0
rexhxiao created
4 Answer(s)
-
0
- Solution
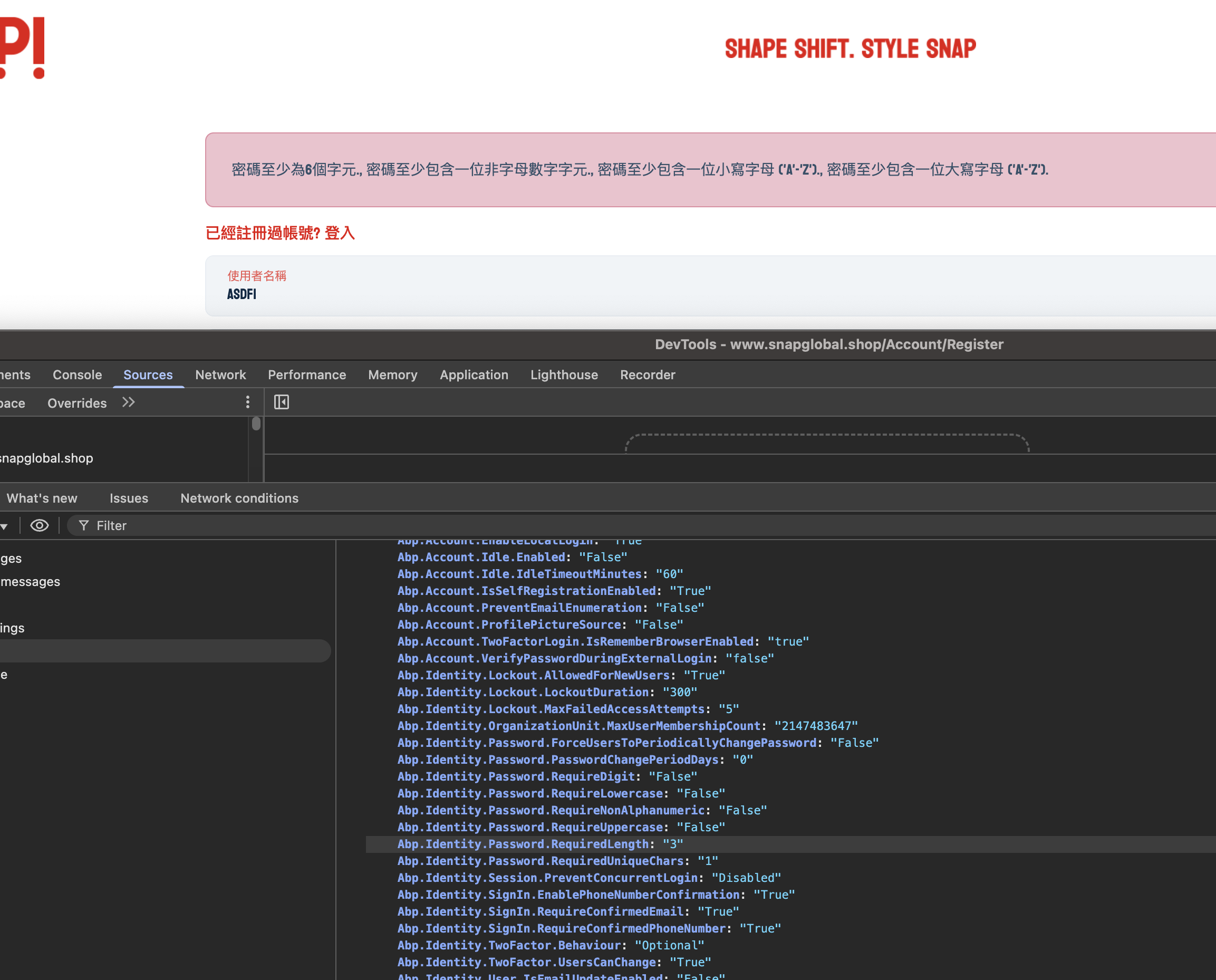
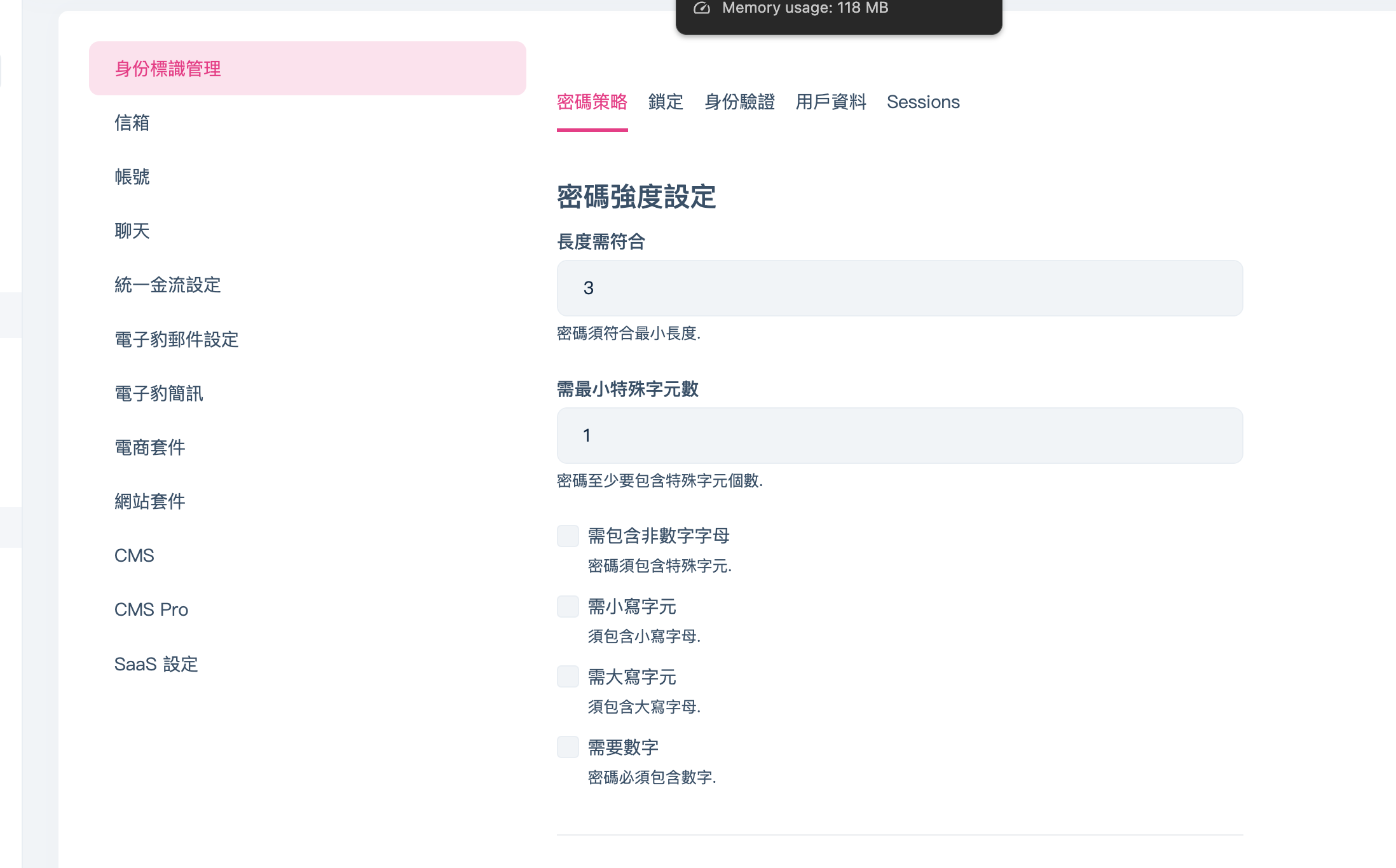
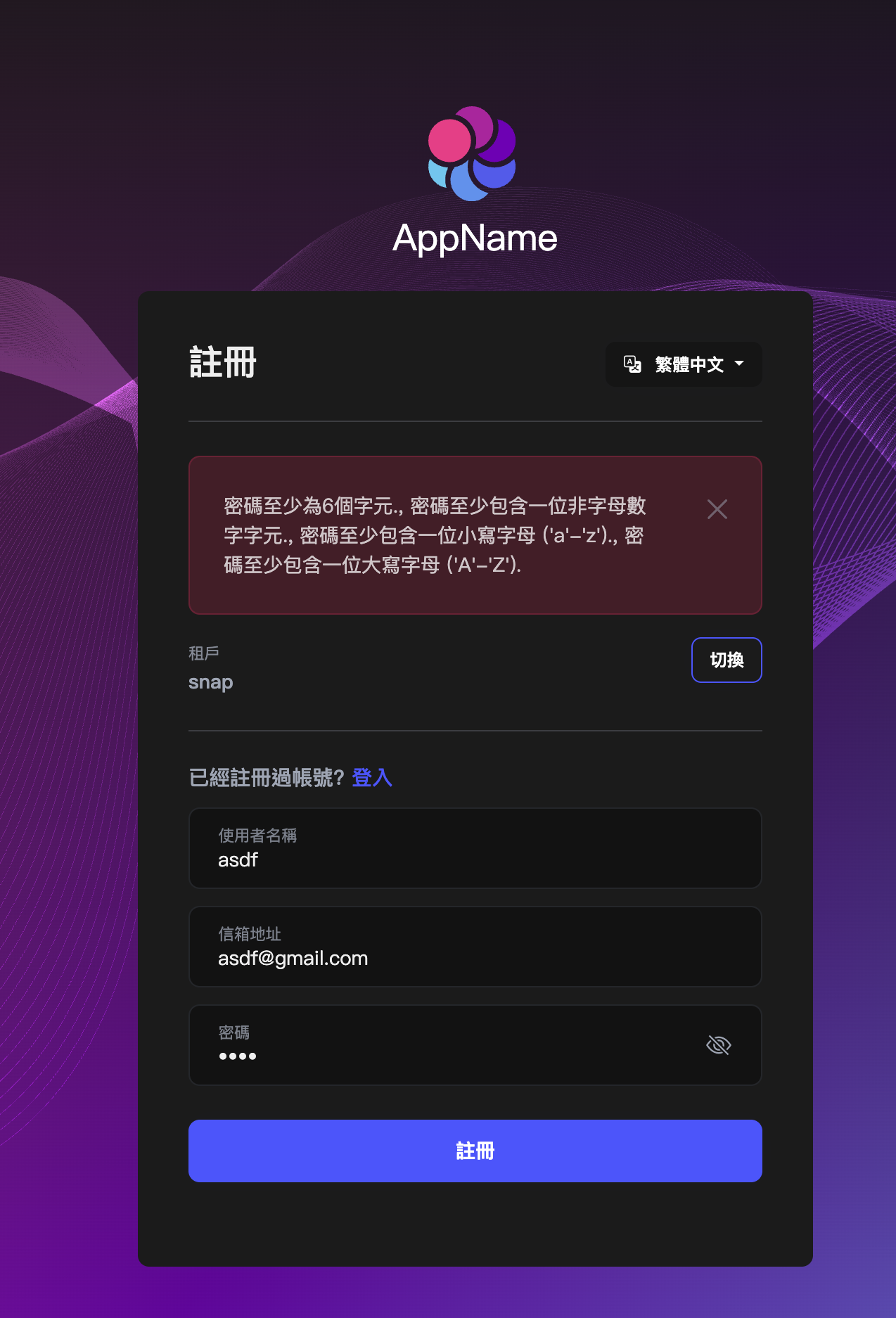
Reason: The client (Login/Register/ChangePassword pages) adds its own validators. If you lower Identity password requirements on the server (e.g., RequiredLength = 3), but the UI still shows “min 6” (or other rules), it means the client-side validators are not refreshed or they are hard-coded/defaulted.
Fix (Angular UI):
- Make sure the password rules are coming from the dynamic application configuration and not hard-coded. Update ABP Angular packages to the latest compatible version.
- Run:
- yarn upgrade @abp/ng.core @abp/ng.account.core @abp/ng.account @volo/abp.ng.identity.config
- Delete node_modules and yarn.lock (or package-lock.json) and reinstall.
- Run:
- Ensure the Register/ChangePassword forms use the validators provided by @volo/abp.ng.identity.config (or read them from getApplicationConfiguration) instead of a fixed Validators.minLength(6). Any local form code that sets Validators.minLength(6) must be changed to use the value from configuration (identity.password.requiredLength).
- After changing settings at runtime, refresh application configuration so the UI gets new rules. A full page reload always works. In SPA scenarios where you change settings without reload, reinitialize CurrentApplicationConfiguration on the client after saving settings.
- Make sure the password rules are coming from the dynamic application configuration and not hard-coded. Update ABP Angular packages to the latest compatible version.
Fix (MVC UI):
- Remove any hard-coded minlength attributes or model validators that conflict with IdentityOptions and bind to the IOptions<IdentityOptions>.Value.Password.RequiredLength for client validation metadata, or disable conflicting client rules.
Notes:
- Server-side validation always uses the backend settings (IdentityOptions). Even if the client lets a weak password through, the server will still reject it if it violates current rules.
- Historically, mismatches were fixed by updating the identity config package in Angular projects. If you’re on an older version, upgrade the UI packages to align with backend rules.
- Sources
- Validated:
- https://github.com/abpframework/abp
- https://abp.io/support/questions/166
- https://abp.io/support/questions/3226
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
hi
What is your project version?
I'm unable to reproduce it in a new template project.
Have you overridden any page(
Login/Register)?Thanks.
-
0
-
0
hi
What is your abp version?
Can you try to override the
RegisterModel?[Dependency(ReplaceServices = true)] [ExposeServices(typeof(RegisterModel), typeof(MyRegisterModel))] public class MyRegisterModel : RegisterModel { public MyRegisterModel( IAuthenticationSchemeProvider schemeProvider, IOptions<AbpAccountOptions> accountOptions, IAccountExternalProviderAppService accountExternalProviderAppService, ICurrentPrincipalAccessor currentPrincipalAccessor, IHttpClientFactory httpClientFactory) : base(schemeProvider, accountOptions, accountExternalProviderAppService, currentPrincipalAccessor, httpClientFactory) { } public override async Task<IActionResult> OnPostAsync() { await IdentityOptions.SetAsync(); return await base.OnPostAsync(); } }Thanks.