- Template: microservice
- Created ABP Studio Version: 1.3.2
- Current ABP Studio Version: 1.4.2
- Multi-Tenancy: Yes
- UI Framework: mvc
- Theme: leptonx
- Theme Style: system
- Theme Menu Placement: side
- Run Install Libs: Yes
- Database Provider: ef
- Database Management System: postgresql
- Mobile Framework: react-native
- Public Website: Yes
- Social Login: Yes
- Include Tests: Yes
- Dynamic Localization: Yes
- Kubernetes Configuration: Yes
- Grafana Dashboard: Yes
- Use Local References: No
- Aspire: Yes
- Optional Modules:
- GDPR
- FileManagement
- TextTemplateManagement
- AuditLogging
- Chat
- OpenIddictAdmin
- Selected Languages: English, Arabic, Chinese (Simplified), Chinese (Traditional), Czech, English (United Kingdom), Finnish, French, German (Germany), Hindi , Hungarian, Icelandic, Italian, Portuguese (Brazil), Romanian (Romania), Russian, Slovak, Spanish, Swedish, Turkish
- Default Language: English
- Create Command: abp new TavTechnologies.Treva -t microservice --ui-framework mvc --mobile react-native --database-provider ef --database-management-system postgresql --theme leptonx --skip-migrator --public-website --dont-run-bundling -no-language-management -chat -file-management
[10:04:32 INF] Request starting HTTP/1.1 GET http://treva-hangfire/api/hangfire/hangfire - null null
[10:04:36 ERR] Message contains error: 'invalid_request', error_description: 'The specified 'redirect_uri' is not valid for this client application.', error_uri: 'https://documentation.openiddict.com/errors/ID2043', status code '400'.
[10:04:36 ERR] Connection id "0HNH07SJTT7K5", Request id "0HNH07SJTT7K5:00000001": An unhandled exception was thrown by the application.
Microsoft.IdentityModel.Protocols.OpenIdConnect.OpenIdConnectProtocolException: Message contains error: 'invalid_request', error_description: 'The specified 'redirect_uri' is not valid for this client application.', error_uri: 'https://documentation.openiddict.com/errors/ID2043'.
at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.GetPushedAuthorizationRequestUri(HttpResponseMessage parResponseMessage)
at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.PushAuthorizationRequest(OpenIdConnectMessage authorizeRequest, AuthenticationProperties properties)
at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.HandleChallengeAsyncInternal(AuthenticationProperties properties)
at Microsoft.AspNetCore.Authentication.OpenIdConnect.OpenIdConnectHandler.HandleChallengeAsync(AuthenticationProperties properties)
at Microsoft.AspNetCore.Authentication.AuthenticationHandler1.ChallengeAsync(AuthenticationProperties properties) at Microsoft.AspNetCore.Authentication.AuthenticationService.ChallengeAsync(HttpContext context, String scheme, AuthenticationProperties properties) at TavTechnologies.Treva.HangfireService.TrevaHangfireServiceModule.<>c.<<OnApplicationInitializationAsync>b__2_0>d.MoveNext() in /src/TavTechnologies.Treva.HangfireService/TrevaHangfireServiceModule.cs:line 172 --- End of stack trace from previous location --- at Volo.Abp.AspNetCore.Mvc.Libs.AbpMvcLibsService.<CheckLibs>b__1_0(HttpContext httpContext, RequestDelegate next) at Microsoft.AspNetCore.Server.Kestrel.Core.Internal.Http.HttpProtocol.ProcessRequests[TContext](IHttpApplication1 application)
[10:04:36 INF] Request finished HTTP/1.1 GET http://treva-hangfire/api/hangfire/hangfire - 500 0 null 3551.7917ms
It's working on local environment but in remote environment it's giving above error and get HTTP 500.
In remote environment new Hangfire Client settings lilke below:
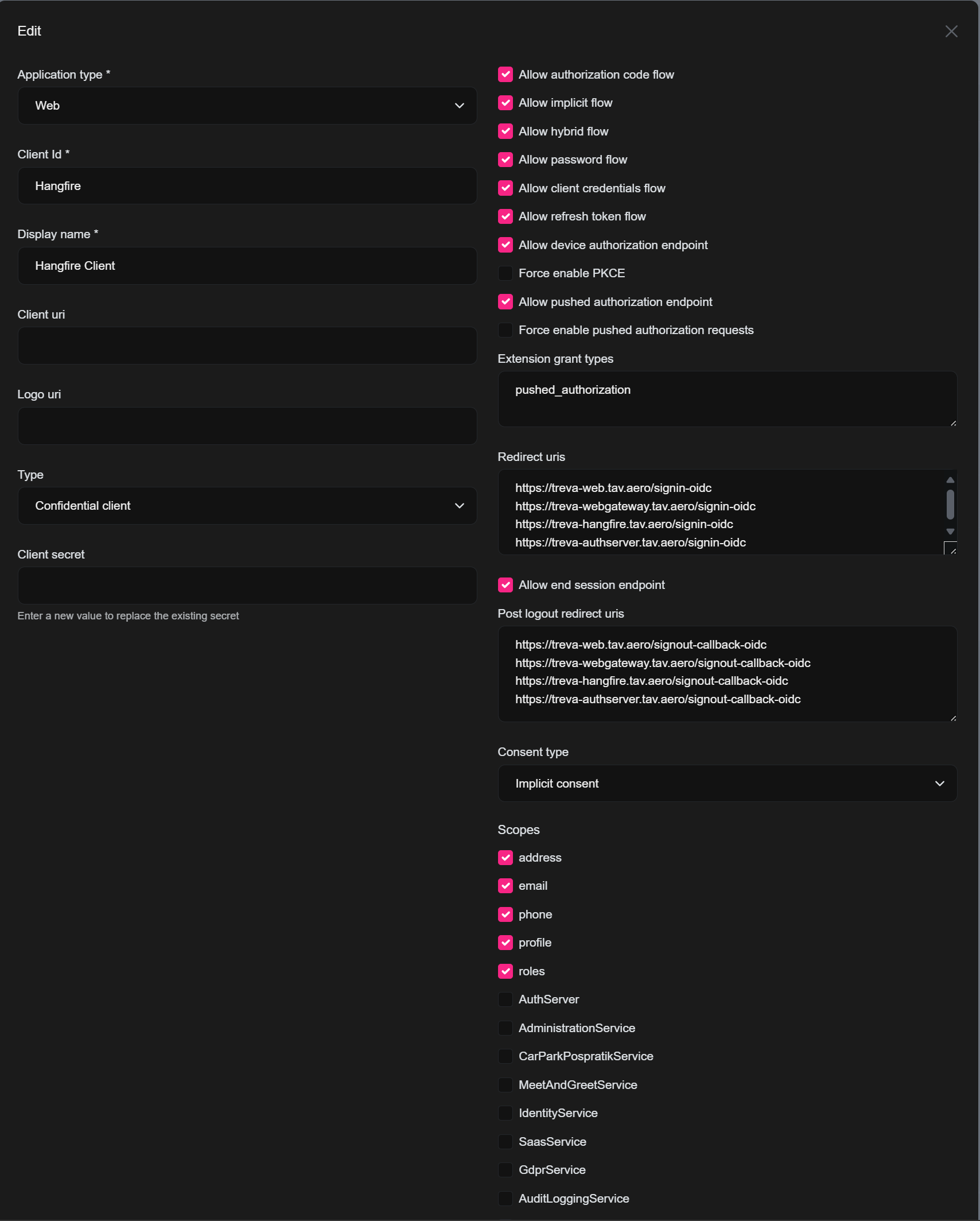
And HangfireClient creation like below
await CreateOrUpdateApplicationAsync(
name: "Hangfire",
type: OpenIddictConstants.ClientTypes.Confidential,
consentType: OpenIddictConstants.ConsentTypes.Implicit,
displayName: "Hangfire Client",
secret: "1q2w3e*",
grantTypes:
//Hybrid flow
[
OpenIddictConstants.GrantTypes.AuthorizationCode,
OpenIddictConstants.GrantTypes.Password,
OpenIddictConstants.GrantTypes.ClientCredentials,
OpenIddictConstants.GrantTypes.RefreshToken,
OpenIddictConstants.GrantTypes.Implicit,
OpenIddictConstants.GrantTypes.DeviceCode,
"pushed_authorization"
],
scopes: [.. commonScopes.Union(
[
"HangfireService"
])],
redirectUris: [$"{webClientRootUrl}signin-oidc"],
postLogoutRedirectUris: [$"{webClientRootUrl}signout-callback-oidc"]
);
webClientRootUrl= web application root url
Can you help us, please?
8 Answer(s)
-
0
- Solution Your error comes from OpenIddict rejecting the redirect_uri used by the Hangfire Dashboard OIDC challenge in your remote environment. In Kubernetes (and when services are split behind gateways/ingress), the actual callback URL that the browser hits often differs from the value you seeded for the client. You must ensure that every possible redirect URI used by the Hangfire site is registered for the Hangfire client in OpenIddict, and that you request a redirect URI that exactly matches one of them.
Do all of the following:
Register every real redirect URI used by Hangfire in the remote environment:
- If users access Hangfire via an ingress/gateway (e.g., https://treva-hangfire.tav.aero), add:
- https://treva-hangfire.tav.aero/signin-oidc
- If you also allow access via gateway/edge or different hostnames/ports, add all of them:
- https://treva-web.tav.aero/signin-oidc
- https://treva-webgateway.tav.aero/signin-oidc
- https://treva-authserver.tav.aero/signin-oidc
- Do the same for Post Logout Redirect URIs:
- https://treva-hangfire.tav.aero/signout-callback-oidc
- https://treva-web.tav.aero/signout-callback-oidc
- https://treva-webgateway.tav.aero/signout-callback-oidc
- https://treva-authserver.tav.aero/signout-callback-oidc
- If users access Hangfire via an ingress/gateway (e.g., https://treva-hangfire.tav.aero), add:
Seed the Hangfire OpenIddict client with those exact values (seed order doesn’t matter, but strings must match 1:1 with what the browser will use):
await CreateOrUpdateApplicationAsync( name: "Hangfire", type: OpenIddictConstants.ClientTypes.Confidential, consentType: OpenIddictConstants.ConsentTypes.Implicit, displayName: "Hangfire Client", secret: "1q2w3e*", grantTypes: [ OpenIddictConstants.GrantTypes.AuthorizationCode, OpenIddictConstants.GrantTypes.ClientCredentials, OpenIddictConstants.GrantTypes.RefreshToken, // Remove Password & Implicit unless you really need them; not required for server-side MVC OIDC "pushed_authorization" ], scopes: [ OpenIddictConstants.Scopes.OpenId, OpenIddictConstants.Scopes.Profile, OpenIddictConstants.Scopes.Email, OpenIddictConstants.Scopes.Phone, OpenIddictConstants.Scopes.OfflineAccess, "roles", "HangfireService" ], redirectUris: [ "https://treva-hangfire.tav.aero/signin-oidc", "https://treva-web.tav.aero/signin-oidc", "https://treva-webgateway.tav.aero/signin-oidc", "https://treva-authserver.tav.aero/signin-oidc" ], postLogoutRedirectUris: [ "https://treva-hangfire.tav.aero/signout-callback-oidc", "https://treva-web.tav.aero/signout-callback-oidc", "https://treva-webgateway.tav.aero/signout-callback-oidc", "https://treva-authserver.tav.aero/signout-callback-oidc" ] );Ensure the Hangfire Dashboard app challenges with the same authority and callback path:
- In Hangfire service (MVC), your OpenIdConnect defaults already use CallbackPath = "/signin-oidc" by convention. Do not override to something else unless you also update the client’s redirect URIs.
- If you are building your redirect using a root URL, make sure webClientRootUrl resolves to the public URL that the browser uses to reach the Hangfire Dashboard in Kubernetes (the ingress hostname), not an internal service name or localhost.
If you enabled PAR (pushed_authorization):
- Keep the client’s “Allow pushed authorization endpoint” checked and include "pushed_authorization" in extension grant types.
- Make sure the request’s redirect_uri still exactly matches a registered URI. PAR doesn’t relax redirect_uri matching.
Clear caches after seeding:
- If you use Redis/DataProtection caching for OpenIddict validation, clear Redis and restart the AuthServer so it reloads client definitions.
Common pitfalls to avoid:
- Do not point Hangfire to webClientRootUrl of your main web app unless the signin-oidc callback really returns to the main web app and you’ve registered that URI for the Hangfire client.
- Don’t mix HTTP/HTTPS. If ingress terminates TLS and you use HTTPS outside, register HTTPS URIs.
- If you changed ports/hosts between local and remote, update the client’s redirect URIs accordingly.
- Prefer removing “password” and “implicit” grant types for a confidential server-side MVC client; use authorization_code (+ PKCE if you prefer) with refresh_token.
Verify
- Open the AuthServer /.well-known/openid-configuration on the public URL to ensure the browser is using the same authority as your OpenIdConnect handler.
- Attempt login; if it fails, check AuthServer logs for “Client validation failed because '…/signin-oidc' was not a valid redirect_uri” and compare the exact string with your database values.
- Sources
- ABP OpenIddict deployment tip about allowed redirect URLs:
- https://abp.io/docs/latest/solution-templates/layered-web-application/deployment/openiddict-deployment
- Similar ABP support resolutions for “redirect_uri is not valid”:
- https://abp.io/support/questions/6031
- https://abp.io/support/questions/7051
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
hi
Please check the additional logs of the authserver website to determine which URL is invalid.
Thanks.
-
0
Hi ma,
AuthServer logs like below,
[12:31:30 INF] Request starting HTTP/1.1 POST http://treva-authserver.tav.aero/connect/par - application/x-www-form-urlencoded 667 [12:31:30 WRN] Unknown proxy: [::ffff:10.2.155.151]:51962 [12:31:30 INF] The request URI matched a server endpoint: PushedAuthorization. [12:31:30 INF] The pushed authorization request was successfully extracted: { "client_id": "Hangfire", "redirect_uri": "http://treva-hangfire/signin-oidc", "response_type": "code id_token", "scope": "openid profile address email phone roles HangfireService", "response_mode": "form_post", "nonce": "638983746900457193.MDEzMDVmZmQtYmZiNC00YmZjLWEzZGMtYWQyNGVkZDQxNmE0ZTg4OGM4NTMtYmFkYS00OTk0LWI3N2UtZDUxMTI5YjRkMzdj", "state": "CfDJ8KBhtfQcifVKv-63a2B9_LXb0UhUp5WGWbZnu7PIFLIhSwwmUa3NjGQNLRY2vWbL75wz_BArtwjLX7aez2K2J-btBUpR_qQxcZ5I7MmPvsT5e0_KNMSFBuJQ9--GwoBP3b7rIM26rcsma-bC5rTlOxwiuNs6EtiWxIB8bdq8O13Mo5HetG79fl2QAuUA9h_dVge0TSg4XjCRrmKcEvLJH1oSTgM30ED2iOJL0Y4nTO0MhUDcXzk4FPDncQjoTaKfLsEmRgjE6e159Hsxlk15VxCjTfNTbUHJ8rOlyC3m7iZXL32beBs1Zr38ifekgBeFAQ", "client_secret": "[redacted]" }. [12:31:30 INF] Client validation failed because 'http://treva-hangfire/signin-oidc' was not a valid redirect_uri for Hangfire. [12:31:30 INF] The pushed authorization request was rejected because the redirect_uri was invalid: 'http://treva-hangfire/signin-oidc'.
-
0
- Solution Your AuthServer logs show the exact mismatch:
- redirect_uri received: http://treva-hangfire/signin-oidc
- It is not present in the Hangfire client’s Redirect URIs on AuthServer.
In Kubernetes, the browser reaches the Hangfire Dashboard via the public host (ingress), but your Hangfire app is sending an internal host (treva-hangfire) in the OIDC request. OpenIddict requires an exact string match.
Apply all steps below:
Fix the redirect_uri to use the public HTTPS host of the Hangfire Dashboard
- Configure your Hangfire service OpenIdConnect options so the redirect URI is https://treva-hangfire.tav.aero/signin-oidc (or whichever public URL users actually use). Don’t use the internal K8s service name treva-hangfire.
- If you build it from webClientRootUrl, make sure webClientRootUrl is the public Hangfire URL in remote (e.g., https://treva-hangfire.tav.aero/).
Register the exact public callback(s) on the Hangfire client in AuthServer
- Redirect URIs must include the public URI(s) you will use:
- https://treva-hangfire.tav.aero/signin-oidc
- Post-logout redirect URIs similarly:
- https://treva-hangfire.tav.aero/signout-callback-oidc
- Remove internal hosts like http://treva-hangfire unless you really sign in via that URL from a browser (generally not the case).
- If Hangfire can also be reached via other public hosts, add those too. Each must match exactly.
- Redirect URIs must include the public URI(s) you will use:
Keep HTTPS everywhere
- Ensure all registered URIs are HTTPS if your ingress is HTTPS. Don’t mix HTTP/HTTPS.
- If your app is behind an HTTPS reverse proxy/ingress, make sure it reports HTTPS to ASP.NET Core so OpenIdConnect generates https://… URLs:
- Enable ForwardedHeaders middleware to honor X-Forwarded-Proto (K8s ingress sets it).
- Alternatively, force scheme to https at the app start if needed: app.Use((ctx, next) => { ctx.Request.Scheme = "https"; return next(); });
Seed the Hangfire OpenIddict client with the correct URIs Example (adjust hosts to your real public domains):
await CreateOrUpdateApplicationAsync( name: "Hangfire", type: OpenIddictConstants.ClientTypes.Confidential, consentType: OpenIddictConstants.ConsentTypes.Implicit, displayName: "Hangfire Client", secret: "1q2w3e*", grantTypes: [ OpenIddictConstants.GrantTypes.AuthorizationCode, OpenIddictConstants.GrantTypes.ClientCredentials, OpenIddictConstants.GrantTypes.RefreshToken, "pushed_authorization" ], scopes: [ OpenIddictConstants.Scopes.OpenId, OpenIddictConstants.Scopes.Profile, OpenIddictConstants.Scopes.Email, OpenIddictConstants.Scopes.Phone, OpenIddictConstants.Scopes.OfflineAccess, "roles", "HangfireService" ], redirectUris: [ "https://treva-hangfire.tav.aero/signin-oidc" ], postLogoutRedirectUris: [ "https://treva-hangfire.tav.aero/signout-callback-oidc" ] );Notes:
For a server-side MVC client, Authorization Code (+ optional PKCE) with Refresh Token is sufficient. You typically don’t need Implicit or Password grants.
PAR is fine; it still requires the redirect_uri to match exactly.
Clear caches and restart AuthServer
- If you use Redis caches, clear them.
- Restart AuthServer so it reloads OpenIddict applications.
Verify the actual value sent
- After deploying, reproduce and confirm the AuthServer log shows: redirect_uri: "https://treva-hangfire.tav.aero/signin-oidc"
- If not, your Hangfire app is still constructing it from the wrong base URL.
- Sources
- ABP OpenIddict deployment notes (redirect URI and reverse proxy considerations):
- https://abp.io/docs/latest/solution-templates/layered-web-application/deployment/openiddict-deployment
- Relevant ABP support threads showing the same redirect_uri root-cause and resolution:
- https://abp.io/support/questions/6031
- https://abp.io/support/questions/7051
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
[16:37:50 WRN] Unknown proxy: [::ffff:10.2.155.151]:39348 [16:37:50 INF] The request URI matched a server endpoint: PushedAuthorization. [16:37:50 INF] The pushed authorization request was successfully extracted: { "client_id": "Hangfire", "redirect_uri": "http://treva-hangfire.tav.aero/signin-oidc", "response_type": "code id_token", "scope": "openid profile email phone offline_access roles HangfireService", "response_mode": "form_post", "nonce": "638983894708289133.YTkzYjM3N2EtYzFjMS00NWQ1LWE2MzEtOTc5OTYyY2YwY2QxNzc3NjE1NWUtZTc0OC00OWI3LWE2YWEtOGQ0MTYwYjE2NTkz", "state": "CfDJ8KBhtfQcifVKv-63a2B9_LX2LCsBtttAvItfQJwYZ90Ynzqi8kK2RLW7-4-12JnVZJZEI06SCXijyHCl2H1j4x0IstXUpNaTw0KeUk7yF4VD_iHj6h11oN9KPMhMzl7YU5KAB5sbtohfy0gfnRVIj-jHJ6W0B0IX0IZqZ9YfwGBZnu4VjkyOVrTvTAtChU2I8-TSIw6cCUPUiUw05uelP_wQPQGq3WCoN6JT9kVF53IrE0WiU23EaSB_raAKPzqFfFU_f1dcfz6fjEresx5Mos2ZkOoeozRggoiJT6DrG_0lIErW05HHw1fRF78Lp4jQpdf1dfH27_gmy4Hpa4SQ_VU", "client_secret": "[redacted]" }. [16:37:50 INF] The pushed authorization request was successfully validated. [16:37:50 ERR] SessionId is null. It's not possible to save the session during the sign-in process. [16:37:50 INF] The response was successfully returned as a JSON document: { "request_uri": "urn:ietf:params:oauth:request_uri:LO4sePZEaUCJE7p6pDKvhu_R22lnmOuktOJ279wQEdY", "expires_in": 3599 }. [16:37:50 INF] Request finished HTTP/1.1 POST https://treva-authserver.tav.aero/connect/par - 201 122 application/json;charset=UTF-8 86.7409ms [16:37:50 INF] Request starting HTTP/1.1 GET http://treva-authserver.tav.aero/connect/authorize?client_id=Hangfire&request_uri=urn%3Aietf%3Aparams%3Aoauth%3Arequest_uri%3ALO4sePZEaUCJE7p6pDKvhu_R22lnmOuktOJ279wQEdY&x-client-SKU=ID_NET9_0&x-client-ver=8.12.0.0 - null null [16:37:50 WRN] Unknown proxy: [::ffff:10.2.155.151]:34146 [16:37:50 INF] The request URI matched a server endpoint: Authorization. [16:37:50 INF] The authorization request was successfully extracted: { "client_id": "Hangfire", "request_uri": "urn:ietf:params:oauth:request_uri:LO4sePZEaUCJE7p6pDKvhu_R22lnmOuktOJ279wQEdY", "x-client-SKU": "ID_NET9_0", "x-client-ver": "8.12.0.0" }. [16:37:50 WRN] No SessionId was found in the token during ValidateTokenContext. [16:37:50 INF] The authorization request was successfully validated. [16:37:50 INF] Executing endpoint 'Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)' [16:37:50 INF] Route matched with {action = "Handle", controller = "Authorize", area = "", page = ""}. Executing controller action with signature System.Threading.Tasks.Task
1[Microsoft.AspNetCore.Mvc.IActionResult] HandleAsync() on controller Volo.Abp.OpenIddict.Controllers.AuthorizeController (Volo.Abp.OpenIddict.AspNetCore). [16:37:50 INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy [16:37:51 INF] Executing SignInResult with authentication scheme (OpenIddict.Server.AspNetCore) and the following principal: System.Security.Claims.ClaimsPrincipal. [16:37:51 INF] The token '3a1d80ce-5e9e-f16f-f354-4c005a14adee' was successfully marked as redeemed. [16:37:51 INF] The authorization response was successfully returned to 'http://treva-hangfire.tav.aero/signin-oidc' using the form post response mode: { "code": "[redacted]", "id_token": "[redacted]", "state": "CfDJ8KBhtfQcifVKv-63a2B9_LX2LCsBtttAvItfQJwYZ90Ynzqi8kK2RLW7-4-12JnVZJZEI06SCXijyHCl2H1j4x0IstXUpNaTw0KeUk7yF4VD_iHj6h11oN9KPMhMzl7YU5KAB5sbtohfy0gfnRVIj-jHJ6W0B0IX0IZqZ9YfwGBZnu4VjkyOVrTvTAtChU2I8-TSIw6cCUPUiUw05uelP_wQPQGq3WCoN6JT9kVF53IrE0WiU23EaSB_raAKPzqFfFU_f1dcfz6fjEresx5Mos2ZkOoeozRggoiJT6DrG_0lIErW05HHw1fRF78Lp4jQpdf1dfH27_gmy4Hpa4SQ_VU", "iss": "https://treva-authserver.tav.aero/", "culture": "en", "ui-culture": "en" }. [16:37:51 INF] Executed action Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore) in 113.7744ms [16:37:51 INF] Executed endpoint 'Volo.Abp.OpenIddict.Controllers.AuthorizeController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)' [16:37:51 INF] Request finished HTTP/1.1 GET https://treva-authserver.tav.aero/connect/authorize?client_id=Hangfire&request_uri=urn%3Aietf%3Aparams%3Aoauth%3Arequest_uri%3ALO4sePZEaUCJE7p6pDKvhu_R22lnmOuktOJ279wQEdY&x-client-SKU=ID_NET9_0&x-client-ver=8.12.0.0 - 200 2246 text/html;charset=UTF-8 151.2ms [16:37:52 INF] Request starting HTTP/1.1 POST http://treva-authserver.tav.aero/connect/token - application/x-www-form-urlencoded 185 [16:37:52 WRN] Unknown proxy: [::ffff:10.2.155.151]:39348 [16:37:52 INF] The request URI matched a server endpoint: Token. [16:37:52 INF] The token request was successfully extracted: { "client_id": "Hangfire", "client_secret": "[redacted]", "code": "[redacted]", "grant_type": "authorization_code", "redirect_uri": "http://treva-hangfire.tav.aero/signin-oidc" }. [16:37:52 INF] The token request was successfully validated. [16:37:52 INF] Executing endpoint 'Volo.Abp.OpenIddict.Controllers.TokenController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)' [16:37:52 INF] Route matched with {action = "Handle", controller = "Token", area = "", page = ""}. Executing controller action with signature System.Threading.Tasks.Task1[Microsoft.AspNetCore.Mvc.IActionResult] HandleAsync() on controller Volo.Abp.OpenIddict.Controllers.TokenController (Volo.Abp.OpenIddict.AspNetCore). [16:37:52 INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy [16:37:52 INF] Executing SignInResult with authentication scheme (OpenIddict.Server.AspNetCore) and the following principal: System.Security.Claims.ClaimsPrincipal. [16:37:52 INF] The token '3a1d80ce-5f39-e6fb-de64-ba6f3f54c15f' was successfully marked as redeemed. [16:37:52 INF] The response was successfully returned as a JSON document: { "access_token": "[redacted]", "token_type": "Bearer", "expires_in": 3599, "scope": "openid profile email phone offline_access roles HangfireService", "id_token": "[redacted]", "refresh_token": "[redacted]" }. [16:37:52 INF] Executed action Volo.Abp.OpenIddict.Controllers.TokenController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore) in 59.5565ms [16:37:52 INF] Executed endpoint 'Volo.Abp.OpenIddict.Controllers.TokenController.HandleAsync (Volo.Abp.OpenIddict.AspNetCore)' [16:37:52 INF] Request finished HTTP/1.1 POST https://treva-authserver.tav.aero/connect/token - 200 6957 application/json;charset=UTF-8 181.0399ms [16:37:52 INF] Request starting HTTP/1.1 GET http://treva-authserver.tav.aero/connect/userinfo - null null [16:37:52 WRN] Unknown proxy: [::ffff:10.2.155.151]:39348 [16:37:52 INF] The request URI matched a server endpoint: UserInfo. [16:37:52 INF] The userinfo request was successfully extracted: { "access_token": "[redacted]" }. [16:37:52 INF] The userinfo request was successfully validated. [16:37:52 INF] The authentication demand was rejected because the token had no valid audience. [16:37:52 INF] OpenIddict.Validation.AspNetCore was not authenticated. Failure message: An error occurred while authenticating the current request. [16:37:52 INF] Executing endpoint 'Volo.Abp.OpenIddict.Controllers.UserInfoController.Userinfo (Volo.Abp.OpenIddict.AspNetCore)' [16:37:52 INF] Route matched with {action = "Userinfo", controller = "UserInfo", area = "", page = ""}. Executing controller action with signature System.Threading.Tasks.Task1[Microsoft.AspNetCore.Mvc.IActionResult] Userinfo() on controller Volo.Abp.OpenIddict.Controllers.UserInfoController (Volo.Abp.OpenIddict.AspNetCore). [16:37:52 INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy [16:37:52 INF] Executing OkObjectResult, writing value of type 'System.Collections.Generic.Dictionary2[[System.String, System.Private.CoreLib, Version=9.0.0.0, Culture=neutral, PublicKeyToken=7cec85d7bea7798e],[System.Object, System.Private.CoreLib, Version=9.0.0.0, Culture=neutral, PublicKeyToken=7cec85d7bea7798e]]'. [16:37:52 INF] Executed action Volo.Abp.OpenIddict.Controllers.UserInfoController.Userinfo (Volo.Abp.OpenIddict.AspNetCore) in 38.1243ms [16:37:52 INF] Executed endpoint 'Volo.Abp.OpenIddict.Controllers.UserInfoController.Userinfo (Volo.Abp.OpenIddict.AspNetCore)' [16:37:52 INF] Request finished HTTP/1.1 GET https://treva-authserver.tav.aero/connect/userinfo - 200 null application/json; charset=utf-8 62.4327ms [16:37:53 INF] Start processing HTTP request GET http://treva-authserver/health-status [16:37:53 INF] Sending HTTP request GET http://treva-authserver/health-status [16:37:53 INF] Request starting HTTP/1.1 GET http://treva-authserver/health-status - null null [16:37:53 INF] Executing endpoint 'Health checks' [16:37:53 INF] Received HTTP response headers after 7.9361ms - 200 [16:37:53 INF] End processing HTTP request after 8.0299ms - 200 [16:37:53 INF] Executed endpoint 'Health checks' [16:37:53 INF] Request finished HTTP/1.1 GET https://treva-authserver/health-status - 200 null application/json 6.0931ms -
0
- Solution Your redirect_uri issue is fixed. Now the flow succeeds (PAR, authorize, token) and fails only when Hangfire calls /connect/userinfo: “the token had no valid audience”. That means your access token’s aud does not match any audience accepted by the AuthServer’s OpenIddict Validation handler for the UserInfo endpoint request.
Fix it by aligning the API resources/audiences:
Ensure the Hangfire client requests an API scope that maps to a resource with a known audience.
- In ABP/OpenIddict, each service scope (e.g., HangfireService) should be associated with an API resource name. Typically, the audience equals the resource name.
- If your Hangfire service uses Cookie + OIDC only to show the dashboard, you can:
- Either remove the userinfo call (set GetClaimsFromUserInfoEndpoint = false and rely on id_token claims),
- Or keep userinfo but ensure the access token has a proper audience that the validation layer accepts.
Recommended OIDC client options for Hangfire MVC:
services.AddAuthentication() .AddCookie() .AddOpenIdConnect(OpenIdConnectDefaults.AuthenticationScheme, options => { options.Authority = configuration["AuthServer:Authority"]; options.RequireHttpsMetadata = true; // behind ingress, ensure ForwardedHeaders or force https if needed options.ClientId = configuration["AuthServer:HangfireClientId"]; options.ClientSecret = configuration["AuthServer:HangfireClientSecret"]; options.ResponseType = OpenIdConnectResponseType.Code; options.UsePkce = true; options.SaveTokens = true; // If you DON’T need /userinfo, disable it to avoid the "valid audience" check there: options.GetClaimsFromUserInfoEndpoint = false; // Otherwise, keep it true and request a scope that maps to a resource with accepted audience: // options.GetClaimsFromUserInfoEndpoint = true; options.Scope.Clear(); options.Scope.Add("openid"); options.Scope.Add("profile"); options.Scope.Add("email"); options.Scope.Add("phone"); options.Scope.Add("offline_access"); options.Scope.Add("HangfireService"); // must be a registered API scope/resource options.SignInScheme = CookieAuthenticationDefaults.AuthenticationScheme; });Register the API resource/scope on AuthServer properly:
- Ensure an API scope “HangfireService” exists and is tied to an API resource name that will be used as aud in issued tokens. If you use ABP defaults, the audience equals the resource (service) name. Verify that the audience emitted in the access_token contains HangfireService (or your resource name).
- In your microservice, configure JwtBearer Audience to match that resource name when you protect APIs. Even if Hangfire dashboard itself may not call your own APIs, the UserInfo endpoint validates audience internally. So the access token must include a valid audience the server recognizes.
If you don’t need the UserInfo endpoint at all:
- Set options.GetClaimsFromUserInfoEndpoint = false as shown. The id_token already contains standard claims (subject, name, email, etc.) depending on your server configuration. This is the simplest fix for dashboards.
Reverse proxy/K8s scheme consistency:
- Your latest logs still show http for some internal hops. Make sure the app sees HTTPS:
- Enable ForwardedHeaders to honor X-Forwarded-Proto and X-Forwarded-For.
- Or force HTTPS scheme early in pipeline if necessary: app.Use((ctx, next) => { ctx.Request.Scheme = "https"; return next(); });
- Keep all registered redirect URIs on the client as HTTPS and matching the ingress host.
- Your latest logs still show http for some internal hops. Make sure the app sees HTTPS:
Summary of minimal changes to stop the 500 now:
- Disable the userinfo call: options.GetClaimsFromUserInfoEndpoint = false Then redeploy and test: the flow should complete without hitting /connect/userinfo, thus no audience error.
- Or, keep userinfo and fix scopes/resources so access token has a valid aud:
- Ensure “HangfireService” scope exists and maps to a resource; access tokens include aud=HangfireService; server accepts it.
- Sources
- ABP OpenIddict deployment (reverse proxy, HTTPS, audiences/scopes):
- https://abp.io/docs/latest/solution-templates/layered-web-application/deployment/openiddict-deployment
- Similar redirect_uri root-cause and fixes:
- https://abp.io/support/questions/6031
- https://abp.io/support/questions/7051
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
Hi,
Thank you so much, now, it's working.
-
0
Great 👍































































