Hi There we are having real difficult implementing a working solution to enable users to logon using Microsoft Identity (SSO) and then hook that up with the identity server to link roles/permissions.
Do you have any working examples, if not how do we validate the SSO back with identity server to authenticate.
Please can you arrange a call with us to go through.
Dave
14 Answer(s)
-
0
Hi
Any chance we can get a response / support on this, we are having difficult with hooking up permissions on external login provider logged in.
We have tried a number of the examples from ABP, however they do not fit our example and need support.
We have a commercial ABP licence.
Dave
-
0
hi Dave
There we are having real difficult implementing a working solution to enable users to logon using Microsoft Identity (SSO) and then hook that up with the identity server to link roles/permissions.
Can you explain it in detail?
-
0
Hi maliming, Firstly, thanks for responding.
We have a blazor server tiered solution using identity server for authentication. It works fine when using local login and we are trying to implement single sign on through Azure so our customers will not need to login in if they are already signed in through their own AD.
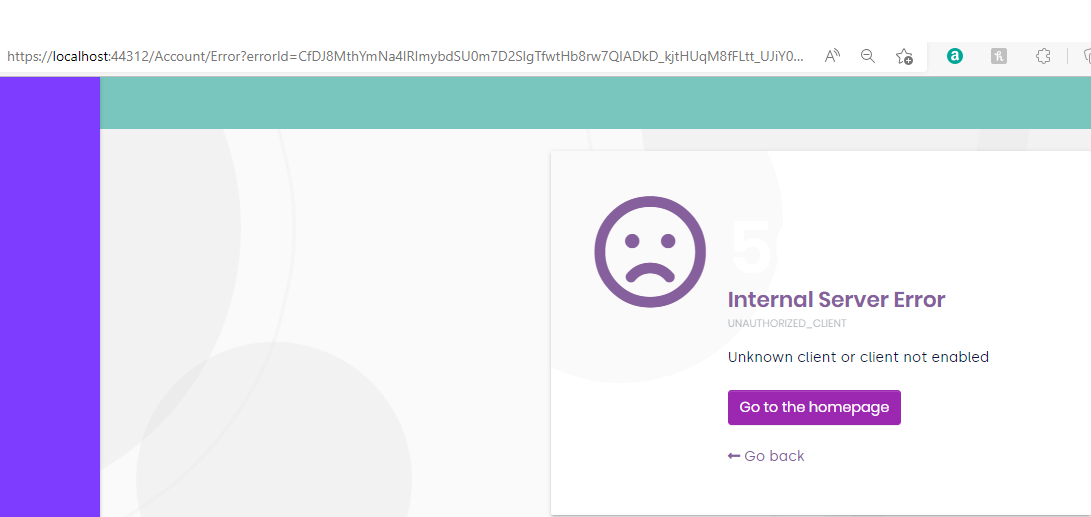
We have not been able to achieve this. We have used as our baseline the example given here, I.e. we have set up the Azure end as described in that article, We understand that article was addressing MVC (we couldn't find any equivalent for blazor server) so the part of the article that addresses changes to the ABP web Application threw us as we don't have Pages in our Api.Host. We added the required code to the api host, we can login via azure, but because there is no relationship between our abp users and our azure users we are not authorizing which of course means our menus are incorrect and our API calls are being bounced. Are there any examples of adding single sign on for blazor server (and identity server). We're quite willing to go to OpenIddict (seems sensible as this point), but we'd obviously then be in a similar boat (we tried it actually), so is there an example for adding OpenIddict for Azure single sign on to an existin blazor server app?
-
0
hi
we can login via azure, but because there is no relationship between our abp users and our azure users we are not authorizing which of course means our menus are incorrect and our API calls are being bounced.
The framework will compare the local user's email with the azure user. Does your application fit this design?
-
0
Perhaps it should fit - i.e. the framework should compare the local user's email with that of the azure user, and we know that claim is certainly available - but it does not appear to be working. Obviously this implies we are missing some step that relates those two.
Would it be possible to arrange an online session to discuss our problem with someone familiar with this scenario?.
Failing that - and anyway - is there an example of using OpenIddict with Blazor Server (Tiered) to achieve single sign on with Azure Ad - as release 6.0 is due real soon it would make sense for us at this stage of development to go that route - but only if it works.
-
0
hi
we know that claim is certainly available - but it does not appear to be working.
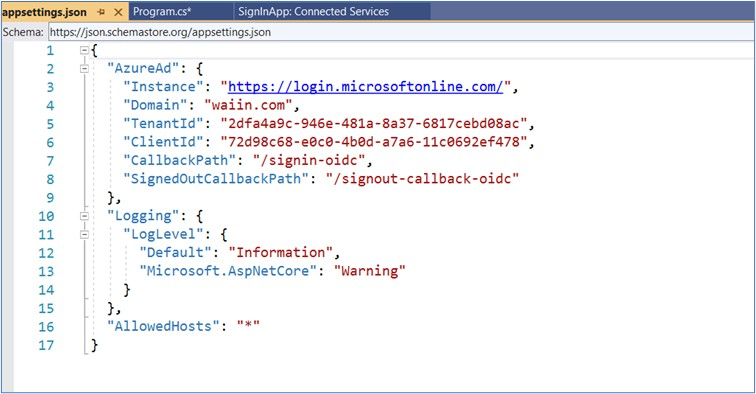
Can you share your azure configuration with me? liming.ma@volosoft.com
I will test it in my locally.
-
0
I've added a repo and invited you The repo does not include the changes I mentioned above - I.e it is only local logon via identity server at the moment - default admin password can be found in Source\Core\SupplierPortal.Domain\SupplierPortalConsts.cs
-
0
-
0
did you receive my email?
-
0
hi
Yes, I will test is asap.
-
1
hi
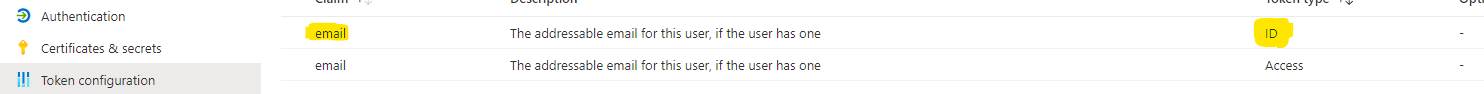
I think you can add email to
id_tokenin your azure AD settings. https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-optional-claimsor you can test with the below code.
private void ConfigureExternalProviders(ServiceConfigurationContext context) { context.Services.AddAuthentication() .AddMicrosoftIdentityWebApp( microsoftIdentityOptions => { microsoftIdentityOptions.Instance = "https://login.microsoftonline.com/"; microsoftIdentityOptions.Domain = "xxx"; microsoftIdentityOptions.TenantId = "xxx"; microsoftIdentityOptions.ClientId = "xxx"; microsoftIdentityOptions.ClientSecret = "xxx"; microsoftIdentityOptions.CallbackPath = "/signin-azuread-oidc"; microsoftIdentityOptions.SignedOutCallbackPath = "/signout-callback-oidc"; microsoftIdentityOptions.SignInScheme = IdentityConstants.ExternalScheme; }, cookieAuthenticationOptions => { }, OpenIdConnectDefaults.AuthenticationScheme, null); context.Services.PostConfigure<OpenIdConnectOptions>(OpenIdConnectDefaults.AuthenticationScheme, options => { // Add email to id_token in your azure AD settings. options.ClaimActions.Add(new AddEmailClaim()); }); }public class AddEmailClaim : ClaimAction { public AddEmailClaim() : base(null, null) { } public override void Run(JsonElement userData, ClaimsIdentity identity, string issuer) { var preferred_username = identity.Claims.FirstOrDefault(x => x.Type == "preferred_username"); if (preferred_username != null) { identity.AddClaim(new Claim(AbpClaimTypes.Email, preferred_username.Value)); } } } -
0
-
0
I think it would be good if you could just point us in the direction of an example that does what we're trying to achieve. I'm sure we're not the only team wanting to do this.
-
0
if you could just point us in the direction of an example that does what we're trying to achieve
ok, Please create a new brand project and send it to me, I will update it and get back to you. liming.ma@volosoft.com