Currently we writing automation scripts for that we need bearer token, can we get it from postman so that i can replicate the same in Jmeter
10 Answer(s)
-
0
- Solution To get a bearer access token for a tenant user using Postman (for ABP 8.x with separated Auth Server/OpenIddict), use the standard OAuth2/OpenID Connect token endpoint. Then you can reuse the same token in JMeter.
Follow these steps:
Determine your Auth Server base URL
- For separated AuthServer in Angular solutions, it’s typically like: https://localhost:44322
- The discovery document shows exact endpoints at: https://localhost:44322/.well-known/openid-configuration
- The token endpoint will be: https://localhost:44322/connect/token
Create or confirm a client that allows the password flow
- In your Auth Server’s data seed (or via UI), ensure a client exists that supports:
- grant_types: password (Resource Owner Password)
- allowed scopes: openid, profile, email, phone, roles, offline_access plus your API scopes (e.g., YourProjectName)
- If required, set ClientSecret and RequireClientSecret accordingly.
- If you don’t have a password-enabled client, you can alternatively use the Authorization Code flow in Postman’s OAuth2 helper, but for automation/password-based login you need the password grant configured.
- In your Auth Server’s data seed (or via UI), ensure a client exists that supports:
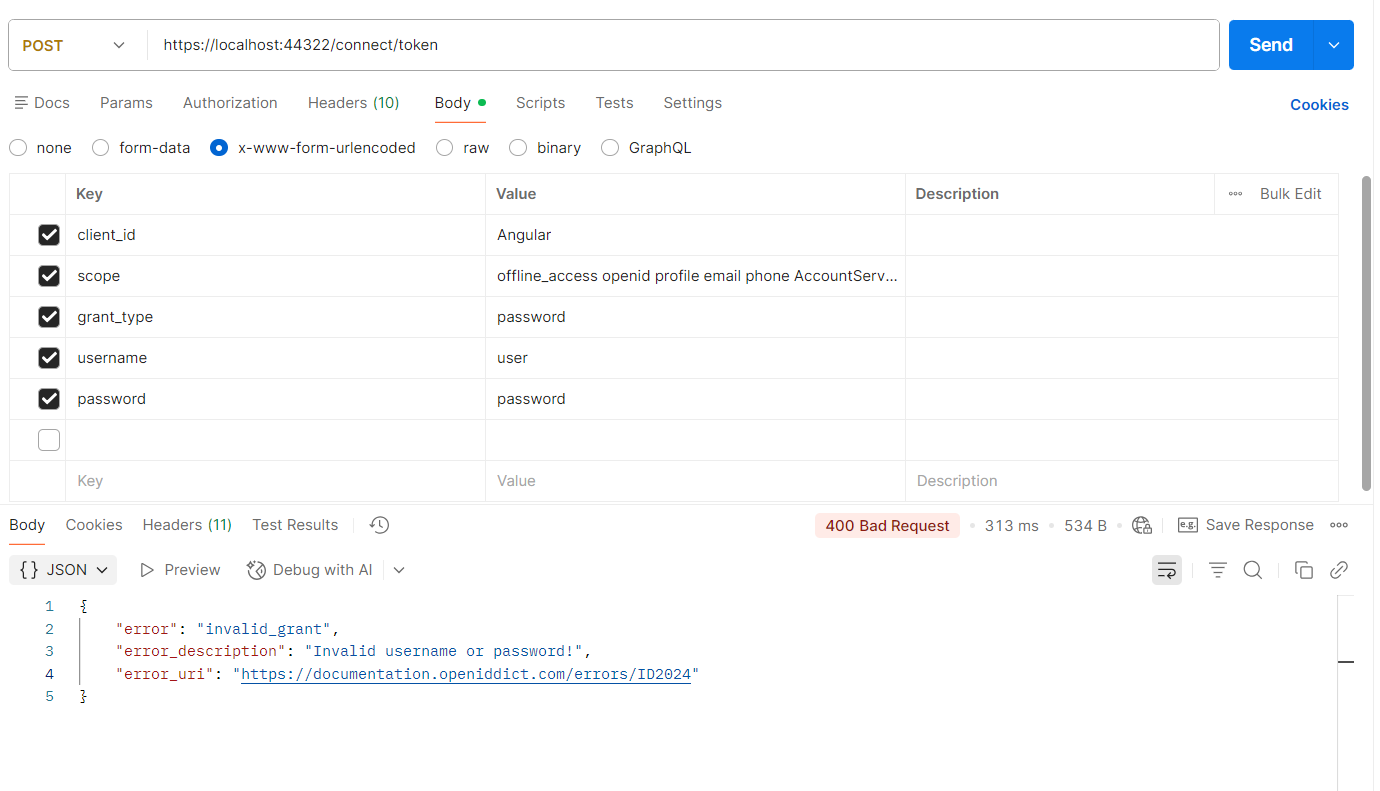
Postman request to get the token (password grant)
- Method: POST
- URL: https://localhost:44322/connect/token
- Headers:
- Content-Type: application/x-www-form-urlencoded
- For multi-tenancy, add: Abp-TenantId: <tenant-guid> (or use the tenant-specific host if you use domain/subdomain tenant resolution)
- If your app uses subdomains per tenant (e.g., https://tenant1.yoursite.com), you don’t need Abp-TenantId; use the tenant host to reach the same token endpoint domain.
- Body (x-www-form-urlencoded):
- grant_type: password
- username: <tenant-user-username-or-email>
- password: <tenant-user-password>
- client_id: <your-client-id>
- client_secret: <your-client-secret> (if the client requires a secret)
- scope: openid profile email phone roles offline_access <YourApiScope1> <YourApiScope2>
- Send. The response contains access_token, token_type, expires_in, and optionally refresh_token.
Important multi-tenancy notes
- If your solution uses header/cookie based tenancy (not domain-based), include either:
- Abp-TenantId header with the tenant’s Id, or
- X-Tenant (older patterns) if you customized it.
- If you use domain/subdomain based tenancy, call the token endpoint on the tenant domain so OpenIddict issues a token for that tenant context.
- Don’t rely on /account/login for API tokens. It’s cookie-based and will interfere with Postman. Always use /connect/token for bearer tokens.
- If you previously called /account/login in Postman, clear cookies before calling /connect/token (cookies can cause 400/CSRF or wrong flow). In Postman, open Cookies for the domain and remove them.
- If your solution uses header/cookie based tenancy (not domain-based), include either:
Use the token in JMeter
- Take the access_token value and set an HTTP Header Manager with:
- Authorization: Bearer <access_token>
- For multi-tenancy (if not domain-based), also add Abp-TenantId: <tenant-guid>
- Optionally, automate token retrieval in JMeter with a pre-HTTP sampler that posts to /connect/token and saves access_token to a JMeter variable for subsequent samplers.
- Take the access_token value and set an HTTP Header Manager with:
Example curl (equivalent to Postman) curl -X POST "https://localhost:44322/connect/token" ^ -H "Content-Type: application/x-www-form-urlencoded" ^ -H "Abp-TenantId: 11111111-1111-1111-1111-111111111111" ^ --data-urlencode "grant_type=password" ^ --data-urlencode "username=admin@mytenant.com" ^ --data-urlencode "password=1q2w3E*" ^ --data-urlencode "client_id=MyAngular_App" ^ --data-urlencode "client_secret=1q2w3e*" ^ --data-urlencode "scope=openid profile email roles offline_access MyProjectName"
If you prefer client credentials (app-to-app, no user), use:
- grant_type: client_credentials
- Remove username/password
- Keep client_id, client_secret, and scopes for your APIs
- Still include Abp-TenantId if your service access must be tenant-scoped.
- Sources
- OpenIddict token flow examples and usage in ABP community articles (password flow and token acquisition were demonstrated and discussed across support threads and samples). No single official page precisely documents Postman steps for tenant tokens, but this approach aligns with ABP’s OpenIddict usage and is consistent with official guidance to use /connect/token rather than cookie-based endpoints.
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
hi
See https://abp.io/support/questions/7044/Unable-to-get-access-token-in-request-response#answer-3a11f692-0164-97bf-03f4-e32afb3b4de4
-
0
[maliming] said: hi
See https://abp.io/support/questions/7044/Unable-to-get-access-token-in-request-response#answer-3a11f692-0164-97bf-03f4-e32afb3b4de4
But i need to login as a tenant user for that i have been using client Id from Identity.OpenIddictApplications table and its giving the below error even though the username, password are correct and grant is being present in the Permissions column of Identity.OpenIddictApplications table
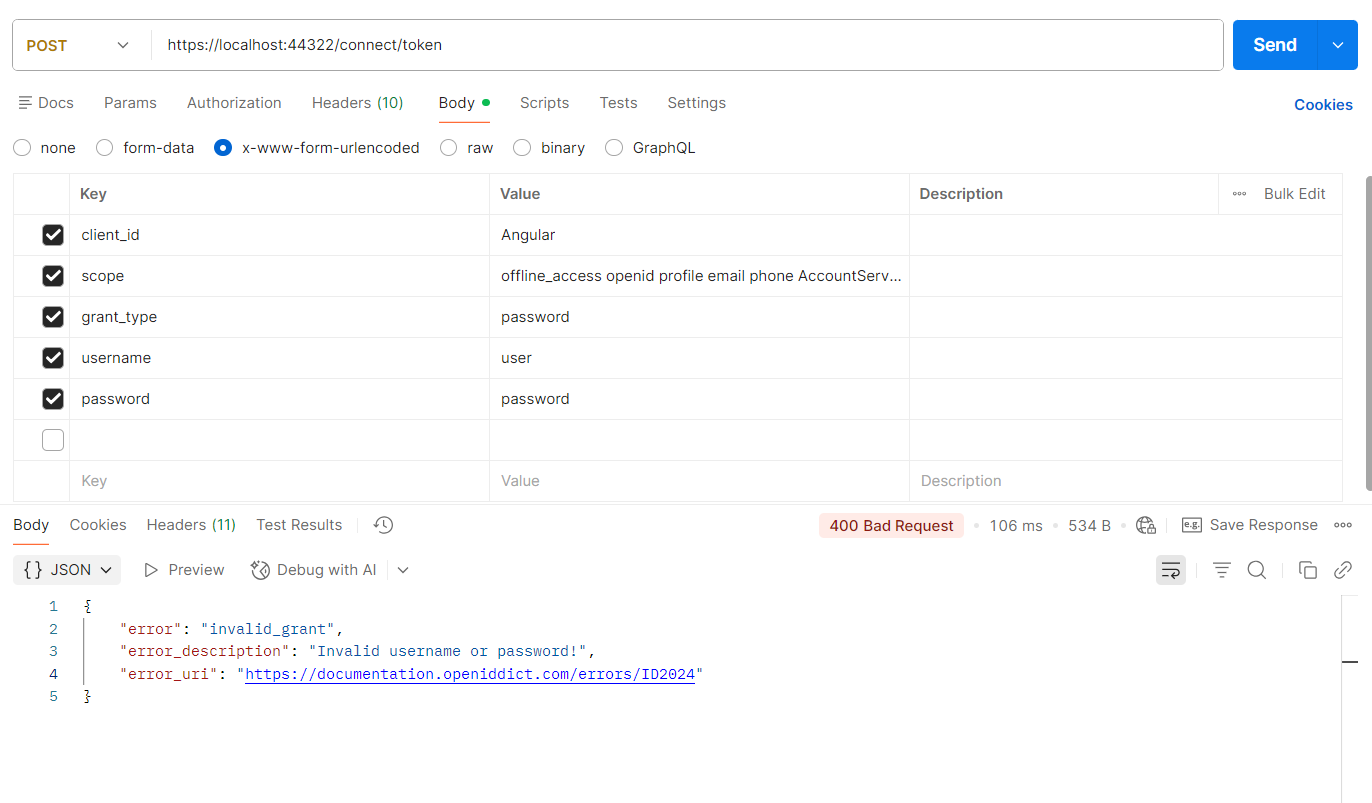
{ "error": "invalid_grant", "error_description": "Invalid username or password!", "error_uri": "https://documentation.openiddict.com/errors/ID2024" }
-
0
hi
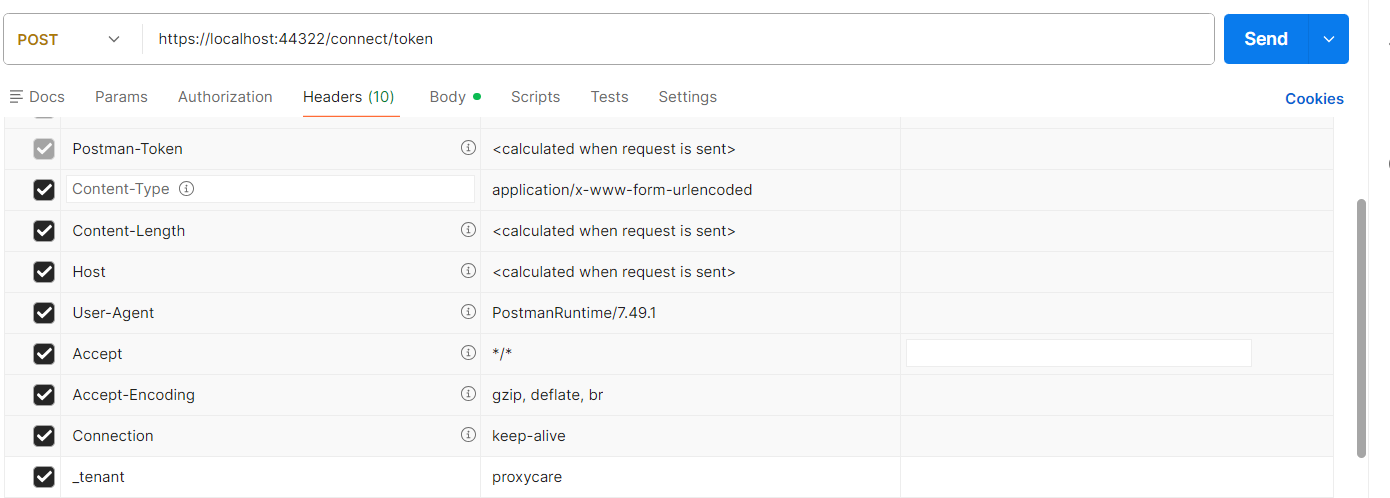
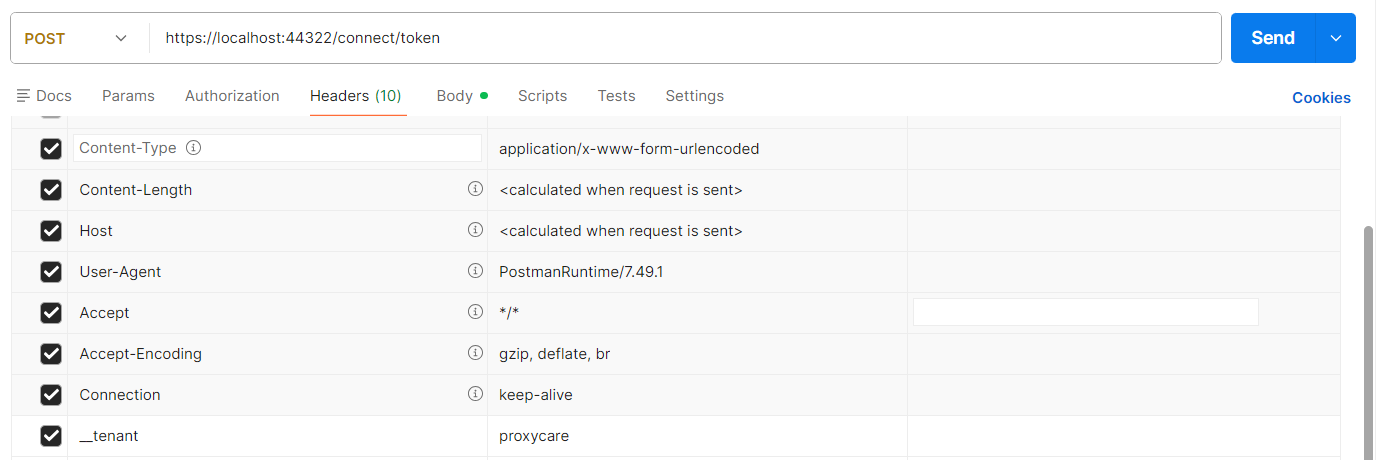
If your username belongs to a tenant, you can add
__tenant: yourtenantto your Postman request header.Thanks.
-
0
-
0
hi
The header name starts with two underscores.
__tenantThanks.
-
0
[maliming] said: hi
The header name starts with two underscores.
__tenantThanks.
am i need to provide any code like below in authserver ** "IdentityClients": { "Default": { "GrantType": "client_credentials", "ClientId": "AdministrationService", "ClientSecret": "1q2w3e*", "Authority": "https://localhost:44322", "Scope": "ClinicService" } },**
-
0
-
0
[maliming] said: hi
Can you add tenant header here?
Please also share the full debug logs.txt of the authserver project.
https://abp.io/support/questions/8622/How-to-enable-Debug-logs-for-troubleshoot-problems
liming.ma@volosoft.com
Thanks.
Hi I have shared the log file of auth server and let me know if you require any further information
Thanks
-
0
hi
No user found matching username: proxyadminAre you sure the
userexists?
Can you try to replace the
HandlePasswordAsyncmethod to debug?[ReplaceControllers(typeof(TokenController))] public class MyTokenController : TokenController { protected override async Task<IActionResult> HandlePasswordAsync(OpenIddictRequest request) { var tenant = await TenantConfigurationProvider.GetAsync(saveResolveResult: false); return await base.HandlePasswordAsync(request); } }Thanks.