We are testing SSO with Okta using OpenID Connect as below:
- Create an OIDC (OpenID Connect) application that link to the ABP tenant in Okta.
- Create the necessary users and assign them to the above OIDC application.
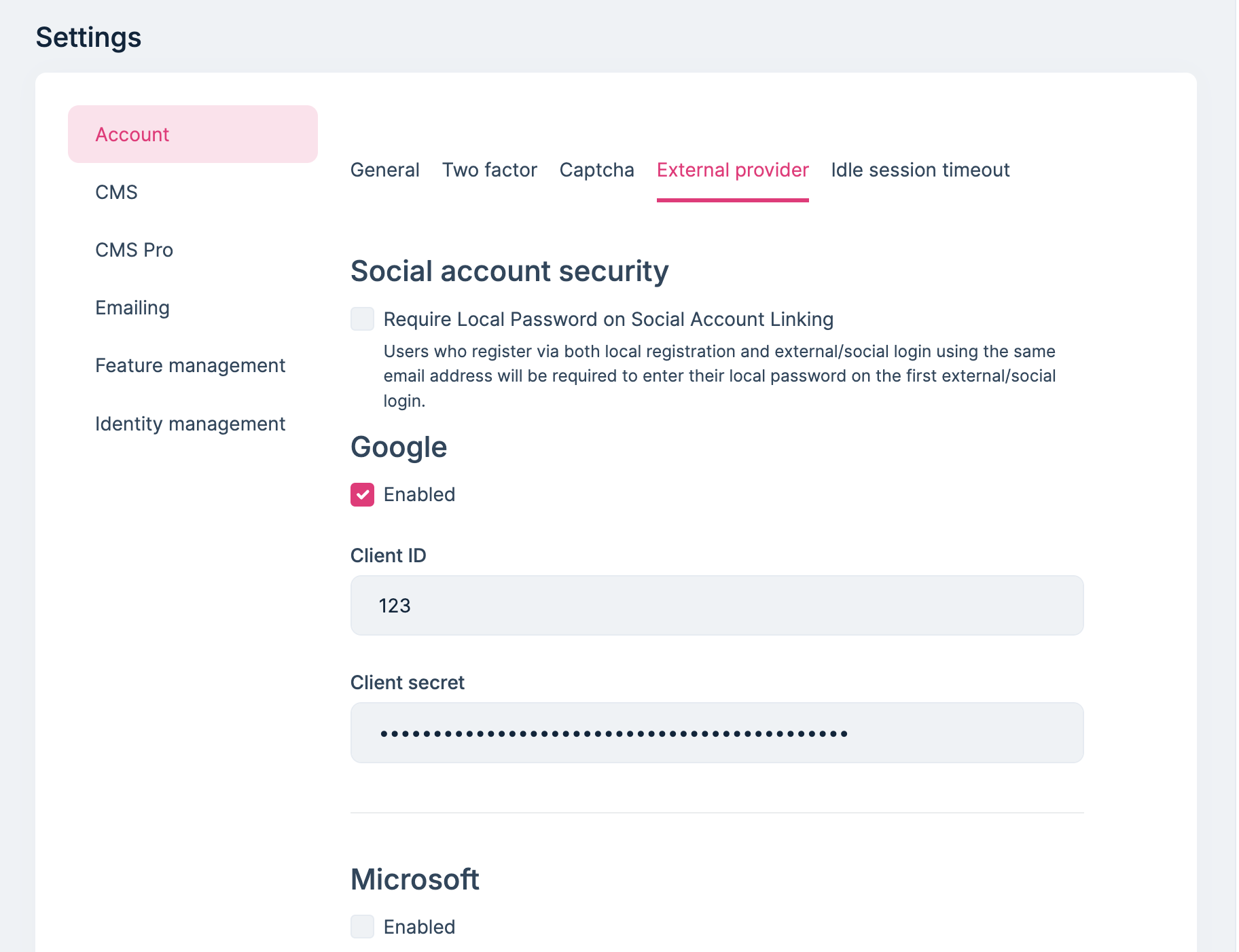
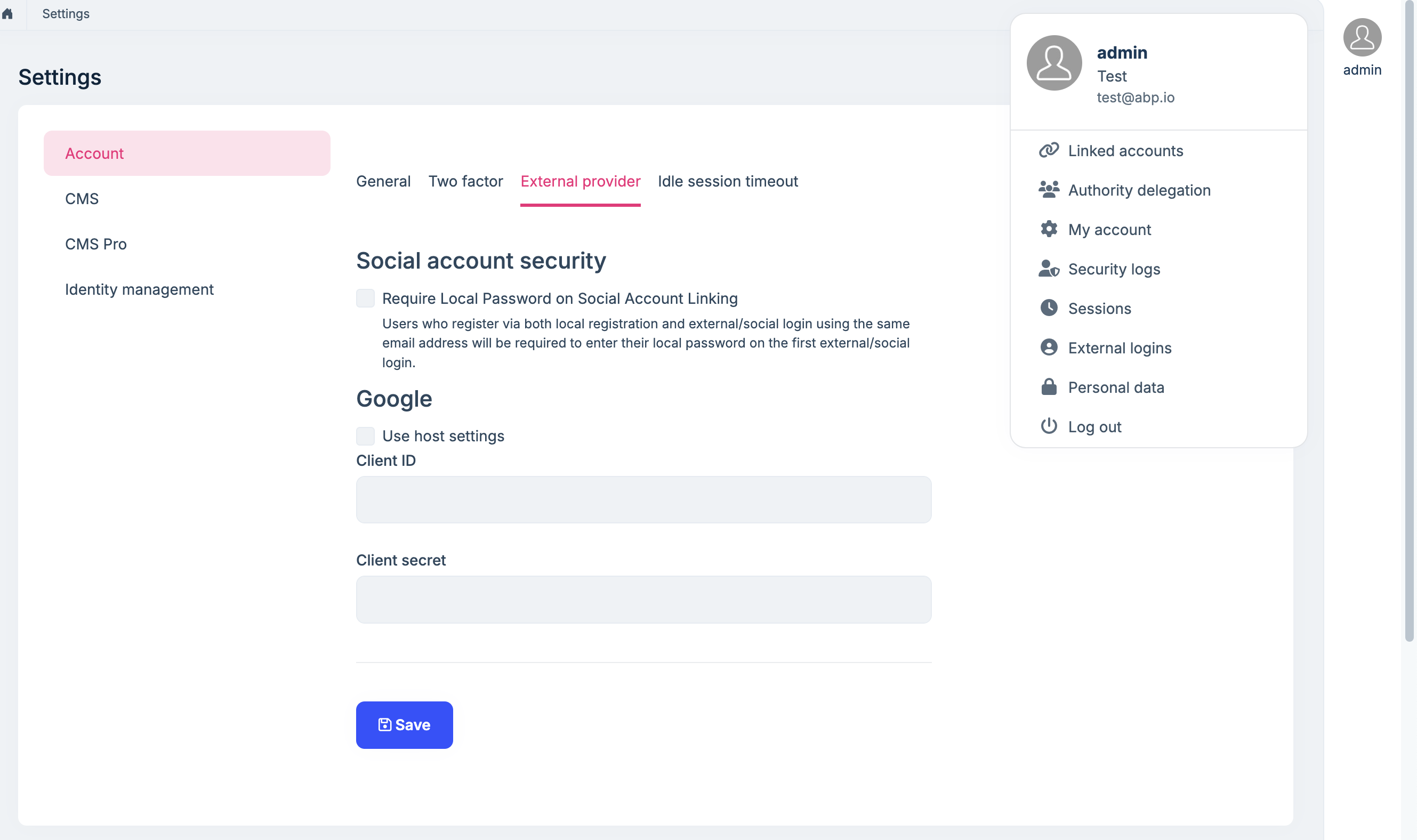
- Enter the client ID and client secret information of the above OIDC application in the OAuth login settings of the ABP tenant and enable OAuth login (pls refer to the attached file).
- Log out.
- Access to the ABP tenant login screen, the SSO option does not appear. Even when logging into the ABP tenant using a user assigned to the OIDC application, it logs in to the ABP tenant directly without going through Okta.
- On the "External logins" screen, the external provider is not displayed, and when pressing the "New external login" button, the message "You have no external login provider to sign in" appears.
When OAuth login is enabled, we would like to achieve the following, but is there any additional configuration required?
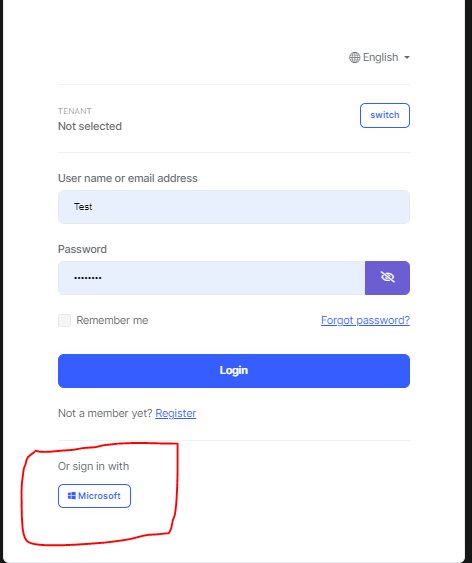
- Display the SSO option on the ABP tenant login screen.
- If the above is not possible, automatically authenticate with the IdP (e.g., Okta) when OAuth login is enabled (such as displaying the IdP login screen and processing authentication).
-----------------------
10 Answer(s)
-
0
Hi, we are currently testing according to your steps and let you know asap.
Best regards.
-
0
hi
You misunderstand the
OAuth Resource Owner Password (ROP) External login ProviderSee https://abp.io/docs/latest/modules/identity/oauth-loginIf you want to see a login option on the Login/Register page, you can add your Okta as an external social login provider.
See https://abp.io/docs/latest/modules/account-pro#manage-external-logins
-
0
Hi, I see. When adding a new external login such as Okta, beyond the pre-installed options like Twitter, Google, and Microsoft, it seems necessary to modify the source code as described in this manual. Is my understanding correct? If so, I think this is not a good experience. Since external logins often need to be added based on customer needs, it would be preferable to dynamically add new external logins without modifying the source code.
Additionally, we would like to enable external login settings at the tenant level rather than at the host tenant level. Is there a way to achieve this?
-
0
hi
it seems necessary to modify the source code as described in this manual. Is my understanding correct?
Yes. You have to add a new package and change the code. because different social login use different nuget package.
Additionally, we would like to enable external login settings at the tenant level rather than at the host tenant level. Is there a way to achieve this?
Once a new external login is added, different
client id/client secretcan be set for the host and tenant. -
0
Once a new external login is added, different client id/client secret can be set for the host and tenant.
In our SaaS services built on ABP, each customer (company) uses one tenant. We have the following requirements for external providers:
-Customer A tenant wants to enable only Okta
-Customer B tenant wants to enable Google and Microsoft
-Customer C tenant does not want to enable any external providers
If we set up an external provider in the host tenant, the above requirements cannot be met, so we would like to be able to set it at the tenant level. If there is a way to do this, please let me know.
-
0
hi
- Customer A tenant wants to enable only Okta
- Customer B tenant wants to enable Google and Microsoft
- Customer C tenant does not want to enable any external providers
You can override the
AuthenticationSchemeProviderto remove external login based on the current tenant.using System.Collections.Generic; using System.Linq; using System.Threading.Tasks; using JetBrains.Annotations; using Microsoft.AspNetCore.Authentication; using Microsoft.Extensions.Options; using Volo.Abp.DependencyInjection; using Volo.Abp.MultiTenancy; namespace Volo.Abp.Account.Public.Web; [Dependency(ReplaceServices = true)] [ExposeServices(typeof(IAuthenticationSchemeProvider))] public class MyAuthenticationSchemeProvider : AuthenticationSchemeProvider, ISingletonDependency { private readonly ICurrentTenant _currentTenant; public MyAuthenticationSchemeProvider([NotNull] [ItemNotNull] IOptions<AuthenticationOptions> options, ICurrentTenant currentTenant) : base(options) { _currentTenant = currentTenant; } protected MyAuthenticationSchemeProvider([NotNull] [ItemNotNull] IOptions<AuthenticationOptions> options, [NotNull] IDictionary<string, AuthenticationScheme> schemes, ICurrentTenant currentTenant) : base(options, schemes) { _currentTenant = currentTenant; } public override async Task<IEnumerable<AuthenticationScheme>> GetAllSchemesAsync() { var schemes = (await base.GetAllSchemesAsync()).ToList(); if (_currentTenant.Name == "TenantA") { schemes.RemoveAll(x => x.Name == "AzureOpenId"); } if (_currentTenant.Name == "TenantB") { schemes.RemoveAll(x => x.Name == "AzureOpenId"); schemes.RemoveAll(x => x.Name == "Google"); } return schemes; } } -
0
We will add an option inthe tenant side to enable/disable it in the next version.
-
0
Thank you for your reply. If each tenant could dynamically add, enable, and disable external providers via the UI without modifying the source code, that would be extremely helpful.
-
0
Hi, I have some additional questions. Should I create a new ticket for them, or is it fine to ask in this ticket?
- Does ABP support SSO via SAML on each tenant? If it is not supported, how should we proceed if we want to implement SAML SSO ourselves? Also, are there any plans to support SAML in the future?
- In ABP's recommended best practices, what are the differences in use cases (best practices) between OAuth login and External logins (social login) on each tenant?
-
0
Hi We will add new setting in 9.2 version.
Please create a new question.
Thanks.