Environment: ABP latest version, separated Auth, angular App and . .NET9 host APi
We are deploying our ABP-based application using two microservices in Kubernetes: an Auth Server and a Host API.
In the Host API, we configure JWT authentication using AddAbpJwtBearer() with Authority and MetadataAddress pointing to the internal service address of the Auth Server , like so:
context.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme) .AddAbpJwtBearer(options => { options.Authority = configuration["AuthServer:Authority"]; options.MetadataAddress = configuration["AuthServer:MetaAddress"]!.EnsureEndsWith('/') + ".well-known/openid-configuration"; options.RequireHttpsMetadata = configuration.GetValue<bool>("AuthServer:RequireHttpsMetadata"); options.Audience = configuration["AuthServer:Audience"]; });
Problem:
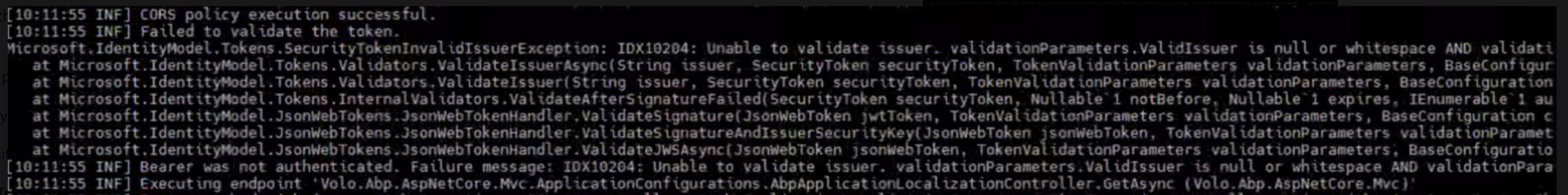
Although the token is successfully returned after login, it fails validation in the Host API.
We receive this error when ValidateIssuer is enabled:
IDX10204: Unable to validate issuer. validationParameters.ValidIssuer is null or whitespace AND validationParameters.ValidIssuers is null. When setting ValidateIssuer = false options.TokenValidationParameters = new TokenValidationParameters { ValidateIssuer = false, / or true with the correct issuer not working also
});
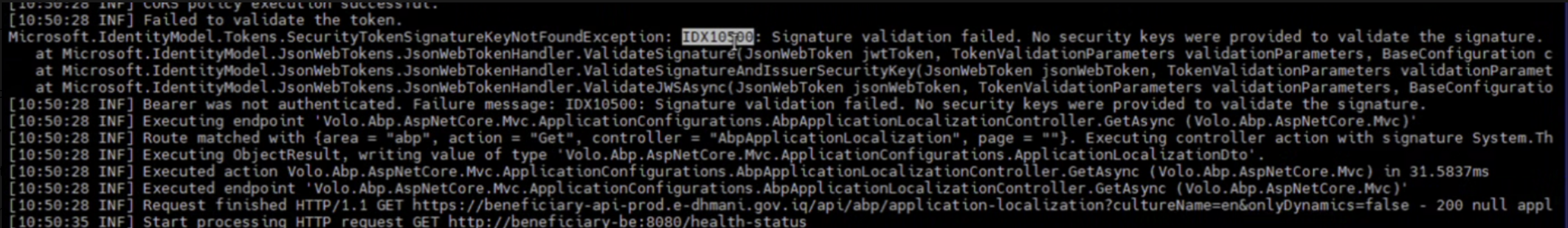
We then get: IDX10500: Signature validation failed. No security keys were provided to validate the signature. Even after setting
ValidateIssuerSigningKey = false,
token validation still fails, and no response is returned from the API. The Angular app remains stuck after login, and Swagger also returns unauthorized.
so, how to use MetadataAddress as an inner address and validate the token
we couldn't upload our code because it is a restricted environment
6 Answer(s)
-
0
To resolve IDX10204 (issuer validation) and IDX10500 (signature validation) errors when using an internal MetadataAddress in Kubernetes, you must ensure that:
- The issuer in your tokens matches the expected issuer in your Host API configuration.
- The Host API can access the Auth Server's OpenID configuration and signing keys using the internal address.
- The ValidIssuers and Authority are set correctly, and the keys are available for signature validation.
Here is a recommended approach for ABP microservice deployments in Kubernetes:
context.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme) .AddAbpJwtBearer(options => { options.Authority = configuration["AuthServer:Authority"]; // Should match the issuer in the token options.MetadataAddress = configuration["AuthServer:MetaAddress"]!.EnsureEndsWith('/') + ".well-known/openid-configuration"; options.RequireHttpsMetadata = configuration.GetValue<bool>("AuthServer:RequireHttpsMetadata"); options.Audience = configuration["AuthServer:Audience"]; // Explicitly set ValidIssuers to match the issuer in the token options.TokenValidationParameters = new TokenValidationParameters { ValidIssuers = new[] { configuration["AuthServer:Authority"].EnsureEndsWith('/') } }; });Key Points:
- The value of
AuthServer:Authoritymust exactly match theiss(issuer) claim in the JWT token. - The
MetadataAddressshould be the internal service address, but the issuer in the token must still match the public/external URL if that's what is issued. - If your Auth Server is behind a reverse proxy or ingress, ensure the issuer in the token is set correctly. You may need to override the issuer in your Auth Server configuration using:
PreConfigure<OpenIddictServerBuilder>(serverBuilder => { serverBuilder.SetIssuer("https://your-public-auth-url/"); }); - The Host API must be able to reach the internal
/.well-known/openid-configurationand the JWKS endpoint to fetch signing keys.
References:
- ABP Support: Unable to Login even after getting token using angular app (IDX10204/IDX10500)
- ABP Docs: IdentityServer Deployment in Kubernetes
This configuration ensures that both issuer and signing key validation work correctly in a Kubernetes environment with internal service addresses.
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
We already try this solution and I mention it earlier we consume a lot of time trying to fix it but still token not validated please provide us with tested solution because in microservice template this portion is not configured well : options.TokenValidationParameters = new TokenValidationParameters { ValidIssuers = new[] { configuration["AuthServer:Authority"].EnsureEndsWith('/') } };
-
0
-
0
We are deploying our ABP-based application(layered app ) using two microservices in Kubernetes: an Auth Server and a Host API.
In the Host API, we configure JWT authentication using AddAbpJwtBearer() with Authority and the MetadataAddress wich pointing to the internal service address of the Auth Server
This is the identitymodel log:
[Error]06/29/2025 12:45:16 Message: IDX20804: Unable to retrieve document from: 'https://auth/.well-known/openid-configuration'., InnerException: The SSL connection could not be established, see inner exception. [Error]06/29/2025 12:45:16 Message: IDX20806: Unable to obtain an updated configuration from: 'https://auth/.well-known/openid-configuration'. Returning the current configuration. Exception: 'System.IO.IOException: IDX20804: Unable to retrieve document from: 'https://auth/.well-known/openid-configuration'. ---> System.Net.Http.HttpRequestException: The SSL connection could not be established, see inner exception. ---> System.Security.Authentication.AuthenticationException: The remote certificate is invalid according to the validation procedure: RemoteCertificateNameMismatch at System.Net.Security.SslStream.SendAuthResetSignal(ReadOnlySpan
1 alert, ExceptionDispatchInfo exception) at System.Net.Security.SslStream.CompleteHandshake(SslAuthenticationOptions sslAuthenticationOptions) at System.Net.Security.SslStream.ForceAuthenticationAsync[TIOAdapter](Boolean receiveFirst, Byte[] reAuthenticationData, CancellationToken cancellationToken) at System.Net.Http.ConnectHelper.EstablishSslConnectionAsync(SslClientAuthenticationOptions sslOptions, HttpRequestMessage request, Boolean async, Stream stream, CancellationToken cancellationToken) --- End of inner exception stack trace --- at System.Net.Http.ConnectHelper.EstablishSslConnectionAsync(SslClientAuthenticationOptions sslOptions, HttpRequestMessage request, Boolean async, Stream stream, CancellationToken cancellationToken) at System.Net.Http.HttpConnectionPool.ConnectAsync(HttpRequestMessage request, Boolean async, CancellationToken cancellationToken) at System.Net.Http.HttpConnectionPool.CreateHttp11ConnectionAsync(HttpRequestMessage request, Boolean async, CancellationToken cancellationToken) at System.Net.Http.HttpConnectionPool.InjectNewHttp11ConnectionAsync(QueueItem queueItem) at System.Threading.Tasks.TaskCompletionSourceWithCancellation1.WaitWithCancellationAsync(CancellationToken cancellationToken) at System.Net.Http.HttpConnectionPool.SendWithVersionDetectionAndRetryAsync(HttpRequestMessage request, Boolean async, Boolean doRequestAuth, CancellationToken cancellationToken) at System.Net.Http.DiagnosticsHandler.SendAsyncCore(HttpRequestMessage request, Boolean async, CancellationToken cancellationToken) at System.Net.Http.RedirectHandler.SendAsync(HttpRequestMessage request, Boolean async, CancellationToken cancellationToken) at System.Net.Http.HttpClient.<SendAsync>g__Core|83_0(HttpRequestMessage request, HttpCompletionOption completionOption, CancellationTokenSource cts, Boolean disposeCts, CancellationTokenSource pendingRequestsCts, CancellationToken originalCancellationToken) at Microsoft.IdentityModel.Protocols.HttpDocumentRetriever.SendAndRetryOnNetworkErrorAsync(HttpClient httpClient, Uri uri) at Microsoft.IdentityModel.Protocols.HttpDocumentRetriever.GetDocumentAsync(String address, CancellationToken cancel) --- End of inner exception stack trace --- at Microsoft.IdentityModel.Protocols.HttpDocumentRetriever.GetDocumentAsync(String address, CancellationToken cancel) at Microsoft.IdentityModel.Protocols.OpenIdConnect.OpenIdConnectConfigurationRetriever.GetAsync(String address, IDocumentRetriever retriever, CancellationToken cancel) at Microsoft.IdentityModel.Protocols.ConfigurationManager1.GetConfigurationAsync(CancellationToken cancel)., InnerException: IDX20804: Unable to retrieve document from: 'https://auth/.well-known/openid-configuration'. [Error]06/29/2025 12:45:16 Message: IDX20803: Unable to obtain configuration from: 'https://auth/.well-known/openid-configuration'. Will retry at '1/1/0001 12:00:00 AM +00:00'. Exception: 'System.IO.IOException: IDX20804: Unable to retrieve document from: 'https://auth/.well-known/openid-configuration'. ---> System.Net.Http.HttpRequestException: The SSL connection could not be established, see inner exception. ---> System.Security.Authentication.AuthenticationException: The remote certificate is invalid according to the validation procedure: RemoteCertificateNameMismatch at System.Net.Security.SslStream.SendAuthResetSignal(ReadOnlySpan1 alert, ExceptionDispatchInfo exception) at System.Net.Security.SslStream.CompleteHandshake(SslAuthenticationOptions sslAuthenticationOptions) at System.Net.Security.SslStream.ForceAuthenticationAsync[TIOAdapter](Boolean receiveFirst, Byte[] reAuthenticationData, CancellationToken cancellationToken) at System.Net.Http.ConnectHelper.EstablishSslConnectionAsync(SslClientAuthenticationOptions sslOptions, HttpRequestMessage request, Boolean async, Stream stream, CancellationToken cancellationToken) --- End of inner exception stack trace --- at System.Net.Http.ConnectHelper.EstablishSslConnectionAsync(SslClientAuthenticationOptions sslOptions, HttpRequestMessage request, Boolean async, Stream stream, CancellationToken cancellationToken) at System.Net.Http.HttpConnectionPool.ConnectAsync(HttpRequestMessage request, Boolean async, CancellationToken cancellationToken) at System.Net.Http.HttpConnectionPool.CreateHttp11ConnectionAsync(HttpRequestMessage request, Boolean async, CancellationToken cancellationToken) at System.Net.Http.HttpConnectionPool.InjectNewHttp11ConnectionAsync(QueueItem queueItem) at System.Threading.Tasks.TaskCompletionSourceWithCancellation`1.WaitWithCancellationAsync(CancellationToken cancellationToken) at System.Net.Http.HttpConnectionPool.SendWithVersionDetectionAndRetryAsync(HttpRequestMessage request, Boolean async, Boolean doRequestAuth, CancellationToken cancellationToken) at System.Net.Http.DiagnosticsHandler.SendAsyncCore(HttpRequestMessage request, Boolean async, CancellationToken cancellationToken) at System.Net.Http.RedirectHandler.SendAsync(HttpRequestMessage request, Boolean async, CancellationToken cancellationToken) at System.Net.Http.HttpClient. -
0
hi
Unable to obtain an updated configuration from: 'https://auth/.well-known/openid-configuration'. Returning the current configuration. Exception: 'System.IO.IOException: IDX20804: Unable to retrieve document from: 'https://auth/.well-known/openid-configuration'.
API website in k8s will request
https://auth/.well-known/openid-configuration, but the auth website has an HTTPS(SSL) problem.Can you set a valid HTTPS certificate for the auth website?
Of course you can disable the SSL check. But it not recommended.
public override void PreConfigureServices(ServiceConfigurationContext context) { PreConfigure<AbpHttpClientBuilderOptions>(options => { options.ProxyClientBuildActions.Add((_, clientBuilder) => { var client = new HttpClientHandler { ServerCertificateCustomValidationCallback = HttpClientHandler.DangerousAcceptAnyServerCertificateValidator };) clientBuilder.ConfigurePrimaryHttpMessageHandler(client); }); }); }context.Services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme) .AddAbpJwtBearer(options => { options.Authority = configuration["AuthServer:Authority"]; options.RequireHttpsMetadata = configuration.GetValue<bool>("AuthServer:RequireHttpsMetadata"); options.Audience = "MyProjectName"; options.BackchannelHttpHandler = new HttpClientHandler { ServerCertificateCustomValidationCallback = HttpClientHandler.DangerousAcceptAnyServerCertificateValidator }; }); -
0
I put RequireHttpsMetadata = false and use http://auth/.well-known/openid-configuration but internally still request /authorize and other configuration using https and couldn't link internal url with certificate the solution for me was disable the certificate check and now it is working
Thank you for your support