I need to customize entire login flow, Like want to implement otp based login which is password less login.so provide way to do that in efficient way as well as I have abp commertial 4.2 and 8.2 subscription and need to customize login flow I need source code of lepton in account flow for version 4.2 and 8.2 differently I have also mailed that but didn't received source code yet attaching screenshot.
Please share source code on following mail nayan.ranjane@softtech-engr.com
21 Answer(s)
-
0
To implement a fully customized login flow such as OTP-based (passwordless) login in ABP Framework, you need to override the default Account module's login logic and UI. Below are the steps and references for both ABP 4.x and 8.x versions. The Lepton theme's account flow source code is not distributed directly, but you can override and customize the login page and logic as shown below.
Override the Login Page and Model:
- Create a new
CustomLoginModelinheriting fromLoginModel. - Place your custom logic (e.g., OTP validation) in this model.
- Add a new
Login.cshtmlunderPages/Accountto override the default UI.
Example:
- Create a new
public class CustomLoginModel : LoginModel { public CustomLoginModel( IAuthenticationSchemeProvider schemeProvider, IOptions<AbpAccountOptions> accountOptions) : base(schemeProvider, accountOptions) { } // Override methods to implement OTP logic here }@page @model YourNamespace.Pages.Account.CustomLoginModel <!-- Custom OTP UI here -->Implement OTP Logic:
- In your
CustomLoginModel, implement the logic to send and verify OTP. - You may need to add new endpoints or handlers for sending OTP and verifying it.
- In your
Customize the UI:
- Copy the default login page source from the ABP repository and modify it as needed:
- For Blazor or other UI types, follow similar override patterns.
Lepton Theme Source:
- The Lepton theme is a commercial product. For ABP Commercial subscribers, the source code for the theme and account flow is available in your commercial package download area or via the ABP Commercial GitHub (if you have access).
- For open-source reference, you can use the default Account module's login page as a base and apply your Lepton theme styles.
Sample Projects:
- See these sample repositories for full customization examples:
Version Differences:
- The override approach is similar in both 4.x and 8.x, but always check the constructor parameters and dependencies for your specific ABP version.
- For ABP 8.x, you may need to inject additional services or use updated APIs.
Lepton Source Code Access:
- For ABP Commercial, source code for Lepton and other commercial modules is provided via your customer portal or private repository access. If you have not received it, please contact ABP Commercial support directly through your customer portal for access.
You can find the default login page source and customization guides at the following links:
Sources:
- ABP Account Login Page Source
- Authentication Customization Sample
- Blazor Login Customization
- Hide Tenant Switch Example
For Lepton theme source code and commercial modules, please use your ABP Commercial customer portal or contact support for direct access.
This response was generated by AI. If it didn’t solve your problem, feel free to post a new answer — our support team will jump in to help you soon.
-
0
hi
I need source code of lepton in account flow for version 4.2 and 8.2 differently I have also mailed that but didn't received source code yet attaching screenshot.
Do you only need the
Account Layoutof the Lepton theme?Thanks.
-
0
Yes requires multiple changes like login page then page to select otp provider then code page where we validation the otp i need to customize this. so please share me accordingly.
-
0
hi
I will share the Layout source with you.
-
0
Let me know after sharing waiting for your mail need to urgently integrate in solution
-
0
-
0
Please check shared mail it is having only layout but other navigation like provider selection in two factor authentication screen and otp validation screen is not there
-
0
hi
provider selection in two factor authentication screen and otp validation screen
These components exist in Account.Pro module.
You can download the source code of Account.Pro module.
https://abp.io/docs/latest/suite/source-code https://abp.io/support/questions/632/How-can-I-download-the-source-code-of-the-framework-Angular-packages-theme-and-pro-modules
Thanks.
-
0
But in ABP suite there is no code for the version 4.2 which i need to configure in my live application. It will be very helpfull if you provide me code if i want to perform otp based login and ui redirection to directly on code entering page in 2f authentication without any provider selection
-
0
hi
I can share the Account Pro 4.2.0 source code, Does this work for you?
Thanks.
-
0
Customizing code by source code given by you will you please help to solve following.
We have Alerts on login page like invalid username and many more how to enable those in my custom login.cshtml
how to use following class in version 4.2.1
namespace Volo.Abp.AspNetCore.Mvc.UI.Theme.LeptonX.Themes.LeptonX.Components.Common.PageAlerts; public class PageAlertsViewComponent : LeptonXViewComponentBase { protected IAlertManager AlertManager { get; }
public PageAlertsViewComponent(IAlertManager alertManager) { AlertManager = alertManager; } public virtual IViewComponentResult Invoke() { return View("~/Themes/LeptonX/Components/Common/PageAlerts/Default.cshtml", AlertManager.Alerts); }}
-
0
hi
You can try to replace this line:
@(await Component.InvokeAsync<ContentAlertsViewComponent>())to
@(await Component.InvokeAsync<PageAlertsViewComponent>()) -
0
thanks maliming,
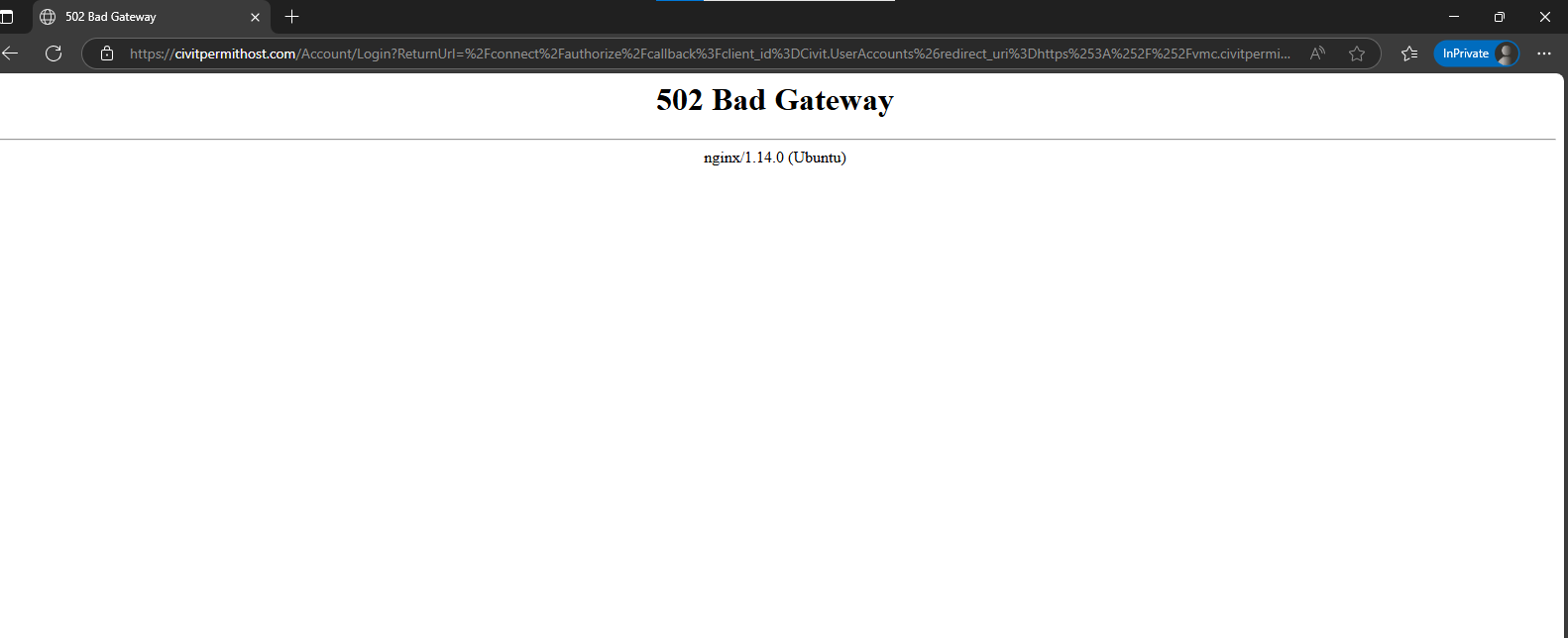
Now my basic flow is good but not able to use openid connect flow, After adding correct username and password flow remains same it doesn't redirect to the required destination sharing you logs.
BG] Start authorize request protocol validation [19:24:19 DBG] client configuration validation for client Civit.UserAccounts succeeded. [19:24:19 DBG] Checking for PKCE parameters [19:24:19 DBG] Calling into custom validator: IdentityServer4.Validation.DefaultCustomAuthorizeRequestValidator [19:24:19 DBG] AuthenticationScheme: Bearer was not authenticated. [19:24:19 INF] No CORS policy found for the specified request. [19:24:19 INF] CORS policy execution successful. [19:24:19 INF] Executing endpoint '/Account/Login' [19:24:19 INF] Route matched with {page = "/Account/Login", action = "", controller = "", area = ""}. Executing page /Account/Login [19:24:19 INF] Skipping the execution of current filter as its not the most effective filter implementing the policy Microsoft.AspNetCore.Mvc.ViewFeatures.IAntiforgeryPolicy [19:24:19 INF] Executing handler method SEL.Civit.Web.Pages.Account.CivitLoginModelModel.OnPostAsync - ModelState is Valid [19:24:19 WRN] Ldap login feature is not enabled! [19:24:19 DBG] Augmenting SignInContext [19:24:19 DBG] Adding idp claim with value: local [19:24:19 DBG] Adding auth_time claim with value: 1754508259 [19:24:19 INF] AuthenticationScheme: Identity.Application signed in. [19:24:19 INF] Start processing HTTP request POST https://www.google.com/recaptcha/api/siteverify [19:24:19 INF] Sending HTTP request POST https://www.google.com/recaptcha/api/siteverify [19:24:19 INF] Received HTTP response headers after 127.4732ms - 200 [19:24:19 INF] End processing HTTP request after 127.6373ms - 200 [19:24:19 WRN] Ldap login feature is not enabled! [19:24:20 DBG] Augmenting SignInContext [19:24:20 DBG] Adding idp claim with value: local [19:24:20 DBG] Adding auth_time claim with value: 1754508260 [19:24:20 INF] AuthenticationScheme: Identity.Application signed in. [19:24:20 DBG] Added 0 entity changes to the current audit log [19:24:20 DBG] Added 0 entity changes to the current audit log [19:24:20 INF] Executed handler method OnPostAsync, returned result Microsoft.AspNetCore.Mvc.RedirectResult. [19:24:20 DBG] Added 0 entity changes to the current audit log [19:24:20 DBG] Added 0 entity changes to the current audit log [19:24:20 INF] Executing RedirectResult, redirecting to /connect/authorize/callback?client_id=Civit.UserAccounts&redirect_uri=https%3A%2F%2Fvmc.civitpermit.in%2Fsignin-oidc&response_type=code&scope=openid%20profile%20Civit%20offline_access&state=6059fdae6b8e47259327d5858fc78aa3&code_challenge=YPUPaLDzpdshl56qs6L0ehC-j-KU27mI8LO-Uh9dqq8&code_challenge_method=S256&response_mode=query&tenantId=221AE9CD-28DF-4739-86F6-2BFAFB02E791. [19:24:20 INF] Executed page /Account/Login in 423.7454ms [19:24:20 INF] Executed endpoint '/Account/Login' [19:24:20 DBG] Added 0 entity changes to the current audit log [19:24:20 DBG] Added 0 entity changes to the current audit log [19:24:20 INF] Request finished HTTP/1.0 POST https://civitpermithost.com/Account/Login?ReturnUrl=%2Fconnect%2Fauthorize%2Fcallback%3Fclient_id%3DCivit.UserAccounts%26redirect_uri%3Dhttps%253A%252F%252Fvmc.civitpermit.in%252Fsignin-oidc%26response_type%3Dcode%26scope%3Dopenid%2520profile%2520Civit%2520offline_access%26state%3D6059fdae6b8e47259327d5858fc78aa3%26code_challenge%3DYPUPaLDzpdshl56qs6L0ehC-j-KU27mI8LO-Uh9dqq8%26code_challenge_method%3DS256%26response_mode%3Dquery%26tenantId%3D221AE9CD-28DF-4739-86F6-2BFAFB02E791 application/x-www-form-urlencoded 2720 - 302 0 - 528.1102ms root@docker:/home/softtech/sel.civit# ^C
-
0
Detailed logs
025-08-06 20:02:03.437 +00:00 [DBG] Endpoint enabled: Token, successfully created handler: IdentityServer4.Endpoints.TokenEndpoint 2025-08-06 20:02:03.437 +00:00 [INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.TokenEndpoint for /connect/token 2025-08-06 20:02:03.437 +00:00 [DBG] Start token request. 2025-08-06 20:02:03.437 +00:00 [DBG] Start client validation 2025-08-06 20:02:03.437 +00:00 [DBG] Start parsing Basic Authentication secret 2025-08-06 20:02:03.437 +00:00 [DBG] Start parsing for secret in post body 2025-08-06 20:02:03.437 +00:00 [DBG] client id without secret found 2025-08-06 20:02:03.437 +00:00 [DBG] Parser found secret: PostBodySecretParser 2025-08-06 20:02:03.437 +00:00 [DBG] Secret id found: Civit.UserAccounts 2025-08-06 20:02:03.449 +00:00 [DBG] client configuration validation for client Civit.UserAccounts succeeded. 2025-08-06 20:02:03.449 +00:00 [DBG] Public Client - skipping secret validation success 2025-08-06 20:02:03.449 +00:00 [DBG] Client validation success 2025-08-06 20:02:03.449 +00:00 [INF] {"ClientId":"Civit.UserAccounts","AuthenticationMethod":"NoSecret","Category":"Authentication","Name":"Client Authentication Success","EventType":"Success","Id":1010,"Message":null,"ActivityId":"0HNEL3G9N6E5J:00000002","TimeStamp":"2025-08-06T20:02:03.0000000Z","ProcessId":1,"LocalIpAddress":"::ffff:172.19.0.6:44374","RemoteIpAddress":"::ffff:172.19.0.1","$type":"ClientAuthenticationSuccessEvent"} 2025-08-06 20:02:03.449 +00:00 [DBG] Start token request validation 2025-08-06 20:02:03.449 +00:00 [DBG] Start validation of refresh token request 2025-08-06 20:02:03.454 +00:00 [INF] Successfully validated the token. 2025-08-06 20:02:03.454 +00:00 [DBG] AuthenticationScheme: Bearer was successfully authenticated. 2025-08-06 20:02:03.456 +00:00 [DBG] CORS request made for path: /api/app/Licences/GetKey from origin: http://localhost:4200 but was ignored because path was not for an allowed IdentityServer CORS endpoint 2025-08-06 20:02:03.456 +00:00 [INF] No CORS policy found for the specified request. 2025-08-06 20:02:03.464 +00:00 [INF] Authorization was successful. 2025-08-06 20:02:03.465 +00:00 [INF] CORS policy execution successful. 2025-08-06 20:02:03.465 +00:00 [INF] Executing endpoint 'SEL.Civit.Licences.LicencesAppService.GetKey (SEL.Civit.Application)' 2025-08-06 20:02:03.465 +00:00 [INF] Route matched with {action = "GetKey", controller = "Licences", area = "", page = ""}. Executing controller action with signature System.String GetKey(ToolIds) on controller SEL.Civit.Licences.LicencesAppService (SEL.Civit.Application). 2025-08-06 20:02:03.466 +00:00 [INF] Executing ObjectResult, writing value of type 'System.String'. 2025-08-06 20:02:03.466 +00:00 [INF] Executed action SEL.Civit.Licences.LicencesAppService.GetKey (SEL.Civit.Application) in 1.0015ms 2025-08-06 20:02:03.466 +00:00 [INF] Executed endpoint 'SEL.Civit.Licences.LicencesAppService.GetKey (SEL.Civit.Application)' 2025-08-06 20:02:03.466 +00:00 [INF] Request finished HTTP/1.0 GET https://civitpermithost.com/api/app/Licences/GetKey?toolKey=1 - - - 200 - text/plain;+charset=utf-8 37.7251ms 2025-08-06 20:02:03.518 +00:00 [DBG] Validation of refresh token request success 2025-08-06 20:02:03.518 +00:00 [INF] Token request validation success, {"ClientId":"Civit.UserAccounts","ClientName":"Civit User Accounts","GrantType":"refresh_token","Scopes":null,"AuthorizationCode":"********","RefreshToken":"****E2CE","UserName":null,"AuthenticationContextReferenceClasses":null,"Tenant":null,"IdP":null,"Raw":{"grant_type":"refresh_token","refresh_token":"REDACTED","scope":"openid profile Civit offline_access","client_id":"Civit.UserAccounts"},"$type":"TokenRequestValidationLog"} 2025-08-06 20:02:03.519 +00:00 [DBG] Updating refresh token 2025-08-06 20:02:03.519 +00:00 [DBG] Token usage is one-time only. Setting current handle as consumed, and generating new handle 2025-08-06 20:02:03.539 +00:00 [DBG] Created refresh token in store 2025-08-06 20:02:03.563 +00:00 [DBG] Getting claims for identity token for subject: 13116f2d-26dd-1fd9-573d-3a17197a7b17 and client: Civit.UserAccounts 2025-08-06 20:02:03.563 +00:00 [DBG] In addition to an id_token, an access_token was requested. No claims other than sub are included in the id_token. To obtain more user claims, either use the user info endpoint or set AlwaysIncludeUserClaimsInIdToken on the client configuration. 2025-08-06 20:02:03.565 +00:00 [INF] {"ClientId":"Civit.UserAccounts","ClientName":"Civit User Accounts","RedirectUri":null,"Endpoint":"Token","SubjectId":"13116f2d-26dd-1fd9-573d-3a17197a7b17","Scopes":"openid profile Civit offline_access","GrantType":"refresh_token","Tokens":[{"TokenType":"id_token","TokenValue":"****M9Kg","$type":"Token"},{"TokenType":"refresh_token","TokenValue":"****B78E","$type":"Token"},{"TokenType":"access_token","TokenValue":"****vy6A","$type":"Token"}],"Category":"Token","Name":"Token Issued Success","EventType":"Success","Id":2000,"Message":null,"ActivityId":"0HNEL3G9N6E5J:00000002","TimeStamp":"2025-08-06T20:02:03.0000000Z","ProcessId":1,"LocalIpAddress":"::ffff:172.19.0.6:44374","RemoteIpAddress":"::ffff:172.19.0.1","$type":"TokenIssuedSuccessEvent"} 2025-08-06 20:02:03.565 +00:00 [DBG] Token request success. 2025-08-06 20:02:03.565 +00:00 [INF] Request finished HTTP/1.0 POST https://civitpermithost.com/connect/token application/x-www-form-urlencoded 174 - 200 - application/json;+charset=UTF-8 176.1894ms 2025-08-06 20:02:03.572 +00:00 [INF] Request starting HTTP/1.0 OPTIONS https://civitpermithost.com/connect/userinfo - - 2025-08-06 20:02:03.598 +00:00 [DBG] AuthenticationScheme: Bearer was not authenticated. 2025-08-06 20:02:03.598 +00:00 [DBG] CORS request made for path: /connect/userinfo from origin: https://vmc.civitpermit.in 2025-08-06 20:02:03.599 +00:00 [DBG] CorsPolicyService allowed origin: https://vmc.civitpermit.in 2025-08-06 20:02:03.599 +00:00 [INF] CORS policy execution successful. 2025-08-06 20:02:03.599 +00:00 [INF] Request finished HTTP/1.0 OPTIONS https://civitpermithost.com/connect/userinfo - - - 204 - - 26.4594ms 2025-08-06 20:02:03.604 +00:00 [INF] Request starting HTTP/1.0 GET https://civitpermithost.com/connect/userinfo - - 2025-08-06 20:02:03.627 +00:00 [INF] Successfully validated the token. 2025-08-06 20:02:03.627 +00:00 [DBG] AuthenticationScheme: Bearer was successfully authenticated. 2025-08-06 20:02:03.629 +00:00 [DBG] CORS request made for path: /connect/userinfo from origin: https://vmc.civitpermit.in 2025-08-06 20:02:03.630 +00:00 [DBG] CorsPolicyService allowed origin: https://vmc.civitpermit.in 2025-08-06 20:02:03.630 +00:00 [INF] CORS policy execution successful. 2025-08-06 20:02:03.638 +00:00 [DBG] Request path /connect/userinfo matched to endpoint type Userinfo 2025-08-06 20:02:03.642 +00:00 [DBG] Endpoint enabled: Userinfo, successfully created handler: IdentityServer4.Endpoints.UserInfoEndpoint 2025-08-06 20:02:03.642 +00:00 [INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.UserInfoEndpoint for /connect/userinfo 2025-08-06 20:02:03.642 +00:00 [DBG] Start userinfo request 2025-08-06 20:02:03.642 +00:00 [DBG] Bearer token found in header 2025-08-06 20:02:03.650 +00:00 [DBG] client configuration validation for client Civit.UserAccounts succeeded. 2025-08-06 20:02:03.658 +00:00 [DBG] client configuration validation for client Civit.UserAccounts succeeded. 2025-08-06 20:02:03.671 +00:00 [DBG] Calling into custom token validator: IdentityServer4.Validation.DefaultCustomTokenValidator 2025-08-06 20:02:03.671 +00:00 [DBG] Token validation success {"ClientId":null,"ClientName":null,"ValidateLifetime":true,"AccessTokenType":"Jwt","ExpectedScope":"openid","TokenHandle":null,"JwtId":null,"Claims":{"nbf":1754510523,"exp":1754514123,"iss":"https://civitpermithost.com","aud":["Civit","offline_access"],"client_id":"Civit.UserAccounts","sub":"13116f2d-26dd-1fd9-573d-3a17197a7b17","auth_time":1754478650,"idp":"local","tenantid":"221ae9cd-28df-4739-86f6-2bfafb02e791","http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname":"V Ramesh","http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname":"VMC","preferred_username":"ArchitectVMC@yopmail.com","given_name":"V Ramesh","family_name":"VMC","role":"Architect","RoleIdnCode":"4.2.1.0.0","phone_number":"9049099888","phone_number_verified":"False","email":"ArchitectVMC@yopmail.com","email_verified":"True","name":"ArchitectVMC@yopmail.com","sid":"73983096067AC211176ADBC57926663F","iat":1754478652,"scope":["openid","profile","Civit","offline_access"],"amr":"pwd"},"$type":"TokenValidationLog"} 2025-08-06 20:02:03.685 +00:00 [DBG] Creating userinfo response 2025-08-06 20:02:03.685 +00:00 [DBG] Scopes in access token: openid profile Civit offline_access 2025-08-06 20:02:03.692 +00:00 [DBG] Requested claim types: sub birthdate family_name gender given_name locale middle_name name nickname picture preferred_username profile role updated_at website zoneinfo 2025-08-06 20:02:03.737 +00:00 [INF] Profile service returned the following claim types: sub role preferred_username name given_name family_name 2025-08-06 20:02:03.737 +00:00 [DBG] End userinfo request 2025-08-06 20:02:03.737 +00:00 [INF] Request finished HTTP/1.0 GET https://civitpermithost.com/connect/userinfo - - - 200 - application/json;+charset=UTF-8 133.6617ms 2025-08-06 20:02:26.788 +00:00 [INF] Request starting HTTP/1.0 POST https://civitpermithost.com/connect/token application/x-www-form-urlencoded 98
-
0
hi
There is no error in your logs.
Can I reproduce it online?
Thanks.
-
0
mailed you reference on <liming.ma@volosoft.com>
-
0
Hii will you check this on priority, I need to make it live
-
0
hi
Can you share a project that can be run and reproduce the problem?
Thanks.
-
0
Hii I have shared you project please check waiting for your reply
-
0
-
0