Running this command...
abp new Foo -t app-pro
...results in this error.
[14:59:07 INF] ABP CLI (https://abp.io)
[14:59:08 INF] Version 4.3.3 (Stable)
[14:59:09 INF] Creating your project...
[14:59:09 INF] Project name: Foo
[14:59:09 INF] Template: app-pro
[14:59:09 INF] Output folder: C:\Users\jogoertzen\temp1
[14:59:11 INF] Downloading template: app-pro, version: 4.3.3
Error occured while downloading source-code from https://abp.io/api/download/template/ :
Error while copying content to a stream.
[14:59:43 ERR] Error while copying content to a stream.
System.Net.Http.HttpRequestException: Error while copying content to a stream.
---> System.IO.IOException: Unable to read data from the transport connection: An existing connection was forcibly closed by the remote host..
---> System.Net.Sockets.SocketException (10054): An existing connection was forcibly closed by the remote host.
--- End of inner exception stack trace ---
at System.Net.Sockets.Socket.AwaitableSocketAsyncEventArgs.ThrowException(SocketError error, CancellationToken cancellationToken)
at System.Net.Sockets.Socket.AwaitableSocketAsyncEventArgs.GetResult(Int16 token)
at System.Net.Security.SslStream.ReadAsyncInternal[TIOAdapter](TIOAdapter adapter, Memory`1 buffer)
at System.Net.Http.HttpConnection.FillAsync(Boolean async)
at System.Net.Http.HttpConnection.CopyToContentLengthAsync(Stream destination, Boolean async, UInt64 length, Int32 bufferSize, CancellationToken cancellationToken)
at System.Net.Http.HttpConnection.ContentLengthReadStream.CompleteCopyToAsync(Task copyTask, CancellationToken cancellationToken)
at System.Net.Http.HttpConnectionResponseContent.SerializeToStreamAsync(Stream stream, TransportContext context, CancellationToken cancellationToken)
at System.Net.Http.HttpContent.LoadIntoBufferAsyncCore(Task serializeToStreamTask, MemoryStream tempBuffer)
--- End of inner exception stack trace ---
at System.Net.Http.HttpContent.LoadIntoBufferAsyncCore(Task serializeToStreamTask, MemoryStream tempBuffer)
at System.Net.Http.HttpClient.SendAsyncCore(HttpRequestMessage request, HttpCompletionOption completionOption, Boolean async, Boolean emitTelemetryStartStop, CancellationToken cancellationToken)
at Volo.Abp.Cli.ProjectBuilding.AbpIoSourceCodeStore.DownloadSourceCodeContentAsync(SourceCodeDownloadInputDto input) in D:\ci\Jenkins\workspace\abp-framework-release\abp\framework\src\Volo.Abp.Cli.Core\Volo\Abp\Cli\ProjectBuilding\AbpIoSourceCodeStore.cs:line 208
at Volo.Abp.Cli.ProjectBuilding.AbpIoSourceCodeStore.GetAsync(String name, String type, String version, String templateSource, Boolean includePreReleases) in D:\ci\Jenkins\workspace\abp-framework-release\abp\framework\src\Volo.Abp.Cli.Core\Volo\Abp\Cli\ProjectBuilding\AbpIoSourceCodeStore.cs:line 112
at Volo.Abp.Cli.ProjectBuilding.TemplateProjectBuilder.BuildAsync(ProjectBuildArgs args) in D:\ci\Jenkins\workspace\abp-framework-release\abp\framework\src\Volo.Abp.Cli.Core\Volo\Abp\Cli\ProjectBuilding\TemplateProjectBuilder.cs:line 56
at Volo.Abp.Cli.Commands.NewCommand.ExecuteAsync(CommandLineArgs commandLineArgs) in D:\ci\Jenkins\workspace\abp-framework-release\abp\framework\src\Volo.Abp.Cli.Core\Volo\Abp\Cli\Commands\NewCommand.cs:line 192
at Volo.Abp.Cli.CliService.RunAsync(String[] args) in D:\ci\Jenkins\workspace\abp-framework-release\abp\framework\src\Volo.Abp.Cli.Core\Volo\Abp\Cli\CliService.cs:line 59
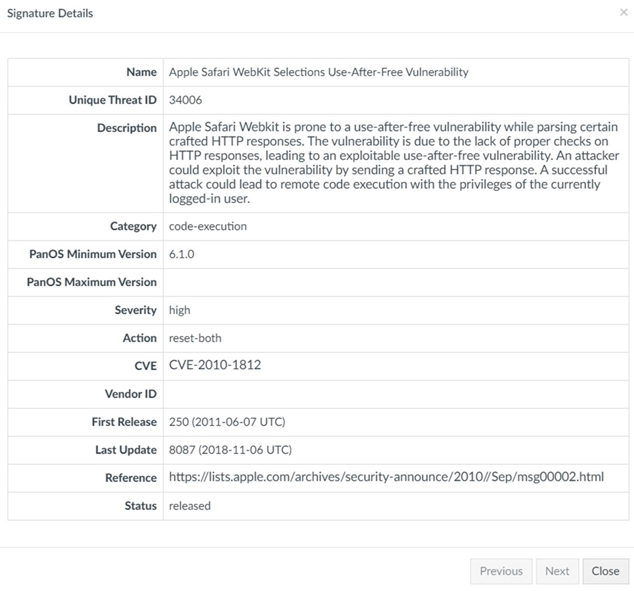
It turns out our firewall is blocking the download due to a high severity vulnerability in the file tui-editor-Editor-full.js called Apple Safari WebKit Selections Use-After-Free Vulnerability.
I have a few questions.
- Are you aware of this?
- Is there anything you can do to fix it?
- Is there anything we can do to work around it?
I have yet to find much information regarding this vulnerability, so any information you can provide would be appreciated.
Thanks!
11 Answer(s)
-
0
Hi,
Thanks for the feedback about this issue.
- Are you aware of this?
- No, we are not aware this.
- Is there anything you can do to fix it?
- this is a 3rd party lib, we have no sanction on it. but as we use it, we can create an issue on the TuiEditor Repo. can you share us the report which prooves this lib has the corresponding vulnerability.
- Is there anything we can do to work around it?
- Tui Editor comes with the template (it's in the
libfolder of MVC project) that's why it's hard to remove it from the template.
- Tui Editor comes with the template (it's in the
As a work around ;
- switch to your mobile phone network (or any other network that allows this download)
- create a new project. when you create it, the project template will be saved in
%UserProfile%\.abp\templates - from now on, you'll be no longer downloading the template
- you can share the zip file
%UserProfile%\.abp\templates\app-pro-4.3.3.zipwith your team. when you copy this file into%UserProfile%\.abp\templates, ABP CLI will not download again.
- Are you aware of this?
-
0
Thanks, albert.
I reached out to our firewall team to see if they can provide the report you requested.
-
0
They gave me this: https://nvd.nist.gov/vuln/detail/CVE-2010-1812
-
0
-
0
by the way this package is being used by ABP Cms-Kit module. if you don't use this module, you can safetly delete it. Once the issue gets fixed by TuiEditor developers, you can add it again.
-
0
Created an issue on the Tui Editor repository https://github.com/nhn/tui.editor/issues/1625
-
0
Hi Albert,
Judging by the responses to the issue you created, it looks like upgrading to
tui.editorv2.xis the recommended way to resolve this issue.Is this something that can be done?
-
0
@jogoertzen as I see, the vulnerability is at
v1.xWe upgraded tov2.xin our latest releases. You can upgrade your ABP version. See where it's used https://github.com/abpframework/abp/blob/dev/npm/packs/tui-editor/package.json#L12 -
0
@albert
We tried using the preview version of the application template with abp suite v4.3.3 which attempts to download the
app-pro-4.4.0-rc.2template, but our firewall blocks it again claiming it found the sameApple Safari WebKit Selections Use-After-Free Vulnerability, but this time the file it claims has the vulnerability istoastui-editor.jsas opposed totui-editor-Editor-full.jswhich was reported previously when downloading theapp-pro-4.3.3template.So it seems the apparent false-positive is still there in
v2.xof Toast UI. -
0
there's not much thing we can do for the false-positive alert. we are using the latest version of Toast UI and we cannot replace it or change the source of this 3rd party. you may ask your system administrator to set it as false-positive.
-
0
Alright. Thanks for looking into it anyways.