Hi, I'm trying to generate the C# API client proxy code with included DTOs. I've tried it both with and without the '--without-contracts' parameter, but the DTO classes are still not being generated
Could you please help us check?
Hi, we are using Identity Server 4 and have a custom claim called 'institution_id,' which we have included in the access token by adding it to the ApiResourcesClaims.
However, this claim does not appear in the id_token, and we need it to be included. Any customization needed to achieve this?
Your help would be greatly appreciated.
Hi, I tried to add the hangfire background job to our identity server, but I encountered an issue that no active servers in the hangfire, below is the screenshot:
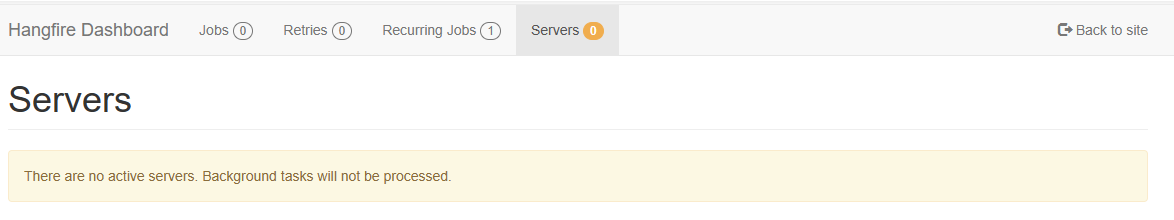
and here is the background job module:
[DependsOn(
typeof(AbpBackgroundJobsAbstractionsModule),
typeof(AbpBackgroundJobsHangfireModule)
)]
public class IdentityServerBackgroundJobsModule : AbpModule
{
public override void ConfigureServices(ServiceConfigurationContext context)
{
var configuration = context.Services.GetConfiguration();
var connectionString = configuration.GetConnectionString("Default");
context.Services.AddHangfire(config =>
{
config.UseSqlServerStorage(connectionString, new Hangfire.SqlServer.SqlServerStorageOptions()
{
SchemaName = "Hangfire"
});
});
}
public override void OnApplicationInitialization(ApplicationInitializationContext context)
{
var app = context.GetApplicationBuilder();
var configuration = context.GetConfiguration();
app.UseHangfireDashboard();
ConfireHangfireJobs(configuration);
}
private void ConfireHangfireJobs(IConfiguration configuration)
{
// remove all the jobs if exist
using (var connection = JobStorage.Current.GetConnection())
{
foreach (var recurringJob in StorageConnectionExtensions.GetRecurringJobs(connection))
{
RecurringJob.RemoveIfExists(recurringJob.Id);
}
}
// add new job
if (Convert.ToBoolean(configuration["RecurringJobs:HousekeepingJob:IsActive"]))
{
RecurringJob.AddOrUpdate<HousekeepingJob>(s => s.ExecuteAsync(), configuration["RecurringJobs:HousekeepingJob:CronSchedule"]);
}
}
}
Any help would be greatly appreciated.
Hi, We want to try the File Management module in ABP commercial demo site but the "Upload Files" does not response when I clicked it.
https://commercial-demo.abp.io/file-management
Anyone can help us check?
Hi, we received a pen test finding indicating that we need to enable the 'Secure' flag for the '.AspNetCore.Culture' cookie:
I have tried to enable by adding this code but it does not work:
Configure<CookiePolicyOptions>(options =>
{
options.Secure = CookieSecurePolicy.Always;
});
Configure<AntiforgeryOptions>(options =>
{
options.Cookie.SecurePolicy = CookieSecurePolicy.Always;
});
could you please assist us on this request?
Hi, we got a code scan finding on the method below in abp.js in identity server:
abp.utils.setCookieValue = function (key, value, expireDate, path) {
var cookieValue = encodeURIComponent(key) + '=';
if (value) {
cookieValue = cookieValue + encodeURIComponent(value);
}
if (expireDate) {
cookieValue = cookieValue + "; expires=" + expireDate.toUTCString();
}
if (path) {
cookieValue = cookieValue + "; path=" + path;
}
document.cookie = cookieValue;
};
The web application's function method creates a cookie, at line 623 of wwwroot/libs/abp/core/abp.js, and returns it in the response. However, the application is not configured to automatically set the cookie with the "httpOnly" attribute, and the code does not explicitly add this to the cookie.
I understand that the "HttpOnly" attribute cannot be set for a cookie using client-side JavaScript. However, I would like to request information about the cookies generated by the method in identity server, including their purpose and whether they contain any sensitive information.
Thank you.
Hi, our application needs to expose an encryption key in JWKS URL for the other party using it to encrypt their data before returning to us, and we have implemented it in IdentityServer, below is how the JWKS URL response look like:
{
"keys": [
{
"kty": "EC",
"use": "sig",
"kid": "esj_keyid",
"alg": "ES256",
"x": "nLrNw5uYtDmFjCTk0wOlukLil3gJyCEYYl5Seat0AXM",
"y": "OIgBQXQFSdvmnOFa59MTQyHhyy6t17yNIbbOFKJdQTw",
"crv": "P-256"
},
{
"kty": "EC",
"use": "enc",
"kid": "6HFIeNOix6zxe2En3bjhZJBX78OY0IG8u1KU41HeNoU",
"alg": "ECDH-ES+A192KW",
"x": "nLrNw5uYtDmFjCTk0wOlukLil3gJyCEYYl5Seat0AXM",
"y": "OIgBQXQFSdvmnOFa59MTQyHhyy6t17yNIbbOFKJdQTw",
"crv": "P-256"
}
]
}
I tried the code below, but it did not succeed in OpenIdDict:
PreConfigure< OpenIddictServerBuilder >(builder =>
{
// get ECDSA certificate
var ecdsaCertificate = CertificateHelper.GetCertificate(configuration["Key:ThumbPrint"]);
ECDsaSecurityKey ecdsaCertificatePublicKey = new ECDsaSecurityKey(ecdsaCertificate.GetECDsaPrivateKey());
// add signing key
builder.AddSigningKey(new ECDsaSecurityKey(ecdsaCertificate.GetECDsaPrivateKey()));
// add encryption credentials
var encryptionKey = JsonWebKeyConverter.ConvertFromECDsaSecurityKey(ecdsaCertificatePublicKey);
encryptionKey.KeyId = "encryption_key_id";
encryptionKey.Use = JsonWebKeyUseNames.Enc;
builder.AddEncryptionCredentials(new EncryptingCredentials(encryptionKey, SecurityAlgorithms.EcdsaSha256, "ECDH-ES+A192KW"));
});
Any idea how to do it?
Hi, understand that IdentityServer4 has reached its End of Support (EOS) date as of December 13th, 2022. I am wondering if you will continue to provide security fixes for IdentityServer4 in your latest version. If so, how long do you plan to provide this support for IdentityServer4?
Check the docs before asking a question: https://docs.abp.io/en/commercial/latest/ Check the samples, to see the basic tasks: https://docs.abp.io/en/commercial/latest/samples/index The exact solution to your question may have been answered before, please use the search on the homepage.
If you're creating a bug/problem report, please include followings:
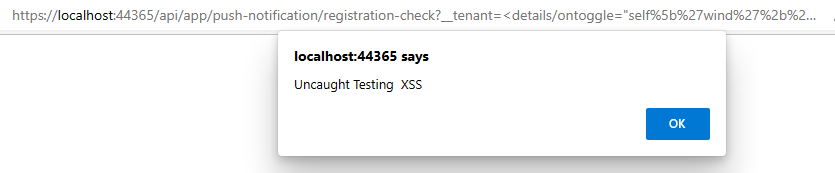
Hi, a cross-site scripting issue has been flagged out in our project by penetration test team. This vulnerability is related to "__tenant" parameter in query string:
Subject:
Reflected Cross-Site Scripting (XSS)
https://<masked url>/api/* [GET parameter: __tenant]
https://<masked url>/identity/* [GET parameter: __tenant]
Description:
Reflected XSS occurs when malicious JavaScript code is supplied in a user’s request and returned back to them for
execution within their browser in the context of the website itself. This allows an attacker to inject code which is executed
by legitimate users when they are tricked into opening a malicious link or visiting a site under an attacker’s control. This
allows an attacker to perform unauthorised actions in the application on behalf of legitimate users or spread malware via
the application.
The __tenant parameter used in the identified subjects is vulnerable to XSS attacks. An example is demonstrated below:
Attached file is the screenshot that I have tested in my local:
Hi, I am unable to create new post, keep getting "access has been blocked"

