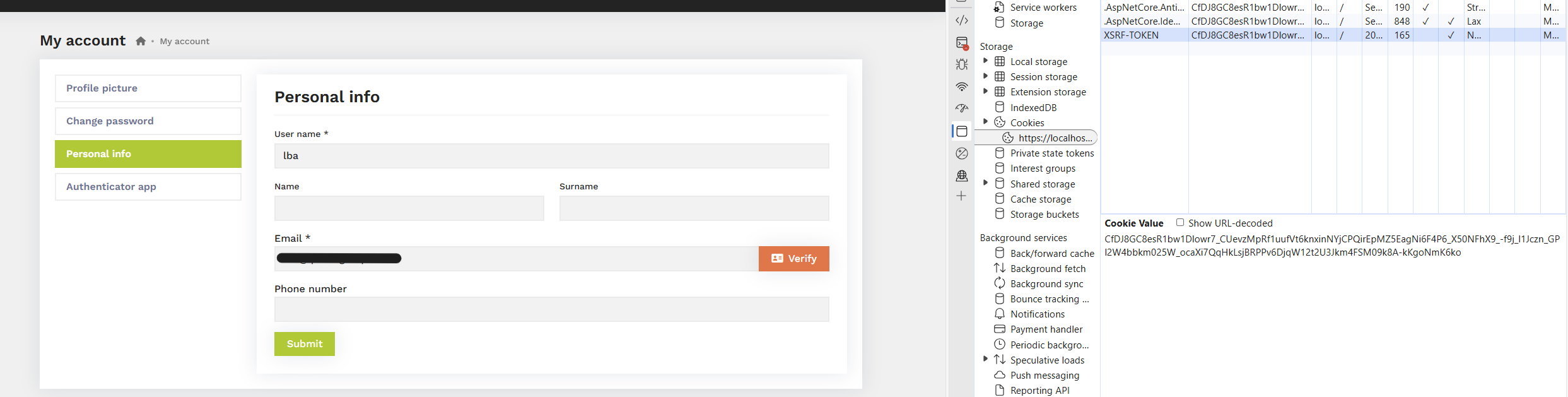
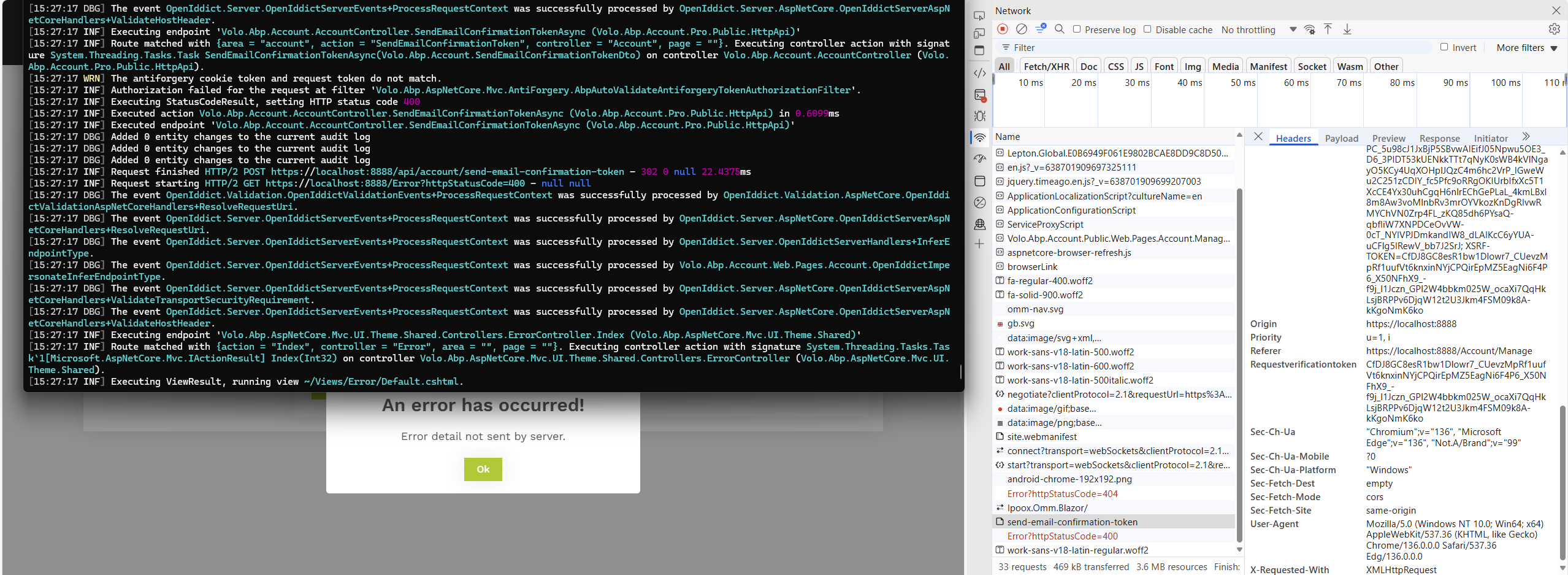
We're having a problem with antiforgery when trying to verify a users email (under "/Account/Manage" -> Personal info).
The value of XSRF-TOKEN is added to request headers as value for RequestVerificationToken
But the application responds with an error and logs a warning "The antiforgery cookie token and request token do not match".
Upon retrying to request email verification, everything works as expected.
Previously, we configured AbpAntiForgeryOptions as follows:
Configure<AbpAntiForgeryOptions>(options =>
{
options.TokenCookie.SameSite = Microsoft.AspNetCore.Http.SameSiteMode.None;
options.TokenCookie.SecurePolicy = Microsoft.AspNetCore.Http.CookieSecurePolicy.Always;
});
Without the above code, RequestVerificationToken would not get added to request headers and email verification did not work at all.
Interestingly, the problem exists only in production environment. No errors occur in development environment.
We look forward to any input on this matter.
2 Answer(s)
-
0
Hi, setting SameSite as None is the default option (https://github.com/abpframework/abp/blob/dev/framework/src/Volo.Abp.AspNetCore.Mvc/Volo/Abp/AspNetCore/Mvc/AntiForgery/AbpAntiForgeryOptions.cs#L53-L60). So, you can leave it as it is for cross-site access.
As far as I understand, after the first request you are able to get the verification code. So, it seems by the time your JS reads
XSRF-TOKENand adds it to the header, the browser hasn't yet attached the freshly issued cookie to the request, so the tokens don't match. On your retry, the cookie is already present and everything works as expected.Maybe you can apply the followings:
- Set samesite as
Lax:SameSite.Laxinstead ofSameSite.None(With None+Secure, some browsers hold off on sending the cookie until after a round-trip establishes that the site is “good.” This can cause the delay maybe) - Apply forwarded headers:
Configure<ForwardedHeadersOptions>(options => { options.ForwardedHeaders = ForwardedHeaders.XForwardedFor | ForwardedHeaders.XForwardedProto; });Regards.
- Set samesite as
-
0
Hello EngincanV,
setting SameSite to something other than "None" resolved our issue. Thanks!