- ABP Framework version: v8.0.2
- UI Type: Blazor Server
- Database System: EF Core (SQL Server)
- Tiered (for MVC) or Auth Server Separated (for Angular): no
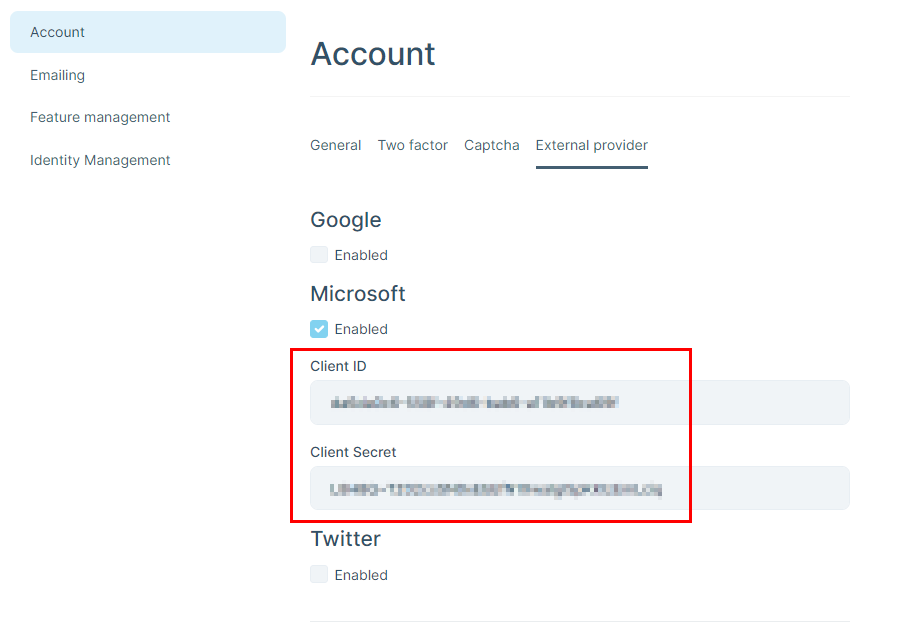
We have a customer who has high security requirements. User authentication runs via Microsoft (AzureAD / Entra). We have configured the external Microsoft provider, which works well.
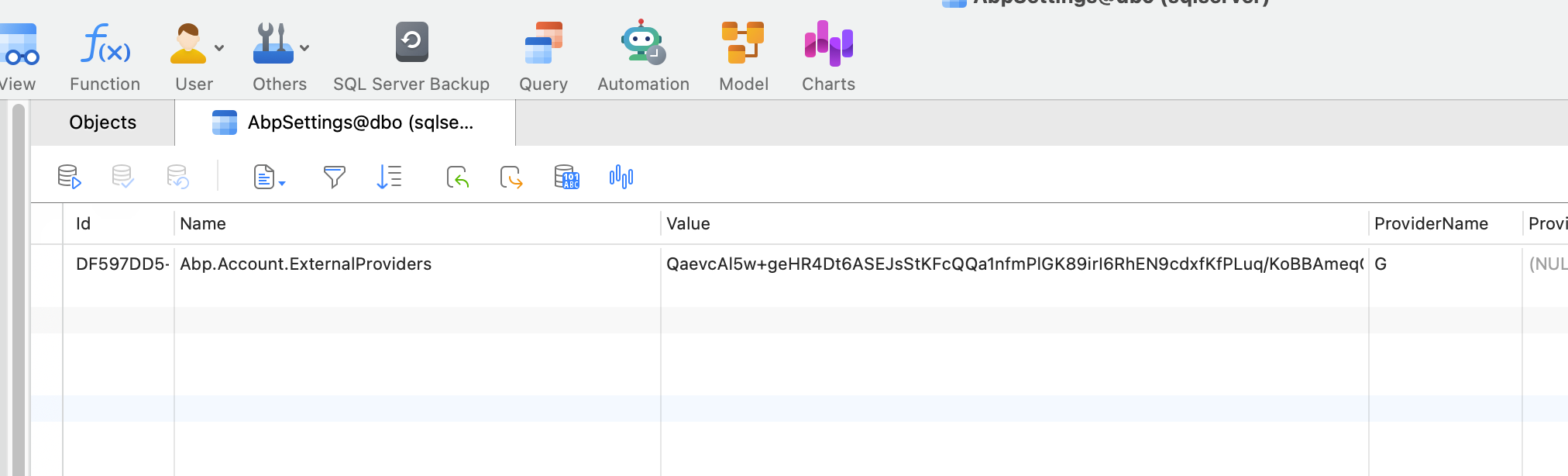
However, the problem is that the customer does not accept that the ClientId & ClientSecret are stored in plain text in the database. The option of storing this information in appsettings.json is of course even worse and therefore not an alternative.
What options would I have to store this information securely?
Of course, it would also be great if you could implement this in a future version so that the information is stored in the AbpSettings in encrypted way, for example. But until then, I need another solution as quickly as possible.
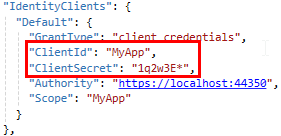
A similar question concerns the credentials of a client that accesses via the HTTP API. As background info: The client runs as a Windows service. Here ClientId & ClientSecret are currently in the appsettings.json file.
I know that there are various approaches to solving this. I would be interested to know which you think is the best option so that even an admin user with access to this file cannot read this information?
Thanks, Adrian
8 Answer(s)
-
0
Hi,
Encrypted storage of
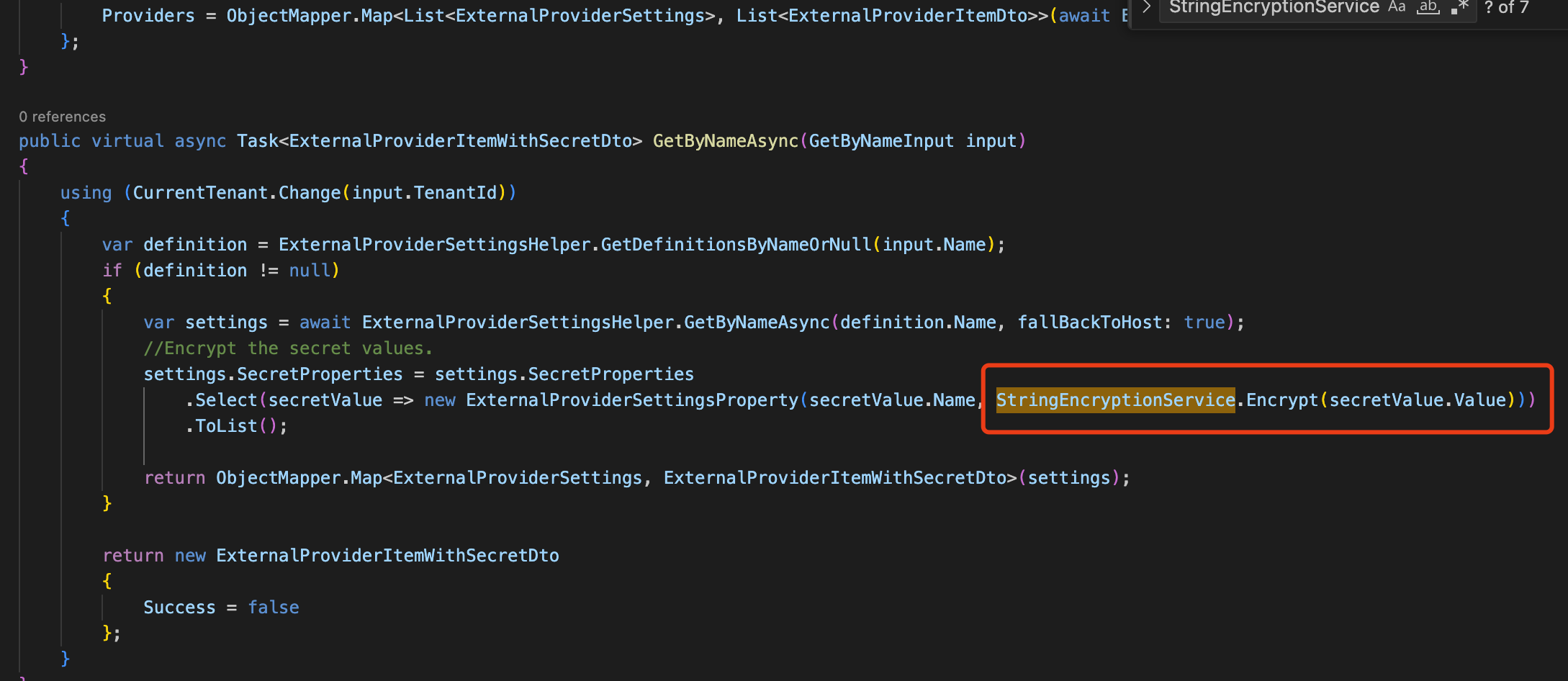
ClientSecretis reasonable. we will enhance it in the 8.2 version.Actually, ABP decrypts the
ClientSecretinternally but doesn't encrypt the storage, which is strange.You can override the
AccountSettingsAppServiceclass[Dependency(ReplaceServices = true)] [ExposeServices(typeof(IAccountSettingsAppService))] public class MyAccountSettingsAppService : AccountSettingsAppService { public override async Task<AccountExternalProviderSettingsDto> GetExternalProviderAsync() { var settigns = await ExternalProviderSettingsHelper.GetAllAsync(); //TODO: Encrypt data return new AccountExternalProviderSettingsDto { Settings = settigns }; } public override async Task UpdateExternalProviderAsync(List<UpdateExternalProviderDto> input) { //TODO: Encrypt data If the data is not encrypted foreach (var setting in input) { await ExternalProviderSettingsHelper.SetAsync(new ExternalProviderSettings { Name = setting.Name, Enabled = setting.Enabled, Properties = setting.Properties, SecretProperties = setting.SecretProperties }); await CurrentUnitOfWork.SaveChangesAsync(); } } }You can consider using the string encryption system provided by ABP
https://docs.abp.io/en/abp/latest/String-Encryption
-
0
-
0
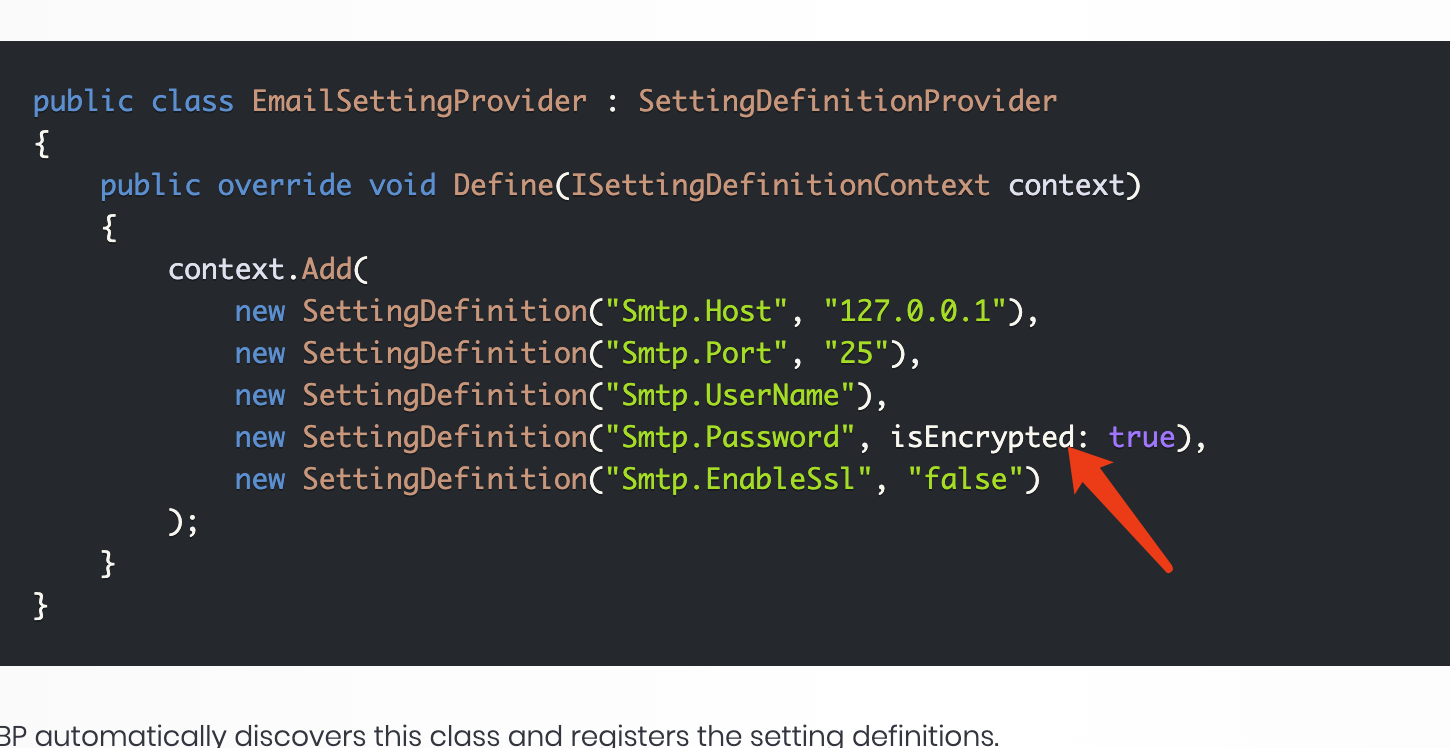
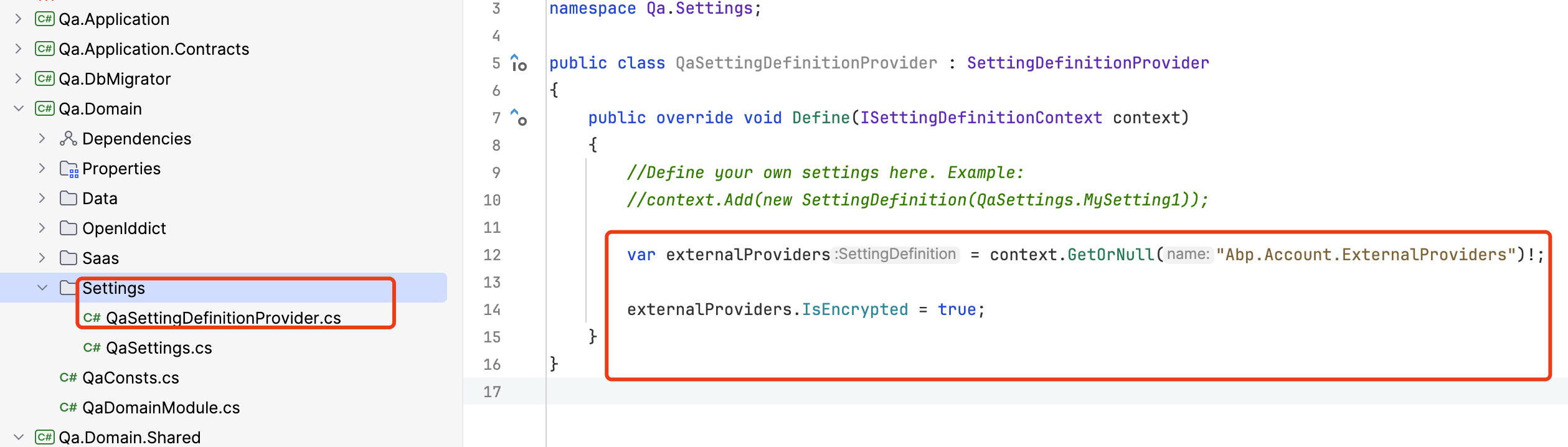
You can take existing settings and edit to encrypted storage
var externalProvidersSetting = context.GetOrNull(AccountSettingNames.ExternalProviders); externalProvidersSetting.IsEncrypted = true;Thank you for this hint. I have to do this in MyAccountSettingsAppService, right?
-
1
-
0
This question has been automatically marked as stale because it has not had recent activity.
-
0
-
1
-
0
It works. Thank you very much @liangshiwei!