is that the best way to go, as it inherits and overrides the AbpExceptionFilter? Better to add another filter, is there a way to do so?
- After creating the filter I see the message is partially gone. Only the 'An error occurred using the connection to database' stays. How to get rid of that line?
[15:48:35 ERR] An error occurred using the connection to database 'portal-test' on server '.'.
[15:48:35 ERR] ---------- RemoteServiceErrorInfo ----------
{
"code": null,
"message": "An internal error occurred during your request!",
"details": null,
"data": {},
"validationErrors": null
}
[15:48:35 ERR] A task was canceled.
System.Threading.Tasks.TaskCanceledException: A task was canceled.
at Microsoft.EntityFrameworkCore.Storage.RelationalConnection.OpenInternalAsync(Boolean errorsExpected, CancellationToken cancellationToken)
at Microsoft.EntityFrameworkCore.Storage.RelationalConnection.OpenInternalAsync(Boolean errorsExpected, CancellationToken cancellationToken)
at Microsoft.EntityFrameworkCore.Stor
using Microsoft.AspNetCore.Mvc.Filters;
using System.Threading.Tasks;
[ExposeServices(typeof(AbpExceptionFilter), typeof(IAsyncExceptionFilter))]
public class SuppressTaskCanceledExceptionFilter : AbpExceptionFilter, ITransientDependency
{
public override Task OnExceptionAsync(ExceptionContext context)
{
if (context.Exception is TaskCanceledException)
{
context.ExceptionHandled = true; // This will suppress the logging
return Task.CompletedTask;
}
return base.OnExceptionAsync(context);
}
}
- ABP Framework version: v5.2
- UI Type: Angular
- Database System: EF Core (SQL Server)
- Tiered (for MVC) or Auth Server Separated (for Angular): Auth Server Separated (for Angular)
Hi ABP team,
i have a question about account creation. We would like to create account for new employees and prepare that before they start their onboarding. But this process is a bit cumbersome at the moment.
Two requirements:
- using google authentication is preferred, to avoid multiple accounts and credentials and different MFA steps
- account creation should not be allowed (otherwise random users can create accounts)
What we do now to create an account with google authentication:
- sit together with the new employee
- admin enables the self registration
- new user goes to login page and clicks the login with google button
- a register user screen appears and the account is created with the email of the google account. A blank screen appears (no permissions)
- admin adds permissions
- new user still sees a blank screen
- new user removes cookies and then the page and data becomes visible
- admin disables the self registration
We would like to improve this proces. Can you point us in a direction how to do this? Are we encountering a (known) bug or desired (to be build) feature of the framework or should we change our implementation?
Thanks a lot!
- ABP Framework version: v5.2.2
- UI type: Angular
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): Angular/
- Exception message and stack trace:
- Steps to reproduce the issue:"
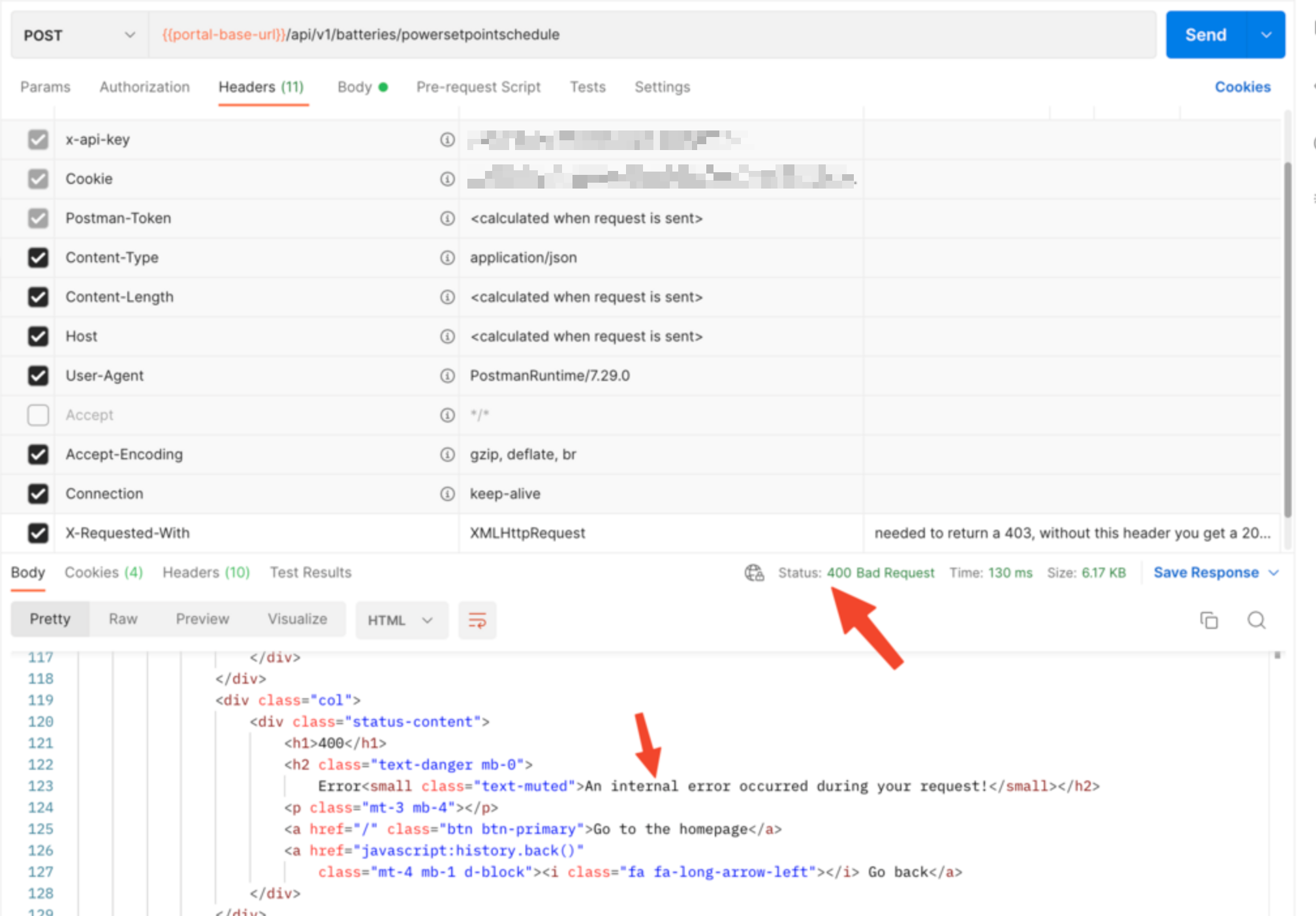
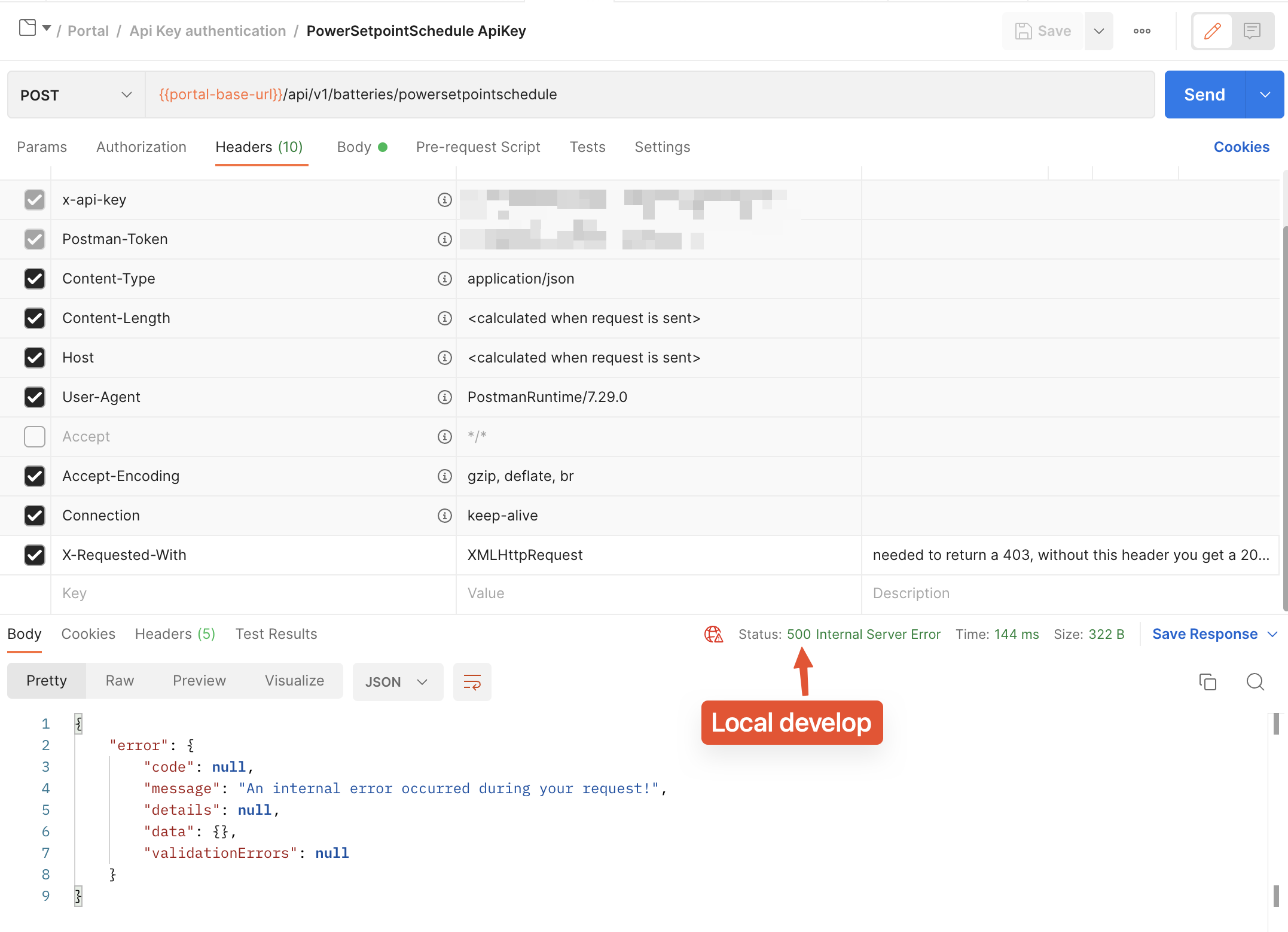
An endpoint always throws an Exception (as test). I expect this endpoint to return a 500 with json, and on a local develop environment it does. However on production the endpoint returns a 400 with html.
What causes this?
- ABP Framework version: v4.3
- UI type: Angular
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): yes
- Exception message and stack trace:
- Steps to reproduce the issue:
Switch the flow to resource owner password, as described in the documentation (https://github.com/abpframework/abp/blob/dev/docs/en/UI/Angular/Account-Module.md) Configure a external client (google for example) Login => google login button is missing.
The mvc login page does contain the google login button. Is this also supported in Angular? Or should I configure someting else to enable it?
ABP Framework version: v4.3-rc1
- UI type: Angular / MVC
- DB provider: MongoDB
- Tiered (MVC) or Identity Server Separated (Angular): no
How can I configure the Settings:Abp.Mailing.Smtp.Host by overriding de defaults in the Azure app service (linux)?
I tried to add the application setting Settings__Abp.Mailing.Smtp.Host, but that doesn't seem to work. app__CorsOrigins does work, so using the double works to set a nested config setting. But this doesn't seem to work for the Abp.Mailing.Smtp.Host part. Maybe the dots need some sort of prefix for Linux?
- ABP Framework version: v4.2.2
- UI type: Angular
- DB provider: MongoDB
- Tiered (MVC) or Identity Server Separated (Angular): yes / no
- Exception message and stack trace:
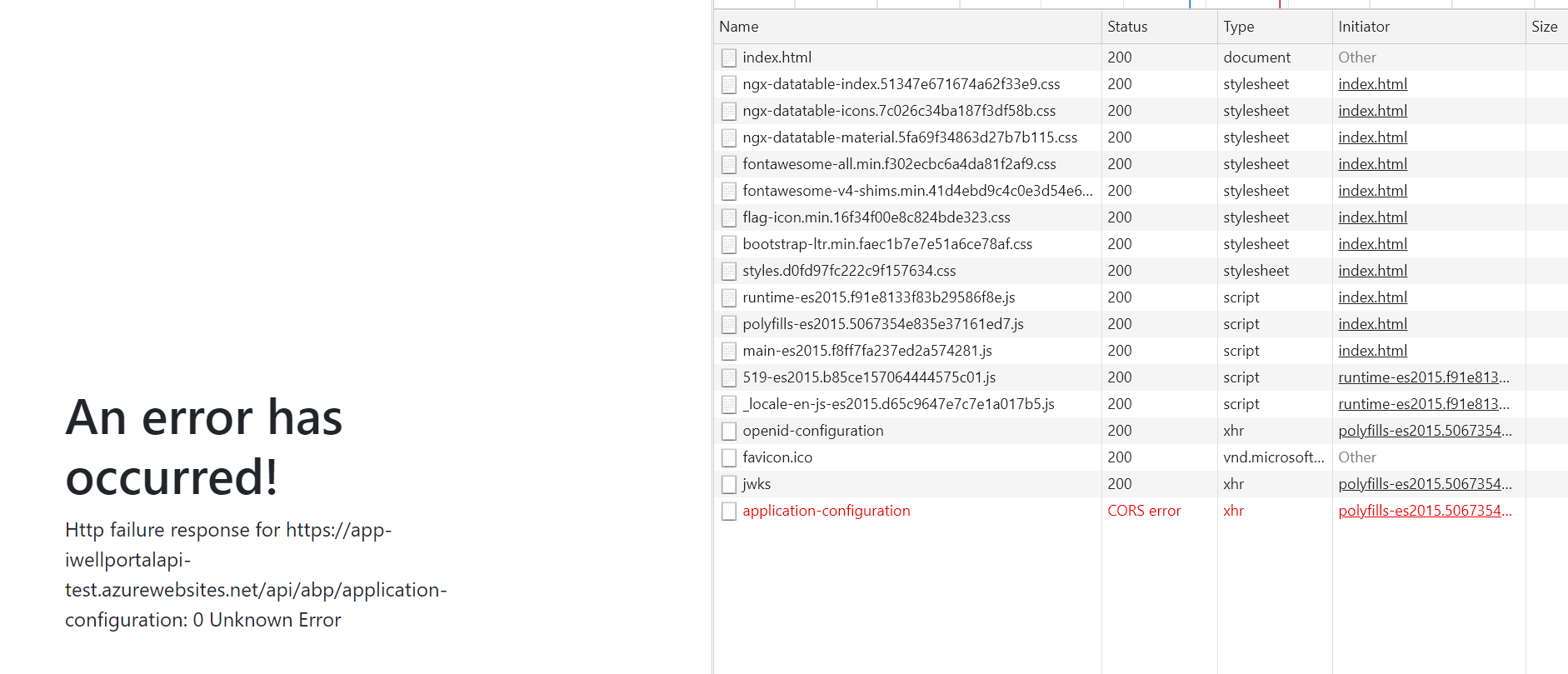
Access to XMLHttpRequest at 'https://app-iwellportalapi-test.azurewebsites.net/api/abp/application-configuration' from origin 'https://app-iwellportalfe-test.azurewebsites.net' has been blocked by CORS policy: No 'Access-Control-Allow-Origin' header is present on the requested resource.
2021-03-23T14:23:38.161958372Z [14:23:38 INF] Request starting HTTP/1.1 GET http://app-iwellportalapi-test.azurewebsites.net/.well-known/openid-configuration - -
2021-03-23T14:23:38.162998333Z [14:23:38 INF] CORS policy execution failed.
2021-03-23T14:23:38.163009434Z [14:23:38 INF] Request origin https://app-iwellportalfe-test.azurewebsites.net does not have permission to access the resource.
2021-03-23T14:23:38.202722084Z [14:23:38 DBG] CORS request made for path: /.well-known/openid-configuration from origin: https://app-iwellportalfe-test.azurewebsites.net
2021-03-23T14:23:38.203473028Z [14:23:38 DBG] CorsPolicyService allowed origin: https://app-iwellportalfe-test.azurewebsites.net
2021-03-23T14:23:38.204043162Z [14:23:38 INF] CORS policy execution successful.
2021-03-23T14:23:38.222146133Z [14:23:38 DBG] Request path /.well-known/openid-configuration matched to endpoint type Discovery
2021-03-23T14:23:38.234305952Z [14:23:38 DBG] Endpoint enabled: Discovery, successfully created handler: IdentityServer4.Endpoints.DiscoveryEndpoint
2021-03-23T14:23:38.234917188Z [14:23:38 INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.DiscoveryEndpoint for /.well-known/openid-configuration
2021-03-23T14:23:38.235332913Z [14:23:38 DBG] Start discovery request
2021-03-23T14:23:38.263539382Z [14:23:38 INF] Request finished HTTP/1.1 GET http://app-iwellportalapi-test.azurewebsites.net/.well-known/openid-configuration - - - 200 - application/json;+charset=UTF-8 109.9435ms
2021-03-23T14:23:38.294173694Z [14:23:38 INF] Request starting HTTP/1.1 GET http://app-iwellportalapi-test.azurewebsites.net/.well-known/openid-configuration/jwks - -
2021-03-23T14:23:38.295129951Z [14:23:38 INF] CORS policy execution failed.
2021-03-23T14:23:38.295750187Z [14:23:38 INF] Request origin https://app-iwellportalfe-test.azurewebsites.net does not have permission to access the resource.
2021-03-23T14:23:38.317353966Z [14:23:38 DBG] CORS request made for path: /.well-known/openid-configuration/jwks from origin: https://app-iwellportalfe-test.azurewebsites.net
2021-03-23T14:23:38.323893753Z [14:23:38 DBG] CorsPolicyService allowed origin: https://app-iwellportalfe-test.azurewebsites.net
2021-03-23T14:23:38.323910253Z [14:23:38 INF] CORS policy execution successful.
2021-03-23T14:23:38.334096556Z [14:23:38 DBG] Request path /.well-known/openid-configuration/jwks matched to endpoint type Discovery
2021-03-23T14:23:38.344425167Z [14:23:38 DBG] Endpoint enabled: Discovery, successfully created handler: IdentityServer4.Endpoints.DiscoveryKeyEndpoint
2021-03-23T14:23:38.345388624Z [14:23:38 INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.DiscoveryKeyEndpoint for /.well-known/openid-configuration/jwks
2021-03-23T14:23:38.345831250Z [14:23:38 DBG] Start key discovery request
2021-03-23T14:23:38.345841651Z [14:23:38 INF] Request finished HTTP/1.1 GET http://app-iwellportalapi-test.azurewebsites.net/.well-known/openid-configuration/jwks - - - 200 - application/json;+charset=UTF-8 48.4587ms
2021-03-23T14:23:38.385268984Z [14:23:38 INF] Request starting HTTP/1.1 GET http://app-iwellportalapi-test.azurewebsites.net/api/abp/application-configuration - -
2021-03-23T14:23:38.386149036Z [14:23:38 INF] CORS policy execution failed.
2021-03-23T14:23:38.386823176Z [14:23:38 INF] Request origin https://app-iwellportalfe-test.azurewebsites.net does not have permission to access the resource.
2021-03-23T14:23:38.446165787Z [14:23:38 DBG] CORS request made for path: /api/abp/application-configuration from origin: https://app-iwellportalfe-test.azurewebsites.net but was ignored because path was not for an allowed IdentityServer CORS endpoint
2021-03-23T14:23:38.447005836Z [14:23:38 INF] No CORS policy found for the specified request.
2021-03-23T14:23:38.449683195Z [14:23:38 INF] Executing endpoint 'Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController.GetAsync (Volo.Abp.AspNetCore.Mvc)'
2021-03-23T14:23:38.509187115Z [14:23:38 INF] Route matched with {area = "abp", action = "Get", controller = "AbpApplicationConfiguration", page = ""}. Executing controller action with signature System.Threading.Tasks.Task`1[Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ApplicationConfigurationDto] GetAsync() on controller Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController (Volo.Abp.AspNetCore.Mvc).
2021-03-23T14:23:38.509212017Z [14:23:38 DBG] Executing AbpApplicationConfigurationAppService.GetAsync()...
2021-03-23T14:23:38.695839158Z [14:23:38 DBG] Executed AbpApplicationConfigurationAppService.GetAsync().
2021-03-23T14:23:38.703242496Z [14:23:38 INF] Executing ObjectResult, writing value of type 'Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.ApplicationConfigurationDto'.
2021-03-23T14:23:38.773197735Z [14:23:38 INF] Executed action Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController.GetAsync (Volo.Abp.AspNetCore.Mvc) in 315.511ms
2021-03-23T14:23:38.773802671Z [14:23:38 INF] Executed endpoint 'Volo.Abp.AspNetCore.Mvc.ApplicationConfigurations.AbpApplicationConfigurationController.GetAsync (Volo.Abp.AspNetCore.Mvc)'
2021-03-23T14:23:38.774209595Z [14:23:38 INF] Request finished HTTP/1.1 GET http://app-iwellportalapi-test.azurewebsites.net/api/abp/application-configuration - - - 200 - application/json;+charset=utf-8 380.1425ms
- Steps to reproduce the issue:
- locally the application runs fine
- update dbmigration settings for test environment and run to update test database
- deploy aspnet-core to azure app service (linux) and update appsettings like below. Swagger authorizations works.
app__CorsOrigins="https://app-iwellportalapi-test.azurewebsites.net, http://app-iwellportalapi-test.azurewebsites.net, https://app-iwellportalfe-test.azurewebsites.net"
app__RedirectAllowedUrls="https://app-iwellportalapi-test.azurewebsites.net,https://app-iwellportalfe-test.azurewebsites.net"
AuthServer__Authority="https://app-iwellportalapi-test.azurewebsites.net/"
AuthServer__SwaggerClientSecret="1q2w3e*"
- update angular environment.prod.ts and deploy angular to separate app service (https://app-iwellportalfe-test.azurewebsites.net)
- open the angular site and see the Cors error