Can you please provide your solution structure and build logs here?
Does dotnet CLI say Menucontributor not found? Or you did not found it?
build operation doesn't look for a specific file unless you define its name in the csproj file. You can check the related project's csproj file if there is a pbysMenuContributor.cs file defined.
Or like other hand, if you cannot find it in the project, you can create a new one that implements the IMenuContributor and configure it in the Module.cs file
Configure<AbpNavigationOptions>(options =>
{
options.MenuContributors.Add(new MyProjectMenuContributor());
});
Hi,
I found its registration like below:
await context.ServiceProvider
.GetRequiredService<IBackgroundWorkerManager>()
.AddAsync(context.ServiceProvider.GetRequiredService<ExpiredAuditLogDeleterWorker>());
It works as background worker.
It resolves ExpiredAuditLogDeleterOptions in the main ExpiredAuditLogDeleterWorker service. And that option class is like below:
public class ExpiredAuditLogDeleterOptions
{
/// <summary>
/// Default: Everyday once.
/// </summary>
public int Period { get; set; } = (int)TimeSpan.FromDays(1).TotalMilliseconds;
}
Unfortunately, there is no a CRON-like condiguration that identifies exact time to work right now. Here a suggestion about how you can do it manually:
dotnet add package Cronos
[Dependency(ReplaceServices = true)]
[ExposeServices(typeof(ExpiredAuditLogDeleterWorker))]
public class MyCustomExpiredAuditLogDeleterWorker : ExpiredAuditLogDeleterWorker
{
// Your expression here:
public const string Expression = "0 23 * * *";
public MyCustomExpiredAuditLogDeleterWorker(
AbpAsyncTimer timer,
IServiceScopeFactory serviceScopeFactory,
IOptions<ExpiredAuditLogDeleterOptions> options) : base(timer, serviceScopeFactory, options)
{
// Cron expressions resolution is 1 minute, so we need to set the period to 1 minute
// Each minute, the worker will check if there are any expired audit logs and delete them
timer.Period = (int)TimeSpan.FromMinutes(1).TotalMilliseconds;
}
protected override async Task DoWorkAsync(PeriodicBackgroundWorkerContext workerContext)
{
var cronExpression = CronExpression.Parse(Expression);
var now = DateTimeOffset.UtcNow;
var nextOccurrence = cronExpression.GetNextOccurrence(now.AddSeconds(-1), TimeZoneInfo.Utc);
// If the next occurrence is within this minute, run the job
if (nextOccurrence.HasValue &&
nextOccurrence.Value > now.AddSeconds(-60) &&
nextOccurrence.Value <= now)
{
await base.DoWorkAsync(workerContext);
}
// else: do nothing, wait for the next tick
}
}
It seems it's better to use background jobs instead background worker, but it's what it's right now. You can use this workaround and I'll inform the ABP team about it. They may want to make an enhancement
Hi,
Our @designteam will answer on this topic
Hi,
When you create a new project, it it's not tiered, they're configured to host IdentityServer in the same application. So they use their own as IdentityServer. You'll need to remove OpenIdDict packages from the application and add configure it to use your existing authentication server.
You can create a new Tiered project and check how it's differently configured to consume a separate AuthServer, you can remove .AuthServer, configure the appsettings.json to use your existing AuthServer and sztart using.
Here how you can process manually:
Volo.Abp.Http.Client.IdentityModel.Web package is installed,appsettings.json: "AuthServer": {
"Authority": "https://localhost:44385",
"RequireHttpsMetadata": true,
"ClientId": "AbpSolution2741_Web",
"ClientSecret": "1q2w3e*"
},
Hi,
It might be false-positive detection but we have to be sure about it. Can you export a detailed report from this threat detection? Or can you share Quarantined Files? It'll help to determine the real problem or behaviour of the application that triggers anti-virüs programs
Hi,
The best practice for server-to-server communication mostly depends on security, scalability, and maintainability requirements. Instead of using the default admin user you can use separate users and specific permissions for your each application. So you can easily track in audit logs and separately manage their permissions etc. You can use dedicated account for each service.
Instead of using an admin user account, it's recommended to use OAuth 2.0 Client Credentials Flow, where the server authenticates itself using a client ID and secret rather than a user’s credentials. Since ABP does not implement OpenID flows itself and uses OpenIddict open source library, you can check its own documentation from here: https://documentation.openiddict.com/guides/choosing-the-right-flow.html
The current approach is not anti-pattern or a bad-practise, but as an alternative we recommend using Integration Service in ABP Framework but it'll bring some extra development cost, you'll create similar integration services for all of your application services. Against this development cost, you can consume your existing app services as an user from your other servers.
There is another alternative approach which is Api-Key approach. This is widely used in the web, but ABP doesn't have a built-in api-key management system, you can use hard-coded API-keys and validate them in a middleware. But this brings much more development cost since ABP doesn't help you on this topic.
Hi,
does it have anything to do with the fact that im using the basic ui template?
I posted an article about that topic, you may want to follow this one for the basic theme: https://abp.io/community/articles/you-do-it-wrong-customizing-abp-login-page-correctly-bna7wzt5#gsc.tab=0
Hi,
My suggestion will be to use Integration Service by default but it seems you already have your endpoints, and you'll consume your existing endpoints and you won't create a new services for those operations.
Here is how you can approach:
YourProjectName.HttpApi.Client.ConsoleTestApp under tests folder. You can check that implementation. It's configured to authenticate itself automatically with a user and it uses token on each request sent over application services. You see credentials for this client in appsettings.json: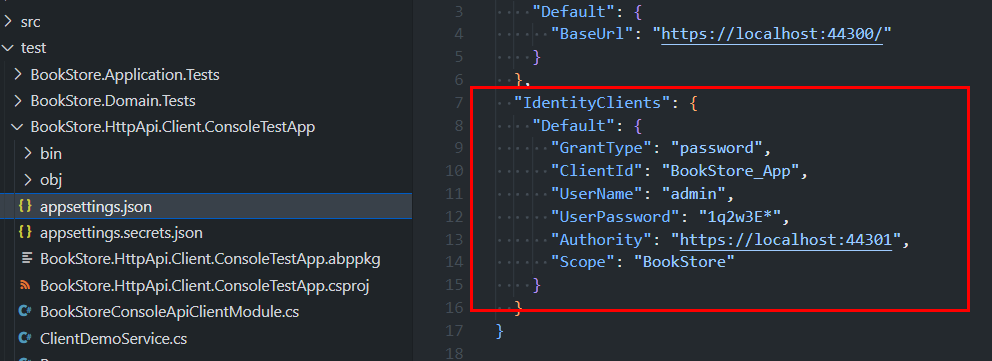
It directly inject client-proxy implementation of an app service interface and consumes APIs like it's admin user (or which user you define in the appsettings.json)
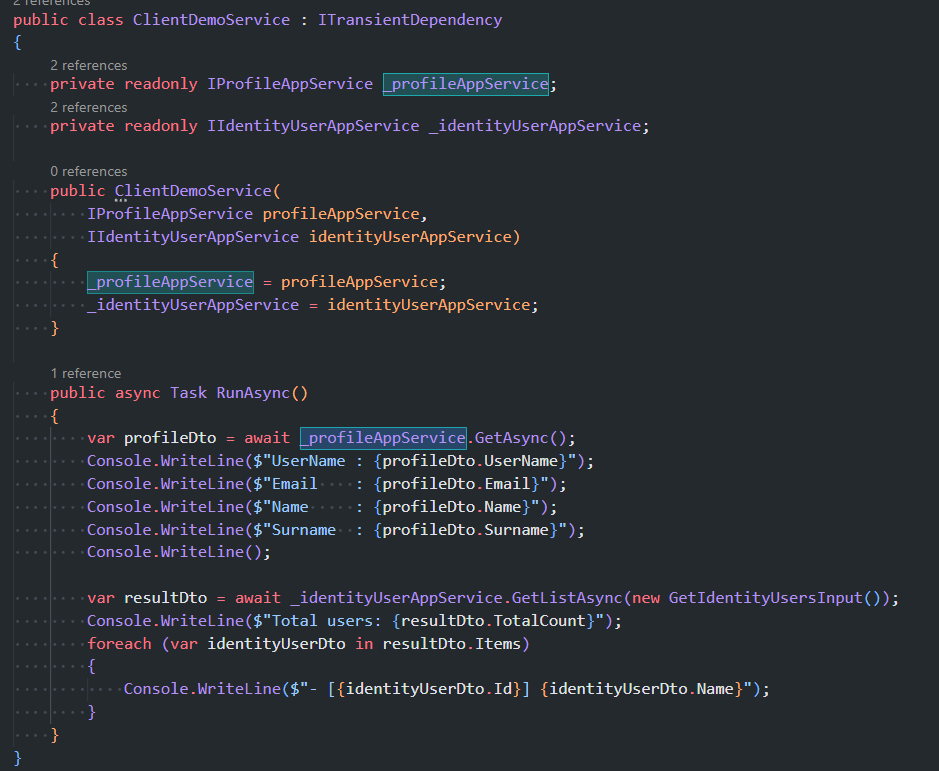
This might help. Can you check this logic. If your solution doesn't have this application, you can try creating it with the latest version of ABP to check this test application
Hi,
You can define permissions to your clients without requiring an account token.
https://abp.io/docs/latest/framework/fundamentals/authorization#permission-value-providers
ABP has ClientPermissionValueProvider implementation by default and you can give permissions to specific client. ClientId will be retrieved from AbpClaimTypes.ClientId claim.
Or, if you wish you can have a custom implementation:
public class SystemAdminPermissionValueProvider : PermissionValueProvider, ITransientDependency
{
public SystemAdminPermissionValueProvider(IPermissionStore permissionStore)
: base(permissionStore)
{
}
public override string Name => "SystemAdmin";
public async override Task<PermissionGrantResult>
CheckAsync(PermissionValueCheckContext context)
{
// Anything you want to check
if (context.Principal?.FindFirst("User_Type")?.Value == "SystemAdmin")
{
return PermissionGrantResult.Granted;
}
return PermissionGrantResult.Undefined;
}
}
-or-
If permissions and claims is not good at your case, you can check IntegrationServices. Integration services are built for inter-service communication and cannot be consumed from clients.You can check the documentation about more information and use-cases: https://abp.io/docs/latest/framework/api-development/integration-services
Hello @k-s-c,
Thanks for reaching out and providing such a clear description of your setup and the issue you're facing. This "Unauthorized" error in a tiered application with an API Gateway is a classic scenario, and we can definitely help you debug it.
Based on your description, the problem lies in the authentication flow between your Public Gateway and your Host API, specifically concerning JWT token validation when requests are proxied from HTTPS to HTTP.
Let's break down the potential causes and how to diagnose them:
1. RequireHttpsMetadata = false (Revisit this carefully!)
You've correctly identified RequireHttpsMetadata = false on the JwtBearerOptions as a potential fix for the Host API. This setting is crucial when your IdentityServer (which is your Host API in this case, acting as the token issuer) issues tokens with an iss (issuer) claim that is an HTTPS URL, but the token is then validated by an API (your Host API, when accessed via the gateway) that receives the request over HTTP.
Action:
Verify the iss claim: Inspect a JWT token issued by your Host API (you can get one from the working Swagger UI on the Host API, or by logging in from your MVC app). What is the value of the iss claim? If it's https://your-gateway-domain/, and your Host API is receiving requests over http://localhost:port/, then RequireHttpsMetadata = false is indeed necessary on the Host API's AddJwtBearer configuration.
Double-check placement: Ensure RequireHttpsMetadata = false is applied correctly within the ConfigureServices method of your Host API:
C#
context.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme)
.AddJwtBearer(options =>
{
options.Authority = "https://your-gateway-domain/"; // Or your Host API's public URL if it's directly accessible for discovery
options.RequireHttpsMetadata = false; // <-- This is the key
options.Audience = "YourProjectName_Host"; // Or the audience of your Host API
});
Note: options.Authority should point to the public URL where the IdentityServer discovery document can be found, which would typically be your Public Gateway's HTTPS URL.
2. Audience Mismatch
Both the Public Gateway (if it validates) and the Host API must be configured to accept the correct audience (aud claim) in the JWT token. The audience for your Host API is typically its own unique identifier (e.g., "YourProjectName_Host").
Action:
Check OpenIddict configuration: In your Host API's PreConfigureServices, where you configure OpenIddict (ABP's default IdentityServer), ensure the client configuration for your Web MVC app (and any other clients) requests the correct scope/audience:
C#
PreConfigure<OpenIddictBuilder>(builder =>
{
builder.AddValidation(options =>
{
options.AddAudiences("YourApplicationName");
options.UseLocalServer();
options.UseAspNetCore();
});
});
Check client applications: Verify that your Web MVC application (or any client obtaining a token) is requesting the "YourProjectName_Host" scope.
Check appsettings.json in the DbMigrator: ABP layered template has data seeding logic with DbMigrator. Make sure your credentials is correct in the appsettings.json inside YourProjectName.DbMigrator folder and then execute DbMigrator once when your credentials ready to publish. ⚠️ The production database should be properly migrated
Check OpenIddictDataSeedContributor if any change requiremens: In the Domain project you'll see OpenIddict\OpenIddictDataSeedContributor.cs file that seeds all the openiddict configuration to the database. Check there and make sure all of your clients are added there.
3. Swagger UI and Token Injection
When using Swagger UI on the Public Gateway, the "Authorize" button injects the bearer token. The issue here might be how Swagger on the Gateway handles this, or if the token it's using is somehow different or malformed when forwarded.
Action:
Authorization header. Is the bearer token present? Is it the correct token?4. Logging (Your Best Friend!)
Enable detailed logging on both your Public Gateway and your Host API. Look for logs related to authentication, JWT validation, and authorization.
Action:
Configure Serilog (or default logging): Ensure appsettings.json has sufficient logging levels:JSON
"Serilog": {
"MinimumLevel": {
"Default": "Information",
"Override": {
"Microsoft": "Warning",
"System": "Warning",
"OpenIddict": "Debug", // Very useful for token validation issues
"Microsoft.AspNetCore.Authentication": "Debug", // Also very useful
"Volo.Abp": "Information"
}
}
}
Examine logs: Look for messages like "token validation failed," "issuer not found," "invalid audience," or "signature validation failed."
Troubleshooting Steps (Order of operations I'd recommend):
jwt.io.
iss (issuer), aud (audience), and exp (expiration) claims?Authorization).Example Scenario and Solution:
Often, the problem is that the Host API is configured to expect Authority = "https://public-gateway-domain/" (because that's where the discovery document is publicly available), but it's receiving requests over HTTP internally (from the gateway). In this case, RequireHttpsMetadata = false is critical on the Host API's JwtBearerOptions.
Let me know the results of these checks, especially the network tab analysis and any relevant log messages. With more details, we can narrow down the exact cause.
Best regards,

