If you're creating a bug/problem report, please include followings:
- ABP Framework version: v5.3.2
- UI type: Blazor
- DB provider: EF Core
- Tiered (MVC) or Identity Server Separated (Angular): no
- Exception message and stack trace: AADSTS50011 : The redirect URI http://XYZ/signin-azuread-oidc' specified in the request does not match the redirect URIs configured for the application.
- Steps to reproduce the issue:"
Hi,
I'm currently trying to use Azure AD authentication using the Option 2 (AddMicrosoftIdentityWebApp) provided in the Community post. https://community.abp.io/posts/how-to-use-the-azure-active-directory-authentication-for-mvc-razor-page-applications-4603b9cf?_ga=2.233242457.671860167.1658432542-369280404.1658432542
It worked perfectly on my local machine until I had to deploy the app in the Azure environment.
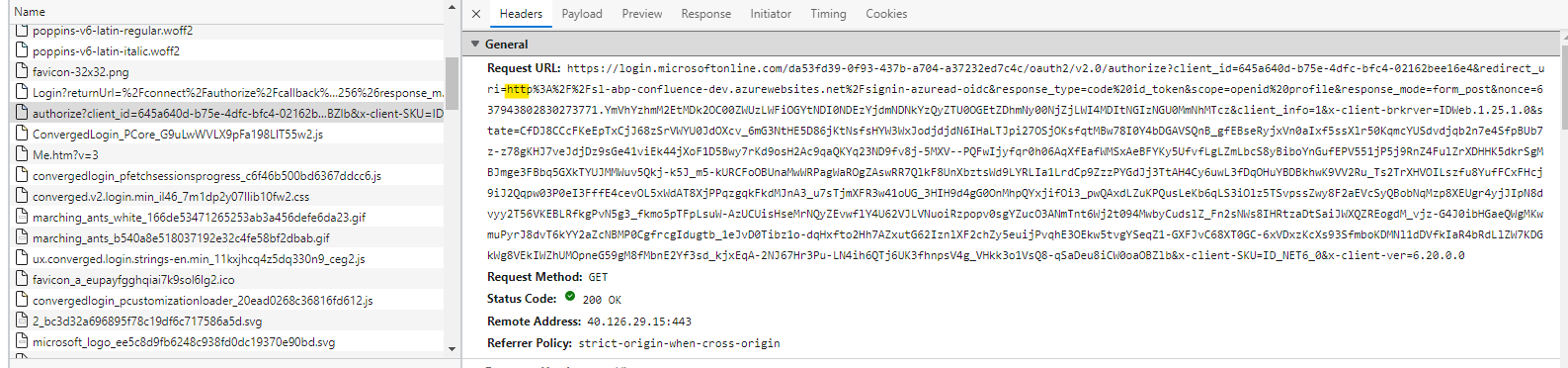
I'm getting the AADSTS50011 authentication error specifying the my redirect URIs are not matching between what's configured in the App Registration and what's provided from the app.
From the message received, I can see that Azure is trying to call my backend over HTTP instead of HTTPS. When I'm looking at my network traffic, I do see that the redirect_uri parameter from the URL is encoded over HTTP!
Tried solving this issue from the FAQs in the previous link and started having issues with the AzureAd:CallbackPath setting. It doesn't allow to put anything that isn't starting with a "/", so the proposed solution to specify an HTTPS return URL isn't going to work.
I'm running the code in an docker container within a Azure App Service running linux.
Any guidance will be greatly appreciated. Thanks
4 Answer(s)
-
0
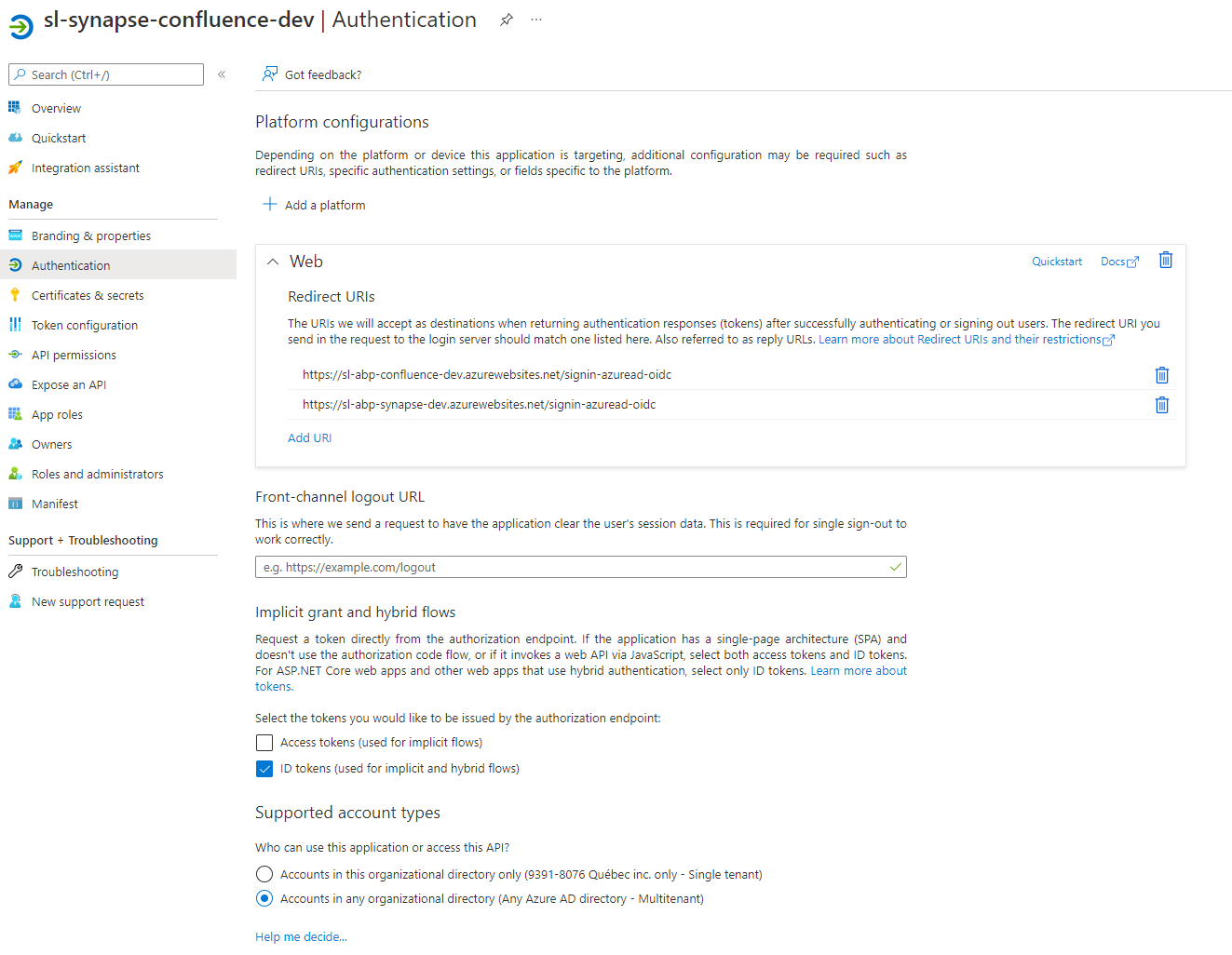
Do you have redirectURI configured as HTTPS on Azure App registry? Can you share information about your azure app registration?
-
0
The app registration only has 2 redirects and doesn't let me configure anything else than an HTTPS URL. It's configured to use ID Tokens and is Multitenant enabled.
Let me know if you need anything more specific.
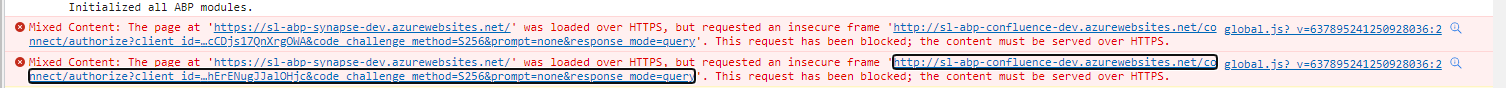
I also have these console issues that come up when accessing my dev environment! They seem to be related!
Thanks
-
0
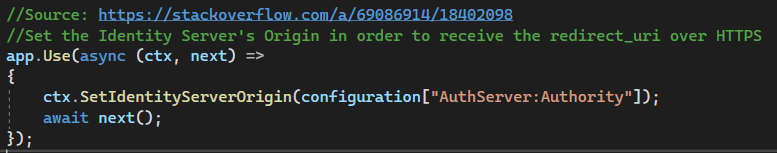
You can use HTTPS redirection at
OnApplicationInitialization:... app.UseHsts(); app.UseHttpsRedirection(); ...that should redirect incoming HTTP to HTTPS. However, I am not sure if this will work if you have a proxy (or web-server configuration) that redirects incoming HTTPS to HTTP.
Do you have any proxy or web-server configuration between your application and azure that can be redirecting HTTPS to HTTP? If not, can you also contact to Azure support about why OpenId Connect configuration doesn't respect to Azure application configuration?
-
0