32 Answer(s)
-
0
- We have upgraded our application from 7.3.2 to 9.2.0
- We are continue to use IdentityServer (we did not Migrated to OpenIddict).
- We are not using any external login.
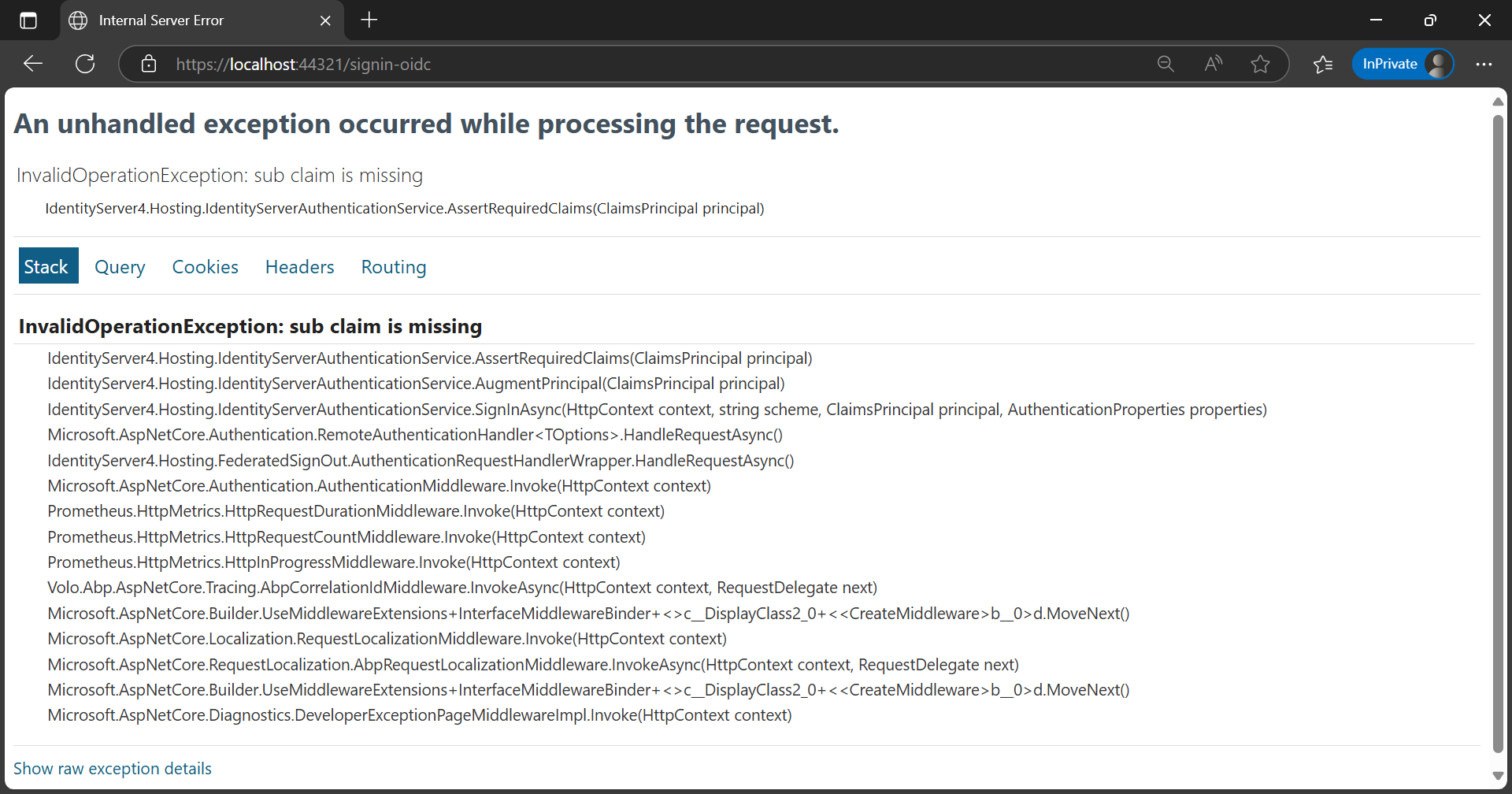
- After upgrade from 7.3.2 to 9.2.0, we were missing the sub and role claims in Back Office Web. We have managed to get thsese claims by adding below code in Back Office Web in AddAbpOpenIdConnect configuration. options.ClaimActions.MapJsonKey("sub", AbpClaimTypes.UserId); options.ClaimActions.MapJsonKey("role", "role");
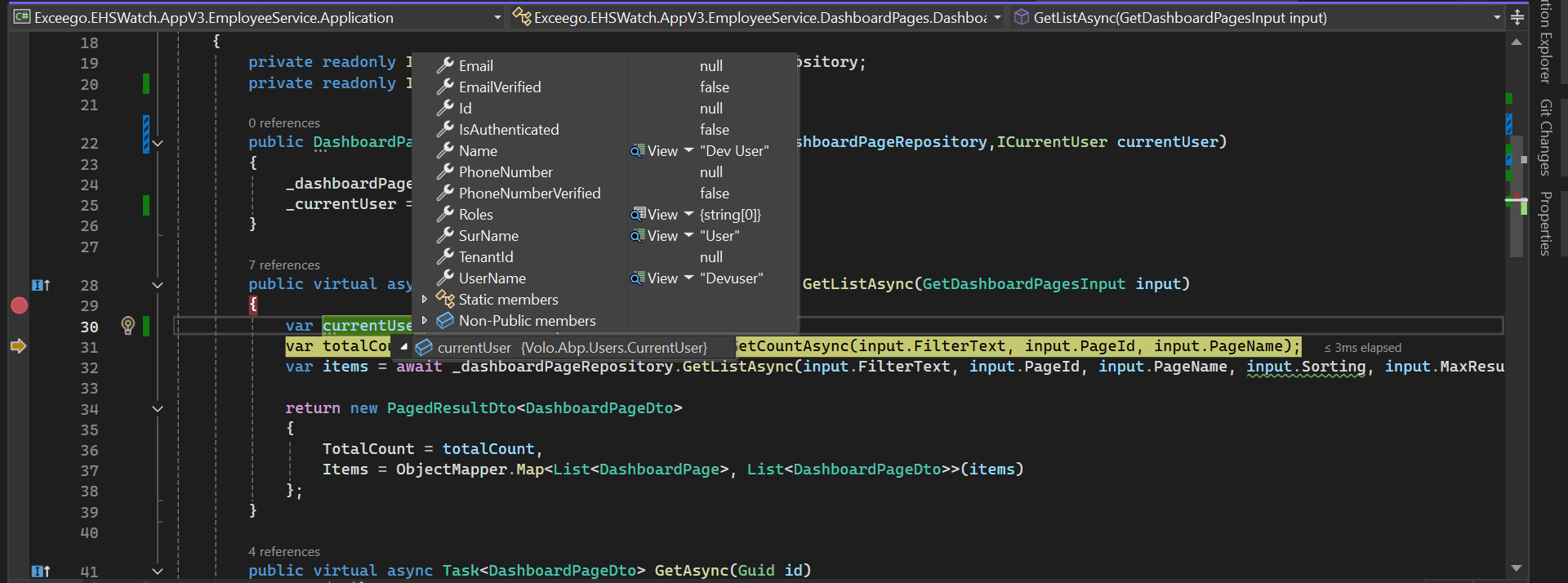
- One of our Micro service called 'Employee Service' have 'EmployeeService.CustomReports' permission and this permission is given to a role and that role assigned to the logged in user. We are able to get that permission from JS, because in Back office web we mapped the roles. But when we check in Employee Service(Micro service), we are missing the roles in claims/CurrentUser, because of this we are not getting the permission.
- After upgrade from 7.3.2 to 9.2.0, we are facing this in Employee Service.
Are we missing anything to get Roles claims/CurrentUser in Employee Service?
-
0
hi
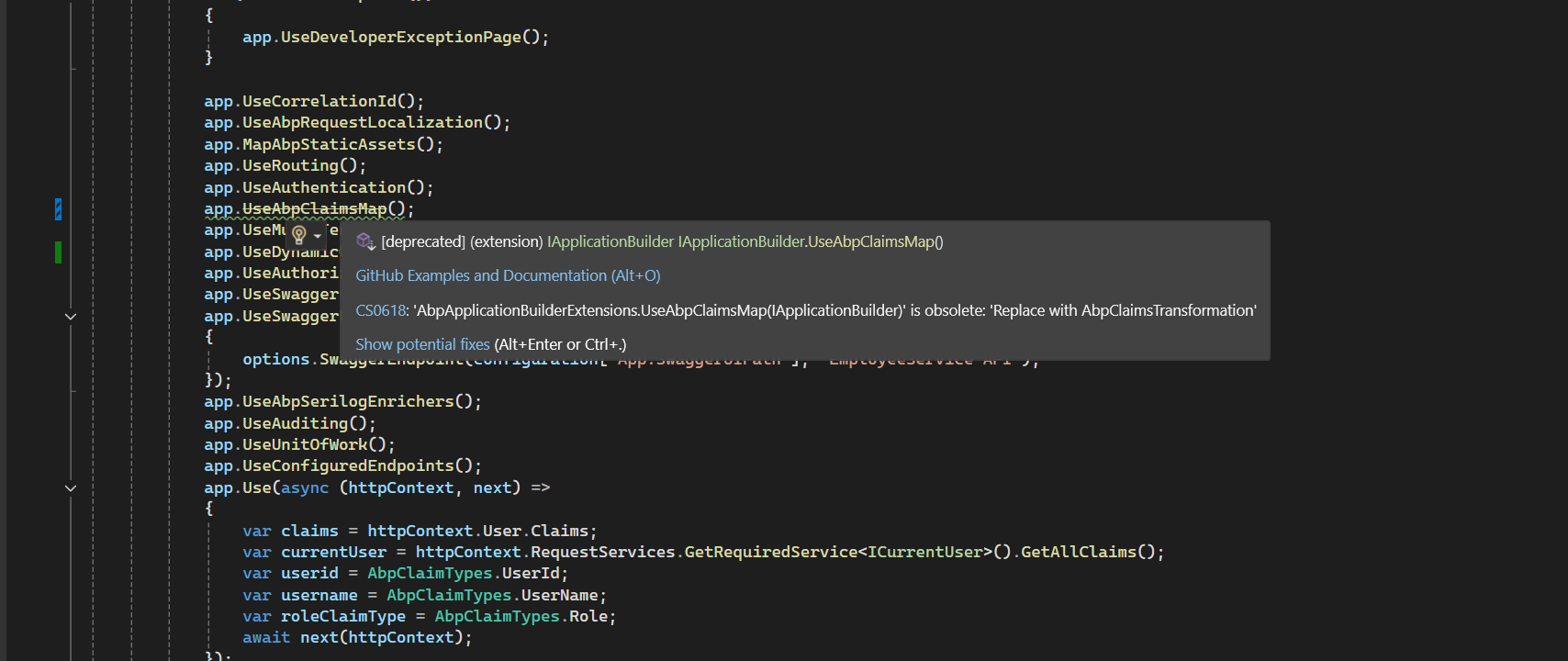
Please add the custom middleware after
app.UseAuthentication();And share the debug logs again(https://abp.io/support/questions/9523/Upgraded-Application-from-732-to-90?CurrentPage=1#answer-3a1ad613-31cb-cb2a-6bd3-323b925e6dc0).
I think the
AbpClaimTypesdoes not match the current claims.Thanks.
app.UseAuthentication(); app.Use(async (httpContext, next) => { var logger = httpContext.RequestServices.GetRequiredService<ILogger<EmployeeServiceHttpApiHostModule>>(); var claims = httpContext.User.Claims.Select(x => new { x.Type, x.Value }).ToList(); logger.LogError("HttpContext.User Claims:"); logger.LogError(JsonSerializer.Serialize(claims)); var currentUser = httpContext.RequestServices.GetRequiredService<ICurrentUser>().GetAllClaims().Select(x => new { x.Type, x.Value }).ToList(); logger.LogError("Current User Claims:"); logger.LogError(JsonSerializer.Serialize(currentUser)); var userid = AbpClaimTypes.UserId; var username = AbpClaimTypes.UserName; var roleClaimType = AbpClaimTypes.Role; logger.LogError($"UserId Claim Type: {userid}"); logger.LogError($"UserName Claim Type: {username}"); logger.LogError($"Role Claim Type: {roleClaimType}"); var authorizationHeader = httpContext.Request.Headers["Authorization"]; logger.LogError(!string.IsNullOrEmpty(authorizationHeader) ? $"Authorization Header: {authorizationHeader}" : "Authorization Header is missing or empty."); await next(httpContext); }); -
0
[liming.ma@volosoft.com] said: hi
The Microsoft logs level still not Debug
Please use the log configuration code below.
var loggerConfiguration = new LoggerConfiguration() .MinimumLevel.Debug() .MinimumLevel.Override("Microsoft.EntityFrameworkCore", LogEventLevel.Warning) .Enrich.FromLogContext() .WriteTo.Async(c => c.File("Logs/logs.txt"))2025-06-30 19:52:16.805 +05:30 [INF] Request starting HTTP/1.1 GET http://localhost:44371/api/employee-service/dashboard-pages?PageId=HOMEDASHBOARD&SkipCount=0&MaxResultCount=20000&api-version=1.0 - null 0 2025-06-30 19:52:17.252 +05:30 [INF] Executing endpoint 'Exceego.EHSWatch.AppV3.EmployeeService.Controllers.DashboardPages.DashboardPageController.GetListAsync (Exceego.EHSWatch.AppV3.EmployeeService.HttpApi)' 2025-06-30 19:52:18.685 +05:30 [INF] Authorization failed. These requirements were not met: PermissionRequirement: EmployeeService.CustomReports 2025-06-30 19:52:19.936 +05:30 [INF] Request finished HTTP/1.1 GET https://localhost:44371/api/employee-service/dashboard-pages?PageId=HOMEDASHBOARD&SkipCount=0&MaxResultCount=20000&api-version=1.0 - 403 0 null 3131.5555msThese requirements were not met: PermissionRequirement: EmployeeService.CustomReports
Does your current user have
EmployeeService.CustomReportspermission?If the
403error only happened onExceego.EHSWatch.AppV3.EmployeeService.HttpApi.Host.website.Please enable the
Debuglog level and share again.Also output some info to the logs.
app.UseAuthentication(); app.Use(async (httpContext, next) => { var logger = httpContext.RequestServices.GetRequiredService<ILogger<EmployeeServiceHttpApiHostModule>>(); var claims = httpContext.User.Claims.Select(x => new { x.Type, x.Value }).ToList(); logger.LogError("HttpContext.User Claims:"); logger.LogError(JsonSerializer.Serialize(claims)); var currentUser = httpContext.RequestServices.GetRequiredService<ICurrentUser>().GetAllClaims().Select(x => new { x.Type, x.Value }).ToList(); logger.LogError("Current User Claims:"); logger.LogError(JsonSerializer.Serialize(currentUser)); var userid = AbpClaimTypes.UserId; var username = AbpClaimTypes.UserName; var roleClaimType = AbpClaimTypes.Role; logger.LogError($"UserId Claim Type: {userid}"); logger.LogError($"UserName Claim Type: {username}"); logger.LogError($"Role Claim Type: {roleClaimType}"); var authorizationHeader = httpContext.Request.Headers["Authorization"]; logger.LogError(!string.IsNullOrEmpty(authorizationHeader) ? $"Authorization Header: {authorizationHeader}" : "Authorization Header is missing or empty."); await next(httpContext); });Thanks.
sent the logs to ur email, Thanks
-
0
-
0
hi
You can change log level in
SerilogConfigurationHelper.Configure(assemblyName);fileCan you set the
MapInboundClaimsproperty ofAddJwtBearer/AddAbpJwtBearermethod tofalse?.AddAbpJwtBearer(options => { options.TokenValidationParameters = new TokenValidationParameters //...tions.MapInboundClaims = false; options.MapInboundClaims = false; //... } -
0
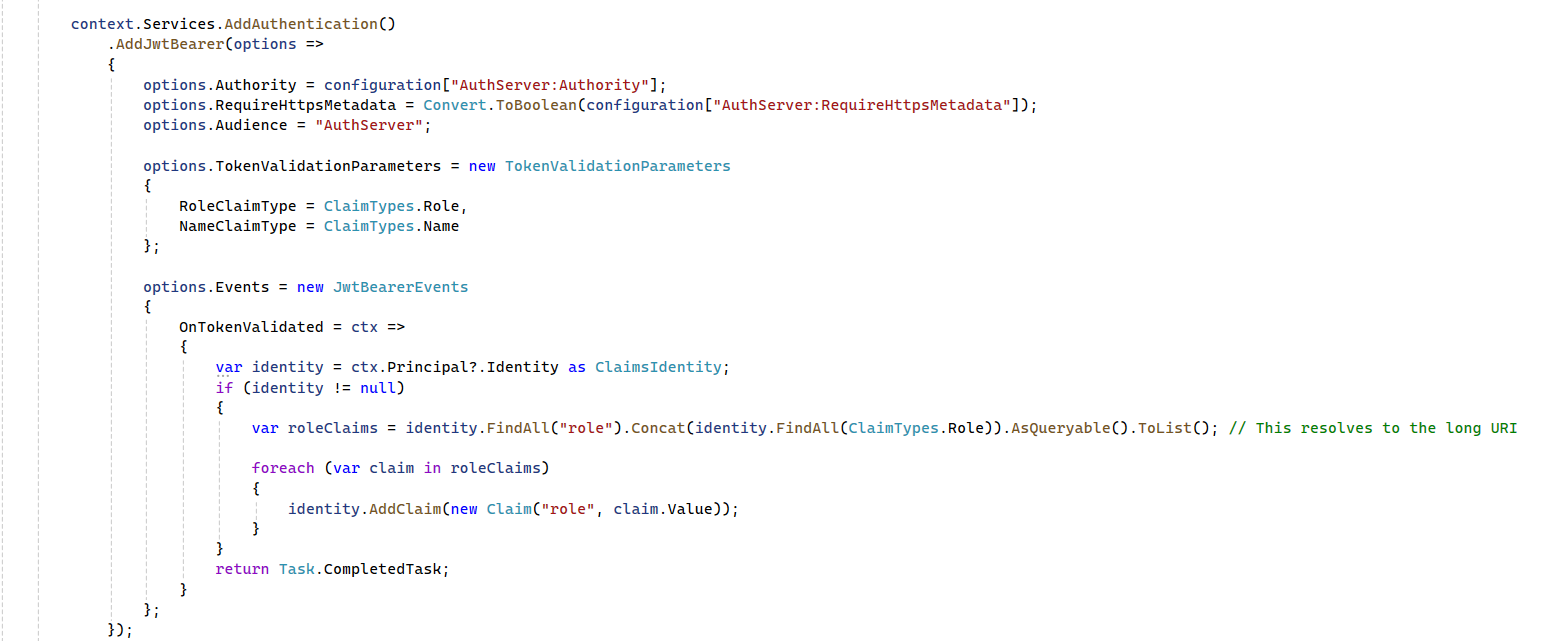
Some how we are able to make the things working with Idenity4 server after upgrade to ABP 9 .
We made changes in Auth server module file
and in JwtBearerConfigurationHelper.cs we have added additional options
After the above changes Login worked perfectly and things are perfect till Auth Server ad Web,
But we we are calling the API's from different services we observed that ICurrentUser object is coming but with null values for Id, Email etc, Also IsAuthenticated also coming as false so services are not respeoning as expected. Any idea what we might have missed?
-
0
hi
Can you log the claims and token again?
app.UseAuthentication(); app.Use(async (httpContext, next) => { var logger = httpContext.RequestServices.GetRequiredService<ILogger<EmployeeServiceHttpApiHostModule>>(); var claims = httpContext.User.Claims.Select(x => new { x.Type, x.Value }).ToList(); logger.LogError("HttpContext.User Claims:"); logger.LogError(JsonSerializer.Serialize(claims)); var currentUser = httpContext.RequestServices.GetRequiredService<ICurrentUser>().GetAllClaims().Select(x => new { x.Type, x.Value }).ToList(); logger.LogError("Current User Claims:"); logger.LogError(JsonSerializer.Serialize(currentUser)); var userid = AbpClaimTypes.UserId; var username = AbpClaimTypes.UserName; var roleClaimType = AbpClaimTypes.Role; logger.LogError($"UserId Claim Type: {userid}"); logger.LogError($"UserName Claim Type: {username}"); logger.LogError($"Role Claim Type: {roleClaimType}"); var authorizationHeader = httpContext.Request.Headers["Authorization"]; logger.LogError(!string.IsNullOrEmpty(authorizationHeader) ? $"Authorization Header: {authorizationHeader}" : "Authorization Header is missing or empty."); await next(httpContext); });