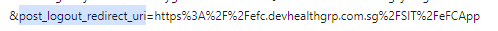Hi, I have migrated Identity server to OpenIddict. It is working fine in local but after deployment, I'm getting below screen
And below is log file
2024-06-12 18:17:58.794 +08:00 [INF] Starting web host.
2024-06-12 18:18:10.941 +08:00 [FTL] Host terminated unexpectedly!
Volo.Abp.AbpInitializationException: An error occurred during ConfigureServices phase of the module Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule, Volo.Abp.OpenIddict.AspNetCore, Version=8.1.3.0, Culture=neutral, PublicKeyToken=null. See the inner exception for details.
---> System.Security.Cryptography.CryptographicException: The specified network password is not correct.
at System.Security.Cryptography.X509Certificates.CertificatePal.FilterPFXStore(ReadOnlySpan`1 rawData, SafePasswordHandle password, PfxCertStoreFlags pfxCertStoreFlags)
at System.Security.Cryptography.X509Certificates.CertificatePal.FromBlobOrFile(ReadOnlySpan`1 rawData, String fileName, SafePasswordHandle password, X509KeyStorageFlags keyStorageFlags)
at System.Security.Cryptography.X509Certificates.CertificatePal.FromBlob(ReadOnlySpan`1 rawData, SafePasswordHandle password, X509KeyStorageFlags keyStorageFlags)
at System.Security.Cryptography.X509Certificates.X509Certificate..ctor(Byte[] rawData, String password, X509KeyStorageFlags keyStorageFlags)
at System.Security.Cryptography.X509Certificates.X509Certificate2..ctor(Byte[] rawData, String password, X509KeyStorageFlags keyStorageFlags)
at Microsoft.Extensions.DependencyInjection.OpenIddictServerBuilder.AddDevelopmentEncryptionCertificate(X500DistinguishedName subject)
at Microsoft.Extensions.DependencyInjection.OpenIddictServerBuilder.AddDevelopmentEncryptionCertificate()
at Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule.<>c__DisplayClass1_0.<AddOpenIddictServer>b__0(OpenIddictServerBuilder builder)
at Microsoft.Extensions.DependencyInjection.OpenIddictServerExtensions.AddServer(OpenIddictBuilder builder, Action`1 configuration)
at Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule.AddOpenIddictServer(IServiceCollection services)
at Volo.Abp.OpenIddict.AbpOpenIddictAspNetCoreModule.ConfigureServices(ServiceConfigurationContext context)
at Volo.Abp.AbpApplicationBase.ConfigureServices()
--- End of inner exception stack trace ---
at Volo.Abp.AbpApplicationBase.ConfigureServices()
at Volo.Abp.AbpApplicationBase..ctor(Type startupModuleType, IServiceCollection services, Action`1 optionsAction)
at Volo.Abp.AbpApplicationWithExternalServiceProvider..ctor(Type startupModuleType, IServiceCollection services, Action`1 optionsAction)
at Volo.Abp.AbpApplicationFactory.Create(Type startupModuleType, IServiceCollection services, Action`1 optionsAction)
at Volo.Abp.AbpApplicationFactory.Create[TStartupModule](IServiceCollection services, Action`1 optionsAction)
at Microsoft.Extensions.DependencyInjection.ServiceCollectionApplicationExtensions.AddApplication[TStartupModule](IServiceCollection services, Action`1 optionsAction)
at eFC.Web.Startup.ConfigureServices(IServiceCollection services) in /agents/work/4/82/s/src/src/eFC.Web/Startup.cs:line 12
at System.RuntimeMethodHandle.InvokeMethod(Object target, Void** arguments, Signature sig, Boolean isConstructor)
at System.Reflection.MethodBaseInvoker.InterpretedInvoke_Method(Object obj, IntPtr* args)
at System.Reflection.MethodBaseInvoker.InvokeDirectByRefWithFewArgs(Object obj, Span`1 copyOfArgs, BindingFlags invokeAttr)
at System.Reflection.MethodBaseInvoker.InvokeWithOneArg(Object obj, BindingFlags invokeAttr, Binder binder, Object[] parameters, CultureInfo culture)
at System.Reflection.RuntimeMethodInfo.Invoke(Object obj, BindingFlags invokeAttr, Binder binder, Object[] parameters, CultureInfo culture)
at Microsoft.AspNetCore.Hosting.MethodInfoExtensions.InvokeWithoutWrappingExceptions(MethodInfo methodInfo, Object obj, Object[] parameters)
at Microsoft.AspNetCore.Hosting.ConfigureServicesBuilder.InvokeCore(Object instance, IServiceCollection services)
at Microsoft.AspNetCore.Hosting.ConfigureServicesBuilder.<>c__DisplayClass9_0.<Invoke>g__Startup|0(IServiceCollection serviceCollection)
at Microsoft.AspNetCore.Hosting.ConfigureServicesBuilder.Invoke(Object instance, IServiceCollection services)
at Microsoft.AspNetCore.Hosting.ConfigureServicesBuilder.<>c__DisplayClass8_0.<Build>b__0(IServiceCollection services)
at Microsoft.AspNetCore.Hosting.GenericWebHostBuilder.UseStartup(Type startupType, HostBuilderContext context, IServiceCollection services, Object instance)
at Microsoft.AspNetCore.Hosting.GenericWebHostBuilder.<>c__DisplayClass7_0.<UseStartup>b__0(HostBuilderContext context, IServiceCollection services)
at Microsoft.Extensions.Hosting.HostBuilder.InitializeServiceProvider()
at Microsoft.Extensions.Hosting.HostBuilder.Build()
at eFC.Web.Program.Main(String[] args) in /agents/work/4/82/s/src/src/eFC.Web/Program.cs:line 36
Can you please help if there is anything missed.
ABP Framework version: v8.1.1
UI Type:React
Database System: EF Core (SQL Server)
Tiered (for MVC) or Auth Server Separated (for Angular): yes
Exception message and full stack trace:NA
Steps to reproduce the issue: Migration from Identity server to OpenIddict
67 Answer(s)
-
0
-
0
-
0
well, that's strange.
Can you reproduce this locally by changing environment to production ?
-
0
well, that's strange.
Can you reproduce this locally by changing environment to production ?
It is working in local environment even if I change environment as production.
-
0
well, that's strange.
Can you reproduce this locally by changing environment to production ?
But it is still not working if Load User Profile is false in SIT, is there anything because of this ?
-
0
hi
It is working in local environment even if I change environment as production.
Can you share a simple project? I will check the source code.
liming.ma@volosoft.com
But it is still not working if Load User Profile is false in SIT, is there anything because of this ?
This is required for the IIS deployment.
https://docs.abp.io/en/commercial/latest/startup-templates/application/deployment-iis?UI=MVC&DB=EF&Tiered=Yes#publish-the-applications-s
-
0
hi
It is working in local environment even if I change environment as production.
Can you share a simple project? I will check the source code.
liming.ma@volosoft.com
But it is still not working if Load User Profile is false in SIT, is there anything because of this ?
This is required for the IIS deployment.
https://docs.abp.io/en/commercial/latest/startup-templates/application/deployment-iis?UI=MVC&DB=EF&Tiered=Yes#publish-the-applications-s
Hi, please find sample project https://github.com/priyankamauryaa/eFC
-
0
hi
Please make your repository PRIVATE and invite https://github.com/maliming as a contributor.
Thanks.
-
0
hi
Can you try to remove the
SignatureValidator?SignatureValidator = delegate (string token, TokenValidationParameters parameters) { var jwt = new JwtSecurityToken(token); return jwt; },and add a middleware to output the request header info?
app.UseCookiePolicy(new CookiePolicyOptions { MinimumSameSitePolicy = SameSiteMode.None, Secure = Microsoft.AspNetCore.Http.CookieSecurePolicy.Always }); app.Use(async (httpContext, next) => { var logger = httpContext.RequestServices.GetRequiredService<ILogger<eFCWebModule>>(); var requestInfo = httpContext.Request.Headers .Select(header => header.Key + " : " + header.Value) .ToList(); logger.LogError("Request Info: {RequestInfo}", string.Join(", ", requestInfo)); await next(); }); app.UseAuthentication(); app.UseJwtTokenMiddleware(); `` -
0
hi
Can you try to remove the
SignatureValidator?SignatureValidator = delegate (string token, TokenValidationParameters parameters) { var jwt = new JwtSecurityToken(token); return jwt; },and add a middleware to output the request header info?
app.UseCookiePolicy(new CookiePolicyOptions { MinimumSameSitePolicy = SameSiteMode.None, Secure = Microsoft.AspNetCore.Http.CookieSecurePolicy.Always }); app.Use(async (httpContext, next) => { var logger = httpContext.RequestServices.GetRequiredService<ILogger<eFCWebModule>>(); var requestInfo = httpContext.Request.Headers .Select(header => header.Key + " : " + header.Value) .ToList(); logger.LogError("Request Info: {RequestInfo}", string.Join(", ", requestInfo)); await next(); }); app.UseAuthentication(); app.UseJwtTokenMiddleware(); ``Hi, I'm able to generate token now but after login getting this error in UI console
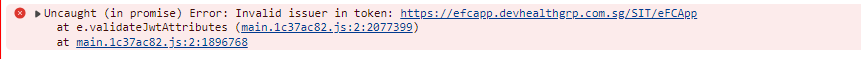
Is there anything needs to add in token or in open-id config, right now it is
export const METADATA_OIDC = { issuer: window.env.REACT_APP_AUTH_URL, jwks_uri: window.env.REACT_APP_API_SERVER_URL + '/.well-known/openid-configuration/jwks', authorization_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/authorize', token_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/token', userinfo_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/userinfo', end_session_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/endsession', check_session_iframe: window.env.REACT_APP_API_SERVER_URL + '/connect/checksession', revocation_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/revocation', introspection_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/introspect', };
-
0
hi
Can you try to remove the
SignatureValidator?SignatureValidator = delegate (string token, TokenValidationParameters parameters) { var jwt = new JwtSecurityToken(token); return jwt; },and add a middleware to output the request header info?
app.UseCookiePolicy(new CookiePolicyOptions { MinimumSameSitePolicy = SameSiteMode.None, Secure = Microsoft.AspNetCore.Http.CookieSecurePolicy.Always }); app.Use(async (httpContext, next) => { var logger = httpContext.RequestServices.GetRequiredService<ILogger<eFCWebModule>>(); var requestInfo = httpContext.Request.Headers .Select(header => header.Key + " : " + header.Value) .ToList(); logger.LogError("Request Info: {RequestInfo}", string.Join(", ", requestInfo)); await next(); }); app.UseAuthentication(); app.UseJwtTokenMiddleware(); ``Hi, I'm able to generate token now but after login getting this error in UI console

Is there anything needs to add in token or in open-id config, right now it is
export const METADATA_OIDC = { issuer: window.env.REACT_APP_AUTH_URL, jwks_uri: window.env.REACT_APP_API_SERVER_URL + '/.well-known/openid-configuration/jwks', authorization_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/authorize', token_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/token', userinfo_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/userinfo', end_session_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/endsession', check_session_iframe: window.env.REACT_APP_API_SERVER_URL + '/connect/checksession', revocation_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/revocation', introspection_endpoint: window.env.REACT_APP_API_SERVER_URL + '/connect/introspect', };
from which file we assign iss value in token? seems like there is case mismatch, expected value is in lowercase.
-
0
-
0
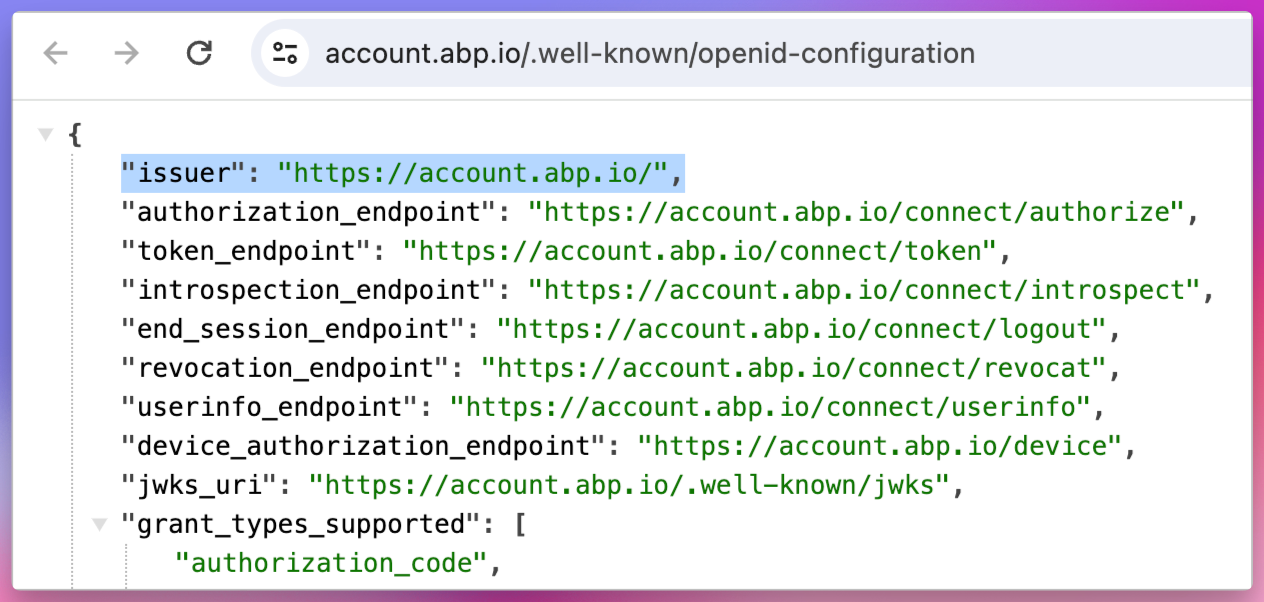
hi
The issuer is coming from the current HTTP request.
You can check it from
/.well-known/openid-configurationCan you also share a jwt token?
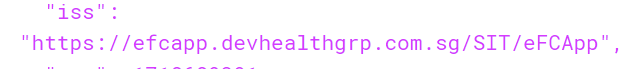
This is my token eyJhbGciOiJSUzI1NiIsImtpZCI6IjRGODQ0QkRCMTk1Rjg5OEIxM0RGQzI0NzA2Njg0MUUxRkVBQTAwQjgiLCJ4NXQiOiJUNFJMMnhsZmlZc1QzOEpIQm1oQjRmNnFBTGciLCJ0eXAiOiJhdCtqd3QifQ.eyJpc3MiOiJodHRwczovL2VmY2FwcC5kZXZoZWFsdGhncnAuY29tLnNnL1NJVC9lRkNBcHAiLCJleHAiOjE3MTg2ODkyOTEsImlhdCI6MTcxODY4NTY5MSwic2NvcGUiOiJvcGVuaWQgb2ZmbGluZV9hY2Nlc3MiLCJqdGkiOiJkMGNhMDI4Yi0wZjRmLTRiNDktOGZiMy02ZTQ5NGJkNTFkM2EiLCJzdWIiOiJhZTg3YjE2Yy01ODY5LTRhMDUtODM0ZS1hMWQ3ZWE5MWU3MzciLCJ1bmlxdWVfbmFtZSI6ImhlYWx0aGdycFxccHJpeWEwNTM0dCIsIkNvbkN1cnJlbnRVc2VySWQiOiI2OTBjYmVkOC1lMzBhLTQyYzgtYmRmMy1mY2JhYWZhMGY5ODEiLCJvaV9wcnN0IjoiZUZDX0FwcCIsIm9pX2F1X2lkIjoiYzdkNzkxYmItNmVjZC03NTUwLTBmYWQtM2ExMzNiMmZiOTQzIiwicHJlZmVycmVkX3VzZXJuYW1lIjoiaGVhbHRoZ3JwXFxwcml5YTA1MzR0IiwiZ2l2ZW5fbmFtZSI6IlByaXlhbmthIiwicm9sZSI6WyJBRE1DX0ZpbmFuY2lhbCBDb3Vuc2Vsb3IiLCJBRE1DX0lEIEFkbWluIiwiQURNQ19JRF9BZG1pbiAiLCJBRE1DX0luc3RpdHV0aW9uIEFkbWluIiwiQURNQ19TeW5hcHhlIEFkbWluX0FsbCBBY2Nlc3MiLCJBTEVYX0ZDVGVzdEFkbWluMSIsIkFMRVhfRmluYW5jaWFsIENvdW5zZWxvciIsIkFMRVhfSW5zdGl0dXRpb24gQWRtaW4iLCJBTEVYX1Rlc3RpbmdSb2xlIiwiSkNIX0ZpbmFuY2lhbCBDb3Vuc2Vsb3IiLCJKQ0hfSW5zdGl0dXRpb24gQWRtaW4iLCJKTUNfRmluYW5jaWFsIENvdW5zZWxvciIsIkpNQ19JbnN0aXR1dGlvbiBBZG1pbiIsIktUUEhfRmluYW5jaWFsIENvdW5zZWxvciIsIktUUEhfSW5zdGl0dXRpb24gQWRtaW4iLCJLVFBIX1Rlc3QgTmV3IFJvbGUiLCJOMVNHX0ZpbmFuY2lhbCBDb3Vuc2Vsb3IiLCJOMVNHX0luc3RpdHV0aW9uIEFkbWluIiwiTlNDX0ZpbmFuY2lhbCBDb3Vuc2Vsb3IiLCJOU0NfSW5zdGl0dXRlIEFkbWluIiwiTlNDX0luc3RpdHV0aW9uIEFkbWluIiwiTlRGSF9GaW5hbmNpYWwgQ291bnNlbG9yIiwiTlRGSF9JbnN0aXR1dGlvbiBBZG1pbiIsIlN1cGVyIEFkbWluIiwiVDFTR19GaW5hbmNpYWwgQ291bnNlbG9yIiwiVDFTR19JbnN0aXR1dGlvbiBBZG1pbiIsIlQxU0dfVklQIFJvbGUiLCJXMVNHX0ZpbmFuY2lhbCBDb3VuY2VsbGVyICIsIlcxU0dfRmluYW5jaWFsIENvdW5zZWxsb3IiLCJXMVNHX0luc3RpdHV0aW9uIEFkbWluIiwiVzFTR19Sb2xlIFRlc3QiLCJXSFBMX0FwcGxpY2F0aW9uIFVzZXIiLCJXSFBMX0FwcGxpY2F0aW9uIFVzZXIgMTIiLCJXSFBMX0ZDMSIsIldIUExfRmluYW5jaWFsIENvdW5zZWxvciIsIldIUExfSW5zdGl0dXRpb24gQWRtaW4iLCJXSFBMX0xvcmVtIGlwc3VtIGRvbG9yMXNpdCBhbWV0LEAjJCIsIldIUExfUm9sZSBTb3J0IFRlc3QgMSIsIldIUExfVGVzdCBTb3J0IFdIUEwiLCJXSFBMX1ZJUCBhbmQgVlZJUCBBY2Nlc3MiLCJZQ0hfRmluYW5jaWFsIENvdW5zZWxvciIsIllDSF9JbnN0aXR1dGlvbiBBZG1pbiJdLCJlbWFpbCI6InByaXlhbmthQGloaXMuY29tLnNnIiwiZW1haWxfdmVyaWZpZWQiOiJGYWxzZSIsInBob25lX251bWJlcl92ZXJpZmllZCI6IkZhbHNlIiwiY2xpZW50X2lkIjoiZUZDX0FwcCIsIm9pX3Rrbl9pZCI6ImYyN2Y3Yzg5LTc3YTgtNjlkNC1mZmY4LTNhMTMzYmQzNDg1NyJ9.fIhf0p_buMG-X17hBHzVQJDi2rEvpAyZvQACN5gLvUVNHpy53DKRgeVFbLtPvl4f-SM6gROroxVwe1aQ86i6-h4v0Lj_0mHPrglDusyy9M7vJwR4HdGdtHALrrwFQUds-sUvOKi-TJ2MZVtDCbSOaICLlU2Ntl_Y-ZWq7_CGqo2fpBvRBQ1iq6e08QYxK4mrXb_jb46i9yjZ28FLh5Q9aKJI1XN0rUOdQQFUzguDE28Pql5b6DOAl2nwIwmwk8yZQF3NuwKVTonVmsOb19XHNcpz_19Ao9gG5SzF0B8t5GzoruTlmA1hQuokBSnk-nNmLYEcGNPAq10oUlxUNeUuTw
and expected value is -https://efcapp.devhealthgrp.com.sg/sit/efcapp
how to update this ?
-
0
hi
You can set issuer by
SetIssuermethodexample:
public override void PreConfigureServices(ServiceConfigurationContext context) { var hostingEnvironment = context.Services.GetHostingEnvironment(); var configuration = context.Services.GetConfiguration(); PreConfigure<OpenIddictBuilder>(builder => { builder.AddValidation(options => { options.AddAudiences("MyProjectName"); options.UseLocalServer(); options.UseAspNetCore(); }); }); if (!hostingEnvironment.IsDevelopment()) { PreConfigure<AbpOpenIddictAspNetCoreOptions>(options => { options.AddDevelopmentEncryptionAndSigningCertificate = false; }); PreConfigure<OpenIddictServerBuilder>(serverBuilder => { serverBuilder.AddProductionEncryptionAndSigningCertificate("openiddict.pfx", "00000000-0000-0000-0000-000000000000"); serverBuilder.SetIssuer(new Uri(configuration["AuthServer:Authority"]!)); }); } } -
0
var configuration = context.Services.GetConfiguration();
It is working after adding this but in DB mode only, but for external Mode It is not redirecting to the app, I had this code for Identity server
public override async Task<IActionResult> OnGetExternalLoginCallbackAsync(string returnUrl = "", string returnUrlHash = "", string remoteError = null) { ..... return RedirectSafely(returnUrl, returnUrlHash); }Now due to openId this is the function
public override async Task<IActionResult> OnGetExternalLoginCallbackAsync(string remoteError = null) { }There is no option to get returnUrl and returnUrlHash as parameter, how to apply RedirectSafely in Open Id's LoginCustomModel?
-
0
hi
The
returnUrl and returnUrlHashare properties of theLoginModelclass.[HiddenInput] [BindProperty(SupportsGet = true)] public string ReturnUrl { get; set; } [HiddenInput] [BindProperty(SupportsGet = true)] public string ReturnUrlHash { get; set; } -
0
hi
The
returnUrl and returnUrlHashare properties of theLoginModelclass.[HiddenInput] [BindProperty(SupportsGet = true)] public string ReturnUrl { get; set; } [HiddenInput] [BindProperty(SupportsGet = true)] public string ReturnUrlHash { get; set; }Thank you. It works. I have one last question in Identity Server I was calling logout, and it was working fine now there is no code change for logout but when I'm calling logout this is coming in post_logout_redirect_uri
and when application is trying to redirect on this URL, I'm getting status code 400
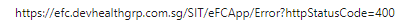
Is there any update require in logout as well while migrating from identity server to OpenIddict?
-
0
hi
now there is no code change for logout but when I'm calling logout this is coming in post_logout_redirect_uri
Please share the full logs of these requests?
-
0
hi
now there is no code change for logout but when I'm calling logout this is coming in post_logout_redirect_uri
Please share the full logs of these requests?
Hi, please find the below logs:
2024-06-19 14:27:37.300 +08:00 [INF] Request starting HTTP/1.1 GET https://efcapp.devhealthgrp.com.sg/SIT/eFCApp/connect/logout?id_token_hint=eyJhbGciOiJSUzI1NiIsImtpZCI6IjRGODQ0QkRCMTk1Rjg5OEIxM0RGQzI0NzA2Njg0MUUxRkVBQTAwQjgiLCJ4NXQiOiJUNFJMMnhsZmlZc1QzOEpIQm1oQjRmNnFBTGciLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL2VmY2FwcC5kZXZoZWFsdGhncnAuY29tLnNnL3NpdC9lZmNhcHAiLCJleHAiOjE3MTg3Nzk1OTIsImlhdCI6MTcxODc3ODM5MiwiYXVkIjoiZUZDX0FwcCIsInN1YiI6ImFlODdiMTZjLTU4NjktNGEwNS04MzRlLWExZDdlYTkxZTczNyIsIm9pX2F1X2lkIjoiYzdkNzkxYmItNmVjZC03NTUwLTBmYWQtM2ExMzNiMmZiOTQzIiwicHJlZmVycmVkX3VzZXJuYW1lIjoiaGVhbHRoZ3JwXFxwcml5YTA1MzR0IiwiYXpwIjoiZUZDX0FwcCIsImF0X2hhc2giOiJNZnZMdkdRY1VDczJXYnYwdllYbXNBIiwib2lfdGtuX2lkIjoiZmYyNTNkZDYtNDQyOS1jNWE4LWExMTgtM2ExMzQxNTljOGJhIn0.UesDrYU9txOUuDv_KsGrfElLBTp9hxIccFp9sYvjnavklx1nlwW2P5N0Atl3CJdsk4FBB_4Hbyw6jALXENNkTuGWJTV42LUV0u-tspseD2HpebIrutnjG33m32tdAN6sqYwg1by3zyXpFlXJHnLJaCOExJycFbTvJGabADn8lcx7p7fSym7IoVFLev6DO3oDdMtQ9EXnNOP8hqzEfEj0dG-2o5rGaUiaKxda4ZgbuWd7Lt-NvPJ0c8XRfUHCF4yBLuSGT3KIbGBlX2FqfWZ56n3qfuyGR_tSCv_yj47NT153ZWkr24rr1_ajZoE5hIVgdFff_0hxslq_VQplNoUSxQ&post_logout_redirect_uri=https%3A%2f%2fefc.devhealthgrp.com.sg%2fSIT%2feFCApp - null null 2024-06-19 14:27:37.301 +08:00 [ERR] Request Info: Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7, Accept-Encoding : gzip, deflate, br, zstd, Accept-Language : en-US,en;q=0.9, Connection : Keep-Alive, Cookie : .AspNetCore.Identity.Application=CfDJ8I6bhRkLkWROlKp09osWwJHoU6llpEbnUhB1Bs7tumvczqUuNFfNC_CQIvMmwl_yf4iYetfcb9KyN02kpwZCbhBLRKDXykO5CqLkdRBMNycrl_OfPMxDU3oplVvlmB2yfnSzdGzGPPM1zdUNy_k1hSMDoVzwmzbwG3dhMK_m-yqaYdRfs9lPxDLUBegGVFMqz4CzbGuWR605rdOHjnNAK_92yuJwH0zynd2mak-N2OIWVDd6ocHKjifcXgpq6N6aNmj6T-mIP6yvOYHQ-a2BaYySoT0Ak5jMo8qfMb4WVuP5TcXf6dqoiisrnIB2E7M9KnamT4j6-YIY-nInRL64ynl2iLnpo9AbKmVfHpyQOPurySFbUUvWNuUQDsrtMeI2-6hRl5CWK6x3BbEDXzJSIgdXMVjgISaUl-guWd0Bg2Gb8xRXpHFTndXckLCEg8MoRG_trizEkZk8Z1mCp-9NosBZ9qTOPms2axqx_a9L6-PLVXjwaZeIOk39RC1MkI9tsYJ4C8YT3PxsBZlLHN4Us86FXZ0kPvk74z_ViJ_BYYVWQYGRFcmrqUNUsTnUNpyZP1YSwInI58vr-_6XgWhsQ3oP1gDvg2EJOS77OczIdtPmurFI3SWCu4qqfjCcs5zLogvJhSwFMd3IhzPrJJzCMfToIFHwwliHK4O6hB7UySCricB8kMqV_jTqynNoygIDgdQVlJLsvNiUJX3yVvzFue4tDlW5JOm6TGz8UZ3QztsadefJVdagZs9iCZUnczyvOMnoyMbx18K4XZn89uhGXb9phXrrp5cqrpQWTOHnMNNnSOTgBE8kCHAS2XiyPwjpGTHACeeIVcPN9R9DCyL2Eh0_0Glj_KD1tPnZelgQNKURlovp7zgNUcxdUFppubxiuWhNrmK-LrtpUSnHeNH-y2PhQdkgsJhLRb5LMCUNeTIjXZrDqHxeoa4Q2HiYmwp90avUkPlENznYIBgT43Fh2JSg8W8hYYU9GdR47NY3W2pr0FPCS_rEyIDeOrLwT3tKMsJ9z2hJgHOuVKAXuTy2U2G863fe1uBLmGLZGs5WmsgvE4mmwRqPsFba7w7oUCRpCumvGdS14vIPG7JpH3fEPzol6p4q8Nf5G_lBaKYf8RGYGgMHIxV7gXdgMwUs97ZQe4SEq4pYP3L2N43uarO5O-Y3sY1Lp8x4LLjS3LSuOqwKYixTF_A2ajw8AX0Ffo9SNrzjcrJmlZQvpulZE7mOT0OPj2RzA0s_va1biuSd3GPxtt6mw6-83Amak3Ns3NWSFNvRihnBQXRz4WtpJEyjlswdwN_roKHdXF6l6xb7d8Kec9pLpJmpeOPY7HSaRTAy8f3hpJ1nkI10pUoeh0neTeEFe6YRBHbb4JyADvysoMxgE_fRfxZnBsM4lSIINaCxXW4y-EBXLqiLEvhjInzstDukLp48UbaqH2MF3RIscboqu5y5MLttAyK9g3-zqp5v63BqXN0rjM-WVl5aNlvTWsdpaf-y5F3RFgTgtaLfG1wUz_xJ7fi18XRoCvYC0L9LyWABfNlRwNNQAqSvJgo0W2uQjdOWcrQH7ExoHvqeIom1EumuOl_Y9ZieGEXN3pW87pWvC9_mOc-tiI5JmVzVamDPkVUWHtkjokJnk6KCO9vZZiB84zpbmJvu7tpH2bhcmdavk8tiygW6Sb8hdexflmpkqnlDcPDlJWhsRO9SqjObm_7NJ48SJL2bfIxw5A0y5l7ge2mKF29VE-s_YhJV9ASibt03AMWdfjh58E8nRwLR4q3_NcI3qGryjFW0kAU5qarMDGm0882da5YfqQX2Go0mgx2cDTu8gwQRcbU4PjphuF2zZ6hKfXYFaA1Ixca7Eu5ghX3WJ_ZIjfw5GkGQA982KHK9iCcPSwV64awWY-K4mGXN193rQNNv7y9ewM173eYinbJl_xIwJCo8usb59g0gDzX64kDuQhqrUK1NQgXJoXrgJM-l2TGXfAZNpZH3CIRrKAzGsLmTQnYbHt65tXpo-ect3lbOqrUsCRnwCeiBRSZRFLYJsjLalXTSbMHnaflpXY8QonPmU7aFtX3Hy6tFBH9P328n9w-Gvbkx3PQZTgzsJz8G7LRdh7THLpbbeXd2a2vaaCYLUD59xDv2CJi5_1PvqwJSDfu-9tX40JT3JiFwvffe-LnEl_OO9MaLFRwt8V1JbuGaBwYZXQDQSL90cg67obq0boNk_vOp7Ol0HPUM9vXNbjqfMo05A6spIczBUWh3t2nSZvTGSORlicWOInhWj2kuTuerXO_AEIzaO0R6VLb3QQpwT0s3FjDcyMsh1gt1P5MyhHmLy7X3Bgtr13NDgqJ4Dl-67tHkYSmNTTn2DMOK7p2MDeVbRDxVNeb3SFCoY7M49JDnwXaPW0WcJcwMThsZprxL2cufhxBuVZQ-Ke4-Ab2AOAKEeIKQ66Kvs-g0zzoWpOnJA4sBk4D_o8p3X-4Gcrr0zKwTLsGX7UImvTe3amNFWcCXFwFDuoYtN5IhxC6htnCAdCyGAn3BFQKrA1DDj2OJtOyQ9WQ-cXuUiygpXP0MiWsTT-x7CXGzpQ6GLfLlu2Ytloqb7WJ7UY-YudHw09g5Yv_V-RCR0V_ceJMOsGYhN5LqLf-1hgbos74mguxJjPVu3sdcWjUyoRPhbI391mNqa42XBsNSLxPWCJv9gTg8jx79C2JE9aAAQqnVDS8NgJQDyFAkVKDYkiYLtP5rt8nYyGxJPWOKKy5TRvnkN20SIsjBVNVW9M1tGwsET43TMQariFO2XP4APm2vwqjZTvPLJnV7s4UlHxdx4fYyzUk4EedKMdVBKSRs71d2mmNQYzqb7cxKaa0nMXk_KC-akEc16XRsYt0l6hDLWohVdXLrxULuxxD_MHkpr4FEUorXx69F6GmlkbnPoRMh2fLRCoPba_vst5-UuLpanfpjs2uuhE__NcQWya54hwQcrzelwQ91Avo-BeeiaYTlcqyWJVmsCgWyFpl3, Host : efcapp.devhealthgrp.com.sg, Max-Forwards : 10, Referer : https://efc.devhealthgrp.com.sg/sit/efcapp/, User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.0.0 Safari/537.36 Edg/123.0.0.0, sec-ch-ua : "Microsoft Edge";v="123", "Not:A-Brand";v="8", "Chromium";v="123", sec-ch-ua-mobile : ?0, sec-ch-ua-platform : "Windows", Upgrade-Insecure-Requests : 1, Sec-Fetch-Site : same-origin, Sec-Fetch-Mode : navigate, Sec-Fetch-User : ?1, Sec-Fetch-Dest : document, X-Forwarded-For : 10.145.12.71, 10.246.136.13:64966, 10.246.136.25, X-Original-URL : /SIT/eFCApp/connect/logout?id_token_hint=eyJhbGciOiJSUzI1NiIsImtpZCI6IjRGODQ0QkRCMTk1Rjg5OEIxM0RGQzI0NzA2Njg0MUUxRkVBQTAwQjgiLCJ4NXQiOiJUNFJMMnhsZmlZc1QzOEpIQm1oQjRmNnFBTGciLCJ0eXAiOiJKV1QifQ.eyJpc3MiOiJodHRwczovL2VmY2FwcC5kZXZoZWFsdGhncnAuY29tLnNnL3NpdC9lZmNhcHAiLCJleHAiOjE3MTg3Nzk1OTIsImlhdCI6MTcxODc3ODM5MiwiYXVkIjoiZUZDX0FwcCIsInN1YiI6ImFlODdiMTZjLTU4NjktNGEwNS04MzRlLWExZDdlYTkxZTczNyIsIm9pX2F1X2lkIjoiYzdkNzkxYmItNmVjZC03NTUwLTBmYWQtM2ExMzNiMmZiOTQzIiwicHJlZmVycmVkX3VzZXJuYW1lIjoiaGVhbHRoZ3JwXFxwcml5YTA1MzR0IiwiYXpwIjoiZUZDX0FwcCIsImF0X2hhc2giOiJNZnZMdkdRY1VDczJXYnYwdllYbXNBIiwib2lfdGtuX2lkIjoiZmYyNTNkZDYtNDQyOS1jNWE4LWExMTgtM2ExMzQxNTljOGJhIn0.UesDrYU9txOUuDv_KsGrfElLBTp9hxIccFp9sYvjnavklx1nlwW2P5N0Atl3CJdsk4FBB_4Hbyw6jALXENNkTuGWJTV42LUV0u-tspseD2HpebIrutnjG33m32tdAN6sqYwg1by3zyXpFlXJHnLJaCOExJycFbTvJGabADn8lcx7p7fSym7IoVFLev6DO3oDdMtQ9EXnNOP8hqzEfEj0dG-2o5rGaUiaKxda4ZgbuWd7Lt-NvPJ0c8XRfUHCF4yBLuSGT3KIbGBlX2FqfWZ56n3qfuyGR_tSCv_yj47NT153ZWkr24rr1_ajZoE5hIVgdFff_0hxslq_VQplNoUSxQ&post_logout_redirect_uri=https%3A%2f%2fefc.devhealthgrp.com.sg%2fSIT%2feFCApp, X-ARR-SSL : 2048|128|C=SG, O=Healthgrp, OU=Healthgrp, CN=Healthgrp ICA|C=SG, O=Synapxe Pte Ltd, OU=eFC, CN=hisfincvsweb01.devhealthgrp.com.sg, X-ARR-LOG-ID : 2419ae76-dcae-49f2-80fb-3b377b2f89cf, X-dynaTrace-Application : v=2;appId=ea7c4b59f27d43eb;cookieDomain=devhealthgrp.com.sg;rid=-1041925062;rpid=-421407435;en=hwdxt9ow, X-dynaTrace-RequestState : agentId=0x87de86d3d7fe00df&pathDepth=1, X-dynaTrace : FW4;-378283432;7;-671219489;18;2;260533856;742;1d40;2h01;3hd7fe00df;4h12;5h01, traceparent : 00-f1bc21d6dfcc6a928eaf20028d2c83cd-0c391ccd76eba96b-01, tracestate : f876e60-e973da58@dt=fw4;7;d7fe00df;12;2;0;0;2e6;1d40;2h01;3hd7fe00df;4h12;5h01, X-Correlation-Id : b5cd1eece5de44c3b1a8bfc0e86b07db 2024-06-19 14:27:37.301 +08:00 [DBG] The event OpenIddict.Validation.OpenIddictValidationEvents+ProcessRequestContext was successfully processed by OpenIddict.Validation.AspNetCore.OpenIddictValidationAspNetCoreHandlers+ResolveRequestUri. 2024-06-19 14:27:37.301 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ResolveRequestUri. 2024-06-19 14:27:37.301 +08:00 [INF] The request URI matched a server endpoint: "Logout". 2024-06-19 14:27:37.301 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+InferEndpointType. 2024-06-19 14:27:37.301 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by Volo.Abp.Account.Web.Pages.Account.OpenIddictImpersonateInferEndpointType. 2024-06-19 14:27:37.301 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateTransportSecurityRequirement. 2024-06-19 14:27:37.301 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ValidateHostHeader. 2024-06-19 14:27:37.302 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ExtractLogoutRequestContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ExtractGetOrPostRequest`1[[OpenIddict.Server.OpenIddictServerEvents+ExtractLogoutRequestContext, OpenIddict.Server, Version=5.1.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-06-19 14:27:37.302 +08:00 [INF] The logout request was successfully extracted: { "id_token_hint": "[redacted]", "post_logout_redirect_uri": "https://efc.devhealthgrp.com.sg/SIT/eFCApp" }. 2024-06-19 14:27:37.302 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Session+ExtractLogoutRequest. 2024-06-19 14:27:37.302 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateLogoutRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Session+ValidatePostLogoutRedirectUriParameter. 2024-06-19 14:27:37.302 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+ValidateAuthenticationDemand. 2024-06-19 14:27:37.302 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+EvaluateValidatedTokens. 2024-06-19 14:27:37.302 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+ResolveValidatedTokens. 2024-06-19 14:27:37.302 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+ValidateRequiredTokens. 2024-06-19 14:27:37.307 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+ValidateClientId. 2024-06-19 14:27:37.307 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateTokenContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Protection+ResolveTokenValidationParameters. 2024-06-19 14:27:37.312 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateTokenContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Protection+ValidateReferenceTokenIdentifier. 2024-06-19 14:27:37.313 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateTokenContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Protection+ValidateIdentityModelToken. 2024-06-19 14:27:37.313 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateTokenContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Protection+NormalizeScopeClaims. 2024-06-19 14:27:37.313 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateTokenContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Protection+MapInternalClaims. 2024-06-19 14:27:37.313 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateTokenContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Protection+RestoreTokenEntryProperties. 2024-06-19 14:27:37.313 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateTokenContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Protection+ValidatePrincipal. 2024-06-19 14:27:37.313 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateTokenContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Protection+ValidateTokenEntry. 2024-06-19 14:27:37.317 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateTokenContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Protection+ValidateAuthorizationEntry. 2024-06-19 14:27:37.317 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+ValidateIdentityToken. 2024-06-19 14:27:37.317 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessAuthenticationContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+ResolveHostAuthenticationProperties. 2024-06-19 14:27:37.317 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateLogoutRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Session+ValidateAuthentication. 2024-06-19 14:27:37.318 +08:00 [INF] The logout request was rejected because the specified post_logout_redirect_uri was invalid: https://efc.devhealthgrp.com.sg/SIT/eFCApp. 2024-06-19 14:27:37.318 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateLogoutRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Session+ValidateClientPostLogoutRedirectUri. 2024-06-19 14:27:37.318 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ValidateLogoutRequestContext was marked as rejected by OpenIddict.Server.OpenIddictServerHandlers+Session+ValidateClientPostLogoutRedirectUri. 2024-06-19 14:27:37.318 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Session+ValidateLogoutRequest. 2024-06-19 14:27:37.318 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessRequestContext was marked as rejected by OpenIddict.Server.OpenIddictServerHandlers+Session+ValidateLogoutRequest. 2024-06-19 14:27:37.319 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessErrorContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+AttachErrorParameters. 2024-06-19 14:27:37.319 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessErrorContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+AttachCustomErrorParameters. 2024-06-19 14:27:37.319 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyLogoutResponseContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Session+AttachPostLogoutRedirectUri. 2024-06-19 14:27:37.319 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyLogoutResponseContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Session+AttachResponseState. 2024-06-19 14:27:37.319 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyLogoutResponseContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+AttachHttpResponseCode`1[[OpenIddict.Server.OpenIddictServerEvents+ApplyLogoutResponseContext, OpenIddict.Server, Version=5.1.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-06-19 14:27:37.319 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyLogoutResponseContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+AttachCacheControlHeader`1[[OpenIddict.Server.OpenIddictServerEvents+ApplyLogoutResponseContext, OpenIddict.Server, Version=5.1.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-06-19 14:27:37.319 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyLogoutResponseContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+Session+ProcessHostRedirectionResponse. -
0
2024-06-19 14:27:37.319 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyLogoutResponseContext was successfully processed by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ProcessStatusCodePagesErrorResponse`1[[OpenIddict.Server.OpenIddictServerEvents+ApplyLogoutResponseContext, OpenIddict.Server, Version=5.1.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-06-19 14:27:37.319 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ApplyLogoutResponseContext was marked as handled by OpenIddict.Server.AspNetCore.OpenIddictServerAspNetCoreHandlers+ProcessStatusCodePagesErrorResponse`1[[OpenIddict.Server.OpenIddictServerEvents+ApplyLogoutResponseContext, OpenIddict.Server, Version=5.1.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-06-19 14:27:37.319 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessErrorContext was successfully processed by OpenIddict.Server.OpenIddictServerHandlers+Session+ApplyLogoutResponse`1[[OpenIddict.Server.OpenIddictServerEvents+ProcessErrorContext, OpenIddict.Server, Version=5.1.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. 2024-06-19 14:27:37.319 +08:00 [DBG] The event OpenIddict.Server.OpenIddictServerEvents+ProcessErrorContext was marked as handled by OpenIddict.Server.OpenIddictServerHandlers+Session+ApplyLogoutResponse`1[[OpenIddict.Server.OpenIddictServerEvents+ProcessErrorContext, OpenIddict.Server, Version=5.1.0.0, Culture=neutral, PublicKeyToken=35a561290d20de2f]]. -
0
hi
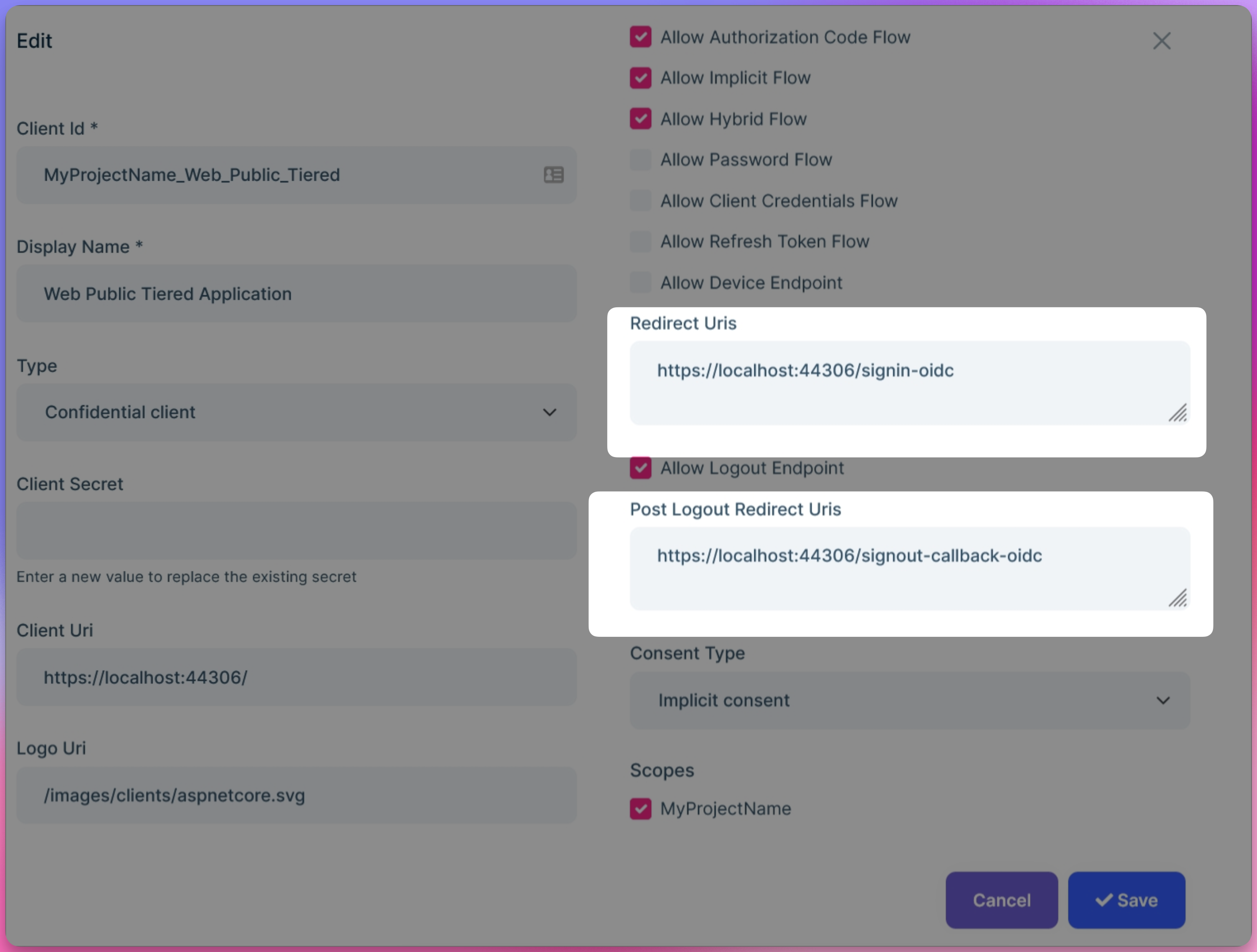
The logout request was rejected because the specified post_logout_redirect_uri was invalid: https://efc.devhealthgrp.com.sg/SIT/eFCApp.Please check your client's
post_logout_redirect_uri.https://github.com/abpframework/abp/blob/dev/templates/app/aspnet-core/src/MyCompanyName.MyProjectName.Domain/OpenIddict/OpenIddictDataSeedContributor.cs#L104
-
0
hi
The logout request was rejected because the specified post_logout_redirect_uri was invalid: https://efc.devhealthgrp.com.sg/SIT/eFCApp.Please check your client's
post_logout_redirect_uri.https://github.com/abpframework/abp/blob/dev/templates/app/aspnet-core/src/MyCompanyName.MyProjectName.Domain/OpenIddict/OpenIddictDataSeedContributor.cs#L104
Hi, webClientRootUrl is supposed to define in appsetting of web? or appsettting of DBMigrator ?
-
0
hi
var configurationSection = _configuration.GetSection("OpenIddict:Applications"); var webClientRootUrl = configurationSection["MyProjectName_Web:RootUrl"]!.EnsureEndsWith('/');`https://github.com/abpframework/abp/blob/dev/templates/app/aspnet-core/src/MyCompanyName.MyProjectName.DbMigrator/appsettings.json#L10
The
configurationSectionvalues are fromDbMigrator/appsettings.jsonfile. -
0
hi
The logout request was rejected because the specified post_logout_redirect_uri was invalid: https://efc.devhealthgrp.com.sg/SIT/eFCApp.Please check your client's
post_logout_redirect_uri.https://github.com/abpframework/abp/blob/dev/templates/app/aspnet-core/src/MyCompanyName.MyProjectName.Domain/OpenIddict/OpenIddictDataSeedContributor.cs#L104
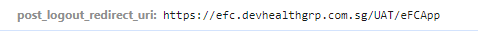
I checked my post_logout_redirect_uri, earlier I was using this https://efc.devhealthgrp.com.sg/SIT/eFCApp
and even in UAT it is still working with this
There will be any specific URL required? Also, it is required to add signout-callback-oidc as well?
I'm using https://github.com/priyankamauryaa/eFC/blob/master/eFC.Web/Pages/Account/CustomLogout.cs for logout, do I need to update something here ?
-
0