Thanks great, did you make any changes angular or api side ? please let me know i will follow the same steps.
We are currently facing an unresolved issue with client authentication that has been escalating internally. This problem is impacting our productivity and is also affecting our client, who is waiting for a resolution.
Given the urgency and complexity of the situation, I believe scheduling a meeting would be beneficial. This will allow us to discuss the issue in detail and work towards a swift resolution.
Could you please arrange a meeting at your earliest convenience? Your assistance in this matter would be greatly appreciated
what is issue ? However, ** "/signin-oidc"** method exist in application after authenticated response redirected this endpoint
?
what is issue ? However, ** "/signin-oidc"** method exist in application after authenticated response redirected this endpoint
First move
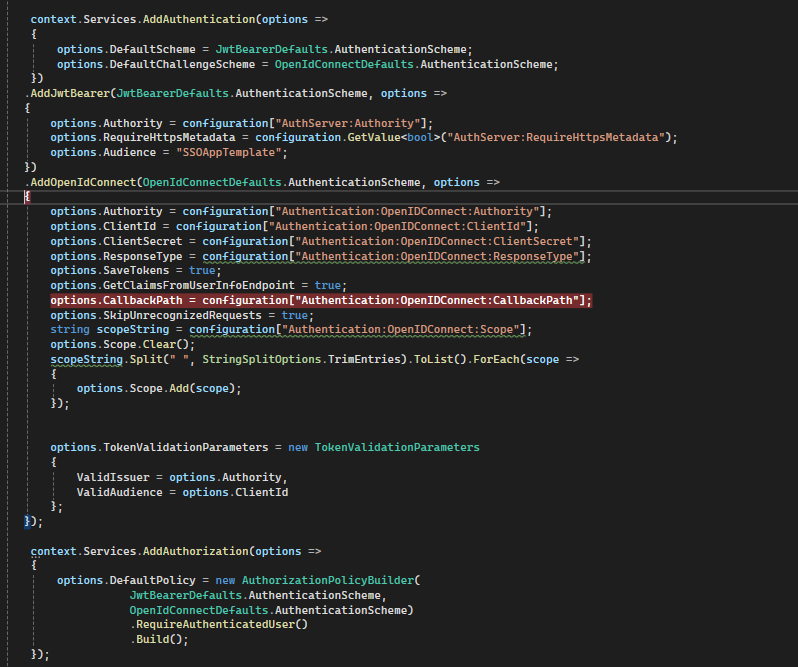
OIDCControllerfromHttpApi.HosttoAuthserverI will do first pointthen remove
CallbackPathfromappsettingsand theAddOpenIdConnectmethod.
CallbackPath it's mandatory for if AddOpenIdConnect, if i remove this then by default read "/sigin-oidc" path and then facing call back URLpath.
we can't remove because it's mandatory.
remove
AuthorizefromOIDCController
One of ABP ticket i have seen we can handle multiple schema like below code, then you can used Authorize for controller.
Note:- it's working this means if i access specific URL endpoint able to access doesn't cause issue Authorize .
Use
api/oidc/loginmethod instead ofauthorize.
Update your logo href link to
<AuthServerURL>api/oidc/login
I have same requirement like this ticket .
https://abp.io/support/questions/5493/How-do-I-generate-the-Auth-url-that-will-allow-a-non-ABP-related-website-authenticate-with-ABP-OpenIddict.
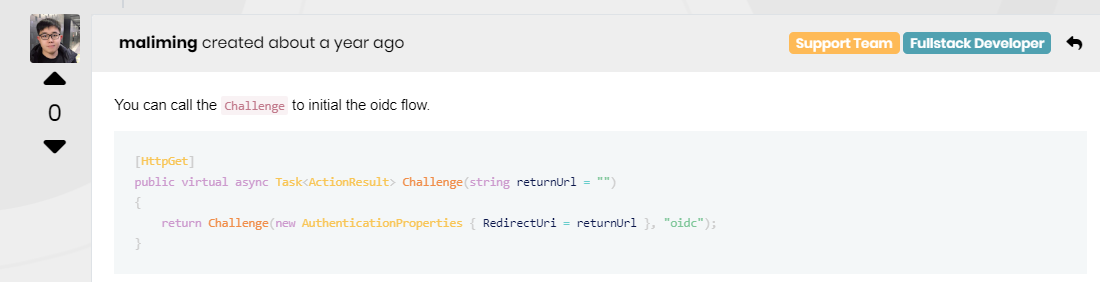
instead of authorize method i used below method to initial OIDC flow.
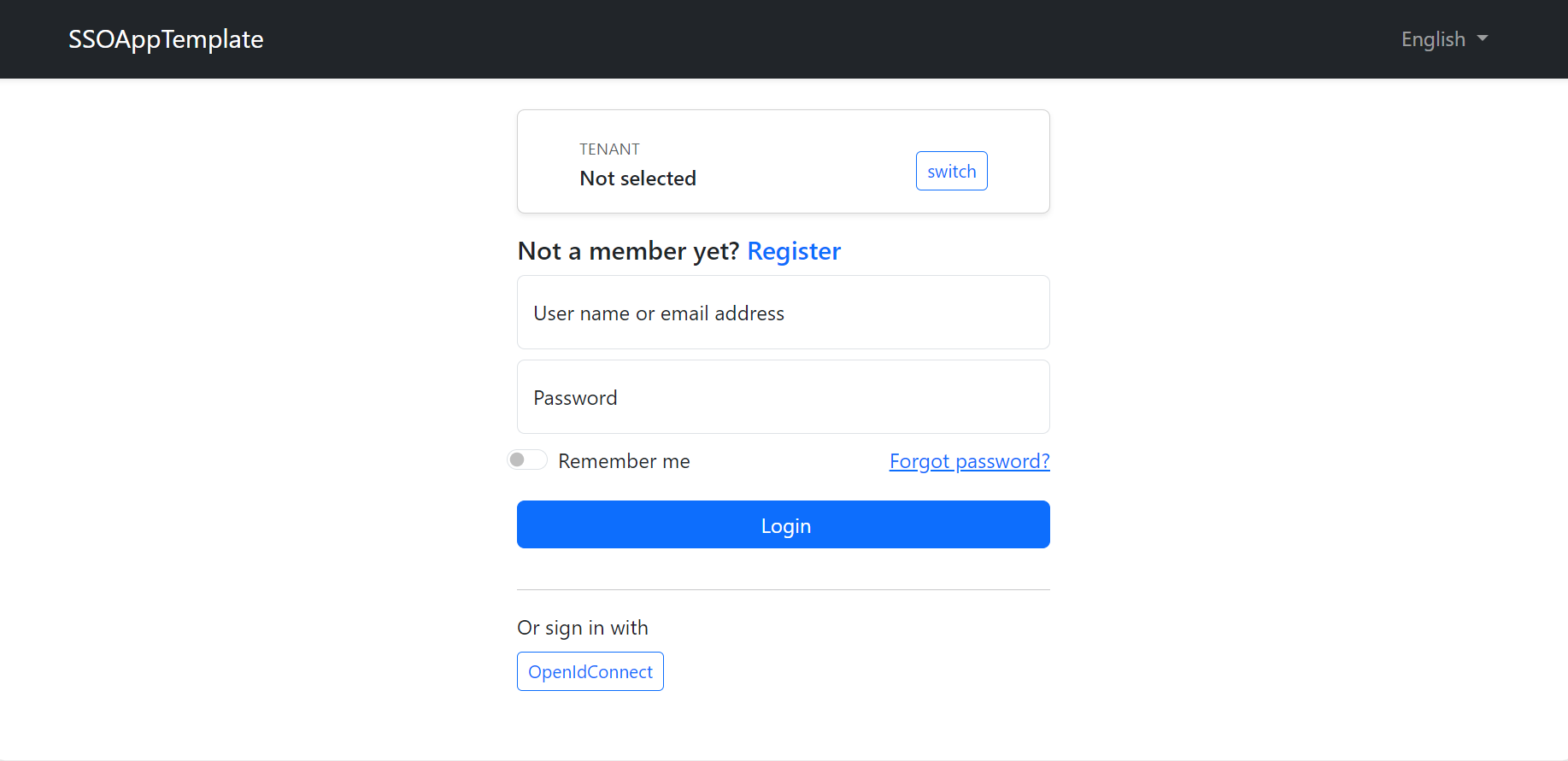
 I was able to log in successfully, but after the login, I need to redirect to the Angular dashboard. However, after being redirected, the dashboard is displaying the following screen.
I was able to log in successfully, but after the login, I need to redirect to the Angular dashboard. However, after being redirected, the dashboard is displaying the following screen.